Discover the revolutionary fleet management dash cam that elevates vehicle safety and enhances operational efficiency. In a world where every second counts, ensuring the safety of your fleet has never been more crucial. This state-of-the-art technology not only captures real-time footage but also provides insights that can transform your fleet management practices.
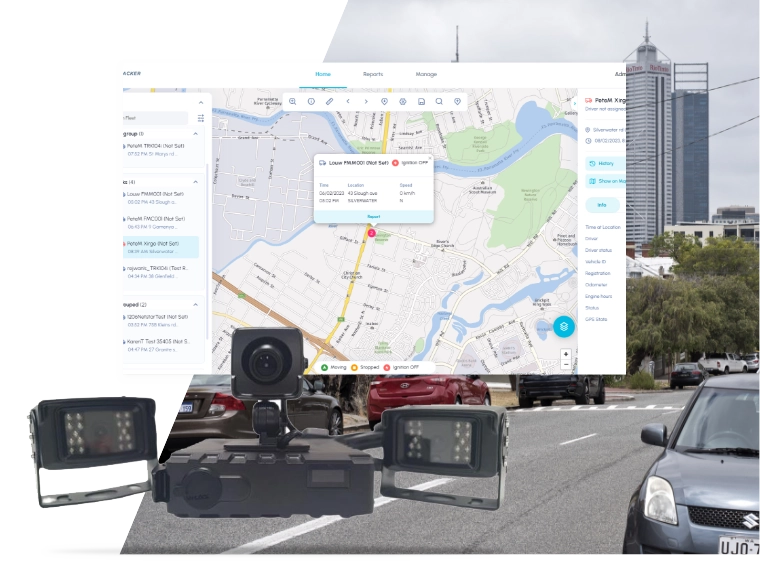
With advanced features such as GPS tracking, collision detection, and 24/7 cloud storage, fleet management dash cams empower businesses to monitor driver behavior, reduce accidents, and optimize routes. This innovative solution is designed to help fleet operators make informed decisions, ensuring the safety of both their drivers and the public.
Are you tired of spending your weekends scrubbing floors and dusting shelves? Do you wish there was a way to make your home cleaning routine faster, easier, and more efficient? Say goodbye to tedious cleaning chores and hello to the revolutionary UltraClean 3000! This incredible device is about to change the way you think about cleaning forever.
Why Choose UltraClean 3000?
Imagine a world where cleaning is as simple as pressing a button. The UltraClean 3000 is designed with cutting-edge technology that takes the hassle out of cleaning. With its powerful suction capabilities, intelligent navigation system, and advanced filtration, this cleaning marvel ensures every corner of your home is spotless. Here’s why the UltraClean 3000 should be your next cleaning companion:
- Powerful Performance: Equipped with a 3000Pa suction power, the UltraClean 3000 tackles dirt, pet hair, and allergens with ease. It pulls in everything from fine dust to large debris, leaving your floors immaculately clean.
- Smart Navigation: No more missed spots! The UltraClean 3000 uses intelligent mapping technology to navigate your home efficiently. It creates a virtual map of your space, ensuring every inch is covered without unnecessary repetition.
- Quiet Operation: Cleaning shouldn’t be disruptive. The UltraClean 3000 operates at a whisper-quiet level, allowing you to continue your daily activities while it works its magic.
- Multi-Surface Capability: Whether you have hardwood floors, carpet, or tiles, the UltraClean 3000 adapts to any surface, ensuring a thorough clean every time.
- Long Battery Life: Don’t worry about interruptions! With a powerful battery that lasts up to 120 minutes, the UltraClean 3000 can clean large areas on a single charge.
Features That Set UltraClean 3000 Apart
The UltraClean 3000 is packed with features that make it the ultimate cleaning solution. Here are some of the standout benefits you can enjoy:
1. Advanced Filtration System
Allergies? Not anymore! The UltraClean 3000 comes with a HEPA filtration system that captures 99.97% of dust, pollen, and other allergens, ensuring the air in your home is as clean as your floors.
2. Remote Control & Smart App
Take control of your cleaning with the dedicated app! Schedule cleanings, set cleaning modes, and monitor your UltraClean 3000’s performance, all from your smartphone. Plus, you can use voice commands with Alexa or Google Assistant for hands-free operation.
3. Obstacle Detection
Worried about your furniture or delicate items? The UltraClean 3000 is equipped with advanced sensors that detect obstacles in its path, so it seamlessly navigates around furniture and avoids falls, giving you peace of mind.
4. Easy Maintenance
No one likes complicated cleanup processes. The UltraClean 3000 features a self-cleaning brush roll and a dustbin that’s easy to empty. Spend less time maintaining your cleaner and more time enjoying your clean home!
How to Use UltraClean 3000
Using the UltraClean 3000 is as easy as 1-2-3!
- Charge the Device: Ensure your UltraClean 3000 is fully charged before the first use. Simply plug in the charging dock and let it power up!
- Set Your Preferences: Use the app or remote to select your preferred cleaning mode. Choose from options like “Spot Clean,” “Edge Clean,” or “Scheduled Clean.”
- Press Start! Hit the start button and watch as the UltraClean 3000 goes to work, leaving you with more free time to relax or spend with family!
Real Customer Testimonials
Don’t just take our word for it! Here’s what satisfied customers are saying about the UltraClean 3000:
“The UltraClean 3000 has made my life so much easier! I love how it navigates my home and gets into all the nooks and crannies. I can finally enjoy my weekends without worrying about cleaning!”
-Sarah M.
“As a pet owner, I struggled with pet hair everywhere. The UltraClean 3000 picks up every last strand! My home has never been cleaner.”
-Jason R.
Order Your UltraClean 3000 Today!
Are you ready to revolutionize your cleaning routine? Order the UltraClean 3000 today and experience the future of home cleaning! For a limited time, when you purchase the UltraClean 3000, you’ll receive a FREE extra filter to keep your device running at peak performance. Don’t miss out on this incredible offer!
Special Offer: 20% Off for First-Time Buyers!
Use the promo code ULTRACLEAN20 at checkout to enjoy 20% off your first purchase. This is the perfect opportunity to elevate your home cleaning experience!
Frequently Asked Questions
1. How long does the battery last?
The UltraClean 3000 has a powerful battery that lasts up to 120 minutes, depending on the cleaning mode and surface type.
2. Can it clean on carpets?
Absolutely! The UltraClean 3000 is designed to work on all floor types, including carpets, tiles, and hardwood floors.
3. Is it easy to maintain?
Yes! The UltraClean 3000 features a self-cleaning brush roll and an easy-to-empty dustbin for hassle-free maintenance.
4. What if it gets stuck?
The device is equipped with advanced obstacle detection sensors, so it will navigate around furniture and avoid getting stuck. In case it does encounter an issue, the app will alert you.
Join the Cleaning Revolution!
Don’t let cleaning take over your life! With the UltraClean 3000, you can enjoy a spotless home without the stress and time commitment. Embrace the future of home cleaning and make your life easier today. Order now and take the first step towards a cleaner, healthier home!
For more information, visit our website or contact our customer service team. We’re here to help you make the best choice for your home cleaning needs. Get ready to enhance your cleaning game with the UltraClean 3000 – your ultimate cleaning partner!
FAQ Resource
What is a fleet management dash cam?
A fleet management dash cam is a camera system installed in vehicles to record driving conditions, monitor driver behavior, and provide real-time footage for safety and analysis.
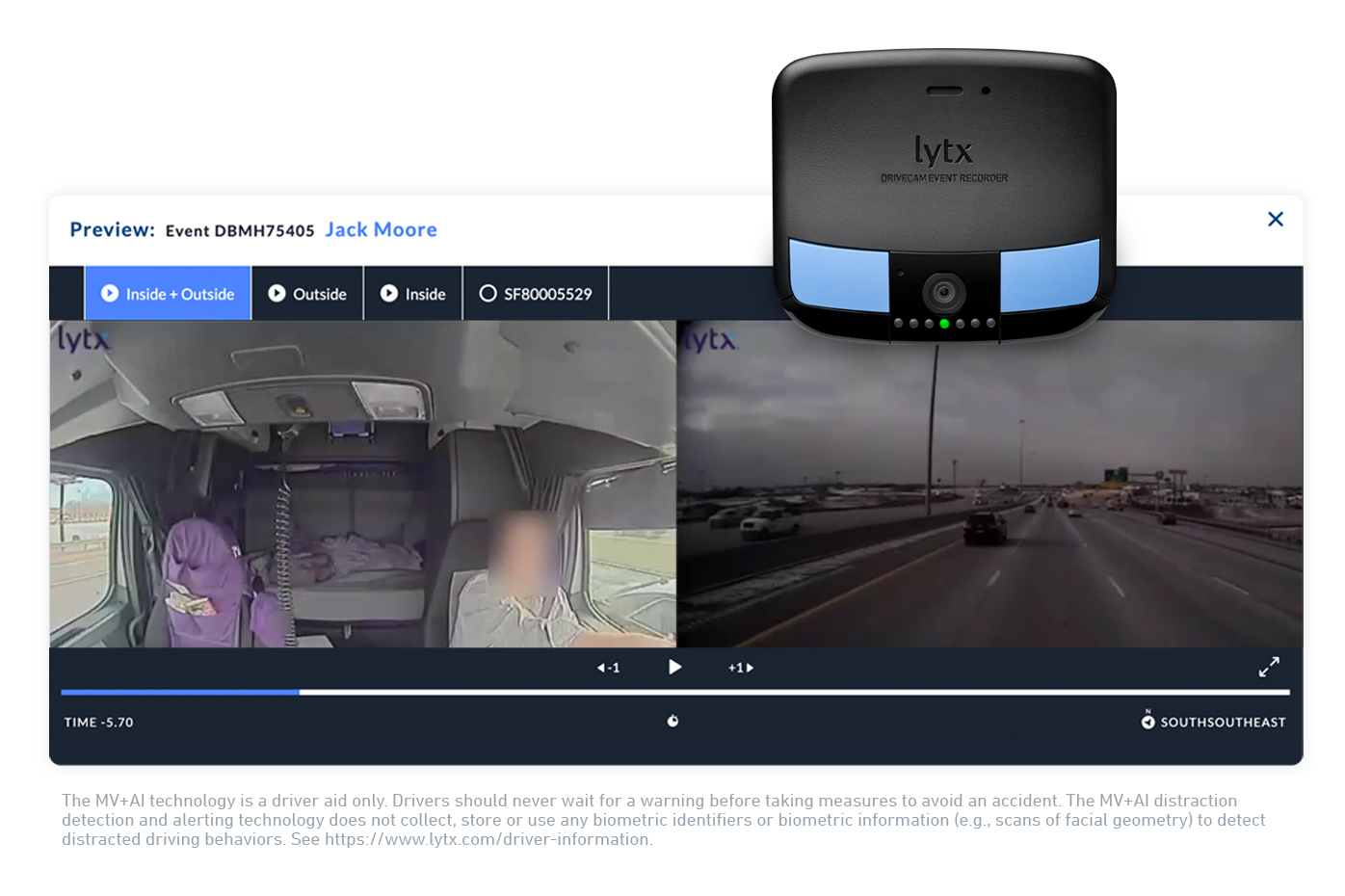
How can a dash cam improve fleet safety?
By capturing incidents and providing evidence, dash cams help identify unsafe driving habits, leading to better training and reduced accidents.
Is cloud storage available for dash cam footage?
Yes, many dash cam systems offer cloud storage options for easy access and management of video footage from anywhere.
Can dash cams help with insurance claims?
Absolutely! Dash cam footage can serve as crucial evidence in the event of an accident, speeding up the claims process and possibly lowering premiums.
What features should I look for in a dash cam?

Look for features such as HD video recording, GPS tracking, night vision, collision alerts, and cloud connectivity for optimal performance.