Fakecall malware employs vishing, a sneaky tactic where scammers use fake phone calls to trick…
Cybersecurity

Malware Analysis Unmasking Digital Threats
Malware analysis: It sounds intense, right? But understanding how malicious software works is crucial in…

Hikvision Network Camera Flaw A Security Breakdown
Hikvision network camera flaw – those three words might send shivers down the spine of…

Lightspy iOS Malware Upgraded A Deeper Dive
Lightspy iOS malware upgraded represents a significant escalation in the mobile threat landscape. This isn’t…

Russian Hackers Attacking Ukraine Military
Russian hackers attacking Ukraine military: It’s a digital battlefield, a silent war waged with malware,…

Building a SOC Your Cybersecurity Fortress
Building a SOC isn’t just about throwing tech at the wall; it’s about strategically fortifying…
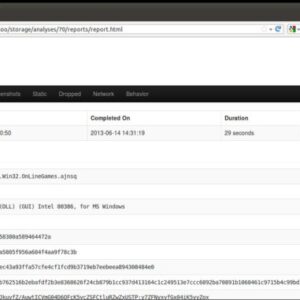
Malware Analysis Report A Deep Dive
Malware analysis report: Uncover the dark secrets of malicious code! This isn’t your grandma’s tech…

ATPC Cyber Forum Next-Gen Cybersecurity
ATPC Cyber Forum to focus on next generation cybersecurity—that’s a mouthful, right? But it’s a…

Phishing Attack Weaponized RDP File
Phishing attack weaponized RDP file: Sounds scary, right? It should. This isn’t your grandpappy’s phishing…

Hackers Downgrading Remote Desktop Security
Hackers downgrading remote desktop security? Yeah, it’s a bigger deal than you think. This isn’t…

WRNRAT Delivered Gambling Games A Deep Dive
WRNRAT delivered gambling games: sounds sketchy, right? This isn’t your grandma’s bingo night. We’re diving…

Data Center Ransomware Attacks A Growing Threat
Data center ransomware attacks are no longer a futuristic nightmare; they’re a brutal reality shaping…

Hackers Fog Ransomware SonicWall VPN Exploit
Hackers Fog ransomware SonicWall VPN: The chilling reality is that your seemingly secure VPN could…
Black Basta Microsoft Teams A Cybersecurity Threat
Black Basta Microsoft Teams: The chilling reality is that this seemingly innocuous collaboration tool can…

Windows Downgrade Attack A Deep Dive
Windows downgrade attacks: Ever heard of hackers deliberately *downgrading* your Windows version? It sounds counterintuitive,…

Which is Better for Your Business Security?
Which is better for your business security? That’s the million-dollar question every entrepreneur wrestles with….
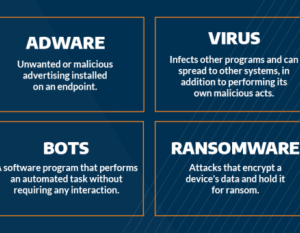
Redline and Meta Infostealers A Deep Dive
Redline and meta infostealers: Sounds like something straight out of a cyberpunk thriller, right? Wrong….

NVIDIA GPU Display Driver Vulnerabilities
NVIDIA GPU display driver vulnerabilities: They sound technical, right? But these flaws aren’t just for…

VMware vCenter Server RCE Vulnerability A Deep Dive
VMware vCenter Server RCE vulnerability: Sounds scary, right? It should. This critical flaw allows attackers…

Weekly Cybersecurity Newsletter October Top Threats & Tips
Weekly Cybersecurity Newsletter October: Dive into the digital dangers and defenses of October! This month…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
