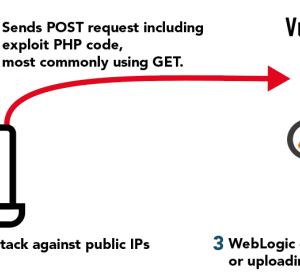
NachoVPN attack exploits RCE: Whoa, hold up! Think your VPN is untouchable? Think again. A…
Cybersecurity
20 Years Old macOS Vulnerability A Deep Dive
20 years old macOS vulnerability? Yeah, we’re diving deep into the dusty corners of Apple’s…
Hackers Weaponizing Typosquatted Libraries
Hackers weaponizing typosquatted libraries? Yeah, it’s a thing, and it’s scarier than your grandma’s Wi-Fi…
VMware Aria Operations Vulnerabilities Exposed
VMware Aria Operations vulnerabilities: Think your virtualized world is safe? Think again. This isn’t your…
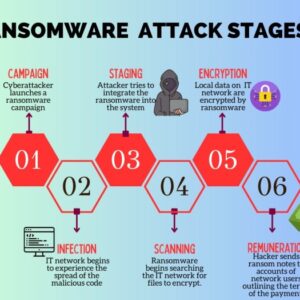
Starbucks Hit by Ransomware Attack
Starbucks hit by ransomware attack? Yep, you read that right. This isn’t your average spilled…

Attack Vectors with a Malware Sandbox
Attack vectors with a malware sandbox: Dive deep into the shadowy world of malware analysis!…

Windows Zero Days, Firefox, Rom-Coms & Groupthink
Windows zero days firefox romcom group – Windows Zero Days, Firefox, Rom-Coms & Groupthink: Sounds…
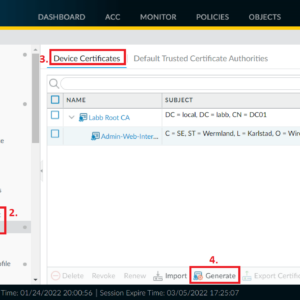
Palo Alto Certificate Validation Flaw
Palo Alto certificate validation flaw: Whoa, hold up! A critical vulnerability has been discovered in…
CISA Details Red Teams Activity, TTPs, Network Defense
CISA details red teams activity including TTPs network defense – sounds intense, right? It is….

New DocuSign Attacks Targeting Organizations
New DocuSign attacks targeting organizations are escalating, highlighting a critical vulnerability in a widely used…

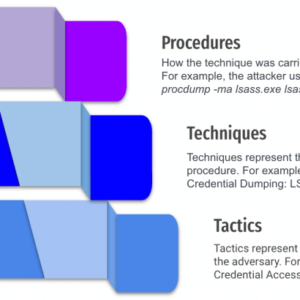
MITRE ATT&CK Techniques A Deep Dive
Mitre attck techniques – MITRE ATT&CK techniques are the secret language of cyberattacks, a framework…
Hackers Abuse Avast Anti-Rootkit Driver to Evade Detection
Hackers abuse avast anti rootkit driver to evade detection – Hackers Abuse Avast Anti-Rootkit Driver…
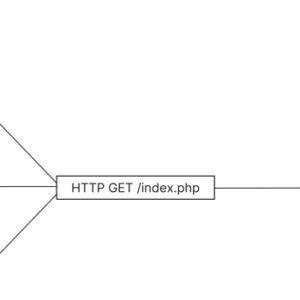
Denial of Service (DoS) Attack A Deep Dive
Denial of servicedos attack – Denial of Service (DoS) attacks: the digital equivalent of a…

Critical QNAP Vulnerability Remote Code Execution
Critical QNAP vulnerability let attackers execute remote code—that’s a pretty scary headline, right? Imagine this:…

Bing.com XSS Vulnerability A Deep Dive
Bing com xss vulnerability – Bing.com XSS vulnerability – sounds scary, right? It’s a serious…

Multiple Veritas Enterprise Vault Vulnerabilities Enable Remote Code Execution
Multiple vulnerabilities in Veritas Enterprise Vault let attackers execute remote code—a seriously scary situation. Imagine…

North Korean IT Workers Mimic US Firms for Jobs
North korean it workers mimic as us organizations for job offers – North Korean IT…
Nearest Neighbor Attack Unveiling the Threat
Nearest neighbor attack: It sounds like something out of a spy thriller, right? But this…
Hackers Abuse URL Rewriting in Sophisticated Phishing Attacks
Hackers Abuse URL Rewriting in Sophisticated Phishing Attacks: Think you can spot a phishing link?…
Hatvibe CherrySpy Hacking Tools Used in Attacks
Hatvibe cherryspy hacking tools used in attacks – Hatvibe and CherrySpy hacking tools used in…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.