Zoom app vulnerability: It’s a phrase that’s become increasingly familiar, whispering anxieties about privacy and…
Cybersecurity
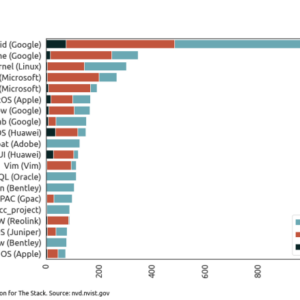
Google to Issue CVEs Security Updates Explained
Google to Issue CVEs: Ever wondered what happens behind the scenes when Google discovers a…

Bitdefender Releases ShrinkLocker Ransomware Decryptor
Bitdefender releases ShrinkLocker ransomware decryptor—a huge win for victims! This new tool offers a lifeline…

Critical KVM Infrastructure Vulnerabilities
Critical KVM infrastructure vulnerabilities? Yeah, we’re diving deep into the shadowy world of virtual machine…

Microsoft November Patch Tuesday Critical Updates
Microsoft November Patch Tuesday dropped, and it’s a big one. This month’s update tackles a…
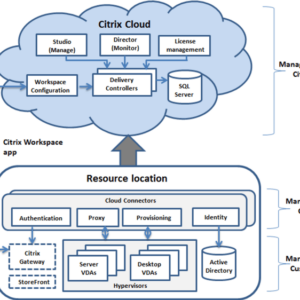
Citrix Virtual Apps Desktops RCE A Deep Dive
Citrix virtual apps desktops rce – Citrix Virtual Apps and Desktops RCE: The phrase alone…
SAP Security Update Patching Your System
SAP Security Update: Ignoring it is like leaving your front door unlocked in a bad…

Hackers Attacking GitHub Users A Deep Dive
Hackers attacking GitHub users—it’s a chilling reality for developers and open-source contributors alike. This isn’t…

Fortinet Patches Critical Flaws
Fortinet patches critical flaws: A recent wave of security updates highlights the ongoing battle against…
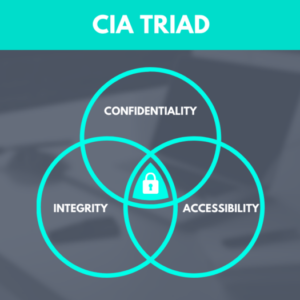
CIA Triad Confidentiality, Integrity, Availability
Cia triad confidentiality integrity availability – CIA Triad: Confidentiality, Integrity, Availability – sounds boring, right?…

Exploited Vulnerabilities 2023 A Deep Dive
Exploited vulnerabilities 2023: The digital world faced a relentless barrage of cyberattacks last year, exploiting…

How to Improve Cybersecurity Skills
How to improve cybersecurity skills? In today’s digital world, it’s not just a question, it’s…

DeltaPrime Exploited A Deep Dive
DeltaPrime exploited – the words themselves whisper of a digital heist, a silent breach in…
SelectBlinds Data Breach What Happened?
SelectBlinds data breach: The online retailer’s security lapse exposed a trove of customer data, sparking…

Dell Enterprise Sonic Vulnerabilities A Deep Dive
Dell enterprise sonic vulnerabilities – Dell Enterprise SonicWall vulnerabilities: The phrase alone sends shivers down…
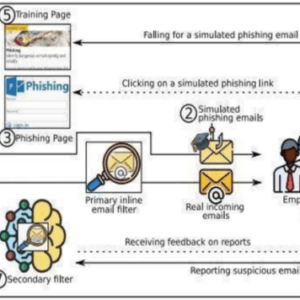
Two-Step Phishing Attack via Visio Files
Two step phishing attack via visio files – Two-step phishing attacks via Visio files are…

MoveIt 0-Day Employee Data Stolen
Moveit 0 day employee data stolen – MoveIt 0-day employee data stolen – that’s the…

Mastering Digital Privacy Your Online Shield
Mastering digital privacy isn’t about becoming a tech wizard; it’s about taking control of your…
Veeam RCE Frag Ransomware A Deep Dive
Veeam RCE Frag ransomware: the name alone conjures images of data chaos and crippling downtime….

Weekly Cybersecurity November Stay Safe Online
Weekly Cybersecurity November: This month, the digital world ramps up its defenses. We’re diving deep…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
