APT37 hackers actively scanning targets—it sounds like a scene straight out of a cyberpunk thriller, right? But this isn’t fiction; it’s a chilling reality. This shadowy group, known for its sophisticated attacks and relentless pursuit of sensitive data, is once again making headlines. Their targets aren’t random; they’re carefully selected based on industry, geographic location, and the juicy data they hold. We’re diving deep into APT37’s methods, from their initial reconnaissance to their advanced evasion techniques, to understand how they operate and, more importantly, how to protect ourselves.
This deep dive will unpack APT37’s target selection process, exploring the criteria they use to identify vulnerable organizations. We’ll examine their scanning techniques, dissecting the tools and vulnerabilities they exploit to gain access. Further, we’ll investigate their command and control infrastructure, revealing how they maintain persistence and evade detection. Finally, we’ll equip you with crucial mitigation strategies and best practices to safeguard your systems against this persistent threat. Get ready for a thrilling exposé into the world of advanced persistent threats.
APT37’s Target Selection
APT37, a notorious North Korean state-sponsored hacking group, demonstrates a highly selective targeting strategy, focusing its efforts on entities offering significant geopolitical or economic value. Their operations are characterized by meticulous planning and persistent infiltration, highlighting a sophisticated understanding of their targets’ technological vulnerabilities and operational workflows.
APT37’s Target Selection Criteria
APT37’s target selection is driven by a combination of factors. Primarily, they focus on industries with access to sensitive data crucial for national security or economic advancement. This includes defense contractors, telecommunications companies, and government agencies. Geographic location also plays a significant role; targets are often located in South Korea, Japan, and other countries deemed strategically important to North Korea. Finally, data sensitivity is paramount; APT37 prioritizes organizations possessing intellectual property, military secrets, or financial data that can be leveraged for espionage or financial gain.
Comparison with Other APT Groups
While many APT groups target similar sectors like finance and government, APT37’s focus exhibits a distinct geopolitical angle, strongly aligning with North Korea’s national interests. Groups like APT41, for instance, may exhibit a more financially motivated approach, often targeting intellectual property for commercial gain alongside espionage activities. Conversely, groups like APT29 (Cozy Bear) demonstrate a greater emphasis on intelligence gathering, often focusing on diplomatic and political targets. APT37’s strategy sits uniquely at the intersection of espionage and potentially financially motivated actions, directly supporting North Korea’s agenda.
Hypothetical APT37 Target Profile
A typical APT37 target might be a South Korean defense contractor with a robust technological infrastructure, including on-premise servers, cloud-based services, and a geographically dispersed workforce. Their data assets would include highly sensitive information on military projects, research and development data, and financial records. The organization’s network security might be considered advanced but still vulnerable to sophisticated spear-phishing attacks or zero-day exploits, precisely the tactics favored by APT37.
Known APT37 Targets
The following table summarizes characteristics of known APT37 targets. Due to the clandestine nature of their operations and the often-delayed public disclosure of breaches, comprehensive information remains limited.
| Industry | Geographic Location | Data Breached (if known) | Impact of Breach |
|---|---|---|---|
| Defense Contractor | South Korea | Military project details, R&D data | Compromised national security, potential technological advantage lost |
| Telecommunications | Japan | Customer data, network infrastructure details | Financial loss, reputational damage, potential espionage |
| Government Agency | South Korea | Internal communications, policy documents | Compromised national security, potential political instability |
| Financial Institution | Various | Financial records, customer data | Financial loss, reputational damage |
APT37 Scanning Techniques
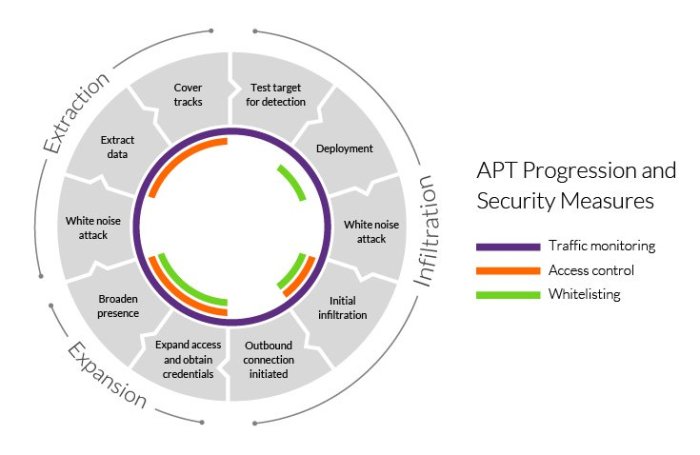
Source: imperva.com
APT37, a notorious North Korean state-sponsored hacking group, employs sophisticated techniques to identify and compromise their targets. Their scanning methods are designed for stealth and efficiency, maximizing their chances of success while minimizing detection. Understanding these techniques is crucial for building effective defenses against their attacks.
APT37’s initial reconnaissance likely involves a multi-pronged approach, combining open-source intelligence (OSINT) gathering with active probing of potential targets. They leverage publicly available information like company websites, social media profiles, and news articles to build a profile of their targets, identifying potential vulnerabilities and entry points. This is followed by active scanning to validate their findings and pinpoint specific weaknesses exploitable for initial access.
Vulnerabilities Exploited During Initial Scanning
APT37’s scanning phase focuses on identifying known vulnerabilities in widely used software and systems. This allows for efficient exploitation using readily available tools and techniques. Common targets include outdated versions of operating systems, web servers, and applications with known security flaws. They also actively seek vulnerabilities related to weak or default credentials, misconfigured network devices, and exposed remote services. Successfully exploiting these vulnerabilities provides the initial foothold necessary for deeper penetration. For example, they might exploit a known vulnerability in a web server to gain initial access, then leverage that access to move laterally within the network.
Tools and Techniques for Undetected Scanning
To avoid detection during the scanning phase, APT37 relies on a combination of tools and techniques designed to mask their activities. This includes using anonymization networks like Tor to obscure their IP addresses and employing custom-built tools to blend in with legitimate network traffic. They might also leverage compromised machines (bots) within the target’s network or in other networks to conduct scanning activities, further obscuring their origin. Furthermore, they carefully craft their scanning requests to avoid triggering intrusion detection systems (IDS) and security information and event management (SIEM) tools. The use of low-and-slow scanning techniques, spread out over extended periods, is another key tactic. Imagine a scenario where they use a series of seemingly benign probes over several weeks, making it harder to pinpoint malicious activity amidst legitimate network traffic.
Hypothetical Timeline of a Successful Intrusion
A successful intrusion by APT37 typically follows a phased approach. The following hypothetical timeline illustrates a possible progression from initial scanning to a successful compromise:
- Phase 1 (Weeks 1-4): Reconnaissance and Vulnerability Assessment. APT37 uses OSINT and automated scanning tools to identify potential targets and assess their vulnerabilities. They focus on organizations with valuable intellectual property or strategic importance.
- Phase 2 (Weeks 5-8): Initial Access. Exploiting a discovered vulnerability (e.g., a known vulnerability in a web server or a phishing campaign targeting an employee) allows APT37 to gain initial access to the target’s network.
- Phase 3 (Weeks 9-12): Lateral Movement and Privilege Escalation. Once inside, they use various techniques to move laterally across the network, gaining access to more sensitive systems and escalating their privileges to gain administrator-level access.
- Phase 4 (Weeks 13 onwards): Data Exfiltration and Persistence. APT37 exfiltrates sensitive data using stealthy methods and establishes persistence mechanisms to maintain long-term access to the compromised network, potentially for future operations.
APT37’s Infrastructure and Control
APT37’s command and control (C2) infrastructure is a critical element of their operations, enabling persistent access to victim networks and facilitating data exfiltration. Understanding its characteristics is crucial for effective defense. The group’s infrastructure is likely designed for resilience and obfuscation, leveraging a variety of techniques to avoid detection and maintain operational secrecy.
APT37’s C2 Infrastructure Characteristics
Geographic Distribution and Resilience
APT37’s C2 servers are likely geographically dispersed across multiple countries, potentially using cloud-based services or compromised servers in various locations. This distribution enhances resilience by making it difficult to take down the entire infrastructure with a single action. For example, they might utilize servers in countries with lax cybersecurity regulations or those known for their internet infrastructure’s anonymity. This approach minimizes the impact of takedowns and allows for redundancy in case of server failures or compromises. The use of multiple, geographically dispersed servers increases the difficulty of tracking the group and allows them to maintain operations even if some servers are compromised or taken offline.
Persistence and Evasion Techniques
To maintain persistent access, APT37 likely employs various techniques. This includes the use of legitimate software vulnerabilities, custom-developed malware, and techniques to blend in with legitimate network traffic. They might use techniques like living off the land (LOLBins) to leverage existing tools on compromised systems, avoiding the need to deploy new malware and reducing the chances of detection. The use of domain generation algorithms (DGAs) or fast flux networks allows them to rapidly change their C2 server addresses, making it difficult for security tools to track them. Additionally, encryption of communication channels is almost certainly employed to protect the confidentiality of their data.
Obscuring C2 Infrastructure
APT37 likely employs several methods to obscure its C2 infrastructure and evade detection. These include using proxy servers to mask the origin of their communications, employing techniques such as tunneling to conceal their traffic within seemingly legitimate connections, and using encryption to prevent the content of their communications from being intercepted and analyzed. They might leverage compromised servers as proxies, creating a layered approach that makes tracing the communication back to the group significantly harder. Furthermore, they may utilize legitimate cloud services to host their C2 infrastructure, blending in with legitimate network traffic and making it harder to identify malicious activity.
Diagram of a Possible APT37 C2 Infrastructure
Imagine a diagram showing multiple layers. At the outermost layer are several compromised servers scattered across different countries (e.g., Server A in China, Server B in Russia, Server C in Vietnam). These act as initial access points and entry points for exfiltrated data. These servers then communicate with a layer of proxy servers (Proxy Server 1, Proxy Server 2, Proxy Server 3) located in different jurisdictions. These proxies further obfuscate the origin of the communication. Finally, a central C2 server (C2 Server) receives the data, possibly located in a country with weaker cybersecurity regulations or in a cloud environment. The communication channels between all these components are encrypted using strong encryption protocols. The entire infrastructure utilizes a combination of protocols (e.g., HTTPS, SSH, custom protocols) and employs techniques like domain fronting and fast flux DNS to further enhance anonymity and resilience. The connections between the layers are not direct, adding an additional layer of complexity for tracking and detection.
Mitigation Strategies Against APT37: Apt37 Hackers Actively Scanning Targets

Source: cyndia.in
APT37, a sophisticated and persistent threat actor, requires a multi-layered defense strategy. Organizations cannot rely on a single security measure to effectively counter their advanced techniques. A proactive and comprehensive approach, encompassing preventative measures, detection capabilities, and robust incident response planning, is crucial for minimizing the risk of a successful APT37 attack.
Effective mitigation against APT37 necessitates a deep understanding of their tactics, techniques, and procedures (TTPs). This understanding allows organizations to tailor their security posture to specifically address the known vulnerabilities APT37 exploits. Furthermore, regular security assessments and penetration testing are essential for identifying weaknesses before they can be exploited.
Effective Security Measures, Apt37 hackers actively scanning targets
Implementing a robust security posture requires a combination of technical controls and security awareness training. This includes deploying advanced endpoint detection and response (EDR) solutions to monitor system activity for malicious behavior. Network segmentation limits the impact of a breach by isolating critical systems. Regular software patching and vulnerability management are essential to prevent exploitation of known vulnerabilities. Multi-factor authentication (MFA) significantly enhances account security and reduces the likelihood of successful credential theft. Finally, strong security awareness training empowers employees to identify and report suspicious activities.
Detecting and Responding to APT37 Scanning Activity
Early detection of APT37’s scanning activity is critical for preventing a successful breach. This requires monitoring network traffic for unusual patterns and suspicious connections. Security Information and Event Management (SIEM) systems play a crucial role in collecting and analyzing security logs from various sources, allowing for the identification of anomalous activity. Intrusion detection systems (IDS) can be configured to alert on known APT37 attack signatures and techniques. Threat intelligence feeds provide valuable information about APT37’s known TTPs, enabling proactive security measures. A well-defined incident response plan, including clear escalation procedures and communication protocols, is essential for effectively handling any detected intrusion.
Successful Incident Response Strategies
Successful responses to APT37 attacks often involve collaboration between internal security teams and external cybersecurity experts. A well-defined incident response plan is critical, outlining steps to contain the breach, eradicate the malware, recover affected systems, and perform post-incident analysis. The use of forensic tools is vital for gathering evidence and understanding the extent of the compromise. Working with law enforcement and sharing threat intelligence with other organizations helps in mitigating future attacks and identifying the full scope of APT37’s operations. Examples of successful responses include rapid isolation of compromised systems, swift deployment of malware removal tools, and comprehensive post-incident analysis to identify vulnerabilities and improve security posture.
Layered Security Approach Against APT37 TTPs
A layered security approach is vital to mitigate APT37’s advanced techniques. This approach combines multiple security controls to create a robust defense in depth.
- Network Security: Implement robust firewalls, intrusion detection/prevention systems (IDS/IPS), and secure web gateways to filter malicious traffic and block known APT37 infrastructure.
- Endpoint Security: Deploy advanced endpoint detection and response (EDR) solutions, regularly update antivirus software, and enforce strong endpoint security policies.
- Identity and Access Management (IAM): Enforce multi-factor authentication (MFA) for all accounts, implement strong password policies, and regularly review user access privileges.
- Data Security: Employ data loss prevention (DLP) tools, encrypt sensitive data both in transit and at rest, and implement regular data backups.
- Threat Intelligence: Leverage threat intelligence feeds to stay informed about APT37’s latest tactics and techniques and proactively mitigate potential threats.
- Security Awareness Training: Regularly train employees on cybersecurity best practices to improve their ability to identify and report phishing attempts and other social engineering attacks.
- Incident Response Planning: Develop and regularly test a comprehensive incident response plan to ensure a coordinated and effective response to any security incident.
The Geopolitical Context of APT37 Activity
Source: portswigger.net
APT37, a North Korean state-sponsored hacking group, operates within a complex geopolitical landscape, its actions reflecting and shaping international relations. Understanding the motivations behind their targets and the consequences of their operations requires analyzing the broader context of North Korea’s foreign policy and its pursuit of economic and technological advancement.
APT37’s activities are deeply intertwined with North Korea’s efforts to circumvent international sanctions and bolster its economy. The group’s cyber operations, primarily focused on stealing intellectual property and financial resources, directly contribute to these objectives. This contrasts with other state-sponsored groups, whose motivations might be focused on espionage, sabotage, or information warfare, though overlap exists.
APT37’s Targeting Choices and Geopolitical Objectives
APT37’s target selection isn’t random. The group consistently targets organizations in South Korea, the United States, and other countries perceived as adversaries or possessing valuable technology. This demonstrates a clear geopolitical strategy aimed at undermining competitors and acquiring sensitive information to advance North Korea’s technological capabilities and economic self-sufficiency. For instance, the theft of intellectual property from South Korean companies in the defense and technology sectors directly weakens a key rival and potentially provides North Korea with a technological edge. Similarly, targeting financial institutions could provide funds to circumvent sanctions.
Comparison with Other State-Sponsored Cyber Operations
While many nation-states utilize cyber operations, APT37’s methods and focus differ somewhat. Groups like Russia’s APT29 (Cozy Bear) often focus on espionage and intelligence gathering, while China’s APT41 engages in both espionage and financially motivated cybercrime. APT37’s emphasis on intellectual property theft and its clear link to North Korea’s economic needs set it apart. The level of direct economic benefit derived from APT37’s actions is arguably more pronounced than that of some other state-sponsored groups whose primary aims may be political influence or disruption.
Consequences of APT37’s Actions on International Relations and Cybersecurity
APT37’s actions destabilize international relations by creating distrust and escalating tensions between North Korea and its adversaries. The constant threat of cyberattacks undermines confidence in global cybersecurity infrastructure and necessitates increased spending on defense measures. These activities contribute to a broader arms race in cyberspace, potentially leading to more sophisticated and destructive attacks. The theft of sensitive information, particularly in the defense sector, can also compromise national security and potentially trigger retaliatory actions, further escalating tensions. The resulting increase in global cybersecurity spending diverts resources from other areas of development.
Examples of APT37’s Activities Achieving Geopolitical Objectives
Successful attacks against South Korean defense contractors, for example, could provide North Korea with valuable insights into military technology, aiding its weapons development programs. Similarly, stealing financial data from international banks could help circumvent sanctions and provide funding for its nuclear and missile programs. These actions directly support North Korea’s geopolitical goals of maintaining its regime and projecting power, despite international pressure. The long-term effects of these actions are a complex interplay of technological advancement for North Korea and increased international pressure to counter these activities.
Conclusive Thoughts
The threat posed by APT37 is real, and understanding their methods is the first step toward effective defense. While their sophisticated techniques make them formidable adversaries, a layered security approach, coupled with proactive threat intelligence and swift incident response, can significantly reduce the risk of a successful attack. Staying vigilant, updating security measures, and keeping abreast of the latest threat landscape are crucial in the ongoing battle against advanced persistent threats like APT37. The fight is far from over, but with knowledge and preparedness, we can tip the scales in our favor.





