Cia triad confidentiality integrity availability – CIA Triad: Confidentiality, Integrity, Availability – sounds boring, right? Wrong! This foundational security model is the bedrock of keeping your data safe, and understanding it is way more exciting than you think. We’re diving deep into the nitty-gritty of protecting your digital assets, exploring how confidentiality, integrity, and availability intertwine to create a fortress against cyber threats. Prepare for a wild ride through encryption, hashing, and disaster recovery – because your data’s safety depends on it.
Think of it like this: confidentiality is keeping your secrets secret, integrity ensures your data isn’t tampered with, and availability means your stuff is always there when you need it. Each pillar is crucial, and a weakness in one can bring the whole system crashing down. We’ll unravel the complexities, explore real-world examples of successes and failures, and arm you with the knowledge to protect your digital kingdom.
Confidentiality
Confidentiality, a cornerstone of the CIA triad, ensures that sensitive information is accessible only to authorized individuals or systems. It’s about protecting data from unauthorized access, use, disclosure, disruption, modification, or destruction. Think of it as the digital equivalent of a locked safe – only those with the right key can get inside.
Confidentiality Breaches and Their Consequences
Confidentiality breaches, unfortunately, are all too common. These breaches can range from accidental exposure of sensitive data to malicious attacks aimed at stealing information. A classic example is a data leak stemming from a poorly secured database. Imagine a company’s customer database, containing names, addresses, credit card numbers, and social security numbers, being publicly accessible online. The consequences could be devastating: identity theft, financial losses for customers, hefty fines for the company, and irreparable damage to its reputation. Another example is phishing scams, where malicious actors trick individuals into revealing sensitive credentials. The fallout can include compromised accounts, financial fraud, and even blackmail. The severity of the consequences directly correlates with the sensitivity of the compromised data and the scale of the breach.
Implementing Strong Confidentiality Measures
Robust confidentiality relies on a multi-layered approach. Encryption is a crucial element. Encryption transforms readable data (plaintext) into an unreadable format (ciphertext) using a cryptographic key. Only those with the correct key can decrypt the ciphertext back into plaintext. Access control mechanisms, such as user authentication and authorization, further bolster confidentiality by restricting access to data based on predefined roles and permissions. Strong passwords, multi-factor authentication, and regular security audits are also essential components of a comprehensive confidentiality strategy. Data loss prevention (DLP) tools can monitor data movement and prevent sensitive information from leaving the network unauthorized.
A Hypothetical Scenario: Successful Confidentiality Implementation
Let’s imagine a hospital implementing a new electronic health record (EHR) system. To ensure patient confidentiality, they encrypt all patient data both at rest (on storage devices) and in transit (during transmission). Access to the EHR system is strictly controlled through multi-factor authentication, with different levels of access granted to different staff members based on their roles (doctors have access to patient records, while administrative staff only see billing information). Regular security audits ensure the system’s ongoing integrity and confidentiality. This layered approach minimizes the risk of unauthorized access to sensitive patient information, protecting patient privacy and adhering to HIPAA regulations.
Encryption Algorithm Comparison
| Algorithm | Key Size (bits) | Encryption Type | Strength |
|---|---|---|---|
| AES | 128, 192, 256 | Symmetric | Very High |
| RSA | 1024, 2048, 4096 | Asymmetric | High |
| ECC | 256, 384, 521 | Asymmetric | High |
| ChaCha20 | 256 | Symmetric | High |
Integrity
Source: securereading.com
Data integrity is the cornerstone of trustworthy information. Without it, the reliability of any data system crumbles, leading to flawed decisions and potentially catastrophic consequences. Think of it as the guarantee that your data remains accurate, complete, and consistent throughout its lifecycle. This isn’t just about preventing accidental changes; it’s about safeguarding against malicious tampering and ensuring the data you rely on truly reflects reality.
Integrity Violations and Their Impact
Compromised data integrity can manifest in various ways, each with significant repercussions. For instance, an alteration to a financial record, even a seemingly minor one, could lead to inaccurate accounting, tax problems, or even legal issues. Imagine a medical database where a patient’s allergy information is incorrectly updated—this could have life-threatening consequences. Data breaches, where unauthorized individuals modify data, are a serious threat, potentially leading to identity theft, financial loss, and reputational damage for organizations. The impact extends beyond individual incidents; systemic integrity violations can erode public trust and undermine the credibility of entire systems.
Techniques for Ensuring Data Integrity
Several robust techniques help maintain data integrity. Hashing, for example, creates a unique digital fingerprint of a data set. Any change, no matter how small, results in a different hash, instantly revealing tampering. Digital signatures, akin to digital handwriting, provide authentication and integrity verification. They use cryptography to ensure that data hasn’t been altered since it was signed. Version control systems, like Git, track changes over time, allowing for the recovery of previous versions and the identification of who made specific alterations. These techniques, used individually or in combination, significantly enhance data security and reliability.
Vulnerabilities and Mitigation Strategies
Despite these safeguards, vulnerabilities exist. SQL injection attacks, for instance, allow malicious actors to insert malicious code into database queries, potentially modifying or deleting data. Proper input validation and parameterized queries are crucial mitigations. Another vulnerability is unauthorized access to data storage systems. Strong access controls, encryption, and regular security audits are essential to prevent this. Furthermore, software bugs can introduce vulnerabilities that compromise data integrity. Thorough software testing and regular updates are vital in preventing these issues.
Best Practices for Maintaining Data Integrity within a Database System
Maintaining data integrity requires a proactive and multi-faceted approach. Here are some key best practices:
- Implement robust access control mechanisms to restrict data modification to authorized personnel only.
- Regularly back up your database to allow for recovery in case of data loss or corruption.
- Use database constraints (e.g., data type constraints, check constraints, foreign key constraints) to enforce data validity and consistency.
- Employ data validation techniques to ensure that data entered into the database conforms to predefined rules and formats.
- Conduct regular audits to identify and address potential integrity violations.
- Implement logging mechanisms to track all data modifications and identify potential anomalies.
- Utilize data encryption to protect data both in transit and at rest.
- Train database administrators and other personnel on best practices for data integrity.
Availability
Source: researchgate.net
Data availability is the cornerstone of any successful operation. It’s not just about having data; it’s about having access to that data when and where you need it. Without reliable data availability, businesses grind to a halt, projects fail, and critical decisions are delayed – leading to significant financial losses and reputational damage. Think of it as the lifeblood of your digital operations. A constant, uninterrupted flow is essential for survival and thriving.
Data unavailability can stem from a multitude of sources, each with potentially devastating consequences. Imagine the impact on a hospital’s ability to treat patients if its electronic health records system crashes. Or consider the chaos in a financial institution if its trading platform becomes inaccessible during peak hours. The consequences can range from minor inconveniences to catastrophic failures.
Causes of Data Unavailability and Their Effects
Data unavailability can arise from various events, each with varying degrees of severity. Hardware failures (server crashes, network outages), software glitches (bugs, application errors), natural disasters (earthquakes, floods), cyberattacks (denial-of-service attacks, ransomware), and even human error (accidental data deletion, misconfiguration) can all lead to disruptions. The effects can range from minor delays to complete system failures, resulting in lost revenue, damaged reputation, legal repercussions, and even loss of life in critical situations. For instance, a ransomware attack crippling a hospital’s system could directly impact patient care, potentially leading to serious health consequences.
Strategies for Ensuring High Data Availability
Building resilience into your systems is paramount. This involves implementing strategies that minimize downtime and ensure rapid recovery. Redundancy, failover mechanisms, and disaster recovery planning are key elements of a robust availability strategy. Redundancy involves creating backups and duplicate systems; failover mechanisms automatically switch to backup systems when primary systems fail; and disaster recovery planning ensures a structured approach to restoring operations after a major disruption. A well-defined plan accounts for all potential scenarios, including data backups, alternative work locations, and communication protocols.
Comparison of High Availability Approaches: Active-Active vs. Active-Passive
Two common approaches to achieving high availability are active-active and active-passive configurations. In an active-active configuration, multiple systems operate simultaneously, sharing the workload. If one system fails, the others seamlessly take over, ensuring continuous operation. This offers superior performance and redundancy but is more complex and expensive to implement. Active-passive configurations, on the other hand, involve one primary system handling the workload, with a backup system standing by. The backup system only takes over if the primary system fails. This is simpler and cheaper but may lead to a brief service interruption during the failover process.
Design of a Highly Available Cloud-Based System
Cloud computing offers inherent advantages for building highly available systems. Leveraging cloud services allows for easy scalability, redundancy, and disaster recovery capabilities.
- Multiple Availability Zones (AZs): Distributing resources across multiple AZs geographically separated ensures resilience against regional outages.
- Load Balancing: Distributing traffic across multiple instances prevents overload on any single server.
- Database Replication: Maintaining multiple copies of the database in different AZs ensures data availability even if one database instance fails.
- Automated Failover: Configuring automatic failover mechanisms ensures seamless transition to backup systems in case of failures.
- Regular Backups and Snapshots: Frequent backups and snapshots provide a safety net for data recovery in case of unexpected events.
- Monitoring and Alerting: Real-time monitoring and automated alerts enable proactive identification and resolution of potential issues.
Interrelationships within the CIA Triad
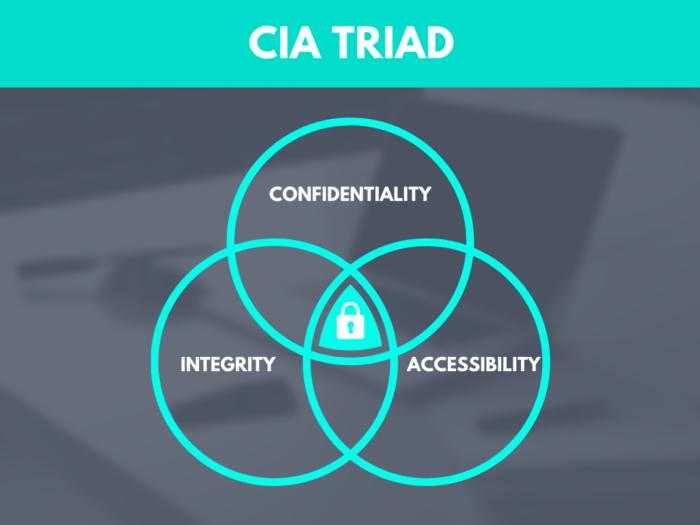
Source: saymedia-content.com
The CIA triad – Confidentiality, Integrity, and Availability – isn’t a set of independent pillars; they’re intricately interwoven. A compromise in one area almost always impacts the others, creating a domino effect that can severely jeopardize an organization’s security posture. Understanding these interdependencies is crucial for effective risk management.
A breach in one area often triggers a cascade of consequences affecting the others. For example, a data breach (confidentiality violation) can lead to data manipulation (integrity compromise) and subsequent system downtime while the damage is assessed and repaired (availability disruption). This interconnectedness highlights the need for a holistic security approach, rather than focusing on individual elements in isolation.
Real-World Example of CIA Interdependence
Consider a hospital’s electronic health record (EHR) system. A successful ransomware attack (availability breach) could encrypt patient data, rendering it inaccessible (availability). This immediately impacts the ability of medical staff to access critical patient information for diagnosis and treatment. Furthermore, if the attackers modify the data before encryption (integrity breach), the accuracy of patient records is compromised, potentially leading to misdiagnosis or incorrect treatment. The confidentiality of sensitive medical information is also violated as the attackers may exfiltrate the data, leading to further legal and reputational damage. This illustrates how a single attack can compromise all three aspects of the CIA triad simultaneously.
Challenges in Balancing the CIA Triad, Cia triad confidentiality integrity availability
Balancing confidentiality, integrity, and availability presents ongoing challenges. For instance, strong encryption (enhancing confidentiality and integrity) can significantly impact system performance and accessibility (reducing availability). Similarly, rigorous access controls (improving confidentiality and integrity) might inconvenience users and slow down workflows (affecting availability). Finding the optimal balance requires careful consideration of risk tolerance, operational needs, and regulatory compliance. The process often involves making difficult trade-offs between these competing priorities.
Strategies for Mitigating Risks Across the CIA Triad
Effective risk mitigation requires a multi-faceted approach that addresses the interconnectedness of the CIA triad. This includes implementing robust access control mechanisms, employing strong encryption techniques, maintaining regular backups, implementing intrusion detection and prevention systems, and conducting regular security audits and penetration testing. A comprehensive disaster recovery plan is also essential to ensure business continuity in the event of a security incident. Furthermore, employee training and awareness programs are crucial in preventing human error, a significant contributor to security breaches impacting all three elements of the triad.
Visual Representation of CIA Triad Interrelationships
Imagine a Venn diagram with three overlapping circles, each representing one element of the CIA triad: Confidentiality, Integrity, and Availability. The overlapping areas show the interconnectedness. For example, the area where Confidentiality and Integrity overlap represents the protection of data from unauthorized access and modification. The area where Integrity and Availability overlap shows that data must be accurate and accessible. The area where Confidentiality and Availability overlap represents ensuring that authorized users can access data securely. The central area where all three circles overlap represents the ideal state where all three aspects are simultaneously protected and balanced. Arrows could be drawn between the circles to illustrate how a breach in one area can impact the others. For instance, an arrow from the “Availability” circle could point to the “Confidentiality” and “Integrity” circles, indicating that a loss of availability can lead to compromises in the other two.
Implementing CIA Triad Controls: Cia Triad Confidentiality Integrity Availability
Protecting your digital assets requires a robust security strategy. The CIA triad – Confidentiality, Integrity, and Availability – provides a foundational framework, but its effectiveness hinges on proper implementation of security controls. This section details practical steps to safeguard your data and systems.
Access Control Lists (ACLs) and Confidentiality
Access Control Lists are fundamental to maintaining confidentiality. ACLs define which users or groups have permission to access specific resources, such as files, folders, or databases. By carefully crafting ACLs, organizations can restrict access to sensitive information to only authorized personnel. For example, a company might create an ACL for a database containing customer financial information, granting access only to employees in the finance and customer service departments, and restricting access based on specific roles and responsibilities (e.g., read-only access for customer service, full access for finance). Granular control, offered by many modern systems, allows for precise permission settings, preventing unauthorized disclosure of confidential data. Regular review and updates of ACLs are crucial to ensure they remain effective as personnel change and security needs evolve.
Intrusion Detection and Prevention Systems (IDPS) and Availability and Integrity
Intrusion Detection and Prevention Systems play a critical role in maintaining both availability and integrity. Intrusion Detection Systems (IDS) monitor network traffic and system activity for suspicious behavior, alerting administrators to potential threats. Intrusion Prevention Systems (IPS) go a step further, actively blocking malicious traffic and preventing attacks from succeeding. By identifying and mitigating attacks before they cause damage, IDPS helps ensure the continued availability of systems and data. Simultaneously, by preventing unauthorized modifications or deletions, IDPS safeguards data integrity. For example, an IPS could block a denial-of-service (DoS) attack, preserving system availability, and it could also prevent malware from infecting systems, maintaining data integrity. Effective IDPS implementation requires careful configuration, regular updates, and integration with other security tools.
Data Loss Prevention (DLP) Tools and Confidentiality and Integrity
Data Loss Prevention (DLP) tools actively monitor and prevent sensitive data from leaving the organization’s control. These tools can scan emails, files, and network traffic for confidential information, blocking or alerting administrators to potential data breaches. This protects confidentiality by preventing unauthorized disclosure. Additionally, DLP tools can help maintain data integrity by preventing unauthorized copying or modification of sensitive information. For example, a DLP system could prevent an employee from emailing a sensitive document to a personal email account or uploading it to an unauthorized cloud storage service. The system might also flag attempts to copy sensitive data to a USB drive. Proper configuration and regular updates are essential for effective DLP.
Example Security Policy Addressing the CIA Triad
A comprehensive security policy should explicitly address all three aspects of the CIA triad. Here’s an example:
- Confidentiality: Restrict access to sensitive data based on the principle of least privilege. Implement strong authentication and authorization mechanisms. Use encryption for data at rest and in transit. Regularly review and update access control lists.
- Integrity: Implement robust change management processes. Regularly back up data and systems. Use version control systems for important documents. Employ intrusion detection and prevention systems.
- Availability: Maintain redundant systems and data backups. Implement disaster recovery plans. Regularly test business continuity plans. Employ robust network infrastructure.
Examples of Security Audits to Verify CIA Triad Controls
Regular security audits are crucial to verify the effectiveness of implemented controls. Examples include:
- Vulnerability assessments: Identify weaknesses in systems and applications that could compromise the CIA triad.
- Penetration testing: Simulate real-world attacks to evaluate the effectiveness of security controls.
- Access control reviews: Verify that access controls are properly configured and enforced.
- Data loss prevention audits: Assess the effectiveness of DLP tools in preventing data breaches.
- Incident response reviews: Evaluate the organization’s ability to respond to and recover from security incidents.
Ending Remarks
So, there you have it – the CIA Triad demystified. Understanding confidentiality, integrity, and availability isn’t just about ticking boxes; it’s about building a robust, resilient system that protects your valuable data. From encryption algorithms to disaster recovery plans, securing your digital world requires a multi-faceted approach. By mastering the CIA Triad, you’re not just protecting data; you’re safeguarding your future. Now go forth and build that impenetrable digital fortress!





