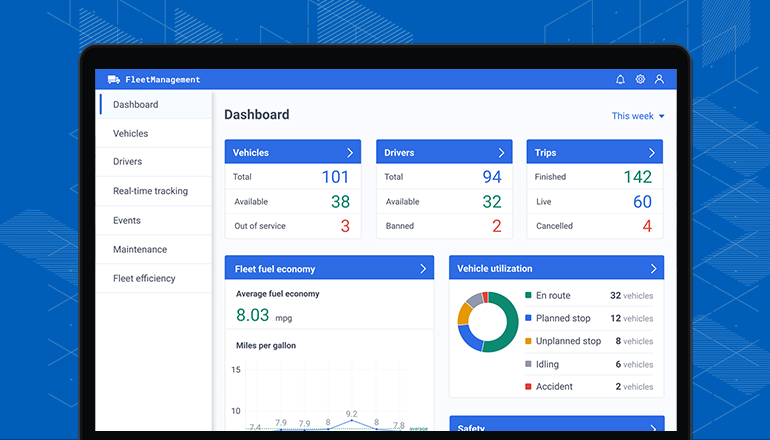
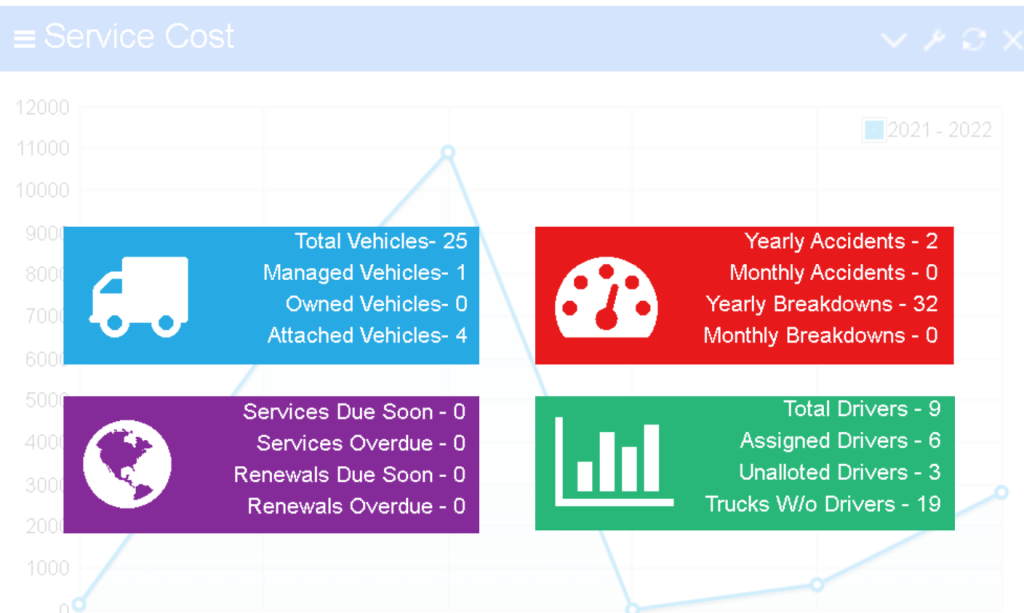
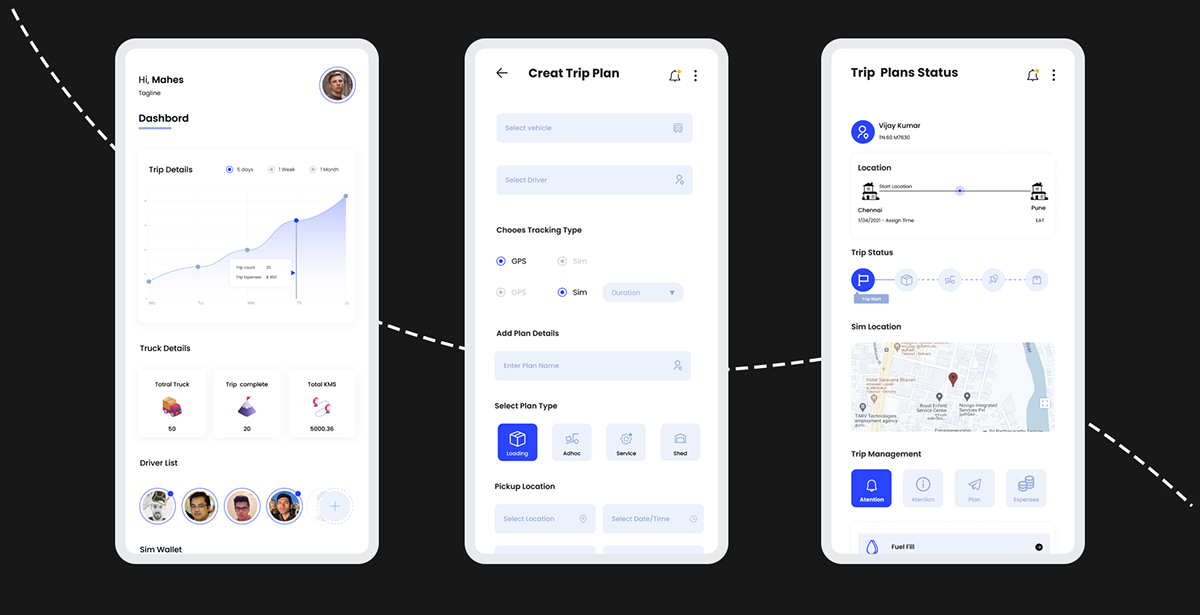
Discover the transformative power of fleet and equipment management software, a game-changer for businesses seeking efficiency and cost savings. This innovative tool streamlines operations, enhances communication, and maximizes productivity, ensuring your fleet operates at peak performance.
From tracking assets in real-time to optimizing maintenance schedules, this software is indispensable for organizations aiming to stay ahead in today’s competitive landscape. Dive into a world where technology meets strategy, paving the way for smarter decision-making and improved resource management.
Welcome to the ultimate destination for innovation, style, and usability! Are you ready to upgrade your life with products that not only meet your needs but exceed your expectations? Dive into the world of modern solutions designed just for you. Our range of products is not just about functionality; they embody the essence of contemporary life, marrying cutting-edge technology with stunning aesthetics.### Discover the Next Level of TechnologyIn today’s fast-paced world, technology is at the core of everything we do.
Our latest gadgets represent the pinnacle of innovation, featuring designs that are as sleek as they are powerful. Imagine holding a device that fits perfectly in your hand, intuitively responds to your commands, and seamlessly integrates into your lifestyle. Whether it’s our latest smartphone with an unrivaled camera system or our ultra-lightweight laptop that boasts unrivaled performance, we guarantee you’ll find the perfect tool to keep you connected and productive.
Smartphones That Transform Your ExperiencePicture this: A smartphone that not only captures the beauty of the moment but also brings your wildest ideas to life. With our latest flagship model, experience a camera system that rivals professional gear. It features night mode for capturing stunning night shots, a wide-angle lens for breathtaking landscapes, and a portrait mode that makes your selfies pop. But that’s not all! Our smartphones come equipped with AI-powered features that learn your preferences, making recommendations that enhance your daily life.
Laptops That Empower CreativityFor those who demand the best, our ultra-thin laptops offer performance that can handle anything from graphic design to extensive data analysis. Powered by the latest processors and equipped with vibrant displays, our laptops are built for creators. With a battery life that lasts all day long, you can work, play, and create without boundaries. The ergonomic keyboard and intuitive touchpad ensure that every keystroke is a pleasure, fostering an environment where creativity can flow effortlessly.### Elevate Your Living SpaceTransform your home into a sanctuary of style and comfort with our exceptional range of home products.
From smart home devices that enhance your daily routines to beautifully designed furniture that adds a touch of elegance, we have everything you need to create a living space that reflects your personality and lifestyle. Smart Home Solutions for Modern LivingImagine walking into a home that anticipates your needs. With our smart home devices, you can control your lights, thermostat, and security system from the palm of your hand.
Enjoy peace of mind with our advanced security cameras that keep a watchful eye on your property and notify you of any unusual activity. Our smart speakers not only play your favorite tunes but also assist you in managing your day with voice commands. Embrace the convenience of a smart home and elevate your living experience. Stylish Furniture That Speaks VolumesRedefine your space with our stunning furniture collection.
Each piece is meticulously crafted to ensure quality and style. From chic sofas that invite relaxation to sophisticated dining sets that impress your guests, our furniture enhances the aesthetic of any room. Choose from a variety of designs, colors, and materials to create an environment that is uniquely yours. With our furniture, your home will not just be a place to live, but a reflection of your personal journey and taste.### Fashion That Makes a StatementStep out in confidence and style with our curated collection of apparel and accessories.
Fashion is not just about clothing; it’s about expressing who you are. Our designs are crafted with the modern individual in mind, embracing both comfort and elegance. Clothing That Fits Your LifestyleOur clothing line features versatile pieces that can take you from day to night effortlessly. Whether you’re looking for a casual outfit for brunch with friends or something more sophisticated for a night out, we’ve got you covered.
Made with high-quality fabrics, our clothes are designed to last while keeping you comfortable. Choose from a variety of styles, colors, and sizes that cater to every body type. Feel good in what you wear and let your outfit be a canvas for self-expression. Accessories That Complete the LookNo outfit is complete without the right accessories. Our collection includes everything from statement jewelry that adds a touch of glam to everyday essentials like stylish bags and functional watches.
Each accessory is carefully chosen to complement our clothing line, ensuring you can create a cohesive look that turns heads. Elevate your style with pieces that are not just fashionable but also tell your story.### Wellness Products for a Healthier YouIn a world where health and wellness are paramount, we offer a range of products designed to support your journey towards a healthier lifestyle.
From fitness trackers that monitor your progress to high-quality supplements that nourish your body, we are committed to helping you achieve your wellness goals. Fitness Trackers That Keep You MotivatedStay on top of your fitness game with our state-of-the-art fitness trackers. These devices don’t just count steps; they provide insights into your health, track your workouts, and even monitor your sleep patterns. With customizable goals and reminders, you’ll be motivated to keep moving and stay active.
Our fitness trackers are sleek and stylish, making them a perfect accessory for any outfit. Take control of your health and awaken the athlete within you! Nutritional Supplements for Optimal HealthAchieving balance in your diet can be challenging. That’s why we offer a range of high-quality nutritional supplements to help you fill in the gaps. Whether you’re looking for vitamins, protein powders, or herbal remedies, our products are formulated to support your health goals.
Made with natural ingredients and backed by science, our supplements are designed to boost your energy, enhance your immunity, and promote overall wellness. Invest in your health and feel the difference.### Experience Extraordinary Customer ServiceAt the heart of our brand is a commitment to our customers. We believe that your shopping experience should be nothing short of extraordinary. That’s why our customer service team is dedicated to providing you with assistance at every step of your journey.
Have a question? Need help with a product? Our friendly representatives are just a call or click away. Hassle-Free Returns and ExchangesWe understand that sometimes things don’t work out as planned. That’s why we offer a hassle-free return and exchange policy.
If you’re not completely satisfied with your purchase, simply return it within the specified timeframe, and we’ll make it right. Your satisfaction is our priority, and we want you to feel confident in your choices.### Join Our CommunityWhen you choose our products, you’re not just buying items; you’re joining a community of like-minded individuals who value quality, innovation, and style.
Engage with us on social media, share your experiences, and connect with others who are just as passionate about enhancing their lives. We love hearing from you and celebrating the unique ways our products make a difference in your daily routine.### Conclusion: Elevate Your Life Today!It’s time to take that first step towards a more vibrant, stylish, and fulfilling life.
Explore our range of innovative products, discover solutions that cater to your needs, and embrace the opportunity to elevate every aspect of your life. Don’t wait—join the movement towards a better tomorrow with us today!Remember, your best life is just a purchase away. Shop now and let the transformation begin!
FAQ Summary
What is fleet and equipment management software?
It is a technological solution that helps businesses manage their vehicles and equipment efficiently, including tracking, maintenance, and operational costs.
How can this software improve my business operations?
By optimizing resource allocation, enhancing communication, and providing real-time data, it helps reduce costs and improve overall efficiency.
Is fleet and equipment management software easy to use?
Most solutions are designed with user-friendly interfaces, making it easy for teams to adapt and utilize effectively.
Can the software integrate with other business systems?
Yes, many fleet management solutions offer integration capabilities with existing business systems to streamline processes.
What industries benefit from this software?
Industries such as transportation, logistics, construction, and utilities greatly benefit from implementing fleet and equipment management software.