Weekly Cybersecurity Newsletter Dec: ‘Tis the season for giving…and for scammers! December brings a surge…
admin491 Pos

Hackers Stole Millions from EBT Accounts
Hackers stolen millions of dollars from ebt accounts – Hackers stole millions of dollars from…
Endpoint Protection Platform Your Digital Shield
Endpoint Protection Platform (EPP): Think of it as your digital immune system, constantly scanning and…

Elizarat Leveraging Google, Telegram, and Slack Services
Elizarat leveraging google telegram and slack services – Elizarat Leveraging Google, Telegram, and Slack Services:…

Beware of New Phishing Scams
Beware of new phishing scams! These digital traps are getting sneakier, using everything from convincing…

Hackers Can Access Laptop Webcams Stay Safe
Hackers can access laptop webcams—it’s a chilling reality. From sneaky malware to social engineering tricks,…

US IT Worker Sentenced for Spying
U s it worker sentenced for spying – US IT worker sentenced for spying—the headline…

Hackers Actively Deploying Zyxel Firewall Flaw
Hackers actively deploying zyxel firewall flaw – Hackers actively deploying the Zyxel firewall flaw is…
Active Directory Certificate Services Vulnerability A Deep Dive
Active Directory Certificate Services vulnerability—sounds boring, right? Wrong. Think of it as the digital equivalent…

UK Healthcare Provider Suffered Cyberattack
UK healthcare provider suffered cyberattack – a headline that chills you to the bone, right?…
GodLoader Malware Multiple Platform Threat
GodLoader malware multiple platform—that’s the chilling reality facing users today. This isn’t your grandma’s computer…

Why Cybersecurity Leaders Trust MITRE ATT&CK Evaluations
Why cybersecurity leaders trust the mitre attck evaluations – Why Cybersecurity Leaders Trust MITRE ATT&CK…

XT Exchange Hack The Inside Story
XT Exchange hack: The digital heist that rocked the crypto world. This wasn’t just another…

Weaponized JavaScript Projects A Deep Dive
Weaponized JavaScript projects: Sounds like a villain’s plot straight out of a cyberpunk movie, right?…

Zabbix SQL Injection Vulnerability A Deep Dive
Zabbix SQL injection vulnerability: It sounds technical, right? But this sneaky security flaw can unravel…

Skimmer Malware Credit Card Theft Exposed
Skimmer malware credit card theft: It sounds like something out of a spy thriller, right?…
HPE Insight Remote Support Vulnerabilities
HPE Insight Remote Support vulnerabilities: Think your server’s locked down tight? Think again. This seemingly…
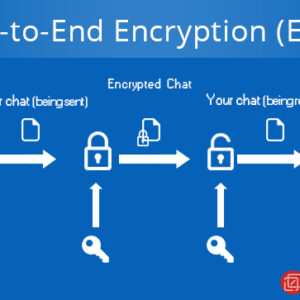
End-to-End Encryption Your Digital Privacy Shield
End to end encryption – End-to-End Encryption: It sounds techy, right? But it’s the secret…

Windows 11 Integer Overflow Vulnerability Explored
Windows 11 integer overflow vulnerability: Sounds scary, right? But before you panic and start reinstalling…

Kemp Load Balancer Command Injection Vulnerability
Kemp Load Balancer command injection vulnerability: It sounds like something out of a cyberpunk thriller,…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
