Sweet security announces availability of its cloud native detection response platform – Sweet Security announces…
Cybersecurity
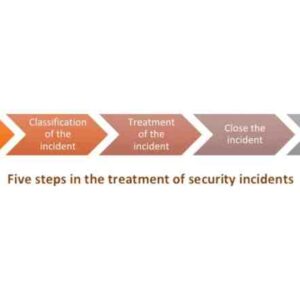
Incident Response Steps A Practical Guide
Incident response steps are your cybersecurity survival guide. Think of it like this: your digital…

Roblox Developers Under Attack A Growing Threat
Roblox developers under attack – it’s a chilling reality. Cybercriminals are increasingly targeting creators on…

Cisco Identity Services Engine Flaw 2 Exposed
Cisco Identity Services Engine Flaw 2? Yeah, we’re diving headfirst into this serious security vulnerability….

How to Assess and Improve Your Companys Cybersecurity Posture
How to assess and improve your companys cybersecurity posture – How to assess and improve…

Cisco Flaw Attackers Command Root User
Cisco flaw attackers command root user—that’s the chilling reality facing network administrators. A newly discovered…

Hackers Employ Zip File Concatenation
Hackers employ zip file concatenation—a sneaky technique where malicious code hides within seemingly innocent zipped…

100 Fake Web Stores Steal Data A Shocking Truth
100 fake web stores steal data—that’s not a typo. This isn’t some sci-fi thriller; it’s…

Hookbot Overlay Attacks Data Theft Exposed
Hookbot overlay attacks data theft – Hookbot overlay attacks: data theft is a sneaky digital…

Nokia Investigating Data Breach
Nokia investigating data breach: The tech giant’s recent security scare has sent ripples through the…
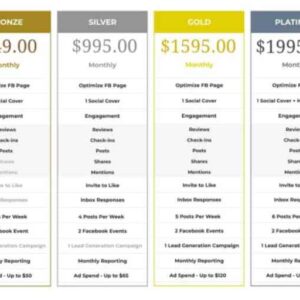
SOC Pricing A Deep Dive
SOC pricing: It’s the elephant in the room when it comes to securing your digital…
AV EDR Bypass Tool Cracking Endpoint Security
AV EDR bypass tools: the shadowy figures lurking in the digital world, silently slipping past…

Chinese Hackers Target Microsoft Customers
Chinese hackers microsoft customers – Chinese hackers targeting Microsoft customers? It’s a bigger deal than…

Okta Verify Agent Windows Flaw A Deep Dive
Okta Verify Agent Windows flaw: The vulnerability rocked the cybersecurity world, exposing a critical weakness…

Weekly Cybersecurity Newsletter Nov Stay Safe Online
Weekly Cybersecurity Newsletter Nov: Dive into the digital wild west of November, where cyber threats…

Opera Browser 0 Day Flaw A Critical Vulnerability
Opera browser 0 day flaw? Yeah, that’s a serious buzzkill. Imagine a hidden backdoor in…

LastPass Hackers Misusing Reviews
LastPass hackers misusing reviews? It’s a wild ride, folks. This isn’t your grandma’s password manager…

Okta AD LDAP Authentication Vulnerability Exposed
Okta AD LDAP authentication vulnerability: Sounds boring, right? Wrong. This seemingly technical glitch is a…

Email Phishing Playbook A Deep Dive
Email Phishing Playbook: Navigating the treacherous waters of online deception requires a deep understanding of…

DDoS Service Provider Seized The Fallout
DDoS service provider seized! The headlines scream it, but what does it *really* mean? This…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
