PFSense stored XSS vulnerability: Sounds scary, right? Imagine a tiny bit of malicious code hiding in your firewall’s seemingly innocent settings, waiting to pounce. This isn’t some theoretical threat; it’s a real possibility that could hand over control of your network to bad actors. We’re diving deep into the dark corners of this vulnerability, exploring how it works, how to spot it, and most importantly, how to stop it before it wreaks havoc on your digital fortress.
This vulnerability allows attackers to inject malicious scripts into your PFSense system, potentially stealing sensitive data, redirecting traffic, or even taking complete control. We’ll examine various attack vectors, delve into effective mitigation strategies, and provide practical steps to secure your PFSense installation. Think of this as your ultimate guide to surviving a digital siege.
Understanding the PFSense Stored XSS Vulnerability
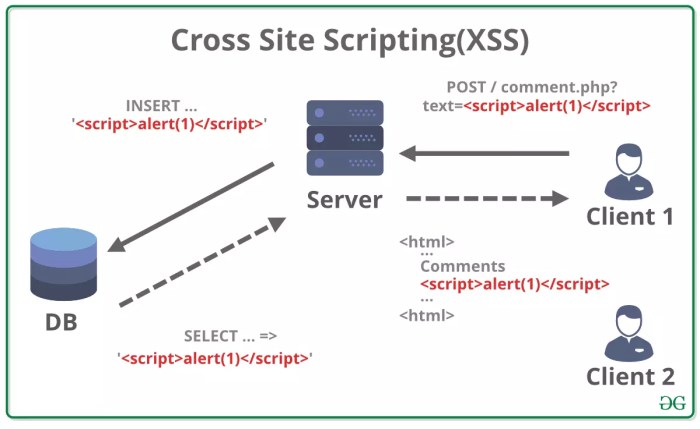
PFSense, a popular open-source firewall, isn’t immune to security vulnerabilities. One particularly nasty threat is the Stored Cross-Site Scripting (XSS) vulnerability. Unlike reflected XSS, which relies on manipulating links, stored XSS involves injecting malicious code into the PFSense system itself, where it persists and waits to be executed. Understanding how this works is crucial for securing your network.
Stored XSS vulnerabilities in PFSense arise when user-supplied data is improperly sanitized before being saved to the system’s database or configuration files. This unsanitized data, which could contain malicious JavaScript code, is then served back to other users, potentially compromising their sessions or the entire system.
Mechanics of a Stored XSS Vulnerability in PFSense
A stored XSS vulnerability in PFSense occurs when a malicious actor manages to inject JavaScript code into a field within the PFSense web interface that is subsequently stored by the system. This could be a comment field in a log, a custom description for a network rule, or even within a less obvious field. When a legitimate user later views this data, the malicious JavaScript code executes within their browser context, granting the attacker potential access to their session cookies, network credentials, or even the ability to execute further attacks on the PFSense system itself. The key is that the attacker only needs to inject the malicious code once; it remains stored and active until removed.
Potential Impact of a Successful Stored XSS Attack on a PFSense System
The consequences of a successful stored XSS attack on a PFSense system can be severe. A malicious script could allow an attacker to:
* Steal session cookies: This grants the attacker access to the administrator’s account, allowing them complete control over the firewall’s configuration.
* Redirect users to malicious websites: The attacker could redirect users to phishing sites or sites hosting malware.
* Modify PFSense configuration: This could include disabling security features, opening ports, or altering routing tables, severely compromising the network’s security.
* Install malware: In more sophisticated attacks, the attacker could potentially upload and execute malicious code on the PFSense system itself.
* Gain access to sensitive network data: Depending on the system’s configuration, the attacker might gain access to sensitive data such as passwords, network traffic, or other confidential information.
Examples of User Inputs That Could Be Exploited in a Stored XSS Attack
Several user input fields within PFSense could be vulnerable to stored XSS attacks if not properly sanitized. Examples include:
* Description fields: Fields where administrators provide descriptions for network rules, aliases, or other configuration elements. An attacker could inject JavaScript into these descriptions.
* Log comments: If PFSense allows user comments on log entries, these could be exploited.
* Customizable interface elements: Any field that allows for user-defined text or HTML input, without proper sanitization, is potentially vulnerable.
* Any field accepting user input that’s subsequently stored and displayed without proper encoding. This is the core of the vulnerability.
Comparison of XSS Vulnerability Types
The following table compares different types of XSS vulnerabilities and their relevance to PFSense:
| Type of XSS | Description | Mechanism | Relevance to PFSense |
|---|---|---|---|
| Reflected XSS | Malicious script is reflected back to the user from the server in the response to a request. | User input is included in the server’s response without proper sanitization. | Potentially relevant if PFSense doesn’t properly sanitize user input in specific URLs or parameters. Less severe than stored XSS. |
| Stored XSS (Persistent XSS) | Malicious script is stored on the server and executed when a user views the stored data. | User input is stored in a database or file without proper sanitization. | Highly relevant as it allows for persistent attacks and compromises the system itself. |
| DOM-based XSS | Malicious script is executed by the client-side browser without involving the server. | Manipulating the Document Object Model (DOM) within the client’s browser. | Potentially relevant if client-side JavaScript in PFSense is vulnerable to manipulation. Less severe than stored XSS, but still a risk. |
Identifying Vulnerable Components in PFSense
PFSense, while robust, isn’t immune to vulnerabilities. Understanding potential entry points for stored Cross-Site Scripting (XSS) attacks within its web interface is crucial for maintaining a secure network. This section will pinpoint specific areas requiring careful attention and highlight mitigation strategies.
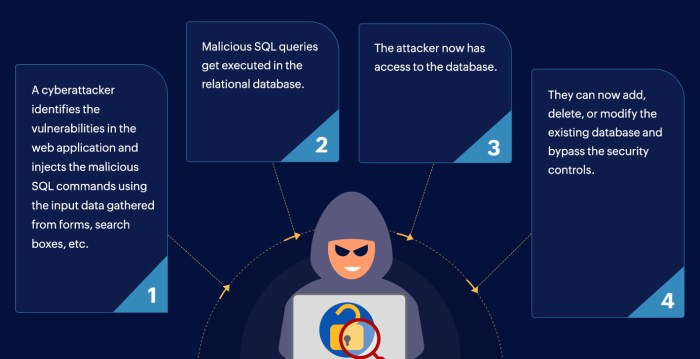
Stored XSS attacks occur when malicious scripts are injected into a web application and persistently stored on the server. When legitimate users access the compromised data, the malicious script executes in their browser, potentially allowing attackers to steal sensitive information, hijack sessions, or perform other harmful actions. In PFSense, this could involve exploiting vulnerabilities in areas where user-supplied data is processed and stored without proper sanitization.
Potential Entry Points for Stored XSS Attacks, Pfsense stored xss vulnerability
The PFSense web interface offers various points where malicious code could be injected. These are typically areas where user input is accepted and subsequently displayed without adequate filtering. For instance, customizable fields in the system’s configuration, such as descriptions for interfaces or aliases, represent a potential risk. If these fields aren’t properly sanitized, an attacker could inject malicious JavaScript code. Similarly, any feature allowing for user-defined content, such as custom messages or descriptions within various modules, needs rigorous security scrutiny.
Vulnerable PFSense Modules and Features
Several PFSense modules and features deserve special attention regarding stored XSS vulnerabilities. The “Diagnostics” section, particularly the “System Information” and “Interface Statistics” pages, could be vulnerable if they display user-provided data without sufficient filtering. Similarly, the “Firewall” rules and “Aliases” sections, if they permit user-defined descriptions or comments, require careful consideration. Customizable settings within packages, such as those related to captive portals or other third-party applications integrated with PFSense, also represent potential vulnerabilities.
The Role of Authentication and Authorization
While authentication and authorization don’t directly prevent stored XSS, they significantly limit its impact. Strong authentication mechanisms, like multi-factor authentication, make it harder for attackers to gain access to the system in the first place. Authorization controls restrict access to sensitive configuration options, limiting the potential damage an attacker can inflict even if they successfully inject malicious code. By limiting who can modify critical system settings, the scope of a successful XSS attack is greatly reduced.
Input Sanitization and Validation to Prevent Stored XSS Attacks
Proper input sanitization and validation are paramount in preventing stored XSS. Sanitization involves removing or escaping characters that could be interpreted as code. Validation ensures that the input conforms to expected formats and constraints. For example, input fields should only accept alphanumeric characters or a predefined set of allowed symbols. PFSense should implement robust input validation and sanitization across all areas where user-supplied data is processed and stored. This includes using parameterized queries for database interactions to prevent SQL injection, which is often intertwined with XSS vulnerabilities. Employing encoding mechanisms like HTML encoding for user-supplied data before displaying it on the web interface is crucial.
Mitigation and Prevention Strategies
Source: siemxpert.com
Preventing Stored XSS vulnerabilities in PFSense requires a multi-pronged approach encompassing secure coding practices, robust input validation, and the implementation of appropriate security headers. Ignoring these measures leaves the system vulnerable to attacks that can compromise user data and system integrity. Let’s delve into the specific strategies that can significantly reduce this risk.
Secure Coding Practices Guideline
Developers working on PFSense should adhere to a strict set of guidelines to minimize the risk of introducing Stored XSS vulnerabilities. This includes consistently applying parameterized queries to prevent the injection of malicious scripts into database queries. All user-supplied data must be treated as potentially harmful, and developers should avoid directly embedding this data into HTML, CSS, or JavaScript. Instead, mechanisms like output encoding and context-aware escaping should be used. Regular code reviews and security audits are essential to identify and address potential vulnerabilities before deployment. A comprehensive training program for developers on secure coding practices is also vital. Following these practices will greatly reduce the chances of introducing vulnerabilities into the codebase.
Input Validation and Sanitization
Robust input validation and sanitization are paramount. Before any user-supplied data is processed or stored, it must undergo rigorous validation to ensure it conforms to expected formats and data types. This includes checking for length restrictions, allowed characters, and data patterns. Sanitization involves removing or escaping potentially harmful characters, such as `<`, `>`, `”`, and `’`, that could be used to construct malicious scripts. Regular expressions can be effectively used for complex validation and sanitization tasks. For example, a regular expression could be used to validate email addresses, ensuring they conform to a specific format before storage. Similarly, any input intended for display should be properly encoded to prevent script execution. Failure to implement thorough input validation leaves the system wide open to attacks.
Security Headers Implementation
Implementing appropriate security headers is crucial for mitigating XSS attacks, even if vulnerabilities exist within the application itself. These headers act as a secondary layer of defense. A crucial header is `Content-Security-Policy (CSP)`. CSP allows defining a whitelist of sources from which the browser is allowed to load resources, thereby preventing the execution of scripts from untrusted domains. For example, a CSP header might look like this: `Content-Security-Policy: default-src ‘self’; script-src ‘self’ ‘unsafe-inline’`. Other important headers include `X-XSS-Protection`, which enables the browser’s built-in XSS filter, and `X-Frame-Options`, which helps prevent clickjacking attacks. Properly configured security headers significantly reduce the impact of a successful XSS attack.
Output Encoding Techniques
Output encoding is a crucial technique to prevent XSS vulnerabilities. This involves converting special characters into their corresponding HTML entities before rendering them in the output. For example, the less-than symbol `<` should be encoded as `<`, and the greater-than symbol `>` should be encoded as `>`. The specific encoding method depends on the context where the data is displayed. For HTML contexts, HTML encoding should be used. For JavaScript contexts, JavaScript encoding should be employed. Failing to use appropriate output encoding leaves the application vulnerable to XSS attacks, even if input validation is performed correctly. Consider this example: instead of directly displaying user input like “, it should be encoded as `
$encodedUserInput
` where `encodedUserInput` is the result of applying appropriate HTML encoding to the user’s input.
Exploitation and Remediation
Source: manageengine.com
Understanding how a stored XSS vulnerability in pfSense can be exploited is crucial for effective remediation. This section details a hypothetical attack scenario, the steps involved in exploitation, and a systematic approach to fixing the vulnerability. We’ll also explore methods for proactively detecting these vulnerabilities.
Imagine a malicious actor discovers a stored XSS vulnerability in pfSense’s web interface, specifically within the “System Logs” section. This section allows administrators to view and filter system events, and perhaps even allows for custom notes or descriptions to be added to specific log entries. If this input isn’t properly sanitized, an attacker could inject malicious JavaScript code.
Hypothetical Stored XSS Attack Scenario
Let’s say the vulnerability resides in the “Add Note” functionality of the System Logs. An attacker crafts a malicious note containing JavaScript code designed to steal administrator cookies. When an administrator views the log entry containing this injected script, their browser executes the malicious code, potentially granting the attacker unauthorized access to the pfSense system.
Exploitation Steps
The exploitation process would typically involve these steps:
- Identifying the Vulnerability: The attacker first identifies a vulnerable input field, such as the “Add Note” field in our hypothetical scenario.
- Crafting the Payload: The attacker crafts a malicious JavaScript payload. This might involve stealing cookies using
document.cookie, redirecting the administrator to a phishing site, or performing other malicious actions. For example: - Injecting the Payload: The attacker submits the crafted payload through the vulnerable input field.
- Triggering the Execution: The malicious script executes when a legitimate user (administrator) views the log entry containing the injected payload.
- Exploiting the Compromise: The attacker leverages the compromised session to gain unauthorized access to the pfSense system or steal sensitive information.
Remediation Steps
Remediating a stored XSS vulnerability requires a structured approach. The following table Artikels the key steps:
| Step | Action | Tools/Techniques | Verification |
|---|---|---|---|
| Identify Vulnerable Code | Review the source code of the affected component (e.g., the “Add Note” functionality) to pinpoint the location where user input is handled without proper sanitization. | Code review, static analysis tools (e.g., SonarQube, FindBugs) | Manual inspection, code analysis reports. |
| Patch the Vulnerability | Implement appropriate input sanitization techniques (e.g., encoding special characters, using parameterized queries, input validation). | Source code editor, version control system. | Code review, unit tests. |
| Test the Fix | Thoroughly test the patched code to ensure the vulnerability has been successfully eliminated. Use both manual testing and automated tools. | Penetration testing tools (e.g., Burp Suite), manual testing, automated security scanners. | Successful prevention of XSS attacks. Absence of vulnerabilities in security scans. |
| Deploy the Patch | Deploy the patched code to the production pfSense system, following established change management procedures. | Deployment scripts, system management tools. | Successful deployment confirmation. |
Detecting Stored XSS Vulnerabilities
Both static and dynamic analysis techniques can be employed to detect stored XSS vulnerabilities. Static analysis involves examining the source code without executing it, while dynamic analysis involves testing the application during runtime.
Static analysis tools can identify potential vulnerabilities by analyzing the code for unsafe input handling practices. Dynamic analysis tools, such as penetration testing suites, simulate real-world attacks to identify vulnerabilities during runtime. Regular security scans and penetration testing are crucial for proactive vulnerability detection and remediation.
Security Best Practices
Securing your PFSense system against Cross-Site Scripting (XSS) attacks requires a multi-layered approach. It’s not just about patching vulnerabilities; it’s about adopting a proactive security mindset that anticipates and mitigates risks. Think of it like building a fortress – multiple layers of defense make it significantly harder for attackers to breach.
Regular security updates and patching are the bedrock of any robust security strategy. Ignoring updates leaves your system vulnerable to known exploits, making it a prime target for malicious actors. Think of it as leaving your front door unlocked – it’s an open invitation for trouble. Staying up-to-date is crucial, and not just for PFSense itself, but for all software and firmware running on your network.
Regular Security Updates and Patching
PFSense, like any software, receives regular updates that address security vulnerabilities, including those that could lead to XSS attacks. These updates often include critical bug fixes and performance improvements. Failing to install these updates exposes your system to potential attacks, which can range from data breaches to complete system compromise. A consistent and automated update schedule is crucial for maintaining a secure environment. For instance, a company might schedule automatic updates during off-peak hours to minimize disruption, while smaller organizations might opt for manual updates with a strict schedule. The key is consistency and timeliness.
Web Application Firewall (WAF) Protection
A Web Application Firewall (WAF) acts as an extra layer of security, filtering malicious traffic before it even reaches your PFSense system. A WAF can effectively detect and block XSS attacks by inspecting incoming HTTP requests for malicious scripts. It’s like having a vigilant guard at the gate, examining every visitor before allowing them access. By using a WAF, you can significantly reduce the risk of successful XSS attacks, even if some vulnerabilities remain unpatched. Consider a scenario where a less sophisticated attacker attempts a known XSS exploit. A WAF would intercept and block this attempt before it reaches your PFSense instance. Choosing a WAF that’s compatible with your PFSense setup and regularly updating its ruleset is vital for its effectiveness.
PFSense Configuration Recommendations
Implementing these configurations significantly minimizes the risk of XSS vulnerabilities. It’s a proactive approach that strengthens your security posture. Consider these recommendations as additional layers of defense, bolstering the core security measures already in place.
- Enable HTTPS: Using HTTPS encrypts communication between clients and your PFSense system, making it significantly harder for attackers to intercept and manipulate data, including potentially malicious scripts.
- Input Validation: Strictly validate all user inputs on any web interface exposed by PFSense. Sanitize and escape any data before displaying it on a webpage. This prevents malicious scripts from being injected.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities. These audits should cover both the PFSense system itself and any custom scripts or plugins used.
- Principle of Least Privilege: Configure user accounts with only the necessary permissions. This limits the impact of a compromised account.
- Disable Unnecessary Services: Disable any services or features that are not essential to your network’s operation. This reduces the attack surface.
- Strong Passwords and Multi-Factor Authentication (MFA): Implement strong passwords and enable MFA wherever possible to protect against unauthorized access.
Case Studies and Examples
Source: githubusercontent.com
Understanding real-world examples of stored XSS vulnerabilities helps us appreciate the severity and impact of such attacks. Seeing how these vulnerabilities manifest in different systems, and the lessons learned from their exploitation and remediation, is crucial for building robust security practices. This section explores several case studies and demonstrates how vulnerability scanners can help in proactive detection.
Analyzing past incidents reveals common patterns and weaknesses in system design and implementation that contribute to XSS vulnerabilities. Learning from these mistakes allows us to develop more effective preventative measures and improve our overall security posture.
Real-World Stored XSS Vulnerability Examples
Several high-profile incidents demonstrate the far-reaching consequences of stored XSS vulnerabilities. These examples highlight the need for rigorous input validation and output encoding across all web applications and network devices.
In 2013, a vulnerability in a popular forum software allowed attackers to inject malicious JavaScript code into forum posts. When other users viewed the posts, the malicious code executed in their browsers, potentially stealing cookies or redirecting them to phishing websites. The impact included compromised user accounts and data breaches.
Another example involves a content management system (CMS) where an attacker injected malicious code into a comment field. This code was then stored in the database and executed whenever a user viewed the page containing the comment. This led to unauthorized access to user accounts and the ability to manipulate site content.
Lessons Learned from Past XSS Vulnerabilities in Network Devices
XSS vulnerabilities in network devices often have more severe consequences than in typical web applications due to the sensitive data these devices handle. Lessons learned from past incidents highlight the critical need for secure coding practices and rigorous security testing.
Past vulnerabilities have demonstrated that insufficient input sanitization is a major contributing factor. Attackers can exploit this weakness to inject malicious code into various device configurations or management interfaces. This can lead to complete device compromise, data theft, and denial-of-service attacks. The lack of robust output encoding further exacerbates the problem, allowing malicious scripts to execute in the victim’s browser.
Using Vulnerability Scanners to Detect XSS Vulnerabilities in PFSense
Vulnerability scanners play a crucial role in proactive security. They automate the process of identifying potential weaknesses, including XSS vulnerabilities, in PFSense and other systems. Regular scanning is essential for maintaining a secure network environment.
Many commercial and open-source vulnerability scanners are available. These scanners utilize various techniques to detect XSS vulnerabilities, such as analyzing web application traffic, identifying insecure coding patterns, and checking for known vulnerabilities in PFSense’s software components. The results of these scans provide valuable insights into potential security risks, allowing administrators to address vulnerabilities before they can be exploited.
Last Point
Securing your PFSense system against stored XSS vulnerabilities isn’t just about patching holes; it’s about adopting a proactive security mindset. Regular updates, robust input validation, and a healthy dose of paranoia are your best weapons. By understanding the mechanics of this attack and implementing the strategies Artikeld above, you can significantly reduce your risk and keep your network safe from malicious intruders. Remember, vigilance is key in the ever-evolving world of cybersecurity. Don’t let a single vulnerability bring down your entire digital kingdom.





