Gootloader Targets Bengal Cat Lovers: Who knew your love for fluffy, spotted felines could land you in a digital dumpster fire? Turns out, cybercriminals are using your passion for Bengal cats as bait in sophisticated phishing schemes. Think adorable kitten pics hiding malware, or seemingly harmless forum posts leading to data breaches. We’re diving deep into how Gootloader is exploiting this niche community, and what you can do to protect yourself and your precious purring pals.
This isn’t your average malware attack. Gootloader isn’t just targeting random users; it’s specifically honing in on Bengal cat enthusiasts, using their online communities and shared interests as attack vectors. From malicious attachments disguised as adorable kitten videos to fake breeder websites, the criminals are getting creative. We’ll explore the various methods used, the potential damage, and, most importantly, how to stay safe in the digital jungle.
Gootloader Infection Vectors Targeting Cat Lovers
Source: thecyberexpress.com
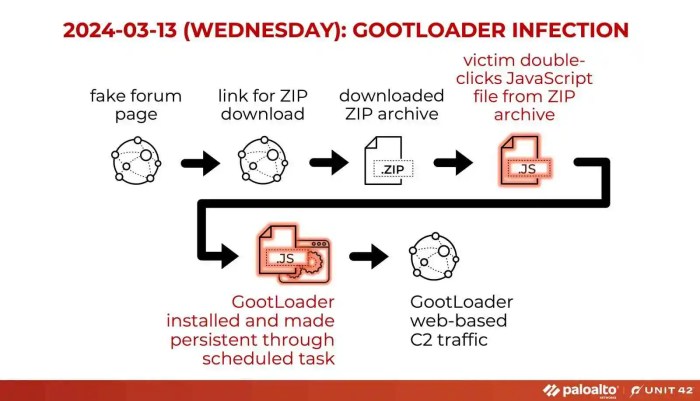
Gootloader, a notorious information-stealing malware, doesn’t discriminate. However, its spread often leverages the passions and online communities of its targets. Bengal cat enthusiasts, with their active online presence, represent a particularly vulnerable group. This analysis explores how Gootloader’s infection vectors specifically target this community.
Gootloader’s infection primarily relies on social engineering, exploiting users’ trust and curiosity. The malware’s creators cleverly disguise malicious files and links within content appealing to Bengal cat lovers, increasing the likelihood of unsuspecting clicks and downloads. This strategy is particularly effective because cat enthusiasts frequently share and download files, such as images, videos, and documents, related to their beloved felines.
Malicious Content Disguised as Cat-Related Material
Cybercriminals craft malicious attachments and links designed to mimic legitimate cat-related content. These deceptive tactics exploit the enthusiasm of Bengal cat owners, prompting them to open infected files or click malicious links without suspicion. For example, an email with the subject line “Adorable Bengal Kitten Videos!” might contain a link to a seemingly harmless video file, actually harboring Gootloader. Similarly, a document titled “Bengal Cat Breed Standards.pdf” could contain embedded malicious macros that trigger the malware’s installation upon opening. Other examples include images with seemingly innocuous names like “Bengal_Kitten_Playing.jpg” or “New_Bengal_Litter.zip,” concealing malicious code within their file structure.
Gootloader Infection Vectors Targeting Bengal Cat Enthusiasts, Gootloader targets bengal cat lovers
The following table details potential attack vectors, their methods, likelihood of success, and mitigation strategies. Likelihood is assessed based on the prevalence of the vector and the susceptibility of the target audience.
| Vector | Method | Likelihood of Success | Mitigation |
|---|---|---|---|
| Online Forums (e.g., Reddit, Facebook Groups) | Malicious links disguised as links to cat photos, videos, or articles; compromised forum posts with infected attachments. | High | Avoid clicking on suspicious links; verify the sender’s identity; scan downloaded files with antivirus software. |
| Social Media Groups (e.g., Facebook, Instagram) | Shared infected images or videos; malicious advertisements or sponsored posts; private messages containing infected links. | Medium-High | Be wary of unsolicited messages and links; verify the source of shared content; use strong passwords and enable two-factor authentication. |
| Websites Dedicated to Bengal Cats | Compromised websites hosting infected downloads; drive-by downloads via malicious ads. | Medium | Only visit reputable websites; use ad blockers; keep your browser and operating system up-to-date. |
| Phishing emails with malicious attachments (e.g., “Your Bengal Cat’s Health Report.pdf”) or links to infected websites. | High | Be cautious of unsolicited emails; verify the sender’s identity; avoid opening attachments from unknown senders; use a spam filter. |
Malware Payload and Bengal Cat-Themed Lures
Gootloader, a notorious malware, isn’t just a digital menace; it’s a chameleon, adapting its tactics to exploit the passions of its targets. Knowing that Bengal cat lovers often frequent online forums, breed-specific websites, and social media groups, cybercriminals can craft highly targeted attacks. This means the malware’s payload and the lures used to deliver it are specifically designed to appeal to this niche community.
The payload itself might be tailored to steal specific data valuable to Bengal cat owners. This could include financial information from online pet supply stores or veterinary clinics, personal details used for identity theft, or even sensitive information related to breeding programs or pedigree registration. The more personal the data, the higher the value for cybercriminals on the dark web. This targeted approach increases the likelihood of successful infection and data exfiltration.
Hypothetical Phishing Email: Bengal Cat Theme
Imagine receiving an email with the subject line: “Urgent! Your Bengal Kitten Needs This!” The email body might contain a seemingly urgent message about a recall of a specific cat food brand popular among Bengal owners, or a special offer on a limited-edition Bengal cat toy. Attached might be a seemingly innocuous image of an adorable Bengal kitten, or a document file containing a “certificate of authenticity” for a supposed breed registry. Clicking on this attachment or link would trigger the Gootloader infection. The email would be crafted to appear legitimate, possibly even mimicking the branding of a well-known pet supply company or veterinary practice. The urgency and emotional appeal are key elements in convincing the recipient to bypass their usual caution.
Malware Disguise Techniques
Gootloader, like other sophisticated malware, employs various techniques to evade detection. It might disguise its activity by mimicking legitimate system processes, making it difficult for antivirus software to identify it as malicious. For example, the malware could use a process name similar to a common Windows system service, or encrypt its communication channels to avoid detection by network security tools. It might also leverage legitimate software components to perform malicious actions, blending in with the background noise of a typical computer’s activity. Another strategy involves modifying system logs to hide its tracks and make forensic analysis more challenging. The sophistication of these techniques underlines the importance of robust security measures and regular system updates.
Impact on Bengal Cat Community
The recent Gootloader malware campaign, cleverly disguised as content appealing to Bengal cat enthusiasts, poses a significant threat to this passionate community. While the primary target is personal data and financial information, the secondary impact on Bengal cat owners and breeders could be substantial, ranging from stolen sensitive information to disrupted online interactions and compromised breeding programs. Understanding these potential consequences is crucial for safeguarding both personal security and the integrity of the online Bengal cat community.
The infiltration of malware into the online spaces frequented by Bengal cat lovers can have far-reaching effects. This isn’t just about losing personal data; it’s about the potential disruption of vital community resources, the dissemination of misinformation, and the erosion of trust within the breeding and adoption networks. The highly specialized nature of Bengal cat care and breeding makes the community particularly vulnerable to targeted attacks.
Potential Vulnerabilities in Online Bengal Cat Communities
Online forums, social media groups, and dedicated websites for Bengal cat enthusiasts are often vibrant hubs of information sharing and community building. However, these platforms also present unique vulnerabilities to cyberattacks. The inherent trust within these communities, combined with the often-unregulated nature of online forums, makes them prime targets for malicious actors seeking to exploit vulnerabilities. For example, a seemingly harmless link to a cute kitten video could actually be a vector for malware, infecting devices and granting access to sensitive personal information. Furthermore, the sharing of private breeder information or sensitive health records within these online spaces could lead to identity theft or the exploitation of valuable breeding lines.
Best Practices for Protecting Against Online Threats
Protecting yourself and your valuable data within the Bengal cat online community requires proactive measures. Here are some essential best practices to consider:
- Practice caution when clicking links: Always verify the source and legitimacy of links before clicking, especially those shared in forums or social media groups. Avoid clicking links from unknown or untrusted sources.
- Use strong and unique passwords: Employ strong, unique passwords for all online accounts related to Bengal cats, including forums, breeders’ websites, and online stores. Consider using a password manager to help you create and manage these passwords securely.
- Keep software updated: Regularly update your operating system, antivirus software, and web browser to patch security vulnerabilities and protect against the latest threats. This is a crucial first line of defense against malware like Gootloader.
- Be wary of phishing attempts: Be cautious of emails, messages, or posts that request personal information, login credentials, or financial details. Legitimate organizations rarely request such information through unsolicited communication.
- Enable two-factor authentication: Whenever possible, enable two-factor authentication (2FA) on all your online accounts. This adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access.
- Educate yourself about online safety: Stay informed about the latest online threats and scams. Regularly review online security best practices and be aware of the tactics used by cybercriminals.
Mitigation Strategies and Prevention
Protecting yourself from Gootloader, especially when your online activities involve your love for Bengal cats, requires a multi-layered approach. This isn’t just about avoiding suspicious emails; it’s about cultivating safe online habits and utilizing robust security tools. Think of it as safeguarding your digital domain, just as you’d protect your beloved feline friend.
The key is proactive defense. Don’t wait for an infection; actively prevent it. This involves careful navigation of the web, especially in forums, social media groups, or websites dedicated to Bengal cats, where malicious actors might lurk. Remember, those adorable kitten pictures might be hiding a nasty surprise.
Preventing Gootloader Infections
Preventing Gootloader infection hinges on a combination of cautious online behavior and strong security software. Avoid clicking on links or downloading attachments from unknown or untrusted sources, even if they seem related to your Bengal cat obsession. Be extra wary of emails promising free Bengal cat-related resources or those containing urgent, emotionally charged messages designed to trigger impulsive clicks. Regularly update your operating system and software, as updates often patch security vulnerabilities that Gootloader exploits. Enable strong, unique passwords for all your online accounts, and consider using a password manager to help you manage them effectively. Finally, be mindful of the websites you visit and the files you download. Stick to reputable sources and always verify the authenticity of any links before clicking.
Comparison of Security Software Solutions
Several security software solutions offer varying degrees of protection against Gootloader. The effectiveness depends on the specific features and the sophistication of the malware’s evasion techniques. Choosing the right software is crucial.
The following table compares some popular options. Note that effectiveness can fluctuate as both malware and security software evolve. This data is based on industry reports and user reviews, and should be considered a general guideline.
| Software Name | Features | Effectiveness Against Gootloader | Cost |
|---|---|---|---|
| Malwarebytes | Real-time protection, malware scanning, ransomware protection, website protection | Generally high; detects and removes Gootloader effectively in most cases | Paid subscription available; free version with limited features |
| Bitdefender | Real-time protection, advanced threat detection, anti-phishing, vulnerability scanner | High; strong detection and removal capabilities | Paid subscription available; free version with limited features |
| Norton 360 | Real-time protection, firewall, VPN, password manager, identity theft protection | High; robust protection against various malware threats, including Gootloader | Paid subscription; various plans available |
| Kaspersky | Real-time protection, machine learning-based threat detection, anti-phishing, secure browser | High; consistently ranks well in independent malware tests | Paid subscription; various plans available |
Identifying and Removing Gootloader
If you suspect a Gootloader infection, immediate action is vital. First, disconnect from the internet to prevent further damage. Then, run a full system scan using your security software. If the infection persists, consider booting your computer into safe mode to disable potentially malicious processes. This allows you to run your security software more effectively. If your security software fails to remove the malware, consider seeking professional help from a cybersecurity expert. They possess the specialized tools and knowledge to thoroughly eliminate Gootloader and restore your system’s security. Remember to back up your important data regularly to minimize data loss in case of an infection. Regular backups are crucial in mitigating the impact of malware.
Illustrative Examples

Source: cyberriskalliance.com
Let’s paint a picture of how a seemingly innocent online activity can lead to a nasty Gootloader infection for a devoted Bengal cat enthusiast. We’ll explore a realistic scenario, detailing the lure, the fake website, and the malicious code’s insidious actions.
Imagine Sarah, a passionate Bengal cat breeder, searching online for high-quality cat food. She stumbles upon an advertisement on a popular cat forum, boasting “Premium Bengal Cat Food – Unbeatable Prices!” The ad features an adorable Bengal kitten, its striking coat glistening. Clicking the link seems harmless enough – who could resist such a cute feline face?
A Deceptive Website Mimicking a Legitimate Breeder
The advertisement leads Sarah to a website that expertly mimics a legitimate Bengal cat breeder’s site. The site’s design is meticulously crafted to appear authentic. The layout is clean and professional, with high-resolution images of various Bengal cats, showcasing their unique markings and playful personalities. The color scheme is soothing, using calming earth tones and shades of brown, reminiscent of a Bengal cat’s coat. Text on the site uses professional font styles and is well-organized, providing seemingly detailed information about the breeder’s cats, their lineage, and their care. A prominent section highlights “exclusive offers” on cat food, subtly urging visitors to download a seemingly harmless “nutrition guide” in PDF format. This PDF is actually the Gootloader payload, cleverly disguised.
Technical Aspects of the Malicious Code
The “nutrition guide” PDF is not a simple document. It’s a cleverly crafted Trojan, containing malicious code designed to exploit vulnerabilities in Sarah’s operating system. Once downloaded, the code silently installs itself, establishing a persistent presence on her computer. It then connects to a remote command-and-control server, allowing the attackers to remotely control her system. The malware could steal her personal information, including banking details and passwords, monitor her online activity, and even use her computer to participate in larger botnets for illicit activities. The Gootloader’s behavior is stealthy; it avoids detection by antivirus software by using obfuscation techniques and constantly changing its signature. It subtly interacts with the operating system, using legitimate processes to mask its malicious activities. This ensures the infection remains undetected for an extended period, allowing the attackers to carry out their malicious operations. The infection could also lead to data loss, system instability, and significant financial losses for Sarah.
Concluding Remarks: Gootloader Targets Bengal Cat Lovers
Source: izoologic.com
So, are you ready to outsmart the digital predators lurking in your favorite Bengal cat forums? Understanding how Gootloader leverages your passion for these beautiful creatures is the first step. By staying vigilant, practicing safe online habits, and using robust security software, you can keep your personal information—and your love for Bengal cats—safe from harm. Remember, a little caution can go a long way in keeping your digital life (and your feline friends) purrfectly secure.





