Trend Micro Deep Security vulnerability—sounds scary, right? But before you panic and start frantically backing…
Cybersecurity

Xenorat Weaponizes Excel XLL Files
Xenorat weaponizes Excel XLL files, turning everyday spreadsheet add-ins into potent attack vectors. This isn’t…
Oracle Agile PLM Zero-Day Vulnerability Exposed
Oracle agile plm zero day vulnerability – Oracle Agile PLM zero-day vulnerability: Imagine a hidden…

Ford Data Breach A Deep Dive
Ford Data Breach: The headlines screamed it, the news cycled it, but what *really* happened?…

Phobos Ransomware Admin Extradited
Phobos ransomware admin extradited – the headline screams across the internet, finally delivering a victory…

Hackers Using Sitting Duck Attacks 1 Million Domains Vulnerable
Hackers using sitting ducks attack to hijack domains 1 million domains vulnerable – Hackers using…
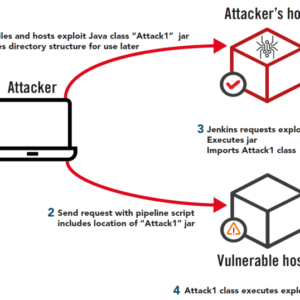
VMware vCenter Server RCE Vulnerability 2 A Deep Dive
VMware vCenter Server RCE Vulnerability 2—the words alone send shivers down the spines of IT…

Maxar Space Systems Suffers Data Breach
Maxar Space Systems suffers data breach – a headline that sent shockwaves through the aerospace…

Team Software Breach A Deep Dive
Team software breach: It’s the digital equivalent of a heist, silently stealing sensitive data and…

Samba AD Vulnerability A Deep Dive
Samba AD vulnerability: It sounds technical, right? But this hidden threat could be silently sabotaging…

BrazenBamboo APT FortiClient Zero Day Exploited
BrazenBamboo APT FortiClient zero day: The cybersecurity world just got a whole lot shadier. This…

Citrix Virtual Apps Desktops Flaw Exploit
Citrix Virtual Apps Desktops flaw exploit: The digital world’s a wild west, and Citrix, a…

Single Right Click Hackers Gain Access
Single right click let hackers gain access – sounds unbelievable, right? But this seemingly innocent…

T-Mobile Hacked 2 Data Breach Fallout
T mobile hacked 2 – T-Mobile Hacked 2 – the words alone send shivers down…

Researchers Detailed Wezrats Attack Commands
Researchers detailed wezrat know for executing attackers commands – Researchers detailed Wezrat, a potent remote…
Analyzing Malwares Network Traffic
Analyzing malwares network traffic: It’s a digital detective story unfolding in packets and protocols. Think…

Lodarat Malware Attacking Windows Users
Lodarat malware attacking Windows users is a serious threat, silently infiltrating systems and wreaking havoc….

Hackers Exploiting Multiple Palo Alto Networks Vulnerabilities
Hackers exploiting multiple Palo Alto Networks vulnerabilities—it sounds like a sci-fi thriller, right? But this…
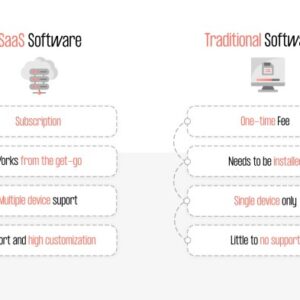
SASE vs Traditional Network Security Which Wins?
SASE vs traditional network security: It’s the cybersecurity showdown of the decade. Forget dusty firewalls…

Hackers Evading MacOS Systems A Deep Dive
Hackers evading MacOS systems isn’t just a sci-fi movie plot; it’s a growing reality. Think…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.