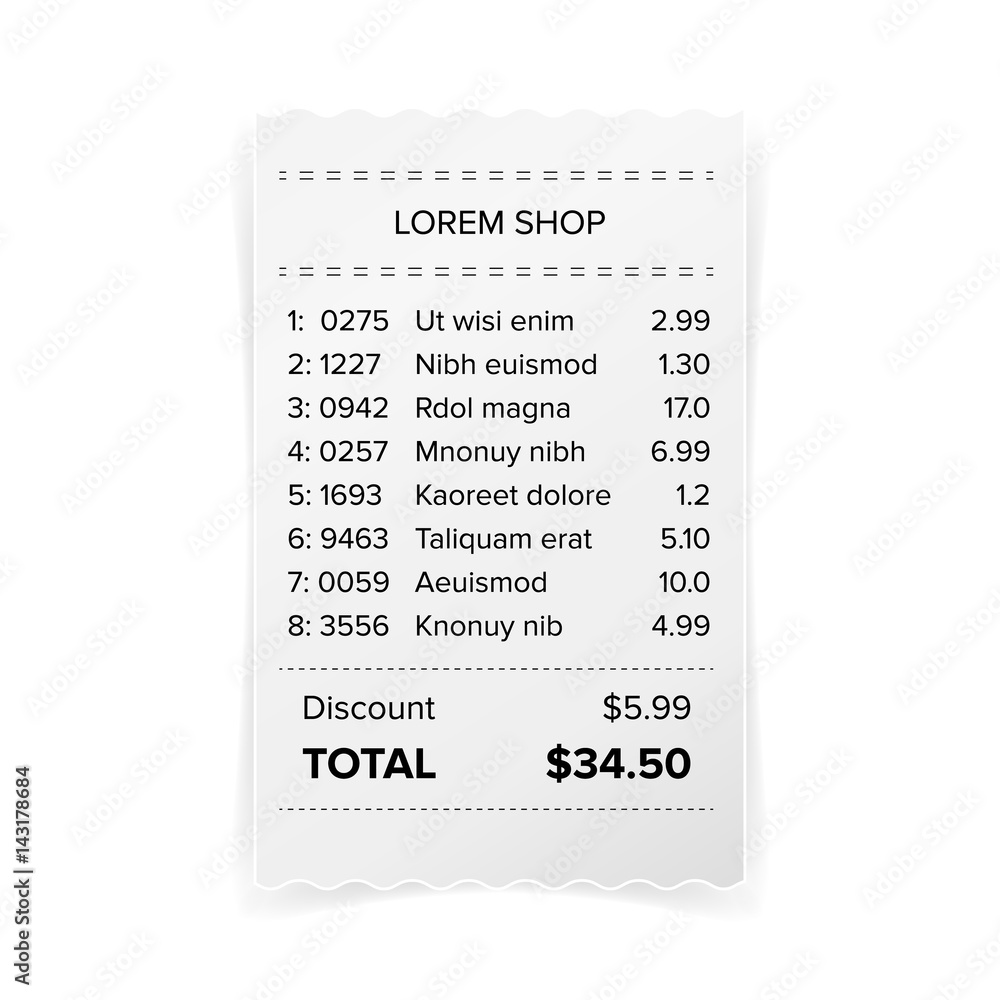
Bill approval software revolutionizes the way businesses manage their financial processes, ensuring swift approvals and seamless transactions. By automating the approval workflow, companies can enhance accuracy, reduce delays, and maintain clear records of all financial activities.
This powerful tool is designed for efficiency, offering features that cater to the specific needs of organizations aiming to optimize their billing processes. With user-friendly interfaces and robust tracking systems, bill approval software not only simplifies the approval chain but also enhances transparency and accountability.

Are restless nights stealing your peace? Wake up feeling refreshed and rejuvenated with our premium luxury mattress, designed specifically to enhance your sleep experience. Imagine sinking into a world of plush comfort every night—our mattress does just that!
The Science of Sleep
Research shows that quality sleep is essential for overall health, and choosing the right mattress is a crucial factor in achieving that elusive slumber. Our luxury mattress is crafted to provide optimal support for your body, aligning your spine and reducing pressure points. Say goodbye to tossing and turning, and hello to a night filled with uninterrupted, restorative sleep!
Unparalleled Comfort
Our mattress features a unique combination of high-density memory foam and advanced pocket spring technology. This premium construction allows the mattress to contour to your body’s shape, providing personalized support while also promoting airflow. No more overheating or discomfort while you sleep; our luxury mattress keeps you cool and comfortable throughout the night!
Quality Materials for Quality Sleep
We understand that the materials you choose are just as important as the technology behind them. Our luxury mattress is made with eco-friendly, hypoallergenic materials that not only feel good against the skin but are also kind to the environment. Each layer of our mattress is designed to provide you with a combination of softness and durability, ensuring it stands the test of time.
Health Benefits You Can Feel
A good night’s sleep is more than just a luxury; it’s an investment in your health! With our luxury mattress, you can experience:
- Improved Sleep Quality: Say goodbye to restless nights and hello to deep, uninterrupted sleep.
- Reduced Back Pain: Our ergonomic design provides the support your back needs for a pain-free morning.
- Allergy Relief: Our hypoallergenic materials repel dust mites and allergens, creating a healthier sleep environment.
- Enhanced Energy Levels: Wake up feeling revitalized and ready to tackle the day ahead.
Customer Testimonials
Don’t just take our word for it! Here’s what our satisfied customers are saying about their experience:
“I never knew how much a mattress could change my sleep! I wake up feeling like a new person!” – Sarah T.
“The support is incredible! My back pain has significantly reduced since I started using this mattress.” – John K.
Affordable Luxury
We believe that everyone deserves to experience the luxury of a good night’s sleep without breaking the bank. That’s why we offer our premium luxury mattress at an affordable price. Plus, with our special discounts and financing options, investing in your sleep has never been easier!
Risk-Free Trial
We are so confident in our product that we offer a 100-night risk-free trial. Sleep on our mattress for 100 nights, and if you’re not completely satisfied, return it hassle-free! Experience the luxury for yourself, risk-free!
Easy Delivery & Setup
Say goodbye to the hassle of shopping in-store! Our luxury mattress is delivered directly to your doorstep in a convenient, compact box. Unpack it, let it expand, and within moments, you’ll be ready to enjoy the comfort of your new mattress. We also provide easy-to-follow setup instructions, ensuring a smooth transition to better sleep.
Join the Sleep Revolution
Tired of waking up feeling groggy? Ready to transform your sleep experience? Join the revolution and invest in our luxury mattress today! Your body deserves the best, and with our luxury mattress, you can achieve the restorative sleep you’ve always dreamed of.
Special Offer: Limited Time Only!
For a limited time, we’re offering an exclusive discount for our online customers. Order now and receive 20% off your luxury mattress plus free shipping! Don’t miss out on this amazing opportunity to elevate your sleep experience.
Contact Us Today!
If you have any questions or need assistance with your order, our friendly customer service team is here to help! Reach out to us via email or phone, and we’ll be happy to assist you.
Conclusion: Invest in Your Sleep
Your sleep is precious, and it’s time to treat it as such! With our luxury mattress, you can experience the comfort and support you need for a night of restful sleep. Don’t wait any longer; invest in your sleep today and wake up feeling your best!
Remember, quality sleep isn’t just a dream—it’s a reality waiting for you!
Answers to Common Questions
What features should I look for in bill approval software?
Key features include automated workflows, real-time tracking, user permissions, and integration capabilities with existing financial systems.
How does bill approval software enhance productivity?
By streamlining the approval process, it reduces the time spent on manual tasks, allowing teams to focus on more strategic initiatives.
Is it easy to implement bill approval software?
Most bill approval software solutions are designed for easy integration and come with support to help with the implementation process.
Can bill approval software help in compliance?
Yes, it helps maintain records and provides an audit trail, ensuring compliance with financial regulations and company policies.
What is the cost range for bill approval software?
The cost can vary widely based on features and the size of the organization, typically ranging from $10 to $100 per user per month.