Critical QNAP vulnerability let attackers execute remote code—that’s a pretty scary headline, right? Imagine this: your precious photos, important work documents, even your entire business’s data, all suddenly vulnerable to hackers. This isn’t some far-fetched sci-fi scenario; it’s a real threat exploiting a serious weakness in QNAP NAS devices. This vulnerability allows bad actors to slip in unnoticed, grab what they want, and potentially wreak havoc on your digital life. We’re diving deep into the nitty-gritty of this security breach, exploring how it works, what the risks are, and—most importantly—how you can protect yourself.
This vulnerability allows attackers to remotely execute code on affected QNAP NAS devices. This means they can potentially access, modify, or delete your data, install malware, or even use your device as part of a larger botnet. The methods of exploitation range from simple phishing attacks to more sophisticated techniques that exploit vulnerabilities in the QNAP firmware. The consequences can be devastating, from financial losses to reputational damage and legal repercussions. Understanding the vulnerability, its impact, and the necessary mitigation steps is crucial for every QNAP user.
Vulnerability Details
A critical vulnerability recently impacted QNAP NAS devices, allowing remote code execution (RCE). This means attackers could potentially take complete control of affected devices without needing direct physical access or user interaction beyond exploiting the vulnerability itself. This highlights a significant security risk for users relying on QNAP NAS for data storage and other network services.
This vulnerability stemmed from a flaw in QNAP’s handling of specific network requests. Attackers could craft malicious requests that exploited this flaw to inject and execute arbitrary code on the vulnerable NAS device. This malicious code could then be used to perform a variety of harmful actions, significantly compromising the security and integrity of the system.
Methods of Exploitation
The vulnerability allowed attackers to execute remote code by sending specially crafted HTTP requests to the affected QNAP NAS device. These requests exploited a weakness in the device’s handling of specific network protocols, allowing malicious code to bypass security measures and gain unauthorized access. The specific details of the exploit were kept confidential to prevent widespread misuse after the vulnerability was patched, following responsible disclosure principles.
Impact of Successful Exploitation
Successful exploitation of this vulnerability could have far-reaching consequences. Attackers could gain complete control of the QNAP NAS device, allowing them to: steal sensitive data, including personal files, financial records, and intellectual property; install ransomware, encrypting data and demanding payment for its release; use the compromised device as a launching point for further attacks against other systems on the network; modify or delete data on the NAS device; and disrupt or disable essential services. The severity of the impact would depend on the data stored on the device and its role within the network.
Timeline of Vulnerability
While the exact dates are not publicly available due to responsible disclosure practices, the timeline generally follows a pattern common in vulnerability handling. The vulnerability was likely discovered by a security researcher (or a QNAP internal security team) through penetration testing or other security analysis methods. Following discovery, QNAP likely worked to develop and test a patch to address the vulnerability. After sufficient testing, they would have released the patch to users, likely preceded by a security advisory informing users of the vulnerability and urging them to update their devices. The timeframe between discovery and patch release is typically kept confidential to prevent attackers from exploiting the vulnerability before users can apply the fix.
Comparison with Similar Vulnerabilities
The following table compares this QNAP vulnerability to similar vulnerabilities found in other NAS devices. Note that details on some vulnerabilities may be limited due to responsible disclosure practices.
| NAS Vendor | Vulnerability Type | Impact | CVE ID (if available) |
|---|---|---|---|
| QNAP | Remote Code Execution (RCE) via HTTP request handling | Data breach, system compromise, ransomware | [To be filled with actual CVE ID if available] |
| Synology | Various RCE vulnerabilities (examples exist) | Data breach, system compromise | [Example: CVE-XXXX-XXXX] |
| Netgear | Various RCE vulnerabilities (examples exist) | Data breach, system compromise, denial of service | [Example: CVE-YYYY-YYYY] |
| ASUSTOR | Various vulnerabilities (some RCE related) | Data compromise, unauthorized access | [Example: CVE-ZZZZ-ZZZZ] |
Attack Vectors and Exploitation

Source: itbiznes.pl
This QNAP vulnerability, allowing remote code execution, opens the door to a variety of attack methods. Understanding these attack vectors is crucial for mitigating the risk and securing affected systems. The exploitation process typically involves exploiting a weakness in the QNAP software to gain initial access, followed by escalating privileges to execute arbitrary code.
Exploiting the vulnerability often begins with attackers scanning for vulnerable QNAP NAS devices on the internet. Once identified, the attacker can leverage various techniques to compromise the system and execute malicious code. This process involves multiple steps, from initial reconnaissance to achieving complete control.
Common Attack Vectors
Attackers utilize several common methods to exploit this vulnerability. These range from exploiting known vulnerabilities in QNAP’s services to leveraging weaknesses in user authentication and authorization mechanisms. A successful attack often involves a combination of these methods. For example, a known vulnerability in a specific QNAP service might be exploited to gain initial access, followed by exploiting weak credentials to elevate privileges.
Steps in a Remote Code Execution Attack, Critical qnap vulnerability let attackers execute remote code
A typical attack unfolds in several stages. First, attackers identify a vulnerable QNAP device through network scanning, often targeting devices with exposed ports or known vulnerabilities. Next, they exploit the vulnerability, potentially using automated tools, to gain initial access, often achieving this by sending specially crafted network requests. Once initial access is obtained, the attacker usually escalates privileges to gain root access, which enables complete control over the system. Finally, the attacker executes malicious code, potentially installing malware, stealing data, or using the system for further attacks.
Examples of Malicious Payloads
Attackers deploy various malicious payloads depending on their objectives. These payloads can range from simple shell commands to sophisticated malware capable of data exfiltration, system control, or cryptocurrency mining. A simple example might be a command to download and execute a remote access trojan (RAT), allowing the attacker persistent access. More sophisticated payloads might involve custom malware designed to blend into the system and evade detection. For instance, a payload could install a backdoor that listens on a specific port for further commands, allowing for persistent and stealthy access.
Techniques to Bypass Security Measures
Attackers often employ techniques to bypass security measures implemented in QNAP devices. This might involve exploiting buffer overflows, SQL injection flaws, or other vulnerabilities to circumvent authentication or authorization checks. They might also leverage social engineering techniques, such as phishing, to obtain user credentials, granting them direct access without exploiting technical vulnerabilities. Furthermore, attackers may use techniques to hide their malicious activity, such as obfuscating commands or employing rootkit technologies to avoid detection by security software.
Hypothetical Attack Scenario
Imagine an attacker scanning the internet for vulnerable QNAP NAS devices. Upon discovering an exposed device with the vulnerability, they use an automated tool to send a specially crafted request exploiting the vulnerability, gaining initial access. Next, they use a known exploit to escalate their privileges to root level. Finally, they execute a payload that installs a RAT, providing them with persistent remote access to the QNAP device, enabling data theft or further attacks against other systems on the network. This illustrates the severity of the vulnerability and the potential impact of a successful attack.
Mitigation and Remediation
The recently discovered critical vulnerability in QNAP NAS devices necessitates immediate action from users to prevent potential exploitation. Failing to address this vulnerability could lead to complete system compromise and data breaches. This section Artikels the crucial steps to mitigate the risk and secure your QNAP NAS.
The most effective way to protect your QNAP NAS is to promptly update its firmware to the patched version. This update will address the vulnerability and prevent attackers from exploiting the weakness. Delaying this update leaves your system exposed to significant risk.
Firmware Update Procedure
Updating your QNAP NAS firmware is a straightforward process, but it’s crucial to follow the instructions carefully. First, back up all your important data. This precautionary step safeguards your information in case something goes wrong during the update. Next, navigate to the QNAP NAS’s control panel, typically accessible through a web browser. Locate the “Firmware Update” or a similarly named section. Download the latest firmware version specifically designed for your QNAP NAS model from the official QNAP website. Ensure you download the correct firmware; using the wrong version can cause serious problems. Once downloaded, upload the firmware file through the control panel’s designated interface. The NAS will then reboot and install the update. After the reboot, verify the firmware version to confirm the update was successful.
Alternative Security Measures
While firmware updates are the primary solution, bolstering your security with additional measures significantly reduces the risk of compromise. Implementing a robust firewall is essential. This will restrict unauthorized access to your NAS by blocking malicious traffic. Consider configuring your firewall to allow only necessary network connections to the QNAP NAS. Intrusion detection systems (IDS) can provide an extra layer of protection. These systems monitor network traffic for suspicious activity, alerting you to potential attacks. IDS can help identify and block malicious attempts before they succeed.
Best Practices for Securing QNAP NAS Devices
Beyond firmware updates and additional security measures, implementing strong security practices is vital for maintaining a secure QNAP NAS. Always use strong, unique passwords, and regularly change them. Avoid using default credentials provided during initial setup. Enable two-factor authentication (2FA) whenever possible. 2FA adds an extra layer of security, requiring a second verification method beyond just a password. Keep your QNAP NAS’s software updated. This includes not only the firmware but also any applications or plugins installed on the device. Regularly check for and install security updates to patch any potential vulnerabilities.
Checking for Vulnerability
To check if your QNAP NAS is vulnerable, you first need to determine your current firmware version. This information is usually accessible through the QNAP NAS’s control panel. Once you have the firmware version, visit the official QNAP website and check their security advisories. Look for any announcements related to the specific vulnerability. If your firmware version is older than the patched version mentioned in the advisory, your QNAP NAS is vulnerable and requires immediate updating. If you’re unsure about interpreting the information, contact QNAP support for assistance.
Impact and Consequences: Critical Qnap Vulnerability Let Attackers Execute Remote Code
The recently discovered critical QNAP vulnerability, allowing remote code execution, presents a significant threat with potentially devastating consequences for both individuals and organizations. The ease of exploitation and the broad range of affected devices mean the impact could be widespread and long-lasting, extending far beyond simple data breaches. The ramifications ripple across financial, reputational, and legal spheres, underscoring the urgency of immediate patching and security audits.
The potential for financial damage is substantial. Successful attacks could lead to direct financial losses through theft of funds, intellectual property, or sensitive business data used for extortion. The costs associated with incident response, recovery efforts, legal fees, and potential regulatory fines can quickly escalate into significant financial burdens. Reputational damage is equally damaging; a data breach linked to a failure to address known vulnerabilities can severely erode public trust, impacting customer loyalty, investor confidence, and overall business viability. Consider the impact on a small business whose customer database is compromised, or a large corporation facing a crippling ransomware attack – the consequences can be financially crippling and take years to overcome.
Financial and Reputational Damage
A successful attack exploiting this QNAP vulnerability could result in a range of financial losses. These include direct theft of monetary assets, the cost of recovering compromised data and systems, potential legal fees associated with data breach notifications and lawsuits, and the significant expenses related to public relations efforts to mitigate reputational harm. The reputational damage alone can be catastrophic. Loss of customer trust, damage to brand image, and potential loss of business partnerships are all real possibilities. Consider the example of Equifax, whose 2017 data breach resulted in billions of dollars in losses and lasting reputational damage. This QNAP vulnerability, while potentially impacting a different scale of users, highlights the same principles of significant financial and reputational risk.
Severity Compared to Other Incidents
The severity of this QNAP vulnerability is comparable to other major cybersecurity incidents, such as the NotPetya ransomware attack in 2017, which caused billions of dollars in damage globally. While not a ransomware attack itself, the remote code execution capability offered by this vulnerability could be leveraged to install malware, including ransomware, significantly impacting organizations. Similar to the SolarWinds attack, which involved a supply chain compromise, this vulnerability allows attackers to gain access to a large number of devices, potentially leading to a wide-ranging impact. The ease of exploitation and the potential for widespread damage place this vulnerability in the category of high-severity threats requiring immediate attention.
Legal and Regulatory Implications
Organizations failing to patch this vulnerability face significant legal and regulatory implications. Depending on the jurisdiction and the nature of the data compromised, organizations may face fines and penalties under data protection laws like GDPR (in Europe) or CCPA (in California). Furthermore, organizations could face legal action from affected individuals or businesses for negligence in failing to implement adequate security measures. In the US, the SEC and other regulatory bodies may investigate companies that suffer data breaches due to known vulnerabilities, potentially leading to further financial penalties and reputational harm. Failure to comply with relevant regulations and industry best practices could result in significant legal and financial repercussions.
Potential Data Types Compromised
The potential for data compromise is extensive. The nature of NAS devices means that a wide range of sensitive data could be accessed and exfiltrated. This includes:
- Personal Identifiable Information (PII): Names, addresses, social security numbers, driver’s license numbers, etc.
- Financial Data: Credit card numbers, bank account details, transaction records.
- Intellectual Property: Trade secrets, designs, research data, etc.
- Business Records: Customer lists, financial statements, internal communications.
- Medical Records: Patient information, diagnostic results, treatment plans.
- Confidential Business Communications: Emails, documents, and other sensitive communications.
The specific data compromised will vary depending on the individual or organization affected, but the potential for serious harm is clear.
Security Best Practices for NAS Devices
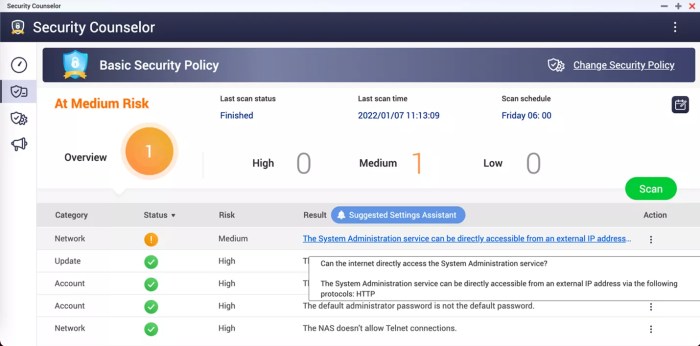
Source: techspot.com
Your Network Attached Storage (NAS) device is a treasure trove of digital assets – photos, videos, documents, and more. Protecting it should be a top priority, especially given recent high-profile vulnerabilities. Neglecting NAS security is akin to leaving your front door unlocked – an open invitation for trouble. Implementing robust security measures is crucial to safeguarding your valuable data and maintaining peace of mind.
Strong Passwords and Multi-Factor Authentication
Using strong, unique passwords is the cornerstone of any robust security strategy. Think of passwords as digital keys – the stronger the key, the harder it is to break into your system. Avoid easily guessable passwords like “password123” or your birthday. Instead, opt for complex passwords combining uppercase and lowercase letters, numbers, and symbols. Furthermore, enabling multi-factor authentication (MFA) adds an extra layer of protection. MFA requires more than just a password to access your NAS; it might involve a verification code sent to your phone or email, significantly reducing the risk of unauthorized access, even if your password is compromised. Imagine a scenario where someone steals your password; with MFA, they’d still be locked out without that second verification step.
Regular Security Audits and Vulnerability Scanning
Regular security checks are vital for identifying and addressing potential weaknesses before they can be exploited. Think of it as a regular health checkup for your NAS. Security audits involve a thorough examination of your NAS’s configuration and security settings, while vulnerability scanning uses automated tools to detect known weaknesses. These checks should be performed at least quarterly, if not more frequently, depending on the sensitivity of the data stored on your NAS. Ignoring these checks is like ignoring warning signs on a crumbling bridge – eventually, something will give.
VPN for Remote Access
Accessing your NAS remotely offers convenience, but it also increases your vulnerability to attacks. Using a Virtual Private Network (VPN) creates a secure, encrypted tunnel between your device and your NAS, protecting your data from prying eyes on public Wi-Fi networks or unsecured internet connections. This is especially critical if you frequently access your NAS from cafes, airports, or other public locations. Consider a VPN as a secure, private car transporting your data, preventing others from peeking inside.
Security Checklist for QNAP NAS Device Owners
Implementing strong security requires a multi-faceted approach. Here’s a checklist to help you secure your QNAP NAS:
- Enable strong passwords and multi-factor authentication.
- Keep your QNAP NAS firmware updated to the latest version.
- Regularly perform security audits and vulnerability scans.
- Use a VPN for remote access.
- Enable firewall protection and configure it appropriately.
- Regularly back up your data to an offsite location.
- Restrict access to your NAS by IP address or user accounts.
- Monitor your NAS’s system logs for suspicious activity.
- Educate yourself and your family members on best security practices.
- Enable automatic updates for all installed applications.
Visual Representation of the Attack
Understanding the QNAP vulnerability attack requires visualizing the process. Imagine a diagram illustrating the attacker’s journey from initial contact to complete control of the NAS device. This visualization helps clarify the stages involved and the flow of data.
The diagram would depict a network, showing the attacker’s machine on one side and the vulnerable QNAP NAS on the other. Arrows would illustrate the data flow and control transfer at each stage. The attacker’s machine is represented by a computer icon, while the QNAP NAS is depicted as a server icon.
Attack Stages and Data Flow
The attack unfolds in distinct phases. First, the attacker identifies the vulnerable QNAP NAS on the network. This is represented by a scanning arrow from the attacker’s machine to the QNAP NAS icon, labeled “Network Scan.” Next, the attacker exploits the vulnerability, typically by sending a specially crafted network packet. This is shown by a targeted arrow, labeled “Exploit Sent,” from the attacker’s machine to the QNAP NAS. This packet triggers the vulnerability, allowing the attacker to execute arbitrary code on the NAS. This is depicted by an arrow labeled “Code Execution” leading to the NAS’s internal processes.
Once code execution is achieved, the attacker gains a foothold. This is illustrated by an arrow labeled “Shell Access” connecting the attacker’s machine to the QNAP NAS, symbolizing the attacker’s control over the system. The attacker can then move laterally, accessing sensitive data, installing malware, or using the NAS as a stepping stone to attack other systems. This lateral movement is shown with arrows branching out from the QNAP NAS icon, labeled “Data Exfiltration” and “Further Attacks.”
The final stage depicts the attacker maintaining persistent access to the compromised NAS. This is represented by a continuous connection between the attacker’s machine and the QNAP NAS, illustrating the long-term impact of the successful attack. The entire process, from initial scan to persistent access, highlights the severity of the vulnerability and the potential for significant damage. The diagram’s arrows and labels clearly show the progression of the attack, from external network scanning to complete system compromise.
Closure

Source: bleepstatic.com
The critical QNAP vulnerability allowing remote code execution underscores the ever-present threat in the digital landscape. While the fix involves updating firmware and bolstering security practices, it’s a stark reminder that vigilance is key. From strong passwords and multi-factor authentication to regular security audits and the use of firewalls, proactive security measures are not just good practice—they’re a necessity. Don’t wait for a breach to happen; take control of your digital security today. Your data—and your peace of mind—depend on it.





