Hackers windows users weaponized excel – Hackers: Windows Users Weaponized Excel – sounds like a…
Cyber Security
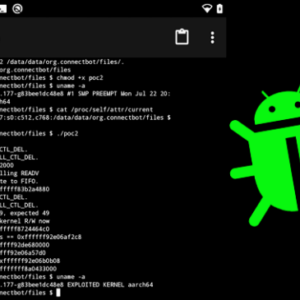
Palo Alto Android Flaws Exploited A Deep Dive
Palo Alto Android flaws exploited? Yeah, we’re diving deep into the murky world of Android…
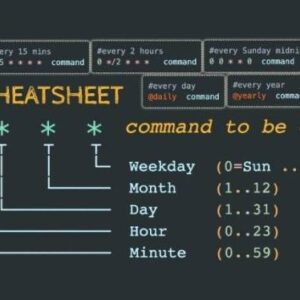
CronTrap Windows Attack A Silent Threat
CronTrap Windows attack: The very phrase whispers of unseen dangers lurking within your seemingly secure…

Malicious Files with Evidence of Execution Using Belkasoft
Malicious files with evidence of execution using Belkasoft: Unraveling the digital breadcrumbs left behind by…

APT37 Hackers Actively Scanning Targets
APT37 hackers actively scanning targets—it sounds like a scene straight out of a cyberpunk thriller,…
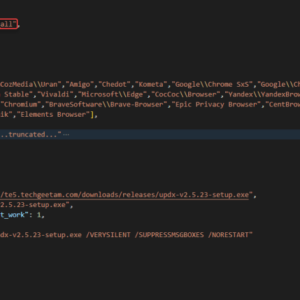
Sys01 Infostealer Attacking Meta Business
Sys01 infostealer attacking Meta business? Whoa, hold onto your hats! This isn’t your average phishing…
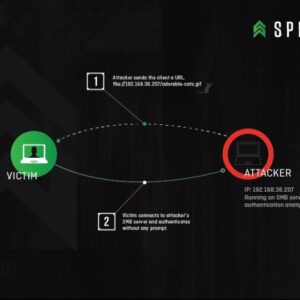
Hackers Exploiting SharePoint RCE Vulnerability
Hackers exploiting SharePoint RCE vulnerability? Yeah, it’s a bigger deal than you think. This isn’t…

IBM Flexible Service Processor Vulnerability A Deep Dive
IBM Flexible Service Processor vulnerability—sounds scary, right? It should. This isn’t your average software glitch;…

NVIDIA vGPU Software Vulnerabilities A Deep Dive
NVIDIA vGPU software vulnerabilities represent a significant threat in today’s increasingly virtualized world. These vulnerabilities,…
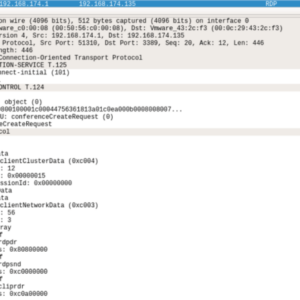
Weaponized RDP Setup Files A Deep Dive
Weaponized RDP setup files: the phrase itself sounds like something out of a cyberpunk thriller,…

DarkComet RAT A Deep Dive
DarkComet RAT, a notorious Remote Access Trojan (RAT), lurks in the digital shadows, silently infiltrating…

10M Rewards for Info on Iranian Hackers
10 m rewards for info on iranian hackers – 10M rewards for info on Iranian…

Microsoft SharePoint Vulnerability A Deep Dive
Microsoft SharePoint vulnerability: It’s a phrase that sends shivers down the spines of IT admins…

Hackers Exploiting Docker Remote API Servers
Hackers exploiting Docker Remote API servers—it sounds like a sci-fi thriller, right? But it’s a…
Akira Ransomware Rust Variant Targets ESXi Servers
Akira ransomware actors developing rust variant to attack esxi servers – Akira ransomware actors developing…
Windows Remote Registry Client EOP Flaw A Deep Dive
Windows Remote Registry Client EOP flaw? Sounds scary, right? It’s not just some tech jargon;…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
