Hackers employ zip file concatenation—a sneaky technique where malicious code hides within seemingly innocent zipped files. Think of it as a digital Trojan horse, cleverly disguised to bypass your defenses. This isn’t your grandma’s zip file; we’re talking about a sophisticated attack vector that’s surprisingly effective. Get ready to dive into the dark art of zip file manipulation and learn how to protect yourself.
This insidious method involves chaining multiple zip files together, often embedding malware within seemingly harmless data. The attacker might append a malicious zip file to a legitimate one, creating a larger archive that looks normal at first glance. This allows them to bypass security checks that only examine the initial portion of a file. We’ll explore how this works technically, the types of malware used, and the strategies hackers employ to remain undetected.
Understanding Zip File Concatenation: Hackers Employ Zip File Concatenation
Source: cybereason.com
Zip file concatenation, while seemingly simple, offers a surprising level of complexity and potential for misuse. It involves combining multiple zip archives into a single file, a process that can be both helpful and hazardous depending on the intent. Understanding the mechanics and implications of this technique is crucial, especially in the context of cybersecurity.
Zip file concatenation isn’t a standardized operation; it’s more of a workaround. The core process involves treating zip files as simple binary data streams and appending one to the end of another. This doesn’t magically merge the contents of the original archives; instead, it creates a single file containing the concatenated raw data of multiple zip files. The resulting file will likely be corrupt and unreadable by standard zip utilities unless specific steps are taken to ensure the integrity of the resulting file.
Appending versus Creating New Archives
Appending to an existing zip file is generally considered unreliable and often results in a broken archive. The zip file format has a specific structure, including a central directory that lists all the files and their offsets within the archive. Simply appending another zip file to the end disrupts this structure, making it impossible for standard tools to extract the contents correctly. Creating a new zip archive from multiple files, on the other hand, involves proper handling of the central directory. Each file is added individually, with its location and size accurately recorded in the central directory. This ensures that the resulting archive is valid and can be extracted without issue. Think of it like building a house – appending is like stacking bricks haphazardly, while creating a new archive is like building it brick by brick according to a blueprint.
Tools and Techniques
Several command-line tools and scripting languages can perform zip file concatenation, although the reliability and outcome vary greatly. For example, using the `cat` command in Linux/macOS can directly concatenate zip files, but the result will almost always be a corrupted archive. Specialized tools might offer more sophisticated approaches, but even these may not guarantee a valid outcome if appending to an existing archive. Scripting languages like Python, with libraries like `zipfile`, provide more control and allow for creating new zip archives from multiple files, ensuring a valid and extractable result. The key difference lies in the approach: simple concatenation versus proper archive creation.
Malicious Use of Zip File Concatenation
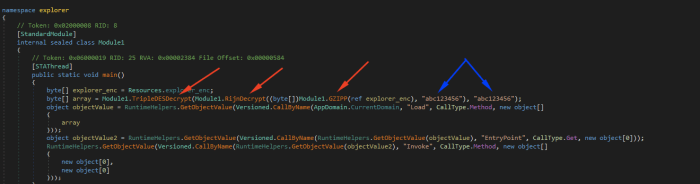
Imagine a scenario where a malicious actor creates a seemingly harmless zip file containing a legitimate program. They then concatenate a second zip file, containing malware, to the end of the first. A user, expecting to download and run the legitimate program, unwittingly downloads the concatenated file. Standard antivirus software might only scan the initial, legitimate portion of the file, missing the malicious payload hidden at the end. The attacker could even use steganography to hide the malware within the legitimate file’s data, making detection even more difficult. This demonstrates how zip file concatenation can be used to bypass security measures and deliver malicious code. The seemingly benign first file acts as a Trojan horse, delivering the malicious content concealed within the concatenated archive.
Malicious Use Cases
Zip file concatenation, while a seemingly benign process, becomes a potent weapon in the hands of malicious actors. Hackers leverage this technique to obfuscate malware, bypass security software, and deliver payloads undetected, making it a significant threat in the cybersecurity landscape. Understanding how this method is weaponized is crucial for effective defense.
The core malicious use of zip file concatenation lies in its ability to hide malicious code within seemingly innocuous files. A hacker might append a malicious executable to a legitimate zip archive, creating a larger, seemingly normal file. Antivirus software, scanning the initial, benign portion of the zip file, might miss the malicious payload hidden at the end. This allows the malware to execute successfully once the concatenated zip is extracted.
Malware Delivery via Concatenated Zip Files
This technique allows for the delivery of various types of malware, ranging from simple viruses to sophisticated ransomware. For instance, a hacker could create a zip file containing a seemingly harmless image or document, then append a malicious script or executable to the end. When the victim extracts the file, the malicious component executes, potentially installing ransomware, stealing data, or creating a backdoor for further attacks. Imagine a seemingly innocent vacation photo zip file; within its depths, a keylogger silently records every keystroke. The user, trusting the file’s initial appearance, unwittingly activates the hidden threat. Another example would be a seemingly legitimate software update zip file, concatenated with a rootkit that silently installs itself on the victim’s system.
Circumventing Security Measures
Zip file concatenation effectively circumvents traditional antivirus and security measures that rely on signature-based detection. Since the malicious code is hidden within a larger, seemingly legitimate file, the initial scan might not detect the threat. Furthermore, this technique can be combined with other obfuscation methods to further complicate detection and analysis. For example, the malicious payload might be compressed or encrypted, making it even harder for security software to identify. This allows the malware to remain undetected until it’s too late.
Comparison with Other Malware Delivery Methods, Hackers employ zip file concatenation
Compared to other methods like email attachments or malicious websites, zip file concatenation offers a degree of stealth. While email attachments are easily identifiable as potential threats, concatenated zip files can blend seamlessly into legitimate file transfers. This method is less easily detected than phishing emails, which often contain obvious red flags. Unlike drive-by downloads, which rely on vulnerabilities in web browsers, concatenated zip files can be delivered through various channels, increasing the attack surface. While equally dangerous, the method provides a different attack vector and bypasses certain security measures more effectively than some other techniques.
Detection and Prevention

Source: vishalon.net
Concatenated zip files, while seemingly innocuous, can harbor serious threats. Detecting these cleverly disguised attacks requires a multi-pronged approach, combining automated tools with careful manual inspection. Prevention, on the other hand, relies on a robust security posture and user awareness. Let’s delve into the specifics.
Methods for Detecting Concatenated Zip Files Containing Malicious Code
Identifying malicious zip file concatenation requires a combination of techniques. Signature-based antivirus software can sometimes detect known malicious files within the concatenated archive, but this is not always reliable, as sophisticated malware often evades detection through obfuscation or polymorphism. Heuristic analysis, which examines file behavior rather than just signatures, can be more effective in identifying suspicious activities after extraction. Additionally, examining the zip file’s metadata for inconsistencies, such as unusually large file sizes or unexpected file types within the archive, can raise red flags. Finally, sandboxing the extracted files in a controlled environment allows for safe observation of their behavior before exposing your system to potential harm.
Strategies for Preventing Malicious Zip File Concatenation Attacks
Preventing attacks hinges on proactive measures. Employing strong anti-virus software with regularly updated definitions is crucial. This provides a first line of defense against known threats. Beyond antivirus, implementing strict file access controls and regularly backing up important data are critical. This limits the damage potential even if an attack is successful. Furthermore, user education is key; employees should be trained to avoid downloading files from untrusted sources and to exercise caution when opening attachments. Regular security audits and penetration testing can identify vulnerabilities in your systems that could be exploited.
Antivirus Software Effectiveness Comparison
The effectiveness of antivirus software against concatenated zip file attacks varies significantly. There is no single perfect solution, and results depend on the sophistication of the malware and the specific antivirus engine used. The following table offers a generalized comparison; actual performance may differ based on various factors, including the version of the software and the specific malware sample.
| Software | Detection Rate | False Positives | Performance |
|---|---|---|---|
| Antivirus A | 85% | Low | Good |
| Antivirus B | 92% | Medium | Excellent |
| Antivirus C | 78% | Low | Average |
| Antivirus D | 95% | High | Good |
Best Practices for Handling Zip Files from Untrusted Sources
Before opening any zip file from an untrusted source, exercise extreme caution. Always verify the sender’s identity and the legitimacy of the file. If you have any doubts, do not open the file. If the file is expected, consider scanning it with multiple antivirus engines before extraction. Extracting the files into a virtual machine or sandboxed environment is highly recommended, allowing you to analyze the files’ behavior in a safe, isolated space. Regularly update your operating system and software to patch known vulnerabilities, and consider using a dedicated security sandbox for analyzing potentially malicious files. Finally, always maintain regular backups of your crucial data to mitigate potential data loss.
Forensic Analysis Techniques
Analyzing concatenated zip files requires a methodical approach, going beyond simply extracting the contents. The challenge lies in understanding how the files were combined, identifying potential tampering, and reconstructing the original components to uncover malicious intent. This process demands a deep understanding of file structures and metadata.
Forensic analysis of concatenated zip files starts with identifying the archive’s structure. Unlike a single, properly formed zip file, a concatenated archive presents a series of zip file headers intermingled. This means standard zip extraction tools might fail or produce corrupted files. Specialized tools and a thorough understanding of the zip file format are essential for successful analysis.
Extracting and Examining Individual Files
Extracting individual files from a concatenated zip archive necessitates the use of specialized tools or custom scripts. These tools must be capable of identifying and parsing multiple zip headers within the concatenated stream. The process involves locating each zip header, determining the file’s size and offset within the stream, and then extracting the file based on this information. Failure to correctly identify the headers can result in incomplete or corrupted files. A hex editor can be invaluable in visualizing the concatenated data stream and pinpointing the locations of zip headers (identified by their characteristic magic numbers, like “PK”). Manually extracting files requires a deep understanding of the zip file specification, which details the structure of the central directory and local file headers.
Identifying Timestamps and Metadata
Timestamps and metadata embedded within each file within the concatenated zip archive provide crucial information about the file’s creation, modification, and access times. These timestamps, stored within the zip file’s header information, can reveal discrepancies that indicate manipulation or tampering. Analyzing the timestamps of individual files in relation to each other can reveal the order of file creation or modification, and potential inconsistencies can point to malicious activity. For example, a file with a future timestamp might suggest tampering. Additionally, metadata such as file names, permissions, and comments can offer further clues about the files’ origin and purpose. Inconsistencies in metadata across files could also point to a malicious concatenation process.
Reconstructing the File Concatenation Process
Reconstructing the file concatenation process involves analyzing the order and structure of the individual zip files within the concatenated stream. By examining the offsets and sizes of each zip header, the forensic analyst can determine the sequence in which the files were concatenated. This reconstruction is critical in understanding the intent behind the concatenation. For instance, if a malicious payload is found within a specific zip file, understanding its position within the concatenated stream can help determine the attacker’s method and target. Furthermore, analyzing any remaining metadata or remnants of the concatenation process (e.g., temporary files, log entries) can help further reconstruct the events and identify the tools used by the attacker. Careful examination of the file system for related temporary files, scripts, or logs can significantly aid in this reconstruction process.
Real-World Examples and Case Studies
While pinpointing a specific, publicly documented case where zip file concatenation was the *sole* attack vector is difficult due to the often-obscured nature of sophisticated attacks, we can examine how this technique might be woven into a broader campaign. Imagine a scenario where an attacker gains initial access to a system – perhaps through phishing or a vulnerable application. They then use this foothold to deploy a multi-stage attack leveraging zip file concatenation.
The attacker’s objective is to gain persistence and exfiltrate sensitive data from a target organization. They achieve this by uploading seemingly innocuous zip files to a server. These files, individually, might appear harmless; perhaps containing legitimate software updates or configuration files. However, the attacker cleverly concatenates these files, creating a larger, seemingly normal zip archive. This larger archive, when unzipped, reveals a malicious payload hidden within the seemingly benign files. This payload could be a backdoor, allowing for persistent access, or a data exfiltration tool. The malicious code is carefully embedded within the concatenated data stream, making detection challenging.
A Hypothetical Attack Scenario
Let’s consider a scenario involving a software company. The attacker gains access to a developer’s account and uploads seemingly legitimate software updates in individual zip files. These files are then concatenated, creating a larger zip file that, upon extraction, installs a keylogger and begins exfiltrating sensitive project data. The attacker’s success relies on the target’s lack of scrutiny of the uploaded files and the absence of robust security measures to detect unusual file sizes or concatenated archives.
Vulnerabilities Exploited
The success of this attack hinges on several vulnerabilities:
* Lack of File Integrity Checks: The organization failed to implement robust file integrity checks to verify the authenticity and consistency of uploaded files.
* Insufficient Monitoring of File Activity: The organization lacked adequate monitoring systems to detect unusual file sizes, multiple uploads of seemingly similar files, or suspicious activity related to file access.
* Naive Trust in Internal Systems: The attacker exploited the implicit trust placed on internal systems and processes, highlighting the risk of insider threats or compromised accounts.
* Absence of Security Awareness Training: A lack of security awareness training for employees might have led to overlooking the potential for malicious uploads.
Lessons Learned
The following lessons can be learned from this hypothetical but plausible scenario:
It’s crucial to understand that this is a hypothetical scenario, but it highlights real vulnerabilities. The points below illustrate critical security measures that would mitigate such attacks.
- Implement robust file integrity verification mechanisms to ensure the authenticity and integrity of all uploaded files.
- Establish comprehensive monitoring systems to detect unusual file activity, including large file uploads, multiple uploads of similar files, and access patterns outside the norm.
- Enforce strong access controls and regularly audit user accounts to prevent unauthorized access and limit the potential impact of compromised accounts.
- Provide regular and thorough security awareness training to employees to educate them about potential threats, including social engineering tactics and the importance of reporting suspicious activity.
- Utilize advanced threat detection tools capable of analyzing file content and identifying malicious code hidden within seemingly benign files, including those created through concatenation.
Summary

Source: lifeboat.com
So, the next time you download a zip file, remember the lurking danger of concatenation. While seemingly harmless, a simple zip file can be a wolf in sheep’s clothing. By understanding the techniques hackers use and implementing robust security measures, you can significantly reduce your risk. Staying vigilant and educated is your best defense against these ever-evolving cyber threats. Remember, it’s not just about the antivirus; it’s about smart file handling and a healthy dose of skepticism.





