New Linux ransomhub attacking ESXi servers is a major cybersecurity threat escalating rapidly. This isn’t…
admin491 Pos

Command Injection Vulnerability Found in Arcadyan Routers
Command injection vulnerability found in Arcadyan routers? Whoa, that’s a serious security breach! Imagine hackers…
Server Monitoring Tools Your Essential Guide
Server monitoring tools are your secret weapon in the world of website performance. Think of…

Mobile Device Management Tools A Deep Dive
Mobile device management tools are no longer a luxury; they’re a necessity in today’s hyper-connected…

Programming Languages for Cyber Security
Programming languages for cyber security aren’t just tools; they’re the very foundation upon which the…

How to Protect Your Online Privacy
How to protect your online privacy? In today’s hyper-connected world, it’s less a question of…

UnitedHealth Data Breach What Happened?
UnitedHealth data breach: The words alone send shivers down the spine, right? Imagine millions of…
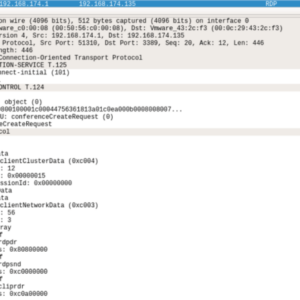
Weaponized RDP Setup Files A Deep Dive
Weaponized RDP setup files: the phrase itself sounds like something out of a cyberpunk thriller,…
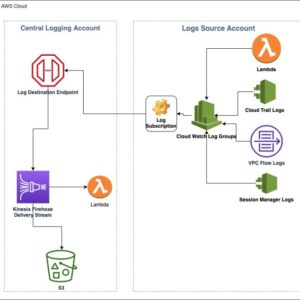
AWS CDK Vulnerabilities A Deep Dive
AWS CDK vulnerabilities: They’re lurking in your Infrastructure as Code (IaC), silently waiting to pounce….
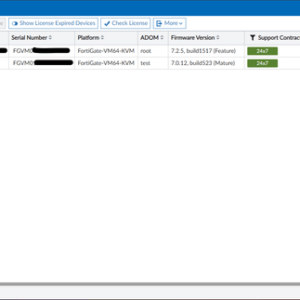
FortiManager Devices Mass Compromise A Deep Dive
FortiManager devices mass compromise: It sounds like a sci-fi thriller, right? Except this isn’t fiction….

Cisco ASA Roundcube Vulnerabilities A Deep Dive
Cisco ASA Roundcube vulnerabilities? Yeah, we’re diving headfirst into the murky waters of securing your…

NoBroker Data Breach Ransom Demand
Breach nobroker users data demands ransom – NoBroker data breach: ransom demand – the headline…
SIEM Pricing A Deep Dive
SIEM pricing: Decoding the cost of cybersecurity. Think of it like this: you’re buying peace…

DarkComet RAT A Deep Dive
DarkComet RAT, a notorious Remote Access Trojan (RAT), lurks in the digital shadows, silently infiltrating…

10M Rewards for Info on Iranian Hackers
10 m rewards for info on iranian hackers – 10M rewards for info on Iranian…

Microsoft SharePoint Vulnerability A Deep Dive
Microsoft SharePoint vulnerability: It’s a phrase that sends shivers down the spines of IT admins…

GitLab XSS DOS Condition Flaws A Deep Dive
GitLab XSS DOS condition flaws: Sounds scary, right? But fear not, internet warriors! This isn’t…
Embargo Ransomware Safe Mode Abuse
Embargo ransomware safe mode abuse – Embargo Ransomware: Safe Mode Abuse – sounds like a…
Cisco ASA SSH Remote Command Injection Flaw
Cisco ASA SSH remote command injection flaw: Think of your network’s security as a fortress….
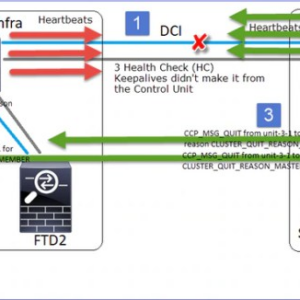
Cisco ASA FTD VPNs Vulnerability A Deep Dive
Cisco ASA FTD VPNs vulnerability: Sounds scary, right? But don’t panic. This isn’t just another…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
