Step into the future with smart home internet, where technology seamlessly weaves into your daily life, making homes more connected and efficient than ever before. Imagine a world where your devices communicate effortlessly, enhancing convenience, security, and energy efficiency.
Smart home internet serves as the backbone for devices ranging from smart speakers to security cameras, all designed to work in harmony. This ecosystem not only simplifies tasks but also empowers users with control at their fingertips, ensuring a smarter, safer, and more enjoyable living environment.
Are you tired of feeling overwhelmed by your daily tasks? Do you wish you could find a way to organize your life and work more efficiently? Look no further! Introducing the Ultimate Productivity Toolkit – your one-stop solution for enhancing productivity, boosting motivation, and achieving your goals like never before!
What’s Inside the Ultimate Productivity Toolkit?
The Ultimate Productivity Toolkit is designed for busy professionals, students, and anyone looking to maximize their time and efforts. This comprehensive set of tools includes:
- Smart Planner: A beautifully designed planner that helps you map out your day, set priorities, and track progress.
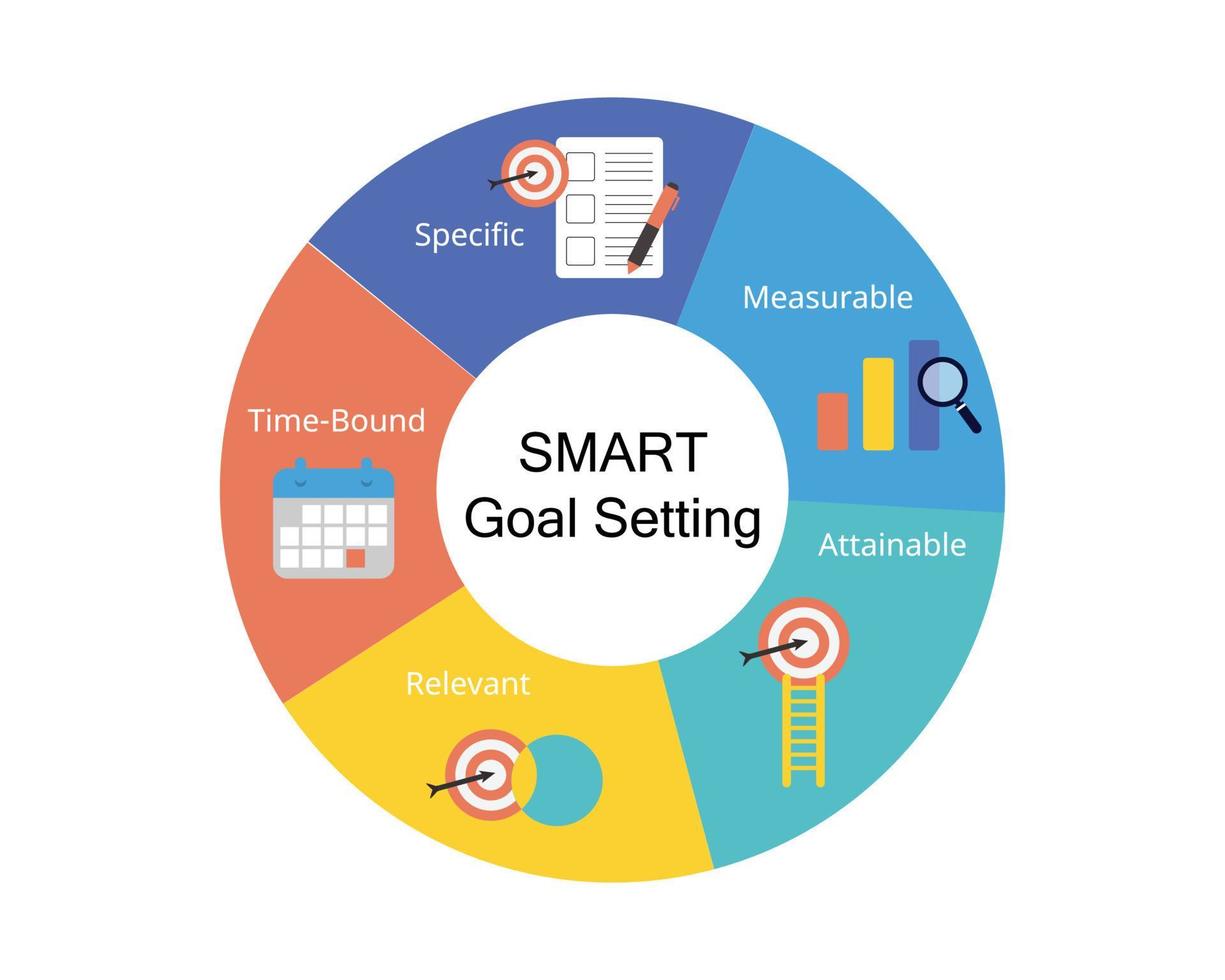
- Goal Setting Workbook: A step-by-step guide to help you define and achieve your short-term and long-term goals.
- Time Management App: Your digital assistant that reminds you of deadlines, schedules your tasks, and helps you stay on track.
- Mindfulness Guide: Techniques and practices to reduce stress and enhance focus, perfect for maintaining balance in a hectic world.
- Exclusive Community Access: Join a group of like-minded individuals where you can share tips, seek advice, and stay motivated.
Why Choose the Ultimate Productivity Toolkit?
In today’s fast-paced world, it’s easy to feel lost in the chaos of everyday life. The Ultimate Productivity Toolkit stands out for several reasons:
- Comprehensive Approach: We combine physical and digital tools for a holistic approach to productivity.
- User-Friendly Design: Our planner and workbook are designed with you in mind, making it easy to use and integrate into your daily routine.
- Proven Techniques: Each component is based on research-backed strategies that have been proven to enhance productivity.
- Support System: With access to our community, you’ll never feel alone on your journey to success.
Transform Your Productivity Today!
Imagine waking up each day feeling organized and empowered. The Ultimate Productivity Toolkit is here to turn that vision into reality! Our satisfied customers have experienced:
- Increased efficiency in completing tasks.
- Greater clarity in setting and achieving goals.
- Improved work-life balance with mindfulness practices.
- Stronger connections and support from a community of peers.
Don’t just take our word for it! Here’s what some of our happy customers have to say:
“I’ve tried countless productivity systems, but the Ultimate Productivity Toolkit is the only one that has worked for me. I’m more organized and focused than ever!” – Sarah L.
“The goal-setting workbook transformed my approach to achieving my dreams. I can’t thank the Ultimate Productivity Toolkit enough!” – James T.
How to Get Started!
Getting started with the Ultimate Productivity Toolkit is simple! Here’s how you can transform your life today:
- Visit Our Website: Go to our official website and explore the Ultimate Productivity Toolkit.
- Choose Your Package: Select the package that best fits your needs – we offer various options tailored for different lifestyles.
- Place Your Order: Follow the easy checkout process and make your purchase.
- Receive Your Toolkit: Get ready to receive your toolkit at your doorstep!
- Start Your Journey: Dive into the resources and join our community to kickstart your productivity journey!
Limited Time Offer!
Don’t wait! For a limited time only, we’re offering an exclusive discount on the Ultimate Productivity Toolkit. Use promo code PRODUCE20 at checkout to receive 20% off your purchase! This is your chance to invest in yourself and unlock your potential.
Frequently Asked Questions
1. Can I use the toolkit if I’m a student?
Absolutely! The Ultimate Productivity Toolkit is perfect for students looking to manage their time effectively and achieve academic success.
2. Is there a money-back guarantee?
Yes! We stand behind our product and offer a 30-day money-back guarantee. If you’re not satisfied, just let us know, and we’ll refund your purchase.
3. How do I access the community?
Once you purchase the toolkit, you’ll receive an email invitation to join our exclusive online community where you can connect with others.
4. Can I use the time management app on multiple devices?
Yes! The time management app is compatible with all your devices so you can stay organized on-the-go!
Get Your Toolkit Now!
The time to take control of your life is now! Stop letting disorganization and chaos rule your day-to-day activities. Invest in the Ultimate Productivity Toolkit and watch as your efficiency skyrockets, and your goals become attainable! Click the link below to start your journey towards a more productive life!
Order Your Ultimate Productivity Toolkit Today!
Conclusion
The Ultimate Productivity Toolkit is not just a product; it’s a lifestyle change. Embrace the power of organization, motivation, and community support as you embark on your journey to success. Whether you’re a busy professional, a student, or simply someone looking to improve their productivity, this toolkit is for you. Don’t miss out on the opportunity to unlock your potential – order yours today!
Q&A
What is smart home internet?
Smart home internet refers to high-speed internet connections that enable various smart devices to communicate and function effectively within a home.
How does smart home internet improve security?
It allows for the integration of security cameras, smart locks, and alarm systems, providing real-time monitoring and alerts.
Can I control my smart home devices remotely?
Yes, smart home internet allows users to control devices remotely through mobile apps or voice assistants from anywhere.
What are the benefits of having a smart home?
Benefits include energy savings, enhanced security, increased convenience, and improved home management.
Is installing smart home internet easy?
Most installations are straightforward, often requiring just a router and compatible devices, with many options available for DIY setups.