Multiple vulnerabilities in Veritas Enterprise Vault let attackers execute remote code—a seriously scary situation. Imagine…
Cybersecurity
Hackers Abuse URL Rewriting in Sophisticated Phishing Attacks
Hackers Abuse URL Rewriting in Sophisticated Phishing Attacks: Think you can spot a phishing link?…
Hatvibe CherrySpy Hacking Tools Used in Attacks
Hatvibe cherryspy hacking tools used in attacks – Hatvibe and CherrySpy hacking tools used in…
Microsoft Seizes 240 Phishing Domains
Microsoft Seizes 240 Phishing Domains: Whoa, that’s a lot of fishy business! Imagine the scale…

Multiple D-Link End-of-Life Routers Vulnerabilities Exposed
Multiple d link end of life routers vulnerabilities – Multiple D-Link end-of-life routers vulnerabilities? Yeah,…

CISA Warns of Apple, Oracle, Agile Vulnerabilities
Cisa warns of apple oracle agile vulnerabilities – CISA warns of Apple, Oracle, and Agile…
Chinese Telecom Attack Worst Hack Ever?
Chinese Telecom attack as worst hack? The sheer scale of this alleged cyberattack is enough…

Nvidia Base Command Manager Vulnerability A Deep Dive
Nvidia Base Command Manager vulnerability: The phrase itself sounds like a tech thriller, doesn’t it?…

Multiple Linux Kernel Vulnerabilities A Deep Dive
Multiple Linux kernel vulnerabilities represent a serious threat to system security. Imagine a fortress with…

2000 Palo Alto Firewalls Hacked A Cybersecurity Nightmare
2000 Palo Alto firewalls hacked? Whoa. That’s a seriously huge cybersecurity breach, folks. We’re talking…

Malware Persistence Mechanisms Used by Hackers
Malware persistence mechanisms used by hackers are the sneaky strategies they employ to keep their…
Gelsemium APT Hackers Attacking Linux Servers
Gelsemium APT hackers attacking Linux servers—it sounds like a scene from a cyberpunk thriller, right?…

Critical AnyDesk Vulnerability Attackers Uncover User IP Addresses
Critical AnyDesk vulnerability let attackers uncover user IP addresses—a chilling revelation that throws user privacy…
Ghost Tap Attack A Deep Dive
Ghost tap attack: Ever felt like someone’s secretly peeking at your digital life? This insidious…

Authorities Charged 5 Hackers
Authorities charged 5 hackers—a headline that screams digital drama. This isn’t your grandma’s bank robbery;…

6 Ways to Test if Your WAF is Actually Working
6 ways to test whether your waf is actually working – 6 Ways to Test…

CISA Warns of VMware vCenter Vulnerabilities
CISA warns of VMware vCenter vulnerabilities—a serious threat to organizations relying on this virtualization platform….
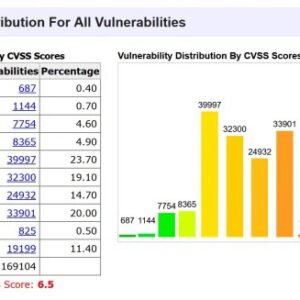
25 Most Dangerous Software Weaknesses A Deep Dive
25 Most Dangerous Software Weaknesses – sounds scary, right? It should. In today’s digital world,…
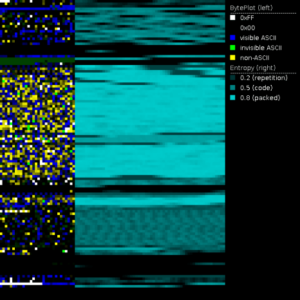
AnyRun Sandbox Now Automates Interactive Analysis
Any run sandbox now automates interactive analysis – AnyRun Sandbox Now Automates Interactive Analysis: Forget…
Trend Micro Deep Security Vulnerability A Deep Dive
Trend Micro Deep Security vulnerability—sounds scary, right? But before you panic and start frantically backing…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
