Dell enterprise sonic vulnerabilities – Dell Enterprise SonicWall vulnerabilities: The phrase alone sends shivers down…
admin491 Pos
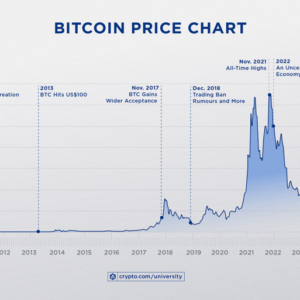
Evolution Bitcoin Trading Platforms A Deep Dive
Evolution Bitcoin trading platforms: From clunky early exchanges to the sleek, sophisticated platforms of today,…

VMware Workstation Free Users A Deep Dive
VMware Workstation Free users represent a diverse group, ranging from students experimenting with virtual machines…
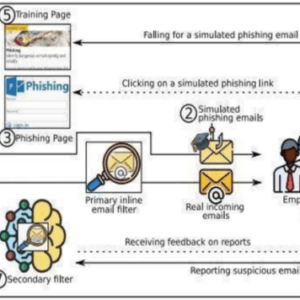
Two-Step Phishing Attack via Visio Files
Two step phishing attack via visio files – Two-step phishing attacks via Visio files are…

MoveIt 0-Day Employee Data Stolen
Moveit 0 day employee data stolen – MoveIt 0-day employee data stolen – that’s the…

How to Choose the Right Proxy Provider
How to choose the right proxy provider? Navigating the world of proxies can feel like…

Mastering Digital Privacy Your Online Shield
Mastering digital privacy isn’t about becoming a tech wizard; it’s about taking control of your…
Veeam RCE Frag Ransomware A Deep Dive
Veeam RCE Frag ransomware: the name alone conjures images of data chaos and crippling downtime….

PAN-OS Remote Code Execution Vulnerability Explored
Pan os remote code execution vulnerability – PAN-OS remote code execution vulnerability: Imagine a digital…
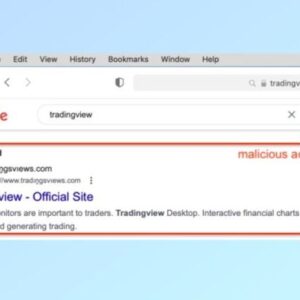
Fakebat Malware Via Google Ads A Deep Dive
Fakebat malware via Google Ads: It sounds like a sci-fi thriller, doesn’t it? But this…

Threat Actors Attacking macOS Users
Threat actors attacking macOS users: It’s not the image that springs to mind when you…

Beware of Fake Copyright Claims
Beware of fake copyright claims! The internet’s wild west has spawned a new breed of…

Weekly Cybersecurity November Stay Safe Online
Weekly Cybersecurity November: This month, the digital world ramps up its defenses. We’re diving deep…

Sweet Security Launches Cloud-Native Platform
Sweet security announces availability of its cloud native detection response platform – Sweet Security announces…
PAN-OS RCE Vulnerability 11k Interface IPS Risks
Pan os rce vulnerability 11k interface ips – PAN-OS RCE vulnerability 11k interface IPS: Sounds…
Gootloader Targets Bengal Cat Lovers
Gootloader Targets Bengal Cat Lovers: Who knew your love for fluffy, spotted felines could land…
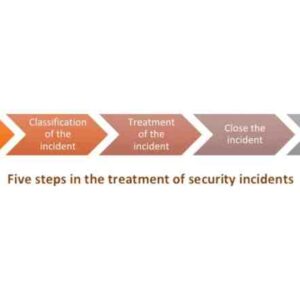
Incident Response Steps A Practical Guide
Incident response steps are your cybersecurity survival guide. Think of it like this: your digital…

Epson Devices Vulnerability A Deep Dive
Epson devices vulnerability: It’s a phrase that might send shivers down the spine of anyone…

Roblox Developers Under Attack A Growing Threat
Roblox developers under attack – it’s a chilling reality. Cybercriminals are increasingly targeting creators on…

Bookings Flaw Impersonate A Growing Threat
Bookings flaw impersonate: It sounds like something out of a spy movie, right? But the…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.
