Dell enterprise sonic vulnerabilities – Dell Enterprise SonicWall vulnerabilities: The phrase alone sends shivers down…
Cybersecurity
Two-Step Phishing Attack via Visio Files
Two step phishing attack via visio files – Two-step phishing attacks via Visio files are…

MoveIt 0-Day Employee Data Stolen
Moveit 0 day employee data stolen – MoveIt 0-day employee data stolen – that’s the…
Veeam RCE Frag Ransomware A Deep Dive
Veeam RCE Frag ransomware: the name alone conjures images of data chaos and crippling downtime….

PAN-OS Remote Code Execution Vulnerability Explored
Pan os remote code execution vulnerability – PAN-OS remote code execution vulnerability: Imagine a digital…
Fakebat Malware Via Google Ads A Deep Dive
Fakebat malware via Google Ads: It sounds like a sci-fi thriller, doesn’t it? But this…

Threat Actors Attacking macOS Users
Threat actors attacking macOS users: It’s not the image that springs to mind when you…

Weekly Cybersecurity November Stay Safe Online
Weekly Cybersecurity November: This month, the digital world ramps up its defenses. We’re diving deep…

Sweet Security Launches Cloud-Native Platform
Sweet security announces availability of its cloud native detection response platform – Sweet Security announces…
PAN-OS RCE Vulnerability 11k Interface IPS Risks
Pan os rce vulnerability 11k interface ips – PAN-OS RCE vulnerability 11k interface IPS: Sounds…
Gootloader Targets Bengal Cat Lovers
Gootloader Targets Bengal Cat Lovers: Who knew your love for fluffy, spotted felines could land…

Epson Devices Vulnerability A Deep Dive
Epson devices vulnerability: It’s a phrase that might send shivers down the spine of anyone…

Hackers Windows Users Weaponized Excel
Hackers windows users weaponized excel – Hackers: Windows Users Weaponized Excel – sounds like a…

Cisco Identity Services Engine Flaw 2 Exposed
Cisco Identity Services Engine Flaw 2? Yeah, we’re diving headfirst into this serious security vulnerability….

How to Assess and Improve Your Companys Cybersecurity Posture
How to assess and improve your companys cybersecurity posture – How to assess and improve…
Palo Alto Android Flaws Exploited A Deep Dive
Palo Alto Android flaws exploited? Yeah, we’re diving deep into the murky world of Android…

Cisco Flaw Attackers Command Root User
Cisco flaw attackers command root user—that’s the chilling reality facing network administrators. A newly discovered…

Steelfox Malware Infects 11k Windows
Steelfox malware infects 11k Windows systems—that’s a seriously scary headline, right? This isn’t some small-scale…

Hackers Employ Zip File Concatenation
Hackers employ zip file concatenation—a sneaky technique where malicious code hides within seemingly innocent zipped…
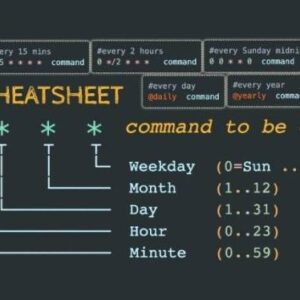
CronTrap Windows Attack A Silent Threat
CronTrap Windows attack: The very phrase whispers of unseen dangers lurking within your seemingly secure…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
