Evasive Panda Attacking Cloud Services: Picture this: a stealthy panda, surprisingly agile and cunning, infiltrating…
admin491 Pos
INE Launches Initiative to Optimize Year-End Training Budgets
Ine launches initiative to optimize year end training budgets – INE launches initiative to optimize…

Data Center Ransomware Attacks A Growing Threat
Data center ransomware attacks are no longer a futuristic nightmare; they’re a brutal reality shaping…

Phishing Attack Mimics Nintendo
Phishing Attack Mimics Nintendo: Level up your awareness! Gamers, rejoice! Or maybe…panic? This isn’t about…

Apple VisionOS 2.1 Security Vulnerabilities
Apple visionos 2 1 security vulnerabilities – Apple VisionOS 2.1 security vulnerabilities: The sleek, futuristic…

Encoding Technique Jailbreaks 4o System
Encoding technique jailbreaks chatgpt 4o – Encoding Technique Jailbreaks 4o System: Dive into the shadowy…

China Hackers Scanning Canadian Systems
China hackers scanning Canadian systems: It sounds like a spy thriller, right? But the reality…

Hackers Fog Ransomware SonicWall VPN Exploit
Hackers Fog ransomware SonicWall VPN: The chilling reality is that your seemingly secure VPN could…

NVIDIA vGPU Software Vulnerabilities A Deep Dive
NVIDIA vGPU software vulnerabilities represent a significant threat in today’s increasingly virtualized world. These vulnerabilities,…
Black Basta Microsoft Teams A Cybersecurity Threat
Black Basta Microsoft Teams: The chilling reality is that this seemingly innocuous collaboration tool can…

Chinese Hackers Toolkit Uncovered
Chinese Hackers Toolkit Uncovered: Whoa, hold onto your hats, folks! A sophisticated hacking toolkit, allegedly…

Windows Downgrade Attack A Deep Dive
Windows downgrade attacks: Ever heard of hackers deliberately *downgrading* your Windows version? It sounds counterintuitive,…

Which is Better for Your Business Security?
Which is better for your business security? That’s the million-dollar question every entrepreneur wrestles with….
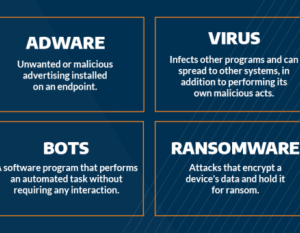
Redline and Meta Infostealers A Deep Dive
Redline and meta infostealers: Sounds like something straight out of a cyberpunk thriller, right? Wrong….

NVIDIA GPU Display Driver Vulnerabilities
NVIDIA GPU display driver vulnerabilities: They sound technical, right? But these flaws aren’t just for…

VMware vCenter Server RCE Vulnerability A Deep Dive
VMware vCenter Server RCE vulnerability: Sounds scary, right? It should. This critical flaw allows attackers…
Realtek Driver Flaws Impact Laptops
Realtek driver flaws impact laptops in ways you might not expect, from annoying glitches to…

Installing a YouTube Ad Blocker on Any Browser
Installing a YouTube ad blocker on any browser is easier than you think! Tired of…

Weekly Cybersecurity Newsletter October Top Threats & Tips
Weekly Cybersecurity Newsletter October: Dive into the digital dangers and defenses of October! This month…

Understanding the Growing Influence A Deep Dive
Understanding the growing influence is more than just recognizing who’s on top; it’s about dissecting…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
