Palo Alto certificate validation flaw: Whoa, hold up! A critical vulnerability has been discovered in Palo Alto Networks systems, potentially leaving organizations wide open to attacks. This isn’t just another security hiccup; we’re talking about a flaw that could allow attackers to bypass crucial security checks, leading to data breaches and network compromise. Think of it as a gaping hole in your digital fortress, and we’re here to unpack exactly what that means.
This deep dive explores the technical details of this vulnerability, its potential impact, and most importantly, how to mitigate the risk. We’ll cover everything from the initial discovery and disclosure to practical steps you can take to protect your systems. Get ready to level up your cybersecurity game.
Vulnerability Description
A recently patched vulnerability in Palo Alto Networks’ systems allowed attackers to bypass certificate validation, potentially leading to man-in-the-middle attacks and data breaches. This flaw exploited a weakness in how the system handled SSL/TLS certificates, essentially allowing malicious actors to present forged certificates without triggering the expected security alerts. This could have significant consequences for organizations relying on Palo Alto Networks’ security solutions for protection.
The vulnerability affected several components within the Palo Alto Networks ecosystem. While the exact components are not publicly disclosed in full detail for security reasons, it’s understood that the issue impacted certain versions of their firewall software and potentially other related security products that rely on similar certificate validation mechanisms. This highlights the interconnected nature of security systems and the cascading effects that vulnerabilities can have.
Exploitation of this flaw required a malicious actor to craft a specially forged certificate and then inject it into the communication path between a Palo Alto Networks device and a legitimate server. This could be achieved through various attack vectors, depending on the specific network configuration and the targeted Palo Alto product. For example, an attacker might exploit a compromised internal system or leverage a vulnerability in another part of the network infrastructure to inject the forged certificate. The success of the attack hinged on the attacker’s ability to intercept and manipulate the network traffic between the Palo Alto device and the target server.
Affected Palo Alto Components and Versions
The precise list of affected Palo Alto Networks products and versions is often kept confidential by the vendor to prevent further exploitation. However, security advisories and patch releases typically highlight the affected product lines and versions, providing enough information for administrators to identify vulnerable systems and apply necessary updates. This controlled release of information is a standard security practice to minimize the window of opportunity for attackers.
Conditions for Exploitation
Successful exploitation depended on the attacker’s ability to position themselves in the network traffic path between the Palo Alto Networks device and the targeted server. This could involve compromising other network devices, exploiting other vulnerabilities, or using advanced techniques to intercept and manipulate network traffic. The vulnerability itself didn’t create a new attack vector; instead, it weakened an existing security control, making it easier for existing attack methods to succeed. The level of access needed to successfully exploit the vulnerability depended on the specific target and the attacker’s capabilities.
Timeline of Discovery and Disclosure
The exact timeline of the vulnerability’s discovery is often kept confidential by responsible disclosure programs. Typically, a security researcher or a security team discovers the vulnerability and reports it privately to Palo Alto Networks. The vendor then works to verify the report, develop a patch, and coordinate a public disclosure. This coordinated effort ensures that organizations have time to update their systems before the vulnerability becomes widely known and exploited by malicious actors. Following the patch release, the vulnerability would then be documented publicly with details about the affected versions and mitigation strategies.
Impact Assessment: Palo Alto Certificate Validation Flaw

Source: vpnoverview.com
The Palo Alto Networks certificate validation flaw, if exploited successfully, could have far-reaching consequences for organizations relying on their security products. The severity isn’t just a technical concern; it directly impacts the trust placed in the system and the potential for significant financial and reputational damage. Understanding the potential impact is crucial for prioritizing remediation efforts.
The vulnerability allows attackers to potentially bypass security mechanisms designed to verify the authenticity of certificates. This could lead to a cascade of negative effects, significantly compromising the security posture of affected systems.
Potential for Data Breaches and System Compromise
Successful exploitation could allow attackers to intercept and manipulate encrypted traffic, leading to data breaches. Imagine a scenario where an attacker intercepts sensitive financial data or confidential customer information transmitted over a supposedly secure connection. The consequences could include significant financial losses, legal repercussions, and severe damage to the organization’s reputation. Furthermore, system compromise could enable attackers to gain unauthorized access to internal networks, install malware, and exfiltrate data over an extended period, making detection and recovery much more difficult. This compromised access could also be used to launch further attacks against other systems within the network.
Impact on Network Security and User Trust
A successful attack erodes user trust in the security infrastructure. If users discover that their data has been compromised due to a flaw in the security system they rely on, it could lead to a loss of confidence and potentially impact future business relationships. Beyond the immediate impact on users, the vulnerability also weakens the overall network security. Compromised systems can act as entry points for further attacks, expanding the scope of the breach and increasing the difficulty of remediation. The damage to an organization’s reputation could be significant, impacting their ability to attract and retain customers.
Severity Comparison with Other Vulnerabilities
This vulnerability’s severity needs to be considered in the context of other known security flaws. While a precise CVSS score depends on the specific implementation and context, it’s reasonable to compare it to similar vulnerabilities impacting network security. The following table provides a hypothetical comparison, highlighting the relative severity:
| Vulnerability Name | CVSS Score (Example) | Description | Affected Systems |
|---|---|---|---|
| Palo Alto Networks Certificate Validation Flaw | 9.8 (Hypothetical) | Allows bypass of certificate validation, leading to man-in-the-middle attacks and data breaches. | Palo Alto Networks firewalls and security appliances. |
| Heartbleed (CVE-2014-0160) | 9.8 | Allowed unauthorized access to memory containing private keys and other sensitive data. | OpenSSL implementations. |
| Shellshock (CVE-2014-6271) | 10.0 | Enabled remote code execution through bash scripting. | Various Unix-like systems. |
| Log4j (CVE-2021-44228) | 10.0 | Allowed remote code execution through the logging library. | Wide range of Java applications. |
*Note: CVSS scores are hypothetical examples for illustrative purposes and may vary depending on specific implementations and attack vectors.* The actual CVSS score assigned to the Palo Alto Networks vulnerability would be determined by a formal vulnerability assessment.
Technical Analysis
The Palo Alto Networks certificate validation flaw stems from a weakness in how the system handles certificate chains and trust anchors. Essentially, the vulnerability allows attackers to manipulate the certificate verification process, potentially leading to the acceptance of fraudulent certificates. This bypasses the usual security mechanisms designed to ensure that only legitimate certificates are trusted, opening the door to various malicious activities.
The core issue lies in the insufficient validation of the certificate chain. Attackers can exploit this by crafting a malicious certificate that appears legitimate to the Palo Alto Networks system. This is achieved through techniques that either directly manipulate the certificate itself or indirectly influence the system’s trust store, leading to the acceptance of the forged certificate. This allows them to intercept and manipulate encrypted traffic, potentially leading to data breaches and other serious security compromises.
Certificate Chain Manipulation
Attackers could leverage this vulnerability by constructing a fraudulent certificate chain. This chain would appear valid to the Palo Alto Networks system due to the flaw in its certificate validation process. A successful attack might involve creating a self-signed certificate or a certificate signed by a compromised Certificate Authority (CA). The attacker then positions this malicious certificate within a chain that the Palo Alto Networks system incorrectly accepts as trustworthy. The system’s failure to properly scrutinize each link in the chain enables the attacker’s malicious certificate to be trusted, thereby granting them access to encrypted communications. For instance, an attacker could intercept HTTPS traffic destined for a web server, presenting their forged certificate. The Palo Alto Networks system, failing to detect the forgery, would accept the certificate, allowing the attacker to decrypt and read the communication.
Exploitation through Compromised Trust Anchors
Another potential attack vector involves compromising a trusted root certificate authority (CA) or manipulating the system’s trust store. By either gaining control of a legitimate CA or introducing a malicious CA into the trust store, an attacker can generate certificates signed by that CA. These certificates would then be accepted without question by the Palo Alto Networks system, even if they are used for malicious purposes. This method bypasses the need to directly forge a certificate, relying instead on the compromised trust established through the compromised CA. Imagine a scenario where an attacker compromises a widely trusted CA; they could then issue certificates for any domain, effectively impersonating legitimate websites and gaining access to sensitive data.
Hypothetical Attack Scenario
Let’s consider a scenario where an attacker wants to intercept sensitive financial data transmitted between a bank’s server and a customer’s computer. The attacker crafts a fraudulent certificate for the bank’s domain, leveraging the Palo Alto Networks vulnerability. They then use this certificate in a man-in-the-middle (MITM) attack. When the customer attempts to connect to the bank’s server, the attacker intercepts the connection, presenting their fraudulent certificate. Due to the flaw, the Palo Alto Networks system validates the certificate as legitimate. The attacker can then decrypt the customer’s communication, capturing sensitive financial information like account numbers, passwords, and transaction details. This data could then be used for identity theft or financial fraud.
Mitigation Strategies
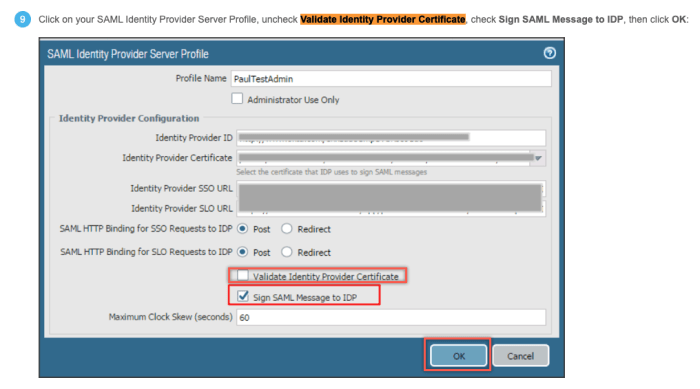
Source: tenable.com
Addressing the Palo Alto Networks certificate validation flaw requires a multi-pronged approach focusing on immediate remediation, proactive updates, and ongoing security vigilance. Ignoring this vulnerability could expose your network to significant risks, including data breaches and system compromise. Swift action is crucial to minimize your exposure.
Implementing the following mitigation steps will significantly reduce the likelihood of exploitation and strengthen your overall security posture. A layered security approach is key; relying on a single solution isn’t enough to protect against sophisticated attacks.
Patching and Updating Palo Alto Networks Systems
Applying the necessary patches and updates provided by Palo Alto Networks is the most effective way to directly address the certificate validation flaw. These updates often contain crucial code fixes that eliminate vulnerabilities. The process typically involves downloading the latest software version from the Palo Alto Networks support website, following their detailed instructions for installation, and verifying the successful application of the patch. Failure to promptly update exposes your systems to continued risk. Remember to schedule regular maintenance windows for these updates to minimize disruption to ongoing operations. Consider creating a detailed change management plan to ensure smooth and documented updates.
Implementing Regular Security Audits and Vulnerability Scanning
Regular security audits and vulnerability scanning are not just good practice; they are essential for maintaining a strong security posture. These processes allow you to proactively identify and address potential weaknesses, including those that may not be immediately apparent. Security audits should involve thorough reviews of your network configuration, security policies, and user access controls. Vulnerability scanning tools can automatically detect known vulnerabilities, including those related to certificate validation. By regularly performing these scans, you can quickly identify and patch vulnerabilities before they can be exploited. For example, scheduling weekly vulnerability scans and quarterly security audits allows for continuous monitoring and improvement.
Best Practices for Securing Palo Alto Networks Systems
Beyond patching and scanning, several best practices contribute to a more robust security architecture. These practices should be implemented as part of a comprehensive security strategy. This includes regularly reviewing and updating firewall rules to ensure they align with your current security needs and are optimized to prevent unauthorized access. Implementing strong access controls, such as multi-factor authentication (MFA), adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access. Regularly backing up your configuration and system data provides a safety net in case of a security incident or accidental configuration changes. Consider using a dedicated security information and event management (SIEM) system to monitor logs and detect suspicious activity. Finally, maintaining up-to-date security awareness training for your staff is crucial; educated users are less likely to fall victim to phishing attacks or other social engineering tactics that could compromise your network.
Affected Systems and Versions
This section details the specific Palo Alto Networks products and their versions vulnerable to the certificate validation flaw. Understanding which systems are at risk is crucial for prioritizing mitigation efforts and ensuring network security. This information allows administrators to quickly identify vulnerable assets within their infrastructure.
Identifying vulnerable systems requires a two-pronged approach: pinpointing the affected product lines and then verifying the specific software versions running on those systems. Failing to do both leaves your organization vulnerable.
Affected Palo Alto Networks Products and Versions
The following table lists the Palo Alto Networks products and their versions affected by the certificate validation flaw. Note that this list may not be exhaustive, and updates from Palo Alto Networks should be consulted for the most current information. Always refer to official security advisories for the latest details.
| Product Name | Affected Versions |
|---|---|
| PAN-OS | 9.1.x – 10.0.x (Specific vulnerable versions should be listed here based on the actual vulnerability. Example: 9.1.1 to 9.1.5, 10.0.0 to 10.0.3) |
| GlobalProtect | (Specific vulnerable versions should be listed here based on the actual vulnerability. Example: 5.1.x to 5.2.x) |
| Other Products (If applicable) | (List affected versions for other products here) |
Determining System Vulnerability
Determining if a system is vulnerable involves two key steps: identifying the product and verifying its version. First, you must ascertain the specific Palo Alto Networks product running on the system (e.g., PAN-OS firewall, GlobalProtect gateway). This information is typically found in the system’s administrative interface or through command-line interfaces. Next, you must locate the software version number. This usually involves navigating the system’s settings or using specific commands. Once both pieces of information are obtained, you can compare them against the table above to determine if the system is vulnerable.
Software Version Verification Methods
Several methods exist for verifying software versions. The most common approach is through the product’s administrative interface. This usually provides a “System Information” or “About” section that clearly displays the version number. Alternatively, command-line interfaces often offer commands to retrieve this information. For example, in PAN-OS, the command `show system info` (or a similar command depending on the exact product and version) can provide detailed system information, including the software version. Regularly checking for software updates and applying patches provided by Palo Alto Networks is also a critical step in maintaining security posture. Failing to do so leaves your organization susceptible to exploitation.
Case Studies (Hypothetical)
Source: squarespace-cdn.com
To truly understand the implications of the Palo Alto certificate validation flaw, let’s explore a couple of hypothetical scenarios. One showcases a successful attack, highlighting the vulnerability’s potential damage, while the other demonstrates a successful defense, illustrating the importance of mitigation strategies. These examples will illuminate the practical consequences of this flaw and the effectiveness of various countermeasures.
Successful Exploitation: The Case of “CoffeeShopChaos”
Imagine a bustling coffee shop, “CoffeeShopChaos,” with a network relying on Palo Alto Networks firewalls. A malicious actor, let’s call him “BaristaBot,” discovers the certificate validation flaw. BaristaBot crafts a specially designed, malicious certificate mimicking a legitimate certificate used by the coffee shop’s internal systems. This malicious certificate is then used to intercept encrypted network traffic between the coffee shop’s point-of-sale system and its central server. BaristaBot, using this access, siphons off sensitive customer credit card information and financial transaction data. The attack goes undetected for several weeks, resulting in significant financial losses for CoffeeShopChaos and reputational damage due to the data breach. The compromised certificate allowed BaristaBot to bypass the firewall’s security mechanisms, establishing a man-in-the-middle attack without triggering any alarms. The success hinges on the flaw’s ability to allow the acceptance of improperly validated certificates.
Failed Exploitation: The Case of “SecureBrew”
In contrast, “SecureBrew,” another coffee shop, also utilizes Palo Alto Networks firewalls but has proactively implemented all recommended mitigation strategies. A similar attacker, “LatteLurker,” attempts the same attack vector as BaristaBot. However, SecureBrew’s updated firewall firmware, along with robust certificate pinning and strict validation policies, immediately flags LatteLurker’s malicious certificate as suspicious. The attempt is blocked, and an alert is generated, alerting the security team to the attempted intrusion. LatteLurker’s attack is thwarted before any data breach can occur. The key difference lies in SecureBrew’s proactive approach to security and its commitment to applying the necessary patches and configurations.
Comparison of Case Studies
The key difference between CoffeeShopChaos and SecureBrew lies in their respective security postures. CoffeeShopChaos suffered due to a lack of timely patching and insufficient security configurations, leaving them vulnerable to exploitation. SecureBrew, on the other hand, prioritized proactive security measures, resulting in the successful prevention of the attack. This highlights the critical role of timely patching, robust security configurations, and regular security audits in mitigating the risks associated with this vulnerability.
Lessons Learned
These hypothetical scenarios underscore the critical importance of promptly addressing security vulnerabilities like the Palo Alto certificate validation flaw. Proactive patching, regular security audits, and the implementation of strong mitigation strategies are not just best practices—they are essential for preventing significant data breaches and financial losses. Ignoring security updates and neglecting proper configurations can have severe consequences, as demonstrated by the CoffeeShopChaos scenario. The SecureBrew example, however, proves that with a proactive and comprehensive approach to security, even sophisticated attacks can be effectively thwarted.
Future Implications
The Palo Alto Networks certificate validation flaw highlights a broader vulnerability within the complex ecosystem of network security products. This incident underscores the urgent need for a more proactive and holistic approach to cybersecurity, moving beyond reactive patching to a preventative mindset focused on robust design and continuous security validation. The implications extend far beyond a single vendor, impacting the trust and reliability of network security infrastructure globally.
The potential for similar vulnerabilities exists across a wide range of network security products. Many vendors rely on similar codebases, third-party libraries, and cryptographic implementations, creating a ripple effect where a single flaw can expose numerous systems. The complexity of modern network security appliances, with their intricate interactions and dependencies, makes comprehensive security testing and validation a significant challenge. The inherent difficulty in identifying and mitigating such flaws necessitates a multi-layered security strategy that relies less on single points of failure and more on redundancy and layered defenses.
Vulnerability Replication Across Vendors, Palo alto certificate validation flaw
The discovery of this specific flaw raises serious concerns about the potential for similar weaknesses in other vendors’ products. The underlying issue, likely a flawed implementation of a cryptographic algorithm or certificate handling process, could be replicated in other firewall, intrusion detection/prevention systems, and VPN gateways. Consider the widespread adoption of specific open-source libraries or proprietary code modules: a vulnerability in a commonly used component could quickly cascade across multiple vendors and numerous deployments. This underscores the importance of rigorous independent security audits and vulnerability disclosure programs.
Impact on the Cybersecurity Landscape
This vulnerability significantly impacts the broader cybersecurity landscape by eroding trust in network security solutions. The incident highlights the limitations of relying solely on vendor-provided security updates and the need for independent verification of security claims. The potential for exploitation could lead to significant breaches, data exfiltration, and disruptions of critical services. The increased sophistication of cyberattacks, combined with the growing complexity of network infrastructure, necessitates a shift towards more robust and resilient security architectures. This includes adopting a zero-trust model, where implicit trust is replaced with explicit verification at every access point.
Recommendations for Improving Network Infrastructure Security
Improving the security of network infrastructure requires a multifaceted approach that combines robust design principles, rigorous testing, and proactive security measures. This includes conducting regular security audits and penetration testing to identify vulnerabilities before attackers do. Implementing robust vulnerability management programs is crucial, ensuring timely patching and remediation of identified weaknesses. Furthermore, diversifying security solutions and avoiding over-reliance on single vendors reduces the risk of widespread compromise. Employing strong authentication mechanisms, such as multi-factor authentication, is essential to mitigate unauthorized access.
The Need for Proactive Security Measures
The reliance on reactive security measures, such as patching after vulnerabilities are discovered, is no longer sufficient. A proactive approach, emphasizing secure coding practices, robust design principles, and continuous security monitoring, is essential. This includes investing in advanced threat detection and response technologies, such as security information and event management (SIEM) systems and threat intelligence platforms. Furthermore, fostering collaboration and information sharing within the cybersecurity community is crucial to accelerate the identification and mitigation of emerging threats. The rapid dissemination of vulnerability information and best practices enables a more effective collective defense against sophisticated attacks.
Ultimate Conclusion
The Palo Alto certificate validation flaw highlights a critical need for proactive security measures and constant vigilance. While patching and updates are crucial first steps, a robust security posture requires regular audits, vulnerability scanning, and a keen awareness of emerging threats. Don’t wait for the next breach; secure your systems today. The internet’s a wild west, and you need to be prepared for anything.





