Intel on north korean chinese hackers at cyberwarcon – CyberWarCon Intel: North Korean-Chinese Hackers –…
Cybersecurity
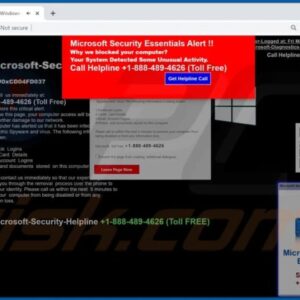
Microsoft Seizes 240 Phishing Domains
Microsoft Seizes 240 Phishing Domains: Whoa, that’s a lot of fishy business! Imagine the scale…

CISA Warns of Apple, Oracle, Agile Vulnerabilities
Cisa warns of apple oracle agile vulnerabilities – CISA warns of Apple, Oracle, and Agile…

Hackers Leveraging Google Docs & Weebly Services
Hackers leveraging google docs weebly services – Hackers Leveraging Google Docs & Weebly Services: Think…
Chinese Telecom Attack Worst Hack Ever?
Chinese Telecom attack as worst hack? The sheer scale of this alleged cyberattack is enough…

Nvidia Base Command Manager Vulnerability A Deep Dive
Nvidia Base Command Manager vulnerability: The phrase itself sounds like a tech thriller, doesn’t it?…

145000 Unsecured ICS Devices Exposed A Critical Threat
145000 unsecured ics devices exposed – 145,000 unsecured ICS devices exposed—that’s the chilling reality facing…
Halo Security Launches Slack Integration for Real-Time Alerts
Halo security launches slack integration for real time alerts – Halo Security launches Slack integration…

2000 Palo Alto Firewalls Hacked A Cybersecurity Nightmare
2000 Palo Alto firewalls hacked? Whoa. That’s a seriously huge cybersecurity breach, folks. We’re talking…

Malware Persistence Mechanisms Used by Hackers
Malware persistence mechanisms used by hackers are the sneaky strategies they employ to keep their…
Gelsemium APT Hackers Attacking Linux Servers
Gelsemium APT hackers attacking Linux servers—it sounds like a scene from a cyberpunk thriller, right?…

Critical AnyDesk Vulnerability Attackers Uncover User IP Addresses
Critical AnyDesk vulnerability let attackers uncover user IP addresses—a chilling revelation that throws user privacy…

Malicious PyPI Package Mimic Claude A Deep Dive
Malicious pypi package mimic chatgpt claude – Malicious PyPI package mimic Claude? Yeah, it’s a…
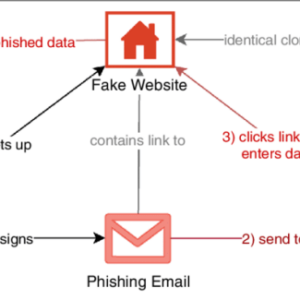
Ghost Tap Attack A Deep Dive
Ghost tap attack: Ever felt like someone’s secretly peeking at your digital life? This insidious…

Authorities Charged 5 Hackers
Authorities charged 5 hackers—a headline that screams digital drama. This isn’t your grandma’s bank robbery;…

CISA Warns of VMware vCenter Vulnerabilities
CISA warns of VMware vCenter vulnerabilities—a serious threat to organizations relying on this virtualization platform….
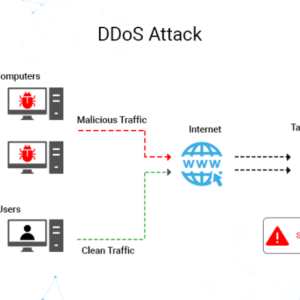
DDoS Attack Growing Bigger A Looming Threat
DDoS attack growing bigger isn’t just a headline; it’s a stark reality reshaping the digital…

Critical Kubernetes Vulnerability A Deep Dive
Critical kubernetes vulnerability – Critical Kubernetes vulnerabilities are a serious threat to modern cloud-native applications….
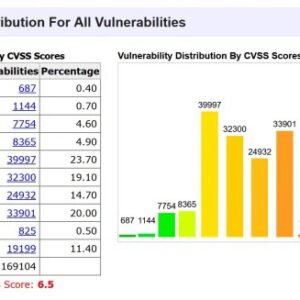
25 Most Dangerous Software Weaknesses A Deep Dive
25 Most Dangerous Software Weaknesses – sounds scary, right? It should. In today’s digital world,…
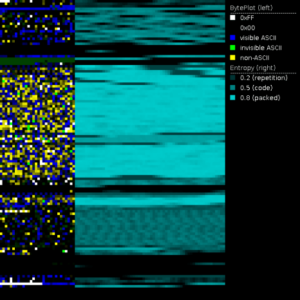
AnyRun Sandbox Now Automates Interactive Analysis
Any run sandbox now automates interactive analysis – AnyRun Sandbox Now Automates Interactive Analysis: Forget…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
