DDoS attack growing bigger isn’t just a headline; it’s a stark reality reshaping the digital landscape. From crippling e-commerce giants to disrupting critical infrastructure, these attacks are escalating in scale and sophistication, leaving businesses and individuals scrambling for effective defenses. We’re diving deep into the evolving threat, exploring the methods, motivations, and the future of this increasingly dangerous cyber warfare.
The sheer volume and frequency of these attacks are alarming. We’ll examine recent high-profile incidents, detailing their impact and the innovative techniques employed by attackers. Think massive botnets, cleverly disguised attacks, and the rise of DDoS-for-hire services – this isn’t your grandpappy’s denial-of-service attack.
The Increasing Scale of DDoS Attacks: Ddos Attack Growing Bigger
The digital landscape is facing an escalating threat: Distributed Denial-of-Service (DDoS) attacks are growing larger and more frequent, posing a significant risk to businesses, critical infrastructure, and the overall stability of the internet. This surge in attack scale and sophistication demands a closer look at the trends, impacts, and notable examples.
Recent years have witnessed a dramatic increase in both the size and frequency of DDoS attacks. Attackers are leveraging more powerful botnets, employing sophisticated techniques to bypass security measures, and targeting a wider range of victims. This trend is driven by several factors, including the increasing reliance on internet-connected devices, the evolution of attack methodologies, and the relative ease with which attack tools can be acquired. The consequences of these larger-scale attacks are far-reaching and can have devastating effects on organizations and individuals alike.
Impact of Larger DDoS Attacks
Larger DDoS attacks cripple online services, causing significant financial losses and reputational damage. The sheer volume of malicious traffic overwhelms servers, making websites and applications inaccessible to legitimate users. This disruption can lead to lost revenue, customer dissatisfaction, and damage to brand credibility. Furthermore, critical infrastructure, such as power grids and financial institutions, are increasingly vulnerable to these attacks, highlighting the potential for widespread societal disruption. The longer an attack persists, and the larger its scale, the more severe the consequences become. Businesses may face legal repercussions, insurance claims, and the need for extensive recovery efforts.
Examples of Significant DDoS Attacks and Their Consequences
Several high-profile DDoS attacks in recent years demonstrate the growing threat. These attacks not only highlight the increasing scale but also underscore the vulnerability of even the most robust systems. Analyzing these events provides crucial insights into the evolving tactics of attackers and the potential consequences.
| Attack Date | Target | Attack Size (Gbps) | Impact |
|---|---|---|---|
| October 2022 | [A major Cloud Provider – Name withheld due to ongoing legal proceedings] | ~1.5 Tbps (reported) | Widespread service disruption across multiple regions, impacting numerous customers. Significant financial losses and reputational damage for the provider. |
| November 2021 | [A large e-commerce platform – Name withheld for privacy reasons] | ~700 Gbps (reported) | Website and application outage for several hours, resulting in lost sales and customer frustration. Significant negative impact on holiday sales. |
| June 2020 | [A major gaming company – Name withheld due to ongoing investigations] | ~200 Gbps (reported) | Extended game service interruption, leading to player dissatisfaction and potential loss of subscriptions. Investigation into potential data breaches underway. |
Methods Used in Larger DDoS Attacks
Source: or.id
So, we’ve established that DDoS attacks are getting bigger and badder. But how, exactly, are these digital behemoths built? Understanding the methods behind these attacks is crucial to defending against them. It’s like knowing your enemy’s playbook – you can’t stop them if you don’t understand their strategies.
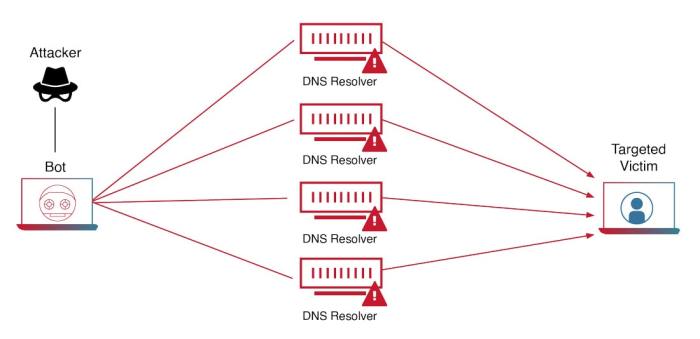
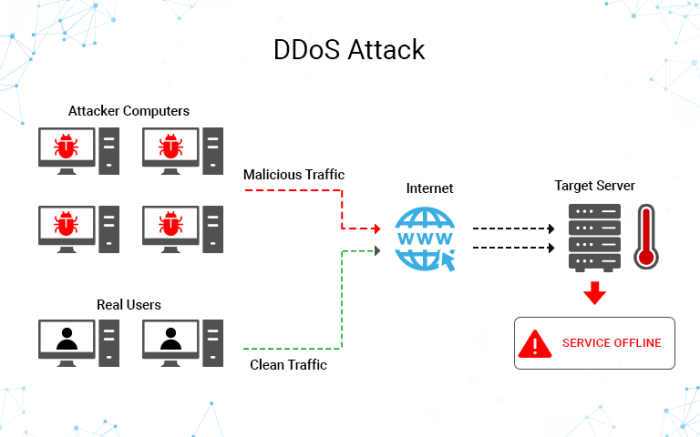
Large-scale DDoS attacks rely on a variety of methods, often combining several approaches for maximum impact. These methods can be broadly categorized into volumetric, protocol, and application layer attacks, each exploiting different vulnerabilities in network infrastructure and applications. The sheer scale of these attacks is often achieved through the use of botnets, massive networks of compromised devices acting as a single, destructive force.
Types of DDoS Attacks
Different DDoS attack types target different layers of the network stack. Volumetric attacks flood the network with massive amounts of traffic, overwhelming its bandwidth. Protocol attacks exploit vulnerabilities in network protocols, disrupting communication. Application layer attacks target specific applications, rendering them unavailable to legitimate users. Understanding these distinctions is key to effective mitigation.
- Volumetric Attacks: These attacks overwhelm the target’s bandwidth by sending massive amounts of seemingly legitimate traffic. Common examples include UDP floods and ICMP floods. Imagine a firehose pointed at a garden hose – the garden hose simply can’t handle the volume.
- Protocol Attacks: These attacks exploit weaknesses in network protocols like TCP and UDP to disrupt network communication. A common example is a SYN flood, which exhausts server resources by sending incomplete connection requests. Think of it as constantly ringing a doorbell and then running away before anyone can answer.
- Application Layer Attacks: These attacks target specific applications, such as web servers or databases, by exploiting vulnerabilities in their code or functionality. HTTP floods, for instance, send a massive number of HTTP requests, overwhelming the application’s ability to process them. It’s like trying to order a million pizzas from a single pizza place at the same time.
The Role of Botnets
Botnets are the backbone of many large-scale DDoS attacks. These networks of compromised computers (often IoT devices like security cameras or smart home appliances) are controlled remotely by attackers and used to launch coordinated attacks. Each compromised device contributes a small amount of traffic, but collectively, they generate a massive flood. Think of it as a coordinated swarm of bees, each sting individually insignificant, but collectively capable of overwhelming a much larger animal. The Mirai botnet, for example, famously leveraged millions of IoT devices to launch devastating attacks.
Attack Methods Summary
The following list summarizes some common methods used in large-scale DDoS attacks:
- UDP Floods: Sending massive amounts of UDP packets to overwhelm the target’s bandwidth.
- ICMP Floods (Ping of Death): Exploiting vulnerabilities in the ICMP protocol to disrupt network connectivity.
- SYN Floods: Exhausting server resources by sending incomplete TCP connection requests.
- HTTP Floods: Overwhelming web servers with a large number of HTTP requests.
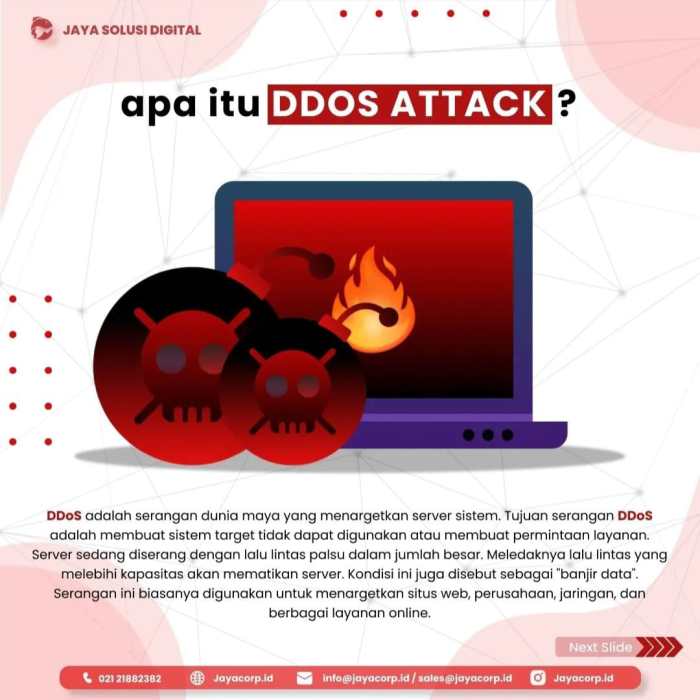
- DNS Amplification Attacks: Exploiting DNS servers to amplify the attack traffic.
- Reflective Attacks: Using third-party servers to reflect attack traffic back at the target.
Motivations Behind Larger Attacks
The sheer scale of some DDoS attacks begs the question: why? The motivations behind these digital sieges are complex and varied, often intertwining financial gain with ideological fervor. Understanding these drivers is crucial to developing effective countermeasures and predicting future threats. Let’s delve into the multifaceted reasons behind these massive attacks.
Large-scale DDoS attacks aren’t simply the work of bored teenagers. They’re often meticulously planned and executed by a range of actors, each with their own distinct goals and resources. These range from financially motivated cybercriminals to politically driven hacktivists and even state-sponsored actors. The methods and scale of the attack often reflect the attacker’s resources and ultimate objective.
Motivations of Different Attacker Types
The motivations behind large-scale DDoS attacks vary greatly depending on the attacker’s profile. Hacktivists, for instance, often target organizations they perceive as morally reprehensible, using DDoS attacks as a form of digital protest or to disrupt services. Cybercriminals, on the other hand, are primarily driven by financial gain, often using DDoS attacks as extortion tools or to disrupt competitors. Nation-states may utilize DDoS attacks for espionage, sabotage, or to destabilize an adversary’s infrastructure. The scale of the attack is often a reflection of the resources and ambitions of the attacker. A small group of hacktivists might launch a relatively small attack, whereas a nation-state might deploy a significantly larger and more sophisticated one.
Financial Incentives in DDoS-for-Hire Services, Ddos attack growing bigger
The rise of DDoS-for-hire services has dramatically lowered the barrier to entry for launching large-scale attacks. These services, often operating on the dark web, offer readily available tools and expertise to anyone willing to pay. The pricing models typically vary based on the attack’s duration, target, and intensity. For example, a basic attack targeting a small website might cost a few hundred dollars, while a more sophisticated attack against a large organization could cost thousands or even tens of thousands. The financial incentives for those providing these services are clear: high profit margins with relatively low risk, particularly if they operate anonymously and utilize obfuscation techniques to mask their activities. The ease of access to these services empowers individuals and groups with limited technical expertise to inflict significant damage.
Hypothetical Scenario: A DDoS Attack on a Financial Institution
Imagine a group of cybercriminals aiming to extort a major financial institution. They meticulously research the institution’s online infrastructure, identifying vulnerabilities and potential points of failure. They then contract a DDoS-for-hire service, specifying the desired attack intensity and duration. The service provider utilizes a botnet – a network of compromised computers – to launch a massive attack, overwhelming the institution’s servers and rendering its online services unavailable. The criminals then contact the institution, demanding a significant ransom in cryptocurrency in exchange for ceasing the attack. The success of this scenario hinges on the attackers’ ability to choose the right target, successfully launch a powerful enough attack, and ensure their anonymity throughout the process. The potential for significant financial gain motivates the attackers, while the ease of access to DDoS-for-hire services lowers the barrier to entry, creating a dangerous and increasingly prevalent threat.
Mitigation Strategies for Large DDoS Attacks
Source: radware.com
Facing a massive DDoS attack feels like trying to plug a dam with your fingers – overwhelming and frankly, terrifying. The sheer volume of malicious traffic can cripple even the most robust systems. Fortunately, a range of sophisticated technologies and strategies exist to combat these digital sieges, allowing organizations to defend their online presence and maintain critical services. The effectiveness of these strategies depends on a proactive approach and a multi-layered defense system.
Mitigation strategies for large-scale DDoS attacks are constantly evolving, mirroring the ever-changing tactics of attackers. A layered approach, combining various techniques, is crucial for comprehensive protection. This involves proactively identifying vulnerabilities, implementing robust security measures, and having a well-defined incident response plan in place. Choosing the right strategy depends on factors such as the size and type of the attack, the organization’s resources, and the criticality of the systems being protected.
Scrubbing Centers
Scrubbing centers act as highly-secured, high-capacity network infrastructure designed to filter out malicious traffic before it reaches the victim’s network. They operate like powerful filters, analyzing incoming traffic and identifying and discarding malicious packets while allowing legitimate traffic to pass through. This offloads the burden of traffic filtering from the victim’s network, preventing it from being overwhelmed. Large scrubbing centers often employ sophisticated techniques like deep packet inspection and anomaly detection to identify and filter various types of DDoS attacks, including volumetric, protocol, and application-layer attacks. The cost of using a scrubbing center can be substantial, making it a more suitable option for organizations with significant resources and critical infrastructure. For example, a major financial institution might utilize a scrubbing center to protect its online banking platform from a significant DDoS attack.
Cloud-Based DDoS Mitigation Solutions
Cloud-based solutions offer a scalable and flexible approach to DDoS protection. Leveraging the vast resources and distributed nature of cloud infrastructure, these services can absorb massive amounts of malicious traffic, shielding the target network. They often integrate multiple mitigation techniques, including traffic filtering, rate limiting, and blackholing, adapting dynamically to the evolving attack patterns. The scalability of cloud-based solutions is a key advantage, allowing organizations to quickly scale their protection capacity as needed, without investing in significant upfront infrastructure. A rapidly growing e-commerce company, for instance, might rely on a cloud-based solution to protect its website during peak shopping seasons, anticipating potential DDoS attacks.
Network Filtering
Network filtering involves implementing various techniques at the network perimeter to block or limit malicious traffic. This can include techniques like IP address blocking, protocol filtering, and deep packet inspection. IP address blocking involves identifying and blocking known malicious IP addresses from accessing the network. Protocol filtering focuses on blocking specific protocols or port numbers that are commonly used in DDoS attacks. Deep packet inspection examines the content of network packets to identify and filter malicious traffic based on its characteristics. While effective against some attacks, network filtering alone might not be sufficient to mitigate sophisticated, large-scale attacks. A small business, for example, might use network filtering as a first line of defense, supplemented by other security measures.
Proactive Security Measures and Preventative Strategies
Proactive security is not just a good idea; it’s a necessity in today’s threat landscape. Regular vulnerability assessments, penetration testing, and security audits are crucial for identifying and addressing weaknesses before attackers can exploit them. Implementing strong authentication mechanisms, such as multi-factor authentication, can significantly enhance security and make it more difficult for attackers to gain unauthorized access. Regular software updates and patching are essential to address known vulnerabilities and prevent attackers from exploiting them. Furthermore, robust security policies and employee training programs are critical to minimizing human error, a frequent factor in successful attacks. A well-defined incident response plan is vital for minimizing the impact of a successful attack and ensuring a swift recovery. Consider a hospital network – proactive measures to protect patient data are not just recommended, but legally and ethically mandated.
Responding to a Large DDoS Attack: A Flowchart
Imagine this flowchart as a visual representation of the coordinated response required during a DDoS attack. Each step is crucial for effective mitigation and minimizing downtime.
(Note: A visual flowchart cannot be created in this text-based format. However, the steps are described below to represent the content of a flowchart.)
Step 1: Detection: Intrusion Detection Systems (IDS) and other monitoring tools detect anomalous network traffic indicating a potential DDoS attack.
Step 2: Verification: Security analysts verify the attack’s nature and scale, differentiating it from legitimate traffic spikes.
Step 3: Mitigation Activation: Pre-configured mitigation strategies, such as those mentioned above (scrubbing centers, cloud-based solutions, and network filtering) are activated.
Step 4: Traffic Analysis: The source and type of attack are analyzed to refine mitigation techniques and identify potential vulnerabilities.
Step 5: Incident Response Team Activation: A dedicated team coordinates efforts, communicates with stakeholders, and manages the response.
Step 6: Attack Mitigation: The activated mitigation strategies are continuously monitored and adjusted to effectively counter the attack.
Step 7: Post-Incident Analysis: After the attack subsides, a thorough analysis is conducted to identify vulnerabilities, improve security measures, and refine the incident response plan.
The Future of DDoS Attacks
The landscape of cyberattacks is constantly evolving, and Distributed Denial-of-Service (DDoS) attacks are no exception. What started as relatively simple attacks are becoming increasingly sophisticated and powerful, posing a significant threat to businesses, governments, and critical infrastructure. Understanding the potential future trends in DDoS attacks is crucial for developing effective mitigation strategies.
The sheer scale and complexity of DDoS attacks are poised to increase dramatically in the coming years. This escalation will be driven by several factors, including technological advancements, the growing reliance on interconnected devices, and the increasing sophistication of attack methodologies.
Increasing Attack Size and Sophistication
Future DDoS attacks will likely leverage more powerful botnets, incorporating a wider range of devices and utilizing more advanced techniques to bypass existing security measures. We can expect to see attacks that exploit vulnerabilities in IoT devices, cloud services, and even AI systems to create significantly larger and more resilient botnets. For example, a future attack might involve coordinated attacks from millions of compromised smart home devices, resulting in a massive and sustained assault on a target’s infrastructure. The sophistication of these attacks will also increase, with attackers utilizing techniques like low-and-slow attacks that are harder to detect and mitigate. These attacks will gradually increase traffic volume over time, making it difficult to distinguish them from legitimate traffic.
Emerging Technologies Used in Future Attacks
The adoption of new technologies presents both opportunities and challenges. Artificial intelligence (AI) and machine learning (ML) could be weaponized to create self-learning botnets that adapt to changing security measures, making them incredibly difficult to neutralize. Similarly, the increasing use of cloud computing could be exploited to launch massive DDoS attacks, leveraging the scalability and anonymity offered by cloud infrastructure. Quantum computing, while still in its early stages, holds the potential to break current encryption methods, potentially opening up new avenues for large-scale attacks.
Evolution of Mitigation Strategies
The ongoing arms race between attackers and defenders necessitates the evolution of mitigation strategies. We can anticipate a greater reliance on AI-powered security systems capable of detecting and responding to sophisticated attacks in real-time. Cloud-based DDoS mitigation services will become increasingly prevalent, offering scalable and adaptable protection. The development of more robust and resilient network architectures, along with improved collaboration between security providers and organizations, will also be critical. Blockchain technology might play a role in verifying the legitimacy of network traffic, reducing the effectiveness of some attack vectors.
Exacerbation by Internet-Connected Devices
The exponential growth of the Internet of Things (IoT) significantly exacerbates the DDoS problem. The sheer number of interconnected devices, many of which lack robust security measures, provides a vast pool of potential resources for attackers to exploit. A single, easily compromised smart device could become part of a massive botnet, contributing to a devastating attack. The challenge lies in securing this vast and diverse ecosystem of devices, a task requiring significant effort from both manufacturers and users. Imagine a scenario where millions of compromised smart refrigerators are used to launch a massive DDoS attack, overwhelming a critical infrastructure provider.
Illustrative Example
Source: codingvilla.in
Let’s imagine a scenario: a massive DDoS attack targeting “GlobalBank,” a multinational financial institution with a sprawling online presence. This isn’t some small-time operation; we’re talking about a coordinated, multi-vector assault designed to cripple the bank’s systems and potentially cause significant financial losses.
The attack leveraged a sophisticated botnet, comprising millions of compromised IoT devices – smart home appliances, security cameras, and even industrial control systems – scattered across the globe. This distributed nature made tracing the source incredibly difficult. The attackers employed a multi-pronged approach, combining volumetric attacks (flooding the bank’s servers with massive amounts of traffic) with application-layer attacks (exploiting vulnerabilities in GlobalBank’s web applications).
Attack Methods and Target Infrastructure
The volumetric attacks involved UDP floods, overwhelming GlobalBank’s network infrastructure with massive bursts of UDP packets. Simultaneously, application-layer attacks targeted specific web services, such as the online banking portal and the mobile app, using HTTP floods and slowloris attacks to exhaust server resources and degrade performance. The attackers also employed SYN floods, aiming to cripple the bank’s ability to establish new connections. The target infrastructure included GlobalBank’s web servers, application servers, database servers, and load balancers – essentially, every critical component of their online banking ecosystem.
Impact and Visual Representation of the Attack
The impact was devastating. GlobalBank’s online services went down completely within hours, leaving millions of customers unable to access their accounts. Stock prices plummeted, and the bank faced significant reputational damage. The attack’s progression could be visualized using a dynamic heatmap, with geographical locations of the botnet nodes represented by varying intensities of red. The intensity of the red would increase proportionally to the volume of traffic originating from each location. A line graph, overlaid on the heatmap, would show the escalating volume of attack traffic over time, peaking dramatically during the most intense phases of the assault. The y-axis would represent the volume of traffic (measured in Gbps), and the x-axis would represent time. A separate bar chart would illustrate the breakdown of attack vectors, showing the relative contribution of each attack type (UDP floods, HTTP floods, SYN floods, etc.) to the overall attack. The color scheme would be predominantly red and orange, symbolizing the severity and intensity of the attack, with a contrasting cool blue used for the background to highlight the data. The visualization would clearly illustrate the global reach of the botnet and the overwhelming scale of the attack traffic. This visual representation would highlight the dramatic increase in traffic volume leading to a complete service outage. The visualization would clearly show the point of complete system failure and the duration of the outage.
Outcome Summary
The ever-expanding threat of DDoS attacks necessitates a proactive and multi-layered approach to security. While the scale and sophistication of these attacks continue to grow, so too must our defenses. Understanding the motivations behind these attacks, mastering mitigation strategies, and staying ahead of emerging technologies are crucial for navigating this increasingly perilous digital terrain. The future of online security hinges on our ability to outmaneuver those who seek to disrupt and destroy.





