Gelsemium APT hackers attacking Linux servers—it sounds like a scene from a cyberpunk thriller, right?…
admin491 Pos

Critical AnyDesk Vulnerability Attackers Uncover User IP Addresses
Critical AnyDesk vulnerability let attackers uncover user IP addresses—a chilling revelation that throws user privacy…

Malicious PyPI Package Mimic Claude A Deep Dive
Malicious pypi package mimic chatgpt claude – Malicious PyPI package mimic Claude? Yeah, it’s a…
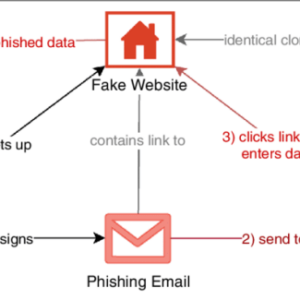
Ghost Tap Attack A Deep Dive
Ghost tap attack: Ever felt like someone’s secretly peeking at your digital life? This insidious…

Authorities Charged 5 Hackers
Authorities charged 5 hackers—a headline that screams digital drama. This isn’t your grandma’s bank robbery;…

6 Ways to Test if Your WAF is Actually Working
6 ways to test whether your waf is actually working – 6 Ways to Test…

CISA Warns of VMware vCenter Vulnerabilities
CISA warns of VMware vCenter vulnerabilities—a serious threat to organizations relying on this virtualization platform….
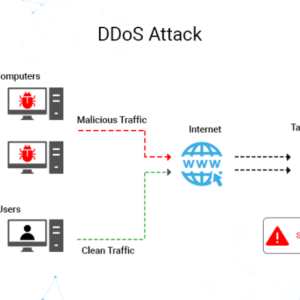
DDoS Attack Growing Bigger A Looming Threat
DDoS attack growing bigger isn’t just a headline; it’s a stark reality reshaping the digital…

Critical Kubernetes Vulnerability A Deep Dive
Critical kubernetes vulnerability – Critical Kubernetes vulnerabilities are a serious threat to modern cloud-native applications….
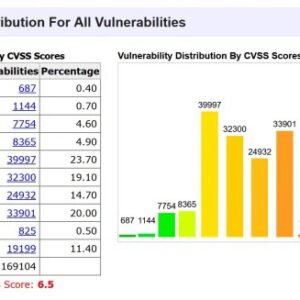
25 Most Dangerous Software Weaknesses A Deep Dive
25 Most Dangerous Software Weaknesses – sounds scary, right? It should. In today’s digital world,…
macOS WorkflowKit Race Vulnerability A Deep Dive
macOS WorkflowKit race vulnerability: Imagine this – a hidden flaw in your Mac’s core, allowing…
AnyRun Sandbox Now Automates Interactive Analysis
Any run sandbox now automates interactive analysis – AnyRun Sandbox Now Automates Interactive Analysis: Forget…

Wireshark 4.4.2 Released Whats New?
Wireshark 4 4 2 released – Wireshark 4.4.2 released—and the network analysis world just got…

Microsoft Ignite New 360 Degree A Tech Revolution
Microsoft Ignite New 360 Degree wasn’t just another tech conference; it was a seismic shift….
Domain Based Message Authentication Reporting & Conformance (DMARC) Explained
Domain based message authentication reporting conformancedmarc – Domain Based Message Authentication Reporting & Conformance (DMARC):…
Trend Micro Deep Security Vulnerability A Deep Dive
Trend Micro Deep Security vulnerability—sounds scary, right? But before you panic and start frantically backing…

Xenorat Weaponizes Excel XLL Files
Xenorat weaponizes Excel XLL files, turning everyday spreadsheet add-ins into potent attack vectors. This isn’t…
Gabagool Leveraging Cloudflare R2 Storage
Gabagool leveraging cloudflares r2 storage service – Gabagool Leveraging Cloudflare R2 Storage Service: Think you’ve…

Apple Security Update 2 Whats New?
Apple Security Update 2 drops, and it’s not just another incremental tweak. This update packs…
Oracle Agile PLM Zero-Day Vulnerability Exposed
Oracle agile plm zero day vulnerability – Oracle Agile PLM zero-day vulnerability: Imagine a hidden…
Tidak Ada Postingan Lagi.
Tidak ada lagi halaman untuk dimuat.