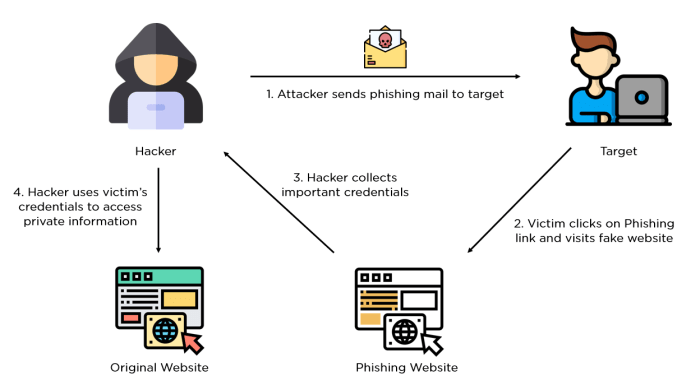
Phishing attack weaponized RDP file: Sounds scary, right? It should. This isn’t your grandpappy’s phishing scam. We’re talking about a sophisticated attack using a seemingly innocent Remote Desktop Protocol (RDP) file to sneak malware onto your system. Think of it as a digital Trojan horse, cleverly disguised and waiting to pounce. This isn’t just about stolen passwords; it’s about complete system compromise, data theft, and potential network-wide havoc. Buckle up, because we’re diving deep into the dark art of weaponized RDP files.
RDP, or Remote Desktop Protocol, is a legitimate tool for accessing computers remotely. But in the wrong hands, it becomes a potent weapon. Attackers leverage vulnerabilities in RDP – weak passwords, default credentials, or even social engineering tricks – to gain unauthorized access. They then use weaponized RDP files, often delivered through cleverly crafted phishing emails or malicious links, to install malware and establish a persistent backdoor into your system. This allows them to steal sensitive data, control your computer, and potentially spread the infection across your entire network.
Understanding RDP and its Vulnerabilities
Source: simplilearn.com
Remote Desktop Protocol (RDP) is a powerful tool that allows you to access and control a computer remotely. It’s incredibly useful for system administrators managing servers, or for individuals needing access to their home computers while traveling. However, this convenience comes with significant security risks if not properly configured and managed. Understanding these vulnerabilities is crucial to preventing successful attacks.
RDP’s core functionality revolves around establishing a secure connection between two computers. This connection allows the user on one machine (the client) to see and interact with the desktop of another machine (the server) as if they were sitting directly in front of it. This seemingly simple process, however, hinges on robust security measures to prevent unauthorized access.
Common RDP Security Misconfigurations
Improperly configured RDP settings are a major contributor to successful attacks. Leaving RDP enabled on a publicly accessible server without any additional security measures is akin to leaving your front door unlocked. Other common misconfigurations include the use of weak passwords, lack of multi-factor authentication (MFA), and failure to regularly update the RDP server software with security patches. These oversights create gaping holes in security, allowing malicious actors easy access. For example, failing to enable Network Level Authentication (NLA) significantly weakens the security of the RDP connection, making it susceptible to credential stuffing and brute-force attacks. Similarly, using a default RDP port (3389) without port forwarding or other obfuscation techniques makes the server an easily identifiable target for automated scanning tools.
Exploiting Weak RDP Passwords and Default Credentials
Attackers frequently exploit weak or easily guessable passwords to gain unauthorized access to RDP-enabled systems. This can involve simple brute-force attacks, where automated tools try various password combinations until they find a match. The use of default credentials, such as the administrator account with a password like “password,” is particularly alarming, as this information is often publicly available. Furthermore, attackers often leverage leaked password databases obtained from previous data breaches to try and gain access to systems. A successful attack on a system with weak credentials can provide the attacker with complete control over the targeted machine, allowing them to steal sensitive data, install malware, or launch further attacks against other systems on the network.
Social Engineering Tactics for Obtaining RDP Access
Social engineering techniques are often employed to trick users into revealing their RDP credentials or enabling access. Phishing emails, for instance, might appear to be from a legitimate IT support team, requesting login credentials to troubleshoot a supposed system issue. Another tactic involves pretexting, where an attacker poses as a trusted individual or organization to gain the victim’s confidence and subsequently obtain RDP access. The attacker might claim to be from a bank, a government agency, or a software vendor, requesting remote access to “assist” the user with a problem. The success of these social engineering tactics hinges on the victim’s lack of awareness and caution. Once the attacker has obtained the credentials, they can easily gain access to the victim’s system through RDP.
Weaponized RDP Files
Getting hacked is never fun, especially when it involves Remote Desktop Protocol (RDP). While RDP is a legitimate tool for remote access, it’s also a favorite target for cybercriminals who weaponize it to gain control of your systems. This section dives into the sneaky ways malicious RDP files find their way onto your computer.
Phishing Email Campaigns: The Trojan Horse Approach
Phishing emails remain a highly effective delivery method for weaponized RDP files. These emails often masquerade as legitimate communications from banks, businesses, or even government agencies. They might contain a seemingly innocuous attachment labeled as an invoice, a shipping confirmation, or even a job application. Clicking on the attachment or following a link within the email can trigger the download and execution of a malicious RDP file, granting attackers unauthorized access to your system. The sophistication of these emails varies; some are crudely crafted, while others are incredibly convincing, making it difficult for even tech-savvy individuals to spot the red flags. For example, a well-crafted phishing email might use your name and other personal details obtained through data breaches, adding a layer of authenticity to the scam.
Malicious Links and Attachments: The Sneaky Download
Weaponized RDP files can be distributed through malicious links embedded in websites, emails, or even social media posts. These links often lead to seemingly harmless websites that actually download and install the malicious file without the user’s explicit knowledge. Alternatively, the malicious file might be disguised as a seemingly harmless attachment, such as a PDF document or a Word file, which, when opened, executes the hidden RDP payload. The user might be tricked into opening the attachment through a sense of urgency, curiosity, or a belief that the file is legitimate. A classic example is an email claiming a package delivery requires you to open an attached “tracking document” which is actually the malicious file.
Social Engineering Tactics: Playing on Human Psychology
Social engineering plays a crucial role in the success of weaponized RDP file delivery. Attackers exploit human psychology by leveraging tactics like urgency, fear, and authority. For example, an email might threaten account suspension unless a user clicks a link to “verify” their account. Alternatively, an attacker might pose as a tech support representative, claiming to need access to the user’s computer to fix a problem. The pressure created by these scenarios can lead users to overlook security warnings and execute the malicious RDP file without hesitation.
Delivery Methods Effectiveness Comparison
| Method | Effectiveness | Detection Difficulty | Mitigation Strategy |
|---|---|---|---|
| Phishing Emails with Attachments | High (especially with sophisticated social engineering) | Moderate (can be detected by email filters and antivirus software) | Employee training on phishing awareness, robust email filtering, and antivirus software. |
| Malicious Links | High (easy to disguise and difficult to detect) | High (requires advanced threat detection systems) | User education on safe browsing practices, URL scanning tools, and robust web security solutions. |
| Social Engineering (Phone calls, SMS) | High (relies on human error) | Very High (difficult to detect proactively) | Employee training on social engineering tactics, security awareness programs, and multi-factor authentication. |
| Drive-by Downloads (Compromised Websites) | Moderate (requires user to visit a compromised site) | Moderate (can be detected by web security solutions) | Regular security updates, web filtering, and use of reputable websites. |
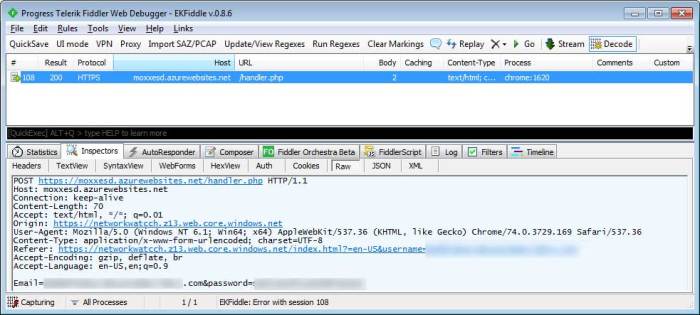
Analyzing the Malicious RDP File
Dissecting a weaponized RDP file requires a methodical approach, combining technical expertise with a keen eye for detail. Understanding the various malware families that can be delivered and the methods employed to establish persistence is crucial for effective analysis and mitigation. This process involves careful examination within a controlled environment to prevent infection of your own systems.
A weaponized RDP file isn’t just a simple Remote Desktop Protocol file; it’s a Trojan horse, often disguised as a legitimate file to trick unsuspecting users. The core threat lies in its ability to establish a backdoor connection, granting malicious actors unauthorized access to the victim’s system. This backdoor can be used for data theft, system manipulation, or as a stepping stone for further attacks. The types of malware delivered vary widely, ranging from simple keyloggers to sophisticated ransomware and botnet components.
Malware Delivered via Weaponized RDP Files
Weaponized RDP files can act as delivery mechanisms for a wide spectrum of malware. These range from relatively simple information stealers, capable of logging keystrokes and capturing screenshots, to highly complex malware capable of performing sophisticated actions like encrypting data (ransomware) or joining the victim’s machine to a botnet for distributed denial-of-service (DDoS) attacks. Examples include information stealers like Remcos, ransomware variants that leverage RDP access for wider network compromise, and various remote access Trojans (RATs) that provide persistent access to the infected system. The specific malware payload is highly dependent on the attacker’s goals.
Establishing a Backdoor Connection
A malicious RDP file typically achieves a backdoor connection by exploiting vulnerabilities in the victim’s system or by leveraging legitimate RDP functionality in a malicious manner. One common technique involves using a compromised RDP server or a server controlled by the attacker. Once the victim connects, the malicious code within the RDP file executes, establishing a persistent connection that allows the attacker to remotely control the system. This connection can be hidden through various techniques, making detection challenging. Another method involves exploiting vulnerabilities in the RDP client itself, allowing the attacker to inject malicious code directly into the running process.
Analyzing the File’s Behavior in a Sandboxed Environment
Analyzing a suspicious RDP file should always be performed in a carefully controlled environment, such as a virtual machine (VM) or a dedicated sandbox. This isolation prevents the malware from infecting your own systems. The analysis process typically involves monitoring the file’s behavior using various tools. Network traffic analysis will reveal any communication with external servers, indicating potential command-and-control (C&C) servers. Process monitoring will highlight the creation of new processes, registry modifications, and file system changes. Memory analysis can uncover malicious code injected into memory. Using a combination of these techniques provides a comprehensive picture of the file’s activities.
Reversing the Malicious RDP File
Reversing an RDP file requires specialized skills in reverse engineering. The process typically involves using disassemblers and debuggers to analyze the file’s code. The goal is to understand the file’s functionality, identify the malware payload, and determine how it establishes the backdoor connection. This step-by-step process might include: 1) Static analysis: Examining the file’s structure and code without execution. 2) Dynamic analysis: Running the file in a sandboxed environment and monitoring its behavior. 3) Identifying key functions: Pinpointing functions responsible for network communication, file system access, and registry modifications. 4) Decoding obfuscation techniques: Many malicious files employ obfuscation to hide their true functionality; reversing this requires significant expertise. 5) Reconstructing the attack chain: Understanding the sequence of events that lead to the establishment of the backdoor.
Malware Analysis Report Structure
A well-structured malware analysis report should provide clear and concise information about the analyzed file. A typical structure might include:
- File Information: File name, size, MD5/SHA hashes, creation date.
- Analysis Environment: Operating system, antivirus software used.
- Behavior: Detailed description of the file’s actions, including network connections, registry modifications, and file system changes.
- Malware Identification: Type of malware, family, and any known variants.
- Indicators of Compromise (IOCs): IP addresses, domain names, and file hashes associated with the malware.
- Mitigation Steps: Recommendations for removing the malware and preventing future infections.
Impact and Consequences of the Attack
A successful phishing attack leveraging a weaponized RDP file can have devastating consequences for individuals and organizations alike. The attacker gains unauthorized access, opening the door to a wide range of malicious activities, resulting in significant financial losses, reputational damage, and operational disruption. The severity of the impact depends on the sensitivity of the compromised data and the attacker’s objectives.
The initial breach, seemingly innocuous, can rapidly escalate into a major security incident. The compromised system becomes a foothold for further attacks, potentially compromising the entire network and exposing sensitive information to malicious actors.
Data Breaches and Theft
Once inside the system, attackers can access a variety of sensitive data. This could include confidential business documents, customer information (including Personally Identifiable Information or PII), financial records, intellectual property, and proprietary software. The stolen data can be used for identity theft, financial fraud, corporate espionage, or blackmail. The value of this stolen data can be immense, depending on its nature and the organization’s industry. For example, a stolen customer database containing credit card numbers could lead to significant financial losses and legal repercussions. The theft of intellectual property could cripple a company’s competitive advantage.
Network Compromise and Lateral Movement
Gaining access via a weaponized RDP file often allows attackers to move laterally within the network. This means they can use the compromised system as a springboard to access other systems, servers, and databases. This can lead to a widespread breach, affecting multiple parts of the organization’s IT infrastructure. Attackers might exploit vulnerabilities in other systems or use stolen credentials to gain access. The entire network could become compromised, potentially leading to a complete shutdown of operations.
Financial and Reputational Damage
The financial consequences of a successful attack can be substantial. This includes the direct costs of data recovery, system repair, legal fees, and regulatory fines. There are also indirect costs, such as lost productivity, business disruption, and damage to customer relationships. Furthermore, a data breach can severely damage an organization’s reputation, leading to loss of customer trust and potential decline in business. The negative publicity surrounding a security breach can have long-lasting effects on an organization’s brand image and financial performance. Stock prices can plummet, and investors may lose confidence.
Real-World Examples
Numerous real-world incidents demonstrate the devastating consequences of weaponized RDP file attacks. The NotPetya ransomware attack in 2017, while not directly caused by a phishing email with a weaponized RDP file, highlights the potential for widespread damage stemming from a single point of compromise. The attack, spread through a compromised accounting software update, crippled many organizations, causing billions of dollars in damages. Similarly, various large-scale data breaches have been linked to initial compromises via phishing campaigns and subsequent lateral movement within networks, resulting in the exposure of sensitive personal and financial information, leading to significant financial and reputational losses for the affected organizations. These examples underscore the critical need for robust security measures to prevent such attacks.
Mitigation and Prevention Strategies
Source: bleepstatic.com
Securing your systems against RDP phishing attacks requires a multi-layered approach, combining technical safeguards with robust security awareness training. Ignoring even one aspect can leave your organization vulnerable. Think of it like a castle – strong walls (technical security) are useless if the gatekeeper (your employees) is easily tricked.
Effective mitigation strategies focus on hardening RDP servers, educating users, and implementing robust monitoring systems. By combining these approaches, organizations can significantly reduce their risk of falling victim to these sophisticated attacks.
Strong Passwords and Multi-Factor Authentication
Implementing strong passwords and multi-factor authentication (MFA) is paramount. Weak passwords are easily guessed or cracked, making them a prime target for attackers. MFA adds an extra layer of security, requiring users to provide two or more forms of authentication, such as a password and a one-time code from a mobile app. This significantly increases the difficulty for attackers to gain unauthorized access, even if they manage to obtain a password. For example, even if an attacker obtains a user’s password through phishing, they’ll still be blocked without the second factor of authentication. Consider using password managers to help enforce strong, unique passwords across all accounts.
Network Segmentation and Access Control Lists, Phishing attack weaponized rdp file
Network segmentation divides your network into smaller, isolated segments. This limits the impact of a successful attack. If one segment is compromised, the attacker won’t have automatic access to the entire network. Access Control Lists (ACLs) further restrict access to RDP servers by only allowing connections from specific IP addresses or networks. This prevents unauthorized users from even attempting to connect, significantly reducing the attack surface. For instance, an ACL could restrict RDP access to only the internal network, preventing external connections unless specifically authorized through a VPN with appropriate security measures.
Intrusion Detection and Prevention Systems
Intrusion Detection and Prevention Systems (IDPS) monitor network traffic for malicious activity, such as brute-force attacks against RDP servers. An IDPS can detect suspicious login attempts and block them before they succeed. Furthermore, they can provide valuable insights into the types of attacks being attempted, allowing for proactive security improvements. A well-configured IDPS can act as an early warning system, alerting administrators to potential breaches and allowing for swift response. For example, an IDPS might flag a large number of failed login attempts from a single IP address, indicating a potential brute-force attack.
Security Awareness Training
Educating employees about the risks of phishing attacks is crucial. Security awareness training should cover various aspects of RDP security, including:
- Recognizing phishing emails and messages attempting to steal RDP credentials.
- Understanding the importance of strong passwords and MFA.
- Knowing how to report suspicious emails and activities.
- The dangers of clicking on unknown links or attachments.
- Best practices for securing personal devices used to access company resources.
Regular training sessions, combined with simulated phishing attacks, can significantly improve employee awareness and reduce the likelihood of successful phishing campaigns. A well-trained workforce is the first line of defense against these types of attacks.
Forensic Analysis and Incident Response: Phishing Attack Weaponized Rdp File
A successful RDP phishing attack requires a swift and thorough forensic investigation to minimize damage and prevent future incidents. This involves a multi-stage process, from identifying the attack vector to recovering compromised systems and documenting the entire event for future analysis and reporting. Effective incident response is crucial in limiting the impact of such attacks and strengthening an organization’s overall security posture.
The forensic investigation begins immediately upon detection of the attack. Speed is critical to limit the attacker’s access and prevent further compromise. This initial response phase should focus on isolating affected systems and preventing further propagation of the malware.
Identifying the Attack Source and Infrastructure
Determining the origin of the attack involves analyzing various logs and network traffic. This includes examining the compromised system’s event logs for suspicious activity, such as unusual login attempts, file modifications, or network connections. Network traffic analysis, using tools like Wireshark, can reveal the attacker’s IP address, communication patterns, and potentially the command-and-control (C2) server used to manage the compromised systems. Analyzing the malicious RDP file itself will also reveal valuable clues, such as embedded indicators of compromise (IOCs) or code signatures that can be used to identify the attacker’s tools and techniques. For example, identifying the specific malware variant used in the attack through hash analysis can help researchers understand the attack’s scope and potential impact.
Containing the Attack and Preventing Further Damage
Once the source is identified, the immediate priority shifts to containing the attack. This involves disconnecting the compromised systems from the network to prevent further lateral movement and data exfiltration. Disabling RDP access on all vulnerable systems is paramount. Implementing temporary firewall rules to block malicious IP addresses identified during the investigation is also a critical step. Furthermore, reviewing and updating security policies, particularly access control lists (ACLs) for RDP and other vulnerable services, is essential to prevent similar attacks in the future. This could involve implementing multi-factor authentication (MFA) for all RDP connections.
Recovering Compromised Systems and Restoring Data
System recovery involves a multi-step process. This starts with creating forensic images of the affected systems before any remediation is attempted. These images are crucial for later analysis. Next, the systems are cleaned of malware, often through a combination of antivirus software, manual malware removal, and operating system reinstallation. Data restoration follows, prioritizing critical data and utilizing backups where available. Verification of data integrity after restoration is crucial. In cases of severe compromise where data integrity is questionable, a more thorough review and potentially data reconstruction might be necessary. For instance, if the attacker encrypted sensitive data, a recovery plan involving decryption tools or professional data recovery services might be required.
Documenting the Incident
Meticulous documentation is essential for both internal analysis and external reporting. This includes a detailed chronology of events, the steps taken during the investigation and remediation, and a comprehensive list of all affected systems and data. A post-incident report should summarize the findings, including the root cause of the attack, the extent of the damage, and recommendations for preventing future incidents. This report serves as a valuable resource for future security improvements and incident response planning. Specific details about the attacker’s infrastructure, the malware used, and the techniques employed should be included. This information can be shared with relevant security information and event management (SIEM) systems and threat intelligence platforms to help improve overall security posture.
Last Word
Source: githubusercontent.com
So, the next time you see an email promising untold riches or a seemingly urgent request for remote access, think twice. Weaponized RDP files represent a serious threat, but understanding the mechanics of these attacks and implementing robust security measures can significantly reduce your risk. Remember, vigilance is your best defense. Stay informed, stay secure, and stay ahead of the digital curve. Because in the world of cybersecurity, complacency is a luxury you can’t afford.





