MSSP pricing can be a confusing maze, but understanding the different models is key to…
Cybersecurity
New NAND Chip Attack A Growing Threat
New NAND chip attack: The phrase itself sounds like something straight out of a cyberpunk…
Legion Stealer V1 A Deep Dive
Legion Stealer V1: The name alone whispers of digital danger. This insidious malware isn’t just…
New Glove Stealer Bypasses App Bound Encryption
New glove stealer bypass app bound encryption: Imagine a digital phantom slipping past your defenses,…

Zoom App Vulnerability A Deep Dive
Zoom app vulnerability: It’s a phrase that’s become increasingly familiar, whispering anxieties about privacy and…

How Malware Ads Compromise Smartphone Cybersecurity
How malware ads compromise smartphone cybersecurity is a scarier question than you think. We’re constantly…
Google to Issue CVEs Security Updates Explained
Google to Issue CVEs: Ever wondered what happens behind the scenes when Google discovers a…

Chinese Hackers Target US Govt Officials
Chinese hackers us govt officials – Chinese hackers targeting US government officials: a shadowy cyber…
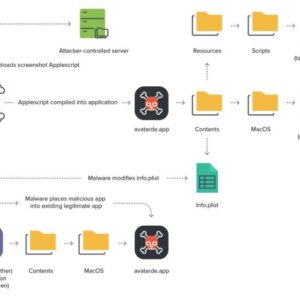
APT Hackers Leverage macOS Flutter Apps
APT hackers leverage macOS Flutter apps, exploiting vulnerabilities to infiltrate systems. These seemingly innocuous applications…

Bitdefender Releases ShrinkLocker Ransomware Decryptor
Bitdefender releases ShrinkLocker ransomware decryptor—a huge win for victims! This new tool offers a lifeline…
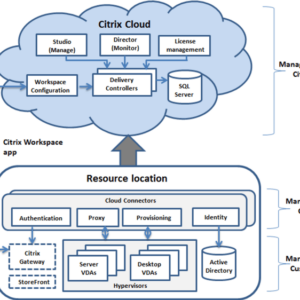
Citrix Virtual Apps Desktops RCE A Deep Dive
Citrix virtual apps desktops rce – Citrix Virtual Apps and Desktops RCE: The phrase alone…

China Nexus Hackers Hijack Websites
China nexus hackers hijack websites—it’s a headline that screams danger, a digital heist playing out…

Hackers Attacking GitHub Users A Deep Dive
Hackers attacking GitHub users—it’s a chilling reality for developers and open-source contributors alike. This isn’t…

CISA Microsoft Zero Day Exploited Urgent Alert
Cisa microsoft zero day exploited – CISA Microsoft zero-day exploited—that’s the headline grabbing everyone’s attention….
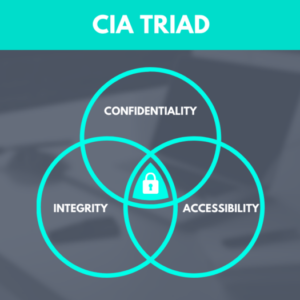
CIA Triad Confidentiality, Integrity, Availability
Cia triad confidentiality integrity availability – CIA Triad: Confidentiality, Integrity, Availability – sounds boring, right?…

Exploited Vulnerabilities 2023 A Deep Dive
Exploited vulnerabilities 2023: The digital world faced a relentless barrage of cyberattacks last year, exploiting…

How to Improve Cybersecurity Skills
How to improve cybersecurity skills? In today’s digital world, it’s not just a question, it’s…

Android Malware SpyAgent Screenshots A Deep Dive
Android malware SpyAgent screenshots: Ever wondered what lurks beneath the surface of those seemingly innocent…

DeltaPrime Exploited A Deep Dive
DeltaPrime exploited – the words themselves whisper of a digital heist, a silent breach in…
SelectBlinds Data Breach What Happened?
SelectBlinds data breach: The online retailer’s security lapse exposed a trove of customer data, sparking…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
