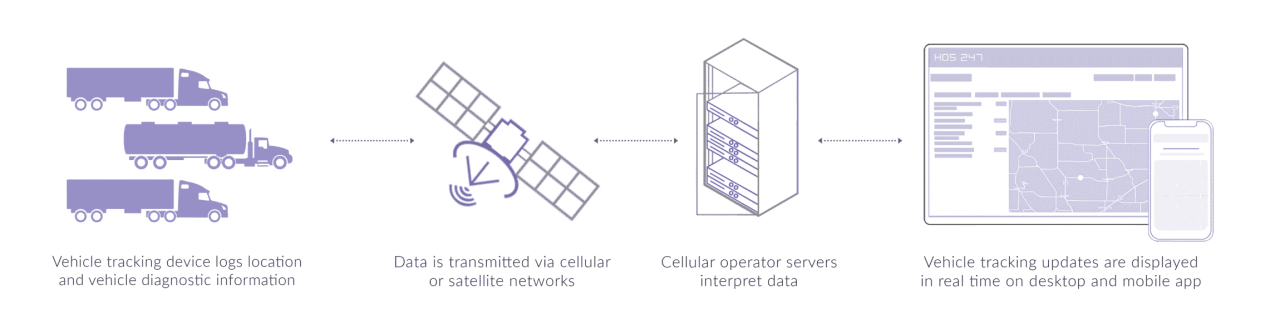
Fleet management vehicle tracking system sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail with product advertising style and brimming with originality from the outset.
This innovative system transforms how businesses manage their fleets, providing real-time tracking, enhanced productivity, and cost-efficiency. By leveraging cutting-edge technology, companies can monitor vehicle locations, optimize routes, and ensure safety, making the fleet management process simpler and more effective than ever.
Are you on the lookout for a handbag that not only complements your style but also embodies sophistication and durability? Look no further! Our Premium Leather Handbags are here to redefine your accessory game, merging functionality with high fashion. Each piece is meticulously crafted from the finest leather, promising a luxurious touch that is sure to turn heads wherever you go.
Unparalleled Quality
When it comes to handbags, quality is non-negotiable. Our Premium Leather Handbags are made using 100% genuine leather sourced from the most reputable suppliers. This means you can trust that your bag will last for years to come, standing the test of time while maintaining its stunning appearance. With a robust construction, these bags resist wear and tear, ensuring you can take them on all your adventures without worry.
Handcrafted to Perfection
Every handbag is handcrafted by skilled artisans who pour their heart into every stitch and detail. Our commitment to artisanal craftsmanship means that your bag won’t just be another accessory but a unique piece of art that showcases individual flair. The attention to detail is evident in our smooth seams, impeccable finishing, and thoughtful designs that cater to the modern woman.
Stylish Designs for Every Occasion
Our collection features a myriad of designs, colors, and sizes, ensuring there’s a perfect handbag for every occasion. Whether you’re heading to the office, a night out, or a casual day out shopping, we have you covered:
- Chic Tote Bags: Spacious and stylish, ideal for work or play. Carry your essentials with ease!
- Elegant Clutches: Perfect for formal events or a night on the town. Minimalist yet luxurious.
- Versatile Crossbody Bags: Hands-free convenience without compromising on style. Perfect for travelers!
- Classic Satchels: A timeless design that blends sophistication with functionality.
Color Palette That Speaks to You
Our handbags are available in a wide range of colors, including classic neutrals like black and brown, as well as vibrant hues like red and teal. Each color is carefully selected to enhance your wardrobe, allowing you to express your personality through your accessories. Whether you prefer a bold statement piece or a subtle classic, we have the right shade to suit your style.
Functionality Meets Fashion
We understand that a handbag must do more than just look good. Our Premium Leather Handbags are designed with practicality in mind. With numerous pockets and compartments, you can easily organize your belongings. From your smartphone to your wallet, everything has its place. The sturdy straps provide comfort while ensuring your bag stays securely in hand or on your shoulder.
Safety First
Your security is our priority! That’s why many of our handbags come equipped with zippers and magnetic closures that keep your belongings safe. No more worrying about pickpockets or losing your essentials when you’re out and about. Enjoy your day with peace of mind, knowing that your valuables are securely stored.
Eco-Friendly Practices
As a brand that values sustainability, we are proud to utilize eco-friendly practices in our production process. From sourcing materials responsibly to minimizing waste, we strive to make a positive impact on the environment. By choosing our Premium Leather Handbags, you’re not just investing in a high-quality accessory; you’re also supporting ethical fashion.
Customer Testimonials
Don’t just take our word for it! Here’s what our satisfied customers have to say:
“I love my new handbag! The quality is unmatched, and it goes with everything. I’ve received so many compliments!” – Sarah T.
“Finally, a bag that is both stylish and practical. I can fit everything I need without sacrificing my look!” – Jessica L.
“The craftsmanship is incredible! I can tell this bag will last me a lifetime. Totally worth every penny!” – Olivia M.
Affordable Luxury
Luxury doesn’t have to come with a hefty price tag. Our Premium Leather Handbags are priced competitively to ensure you get the best value for your investment. We believe that everyone deserves to own a beautiful handbag that they can cherish for years. Experience the luxury without the guilt!
Exclusive Offer Just For You!
To celebrate our commitment to quality and style, we are excited to offer a special promotion just for you! For a limited time only, enjoy 20% off your first purchase when you sign up for our newsletter. Don’t miss out on this exclusive opportunity to elevate your accessory game with our Premium Leather Handbags!
Easy Returns and Customer Support
Your satisfaction is our top priority! If for any reason you’re not completely happy with your purchase, we offer hassle-free returns within 30 days. Our dedicated customer support team is also here to assist you with any inquiries or concerns you may have, ensuring your shopping experience is as seamless as possible.
Join Our Community
Stay connected with us and be the first to know about new arrivals, exclusive deals, and style tips by following us on our social media platforms. Join our community of fashion lovers and share your unique style with the world! Use the hashtag #MyPremiumHandbag to showcase how you incorporate our handbags into your daily life!
Final Thoughts: Make the Right Choice
In a world filled with countless handbag options, make the smart choice by investing in a Premium Leather Handbag. Experience the perfect blend of elegance, quality, and functionality—all while staying true to your unique style. Don’t wait any longer; elevate your accessory collection today and step out in confidence, knowing you own a handbag that is as exceptional as you are.
Visit our website to explore the full collection and transform your look with one of our stunning Premium Leather Handbags. Experience luxury like never before!
Frequently Asked Questions
What is a fleet management vehicle tracking system?
It is a technology that allows businesses to monitor the real-time location and status of their vehicles, enhancing operational efficiency.
How does vehicle tracking improve safety?
By providing real-time data on vehicle behavior and location, it helps in identifying unsafe driving habits and responding quickly to emergencies.
Can fleet tracking systems be integrated with other software?

Yes, most fleet tracking systems can be integrated with existing business software for improved data analysis and reporting.
What are the cost benefits of using a tracking system?

These systems help reduce fuel costs, optimize routes, and decrease maintenance expenses, leading to significant savings over time.
Is it possible to track my vehicles globally?
Yes, many modern fleet management systems offer global tracking capabilities through satellite technology.