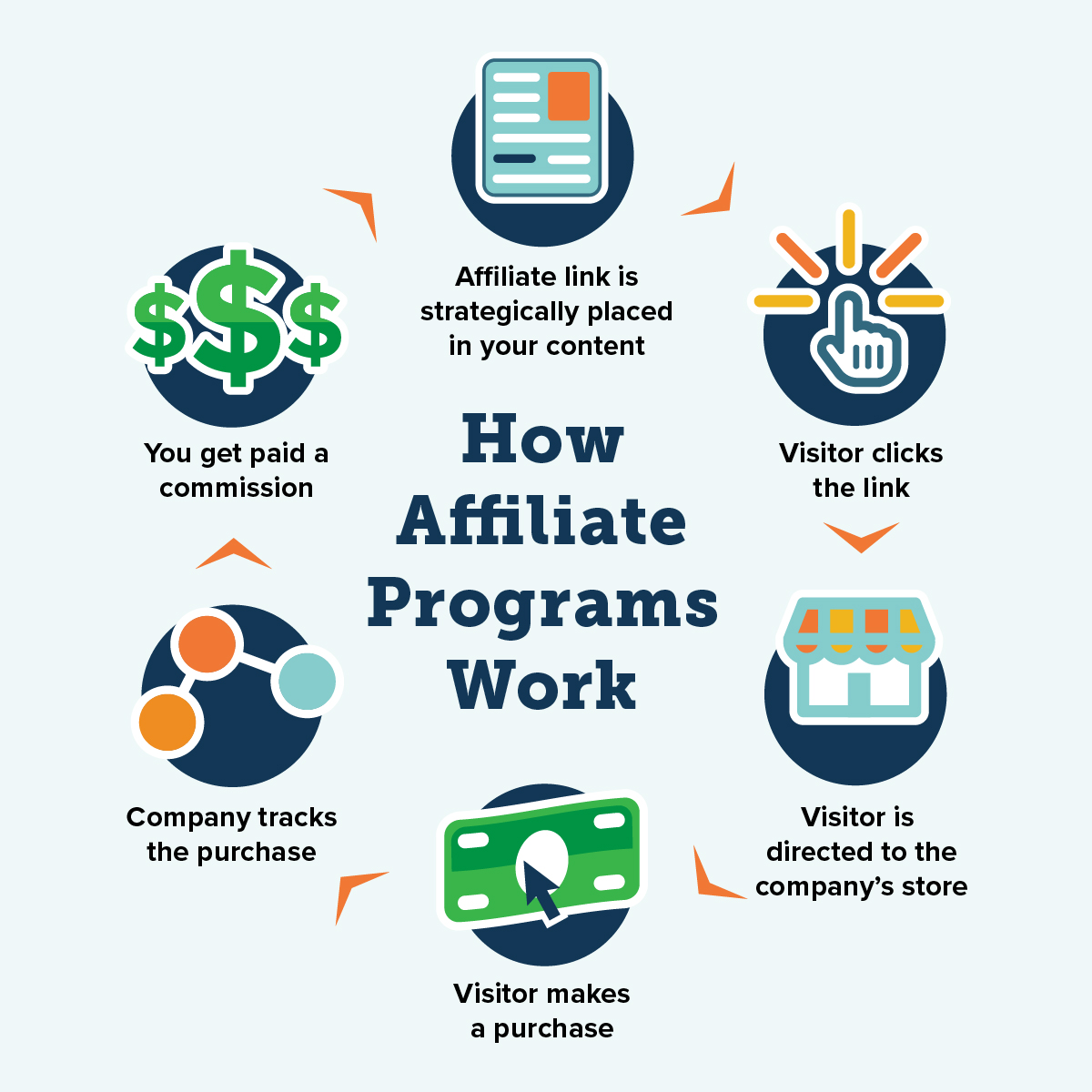
Welcome to the world of affiliate marketing consulting, where expertise meets opportunity! This dynamic field offers individuals and businesses the chance to maximize their revenue streams by leveraging partnerships and strategic collaborations. As the digital marketplace continues to evolve, understanding the intricacies of affiliate marketing becomes essential for thriving in today’s competitive landscape.
Through tailored strategies and comprehensive support, affiliate marketing consulting empowers clients to navigate challenges, optimize performance, and achieve sustainable growth. From crafting compelling campaigns to analyzing market trends, the role of a consultant is pivotal in driving success and unlocking the full potential of affiliate programs.
Are you ready to take your fitness journey to the next level? With our state-of-the-art Fitness Tracker, you can transform your health and wellness routine into a seamless and effective experience. Say goodbye to guesswork and hello to a healthier, more active lifestyle!
Your Personal Trainer on Your Wrist
Our Fitness Tracker is not just a gadget; it’s your personal trainer, calorie counter, and motivation booster all in one. Designed with cutting-edge technology, it tracks your steps, calories burned, heart rate, and even your sleep patterns. Whether you’re an avid athlete or just starting your fitness journey, this device adapts to your needs, providing you with real-time feedback and insights.
Key Features That Set Us Apart
- Accurate Activity Tracking: Track your daily activities with precision. Our advanced sensors ensure that every step you take is counted.
- Heart Rate Monitoring: Stay informed about your heart health with continuous heart rate tracking. Optimize your workouts and ensure you’re in the right zone.
- Sleep Analysis: Understand your sleep patterns to wake up refreshed. Our tracker monitors your sleep stages and gives you tips for better rest.
- Water-Resistant Design: Splash-proof and ready for any adventure! Whether you’re swimming, jogging in the rain, or sweating it out at the gym, our tracker withstands it all.
- Long Battery Life: Keep moving without interruptions. Enjoy up to 10 days of battery life on a single charge.
- Smart Notifications: Stay connected even while you train. Receive calls, texts, and app notifications directly on your wrist.
Stylish and Comfortable
Who says fitness trackers can’t be stylish? Our sleek and modern design ensures that you look great while keeping track of your fitness goals. Available in various colors and adjustable sizes, you can find the perfect fit that complements your style. Whether you’re at the office, gym, or out with friends, it seamlessly blends into every setting.
Empower Your Fitness Journey
Join thousands of satisfied customers who have transformed their lives with our Fitness Tracker. No matter your fitness level, this device empowers you to set goals, track progress, and celebrate achievements. It’s not just about the destination; it’s about enjoying the journey and every step along the way.
Exclusive Offer: Don’t Miss Out!
Ready to make a change? For a limited time, we’re offering an exclusive discount for our first-time buyers. When you purchase your Fitness Tracker today, you’ll receive 20% off the retail price! Plus, enjoy free shipping on all orders. This is your chance to invest in your health and wellbeing without breaking the bank.
How to Get Started
Getting started with our Fitness Tracker is quick and easy! Simply follow these steps:
- Visit our website and choose your favorite color and size.
- Complete the checkout process and look out for your order confirmation email.
- Once your Fitness Tracker arrives, download our user-friendly app to sync your device.
- Set your fitness goals and let the tracker guide you every step of the way!
Join Our Community
When you purchase our Fitness Tracker, you’re not just buying a product; you’re joining a community! Connect with fellow fitness enthusiasts on our online platform where you can share tips, challenges, and successes. Participate in monthly challenges for a chance to win exciting prizes and keep the motivation high!
Customer Testimonials
Don’t just take our word for it! Here’s what some of our customers have to say:
“The Fitness Tracker has completely changed my approach to fitness! I can now track my workouts and sleep without any hassle. Highly recommend!”
-Sarah W.
“I love the sleek design and how comfortable it feels on my wrist. Plus, the insights are incredibly helpful!”
-Mike R.
Your Health Matters
In today’s fast-paced world, it’s easy to neglect your health. Our Fitness Tracker serves as a gentle reminder to prioritize your well-being. With every notification and alert, you’ll be encouraged to move, stay active, and monitor your health metrics.
Conclusion: Invest in Yourself
Are you ready to make a commitment to your health? Don’t let another day pass by without taking action. Invest in yourself and your future with our Fitness Tracker. Experience the difference it makes in your daily routine and watch as you achieve your fitness goals like never before. Order now and take the first step towards a healthier lifestyle!
Frequently Asked Questions
1. Is the Fitness Tracker compatible with both Android and iOS devices?
Absolutely! Our Fitness Tracker is designed to work seamlessly with both Android and iOS smartphones. Download the app and get started!
2. Can I swim with the Fitness Tracker?
Yes, our tracker is water-resistant, making it suitable for swimming and other water activities.
3. How do I charge the Fitness Tracker?
Charging is simple! Use the included USB cable to connect it to any USB power source. A full charge takes about 2 hours.
4. What kind of warranty does the Fitness Tracker come with?
We offer a one-year warranty that covers manufacturing defects. Your satisfaction is our top priority!
5. Can I customize my goals in the app?
Yes! The app allows you to set personalized fitness goals based on your specific needs and lifestyle.
Questions and Answers
What is affiliate marketing consulting?

Affiliate marketing consulting involves providing expert advice and strategies to help businesses effectively implement and manage their affiliate marketing programs.
How can affiliate marketing consulting benefit my business?
It can optimize your marketing efforts, increase revenue, and improve partnerships with affiliates through tailored strategies and insights.
Is affiliate marketing consulting only for large businesses?

No, businesses of all sizes can benefit from affiliate marketing consulting, as it helps in maximizing ROI regardless of scale.
How do I choose the right affiliate marketing consultant?
Look for experience, proven success stories, and a clear understanding of your industry and target market.
What trends should I watch in affiliate marketing?
Monitoring AI integration, influencer partnerships, and evolving consumer behaviors can provide valuable insights into future strategies.