Hackers windows users weaponized excel – Hackers: Windows Users Weaponized Excel – sounds like a…
admin491 Pos

Any Run Upgraded Linux Sandbox A Deep Dive
Any Run Upgraded Linux Sandbox – sounds kinda geeky, right? But trust us, this isn’t…

Cisco Identity Services Engine Flaw 2 Exposed
Cisco Identity Services Engine Flaw 2? Yeah, we’re diving headfirst into this serious security vulnerability….

How to Assess and Improve Your Companys Cybersecurity Posture
How to assess and improve your companys cybersecurity posture – How to assess and improve…
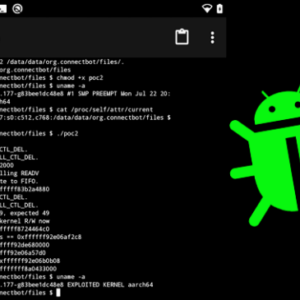
Palo Alto Android Flaws Exploited A Deep Dive
Palo Alto Android flaws exploited? Yeah, we’re diving deep into the murky world of Android…

Cisco Flaw Attackers Command Root User
Cisco flaw attackers command root user—that’s the chilling reality facing network administrators. A newly discovered…

Steelfox Malware Infects 11k Windows
Steelfox malware infects 11k Windows systems—that’s a seriously scary headline, right? This isn’t some small-scale…

Why You Should Consider a Temporary Turkish Phone Number
Why you should consider a temporary Turkish phone number? Think beyond just a phone number;…

Hackers Employ Zip File Concatenation
Hackers employ zip file concatenation—a sneaky technique where malicious code hides within seemingly innocent zipped…
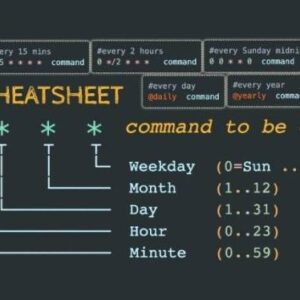
CronTrap Windows Attack A Silent Threat
CronTrap Windows attack: The very phrase whispers of unseen dangers lurking within your seemingly secure…
Azure APIM Vulnerabilities A Deep Dive
Azure APIM vulnerabilities are a serious concern for any organization relying on this platform for…

100 Fake Web Stores Steal Data A Shocking Truth
100 fake web stores steal data—that’s not a typo. This isn’t some sci-fi thriller; it’s…

ClickFix Leveraging GMeet and Zoom
ClickFix leveraging GMeet and Zoom: Imagine a world where troubleshooting is seamless, collaboration is instant,…

North Korean Hackers Acquire Remote Jobs
North Korean hackers acquire remote jobs, using sophisticated techniques to infiltrate companies globally. They craft…

Rockwell Automation ThinManager Vulnerability A Deep Dive
Rockwell Automation ThinManager vulnerability: Sounds boring, right? Wrong. This seemingly technical issue holds the potential…

MDR Services Price A Deep Dive
MDR services price: Decoding the cost of managed detection and response can feel like navigating…

Hookbot Overlay Attacks Data Theft Exposed
Hookbot overlay attacks data theft – Hookbot overlay attacks: data theft is a sneaky digital…

Chrome Security Update Vulnerabilities
Chrome security update vulnerabilities: Think your browser’s updates are just a bunch of boring code…

Nokia Investigating Data Breach
Nokia investigating data breach: The tech giant’s recent security scare has sent ripples through the…

Pygmy Goat Network Device Backdoor A Deep Dive
Pygmy Goat Network Device Backdoor: Imagine a seemingly innocent pygmy goat statue secretly harboring a…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
