Windows Driver Use After Free Vulnerability: Think of it like this – your computer’s driver…
admin491 Pos

Hackers Used Weaponized Resumes A Cybersecurity Threat
Hackers used weaponized resumes – it sounds like something out of a spy movie, right?…

Lifetime Jail for Hydra Developer
Lifetime jail for Hydra developer: The dark web’s infamous Hydra Market, a sprawling online bazaar…
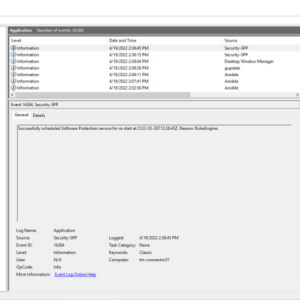
Hackers Exploited Windows Event Logs Tool
Hackers Exploited Windows Event Logs Tool: Think your system’s security logs are untouchable? Think again….

HPE IceWall Products Vulnerability A Deep Dive
HPE IceWall products vulnerability is a serious concern for organizations relying on these firewalls for…

Microsoft Unveils Windows Resiliency Initiative
Microsoft unveils Windows Resiliency Initiative – a game-changer for Windows security and stability. Forget endless…

GitHub Copilot Easier ASP.NET Core API Azure Deployments
Github copilot for azure simplifies deployment of asp net core web api – GitHub Copilot…

Deprecate Bring Your Own License Defender
Deprecate Bring Your Own License Defender: So, your trusty BYOL security solution is getting the…

Amazon GuardDuty Unveils AI-Powered Threat Detection
Amazon guardduty unveils ai powered threat detection – Amazon GuardDuty unveils AI-powered threat detection, revolutionizing…

Linux Kernel 6.13 Whats New?
Linux kernel 6 13 – Linux Kernel 6.13: Dive into the latest iteration of the…

Notepad++ v8.7.2 Launched Whats New?
Notepad v8 7 2 launched – Notepad++ v8.7.2 launched, bringing a wave of fresh features…

Rockstar 2FA Boosting Game Account Security
Rockstar 2FA: Imagine a world where your GTA Online empire, meticulously built over countless hours,…

Apple Safari Remote Code Execution Vulnerability
Apple Safari Remote Code Execution Vulnerability: Imagine this – a simple click, a seemingly harmless…

Trellix Enterprise Security Manager Flaw Urgent Security Risks
Trellix Enterprise Security Manager flaw? Yeah, we’re diving deep into the nitty-gritty of those vulnerabilities….

Mediatek Chipset Bluetooth Vulnerabilities
Mediatek chipset Bluetooth vulnerabilities: A chilling discovery. Imagine your connected devices, your personal data, suddenly…
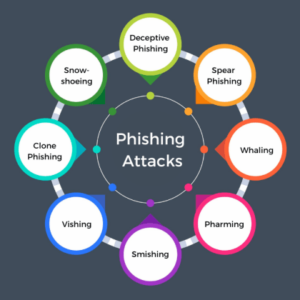
Malwareless URL Phishing Attacks A Deep Dive
Malwareless URL phishing attacks: They sound sneaky, right? And they are. Forget the viruses and…
Windows Server 2012 0-Day Vulnerability A Deep Dive
Windows server 2012 0 day vulnerability – Windows Server 2012 0-day vulnerability: the phrase alone…
IBM Security Verify Vulnerabilities A Deep Dive
IBM Security Verify vulnerabilities: Navigating the complex world of application security is a constant challenge….

Critical GPU DDK Vulnerabilities A Deep Dive
Critical GPU DDK vulnerabilities are a serious threat, lurking beneath the surface of our seemingly…
InputSnatch Novel Side Channel Attack
InputSnatch novel side channel attacks: Ever heard of hackers stealing your data not by cracking…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
