Xenorat weaponizes Excel XLL files, turning everyday spreadsheet add-ins into potent attack vectors. This isn’t…
Cybersecurity
Oracle Agile PLM Zero-Day Vulnerability Exposed
Oracle agile plm zero day vulnerability – Oracle Agile PLM zero-day vulnerability: Imagine a hidden…

Chrome Security Fix for Multiple Vulnerabilities
Chrome security fix for multiple vulnerabilities—that’s a headline that’s grabbed our attention, right? This isn’t…

Ford Data Breach A Deep Dive
Ford Data Breach: The headlines screamed it, the news cycled it, but what *really* happened?…

Phobos Ransomware Admin Extradited
Phobos ransomware admin extradited – the headline screams across the internet, finally delivering a victory…

Hackers Using Sitting Duck Attacks 1 Million Domains Vulnerable
Hackers using sitting ducks attack to hijack domains 1 million domains vulnerable – Hackers using…
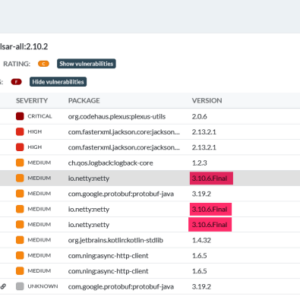
Apache Hertzbeat Vulnerability A Deep Dive
Apache Hertzbeat vulnerability: Sounds scary, right? But before you panic and start frantically Googling “how…
ZohoCorp ManageEngine AD Audit Plus Vulnerable
Zohocorp manageengine adaudit plus vulnerable – ZohoCorp ManageEngine AD Audit Plus vulnerable? Yeah, that’s a…

Team Software Breach A Deep Dive
Team software breach: It’s the digital equivalent of a heist, silently stealing sensitive data and…

BrazenBamboo APT FortiClient Zero Day Exploited
BrazenBamboo APT FortiClient zero day: The cybersecurity world just got a whole lot shadier. This…

Ensuring Data Security in CRM for Nonprofits
Ensuring data security in CRM for nonprofits isn’t just about ticking boxes; it’s about safeguarding…

NSO Developed Another WhatsApp Spyware After Being Sued
NSO developed another WhatsApp spyware even after being sued—talk about audacity! This isn’t just another…

Single Right Click Hackers Gain Access
Single right click let hackers gain access – sounds unbelievable, right? But this seemingly innocent…

T-Mobile Hacked 2 Data Breach Fallout
T mobile hacked 2 – T-Mobile Hacked 2 – the words alone send shivers down…
TP-Link DHCP Vulnerability A Deep Dive
Tp link dhcp vulnerability – TP-Link DHCP vulnerability: It sounds kinda techy, right? But this…
Analyzing Malwares Network Traffic
Analyzing malwares network traffic: It’s a digital detective story unfolding in packets and protocols. Think…
Best Password Managers Your Digital Fortress
Best password managers aren’t just about convenience; they’re your first line of defense against the…
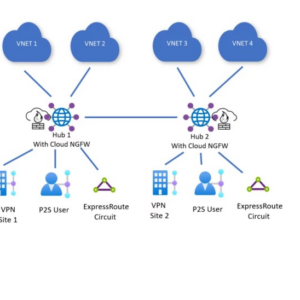
Palo Alto Firewall Management A Deep Dive
Palo Alto firewall management isn’t just about clicking buttons; it’s about orchestrating a symphony of…
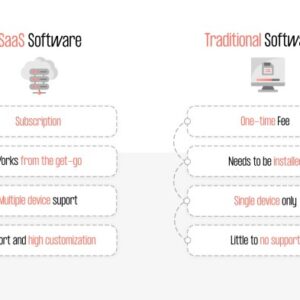
SASE vs Traditional Network Security Which Wins?
SASE vs traditional network security: It’s the cybersecurity showdown of the decade. Forget dusty firewalls…
New Glove Stealer Bypasses App Bound Encryption
New glove stealer bypass app bound encryption: Imagine a digital phantom slipping past your defenses,…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
