HPE Insight Remote Support vulnerabilities: Think your server’s locked down tight? Think again. This seemingly…
Cybersecurity
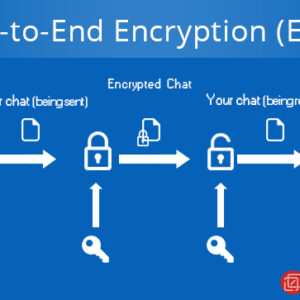
End-to-End Encryption Your Digital Privacy Shield
End to end encryption – End-to-End Encryption: It sounds techy, right? But it’s the secret…

Windows 11 Integer Overflow Vulnerability Explored
Windows 11 integer overflow vulnerability: Sounds scary, right? But before you panic and start reinstalling…
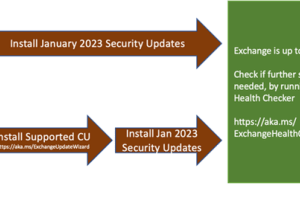
Microsoft Re-Releases Exchange Server Security Update
Microsoft re releases exchange server security update – Microsoft re-releases Exchange Server security update—and this…

China Corporate Academic Assets for Offensive Attacks
China Corporate Academic Assets for Offensive Attacks: It’s a chilling thought, isn’t it? The lines…

T-Mobile Chinese Salt Typhoon Hackers
T mobile chinese salt typhoon hackers – T-Mobile Chinese Salt Typhoon Hackers: Imagine this: a…

Black Basta Ransomware Attacking Microsoft Teams
Black Basta ransomware attacking Microsoft Teams? Yeah, it’s happening. This isn’t your grandpappy’s ransomware; Black…

Hackers Launch Zero-Day Attacks Via Corrupted Files
Hackers launch zero day attacks to exploits corrupted files to evade security tools – Hackers…
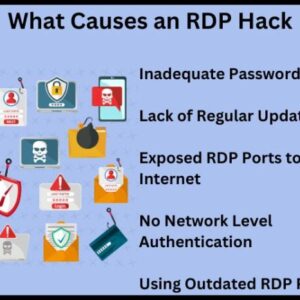
Elpaco Ransomware via RDP A Deep Dive
Elpaco ransomware via RDP: It sounds like a sci-fi thriller, right? But this isn’t fiction….

Chinese APT Attacking Telecoms A Deep Dive
Chinese APT attacking telecoms – it sounds like a spy thriller, right? And it is,…
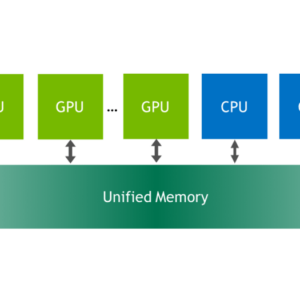
Nvidia UFM Vulnerability A Deep Dive
Nvidia UFM vulnerability: Sounds kinda techy, right? But this isn’t just some geeky glitch; it’s…

Hacking Health Club Computer Systems
Hacking computer systems of health club – Hacking health club computer systems: It sounds like…
VMware Aria Operations Vulnerabilities Exposed
VMware Aria Operations vulnerabilities: Think your virtualized world is safe? Think again. This isn’t your…
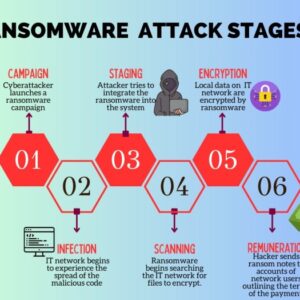
Starbucks Hit by Ransomware Attack
Starbucks hit by ransomware attack? Yep, you read that right. This isn’t your average spilled…
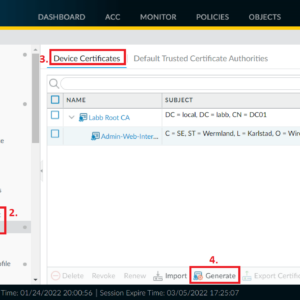
Palo Alto Certificate Validation Flaw
Palo Alto certificate validation flaw: Whoa, hold up! A critical vulnerability has been discovered in…
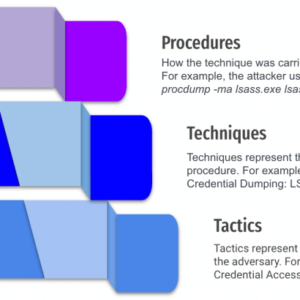
CISA Details Red Teams Activity, TTPs, Network Defense
CISA details red teams activity including TTPs network defense – sounds intense, right? It is….

MITRE ATT&CK Techniques A Deep Dive
Mitre attck techniques – MITRE ATT&CK techniques are the secret language of cyberattacks, a framework…
Hackers Abuse Avast Anti-Rootkit Driver to Evade Detection
Hackers abuse avast anti rootkit driver to evade detection – Hackers Abuse Avast Anti-Rootkit Driver…

Critical QNAP Vulnerability Remote Code Execution
Critical QNAP vulnerability let attackers execute remote code—that’s a pretty scary headline, right? Imagine this:…

Bing.com XSS Vulnerability A Deep Dive
Bing com xss vulnerability – Bing.com XSS vulnerability – sounds scary, right? It’s a serious…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.