Hackers can access laptop webcams—it’s a chilling reality. From sneaky malware to social engineering tricks,…
Cybersecurity

US IT Worker Sentenced for Spying
U s it worker sentenced for spying – US IT worker sentenced for spying—the headline…

Hackers Actively Deploying Zyxel Firewall Flaw
Hackers actively deploying zyxel firewall flaw – Hackers actively deploying the Zyxel firewall flaw is…
Active Directory Certificate Services Vulnerability A Deep Dive
Active Directory Certificate Services vulnerability—sounds boring, right? Wrong. Think of it as the digital equivalent…

UK Healthcare Provider Suffered Cyberattack
UK healthcare provider suffered cyberattack – a headline that chills you to the bone, right?…
GodLoader Malware Multiple Platform Threat
GodLoader malware multiple platform—that’s the chilling reality facing users today. This isn’t your grandma’s computer…

Why Cybersecurity Leaders Trust MITRE ATT&CK Evaluations
Why cybersecurity leaders trust the mitre attck evaluations – Why Cybersecurity Leaders Trust MITRE ATT&CK…

XT Exchange Hack The Inside Story
XT Exchange hack: The digital heist that rocked the crypto world. This wasn’t just another…

Skimmer Malware Credit Card Theft Exposed
Skimmer malware credit card theft: It sounds like something out of a spy thriller, right?…
End-to-End Encryption Your Digital Privacy Shield
End to end encryption – End-to-End Encryption: It sounds techy, right? But it’s the secret…

Windows 11 Integer Overflow Vulnerability Explored
Windows 11 integer overflow vulnerability: Sounds scary, right? But before you panic and start reinstalling…

Beware of PixPirate Malware A Digital Threat
Beware of PixPirate malware; it’s not just another digital headache, it’s a full-blown migraine. This…

T-Mobile Chinese Salt Typhoon Hackers
T mobile chinese salt typhoon hackers – T-Mobile Chinese Salt Typhoon Hackers: Imagine this: a…

Black Basta Ransomware Attacking Microsoft Teams
Black Basta ransomware attacking Microsoft Teams? Yeah, it’s happening. This isn’t your grandpappy’s ransomware; Black…

Hackers Launch Zero-Day Attacks Via Corrupted Files
Hackers launch zero day attacks to exploits corrupted files to evade security tools – Hackers…
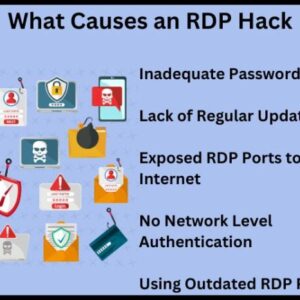
Elpaco Ransomware via RDP A Deep Dive
Elpaco ransomware via RDP: It sounds like a sci-fi thriller, right? But this isn’t fiction….

Chinese APT Attacking Telecoms A Deep Dive
Chinese APT attacking telecoms – it sounds like a spy thriller, right? And it is,…
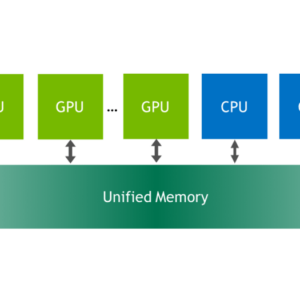
Nvidia UFM Vulnerability A Deep Dive
Nvidia UFM vulnerability: Sounds kinda techy, right? But this isn’t just some geeky glitch; it’s…
Bootkitty The First UEFI Bootkit Targeting Linux Servers
Bootkitty the first uefi bootkit targeting linux servers – Bootkitty, the first UEFI bootkit targeting…

Hacking Health Club Computer Systems
Hacking computer systems of health club – Hacking health club computer systems: It sounds like…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
