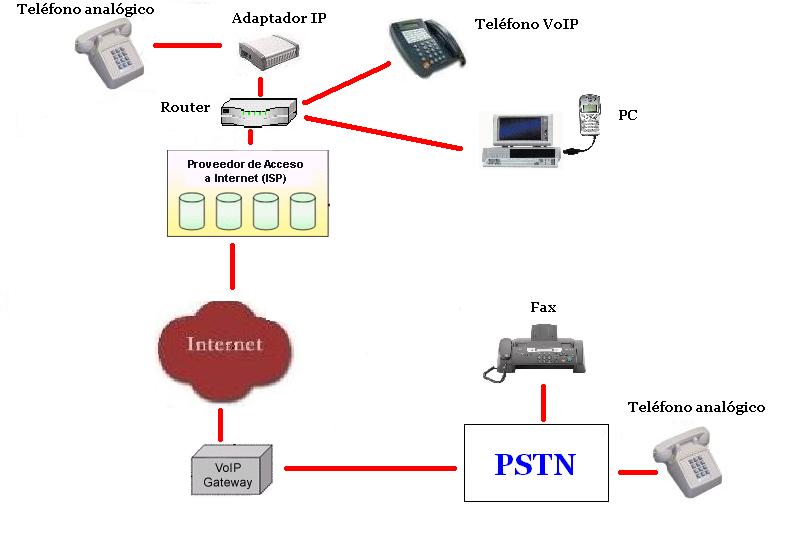
Step into the world of limitless possibilities with the best affiliate marketing software that can skyrocket your online business. Imagine harnessing the power of cutting-edge technology to optimize your affiliate strategies and boost your earnings effortlessly. This software is not just a tool; it’s your partner in navigating the dynamic landscape of digital marketing, ensuring you stay ahead of the competition.

From tracking your performance to managing campaigns seamlessly, the best affiliate marketing software offers a suite of features designed to enhance your efficiency. Whether you are just starting or looking to elevate your current strategies, this software adapts to your needs, providing insights that turn challenges into opportunities.
Are you ready to elevate your skincare routine to the next level? Introducing our revolutionary Ultimate Hydration Serum, the must-have product for anyone seeking radiant, youthful skin. Packed with powerful ingredients, this serum is designed to hydrate, nourish, and rejuvenate your complexion, leaving you with a healthy glow.

Why Choose the Ultimate Hydration Serum?
In today’s fast-paced world, your skin needs all the help it can get. Our Ultimate Hydration Serum is formulated with advanced technology and natural extracts that work synergistically to deliver unparalleled hydration. Here’s why this product stands out:
- Intense Hydration: Infused with hyaluronic acid, this serum attracts moisture to your skin, providing deep hydration that lasts all day.
- Revitalizing Ingredients: With a blend of vitamins C and E, our serum not only hydrates but also brightens and protects your skin from environmental damage.
- Lightweight Formula: The non-greasy texture absorbs quickly, making it suitable for all skin types, including oily and combination skin.
- Clinically Proven Results: Dermatologically tested, our serum has shown significant improvements in skin texture and hydration levels in just two weeks of use.
Key Ingredients That Transform Your Skin
What makes the Ultimate Hydration Serum truly unique is its powerful blend of ingredients:
1. Hyaluronic Acid
This superhero ingredient can hold up to 1000 times its weight in water, making it an essential component for maintaining skin elasticity and moisture.
2. Vitamin C
A potent antioxidant, Vitamin C brightens your complexion, reduces dark spots, and helps combat the signs of aging by promoting collagen production.
3. Vitamin E
This nourishing vitamin helps to protect skin cells from damage caused by free radicals, while also providing deep hydration and promoting healing.
4. Green Tea Extract
Rich in antioxidants, green tea extract soothes the skin and reduces inflammation, giving your complexion a calm and refreshed look.
How to Use Ultimate Hydration Serum
Incorporating our serum into your daily skincare routine is a breeze. Follow these simple steps for best results:
- Start with a clean face: Use your favorite cleanser to remove dirt and impurities.
- Apply toner: A toner will help prepare your skin to absorb the serum better.
- Dispense 2-3 drops of the serum: Gently massage the serum onto your face and neck using upward motions.
- Follow with moisturizer: Lock in all the hydration by applying your favorite moisturizer on top.
- Use morning and night: For optimal results, use the serum twice daily.
Real Results from Real Users
Don’t just take our word for it! Here’s what our customers have to say about the Ultimate Hydration Serum:

“I’ve tried countless serums, but this one is a game-changer. My skin feels plumper and looks so much more radiant!” – Sarah M.
“Finally, a serum that delivers on its promises. I’ve noticed a significant difference in my skin texture and hydration levels!” – James R.
“I love the lightweight formula! It absorbs quickly and leaves my skin feeling refreshed without any oily residue.” – Emily T.
Perfect for All Skin Types
Whether you have dry, oily, or combination skin, the Ultimate Hydration Serum is designed to meet your needs. Its lightweight texture makes it ideal for layering under makeup, while its deeply nourishing properties work wonders for dry or dehydrated skin. Experience the difference for yourself!
Why Hydration Matters
Proper hydration is the foundation of healthy skin. Dehydrated skin can lead to a range of issues, including dullness, fine lines, and increased sensitivity. By incorporating our Ultimate Hydration Serum into your daily routine, you’re taking a crucial step towards achieving the luminous skin you’ve always dreamed of.
Where to Buy
Ready to transform your skin? The Ultimate Hydration Serum is available exclusively on our website and select retailers. Don’t miss your chance to experience the hydration boost your skin craves. Visit our website today to place your order, and enjoy free shipping on your first purchase!
Join the Skincare Revolution
Our mission is to empower everyone to achieve their best skin. By choosing the Ultimate Hydration Serum, you’re not just investing in a product; you’re embracing a lifestyle of self-care and confidence. Say goodbye to lackluster skin and hello to a vibrant, youthful complexion!
FAQs
We know you might have questions! Here are some frequently asked questions about the Ultimate Hydration Serum:
1. Can I use the serum under makeup?
Absolutely! The lightweight formula absorbs quickly and provides a perfect base for makeup.
2. How soon can I expect to see results?
Many of our users experience noticeable improvements in hydration and skin texture within two weeks of regular use.
3. Is this serum suitable for sensitive skin?
Yes! Our serum is formulated with gentle, skin-friendly ingredients that are safe for sensitive skin types.
4. Can I use this serum alongside other skincare products?
Definitely! The Ultimate Hydration Serum works well with your existing skincare products. Just make sure to apply it after cleansing and toning.
Final Thoughts
Don’t wait any longer to unlock your skin’s full potential! The Ultimate Hydration Serum is your ticket to achieving a radiant, hydrated complexion. With its powerful blend of ingredients and proven results, it’s no surprise that this serum is a favorite among skincare enthusiasts. Order now and step into a world of luminous beauty!
FAQs
What is affiliate marketing software?
Affiliate marketing software is a tool that helps businesses manage their affiliate programs, including tracking sales, managing affiliates, and optimizing marketing strategies.
How do I choose the best affiliate marketing software?
Consider factors such as features, ease of use, integration capabilities, customer support, and pricing when selecting the best software for your needs.
Can I use affiliate marketing software with my existing website?
Yes, most affiliate marketing software can easily integrate with popular website platforms, including WordPress, allowing you to enhance your marketing efforts.
Is affiliate marketing software suitable for beginners?
Absolutely! Many affiliate marketing software options are user-friendly and designed to help beginners successfully launch and manage their affiliate programs.
What features should I look for in affiliate marketing software?
Key features to look for include tracking and reporting, affiliate management, payment processing, and marketing automation capabilities.