Critical kubernetes vulnerability – Critical Kubernetes vulnerabilities are a serious threat to modern cloud-native applications. These security flaws can range from simple misconfigurations to sophisticated exploits, allowing attackers to gain unauthorized access, disrupt services, or steal sensitive data. Understanding the different types of vulnerabilities, their potential impact, and effective mitigation strategies is crucial for maintaining the security and integrity of your Kubernetes deployments. This article will equip you with the knowledge to navigate this complex landscape and secure your systems.
From privilege escalation, allowing attackers to gain elevated permissions, to denial-of-service attacks that cripple your applications, the potential consequences are significant. We’ll examine real-world examples of critical vulnerabilities, showcasing the devastating impact they can have on businesses and organizations. We’ll delve into practical methods for identifying, assessing, and mitigating these risks, covering everything from vulnerability scanners to implementing robust security controls and incident response plans.
Understanding the Scope of Critical Kubernetes Vulnerabilities
Kubernetes, the ubiquitous container orchestration system, powers a significant portion of the modern internet. Its complexity, however, introduces a considerable attack surface, making it a prime target for malicious actors. Understanding the various types of critical vulnerabilities and their potential impact is crucial for maintaining secure and reliable deployments.
Critical Kubernetes vulnerabilities can broadly be categorized into several damaging types, each with the potential to severely compromise the security and functionality of your cluster. These vulnerabilities can lead to significant disruptions and data breaches, emphasizing the importance of proactive security measures.
Categories of Critical Kubernetes Vulnerabilities
Critical vulnerabilities in Kubernetes can manifest in various forms, each with unique consequences. Privilege escalation allows attackers to gain unauthorized access to sensitive resources and execute commands with elevated privileges. Denial-of-service (DoS) attacks can render the entire cluster or specific services unavailable to legitimate users. Information leakage vulnerabilities expose sensitive data, such as credentials or application secrets, putting the entire system at risk. These vulnerabilities can occur at various layers within the Kubernetes ecosystem, from the control plane to individual pods and applications.
Impact of Kubernetes Vulnerabilities on Deployments
The consequences of exploiting critical Kubernetes vulnerabilities can range from minor service disruptions to catastrophic data breaches and complete system compromise. A successful privilege escalation attack could allow an attacker to gain root access to the entire cluster, enabling them to modify or delete critical resources. DoS attacks can disrupt services, impacting business operations and user experience. Information leakage can expose sensitive data, leading to regulatory fines and reputational damage. The impact is often amplified by the scale and complexity of modern Kubernetes deployments. A single compromised node could lead to a cascading failure across the entire cluster.
Examples of Real-World Critical Vulnerabilities and Their Consequences
Several real-world examples highlight the severity of critical Kubernetes vulnerabilities. For instance, vulnerabilities in the kubelet (the agent that runs on each node) have historically allowed attackers to gain unauthorized access to the host operating system. Exploiting such vulnerabilities could provide complete control over the node, allowing the attacker to access other nodes within the cluster. Similarly, vulnerabilities in the Kubernetes API server can expose sensitive information or allow attackers to manipulate cluster resources, leading to significant disruptions. The infamous “RunC container escape” vulnerability allowed attackers to escape from their containers and gain access to the host system, showcasing the importance of using patched and up-to-date container images.
Comparison of Critical Kubernetes Vulnerabilities
The following table compares the severity, exploitability, and impact of various critical vulnerabilities. Note that CVSS scores are dynamic and may change as new information becomes available.
| Vulnerability Name | Severity (CVSS Score) | Exploitability | Impact |
|---|---|---|---|
| CVE-XXXX-YYYY (Example: A hypothetical kubelet privilege escalation vulnerability) | 9.8 (Critical) | High (Remotely exploitable) | Complete cluster compromise, data exfiltration |
| CVE-ZZZZ-WWWW (Example: A hypothetical API server denial-of-service vulnerability) | 7.5 (High) | Medium (Requires network access) | Service unavailability, business disruption |
| CVE-AAAA-BBBB (Example: A hypothetical secret leakage vulnerability) | 6.5 (Medium) | Low (Requires unauthorized access to specific resource) | Data breach, potential identity theft |
Identifying and Assessing Critical Vulnerabilities
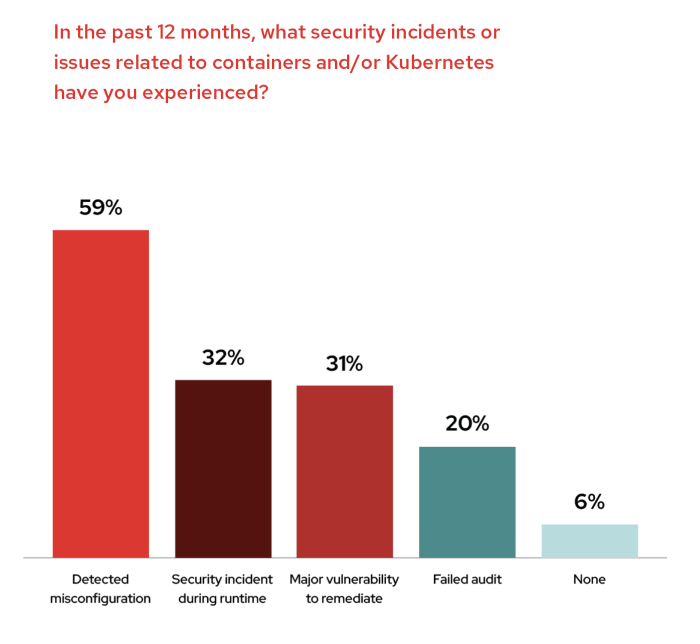
Source: redhat.com
Keeping your Kubernetes cluster secure is a continuous process, not a one-time fix. Proactive vulnerability identification is crucial to preventing breaches and maintaining the integrity of your applications and data. This involves a multi-faceted approach combining automated scanning with diligent manual review.
Identifying and assessing vulnerabilities in a Kubernetes environment requires a robust strategy. This isn’t just about finding problems; it’s about understanding their potential impact and prioritizing remediation efforts. A layered approach, combining automated tools with human expertise, is essential for comprehensive vulnerability management.
Vulnerability Scanning and Security Tools for Kubernetes
Several tools are available to help automate the vulnerability scanning process within your Kubernetes cluster. These tools analyze container images, configurations, and the overall cluster health for known vulnerabilities and misconfigurations. Examples include Trivy, Clair, Anchore, and Snyk. These scanners often integrate directly with your CI/CD pipeline, allowing for early detection of vulnerabilities before deployment. Beyond scanners, security tools like Falco can monitor runtime behavior for suspicious activities, providing another layer of defense. Choosing the right tool depends on your specific needs and infrastructure. Consider factors like scalability, integration capabilities, and the level of detail provided in reports.
Risk Assessment Methodology for Kubernetes Vulnerabilities, Critical kubernetes vulnerability
Once vulnerabilities are identified, a thorough risk assessment is critical. This involves evaluating the likelihood of exploitation and the potential impact on your system. The Common Vulnerability Scoring System (CVSS) provides a standardized framework for quantifying vulnerability severity. However, a CVSS score alone isn’t sufficient. Consider factors specific to your environment: the sensitivity of the data stored in affected pods, the access controls in place, and the overall resilience of your infrastructure. A high CVSS score on a vulnerability affecting a non-critical application might be less urgent than a lower-scored vulnerability affecting a sensitive database. Document your risk assessment process, including the criteria used and the rationale behind your decisions. This documentation will be invaluable during audits and incident response.
Best Practices for Vulnerability Management in Kubernetes
Effective vulnerability management is a continuous cycle. Implementing the following best practices can significantly reduce your attack surface:
Prioritizing proactive vulnerability management ensures a secure and resilient Kubernetes environment. Regular scanning, thorough risk assessment, and consistent patching are crucial elements of a robust security strategy.
- Regularly scan container images and Kubernetes configurations: Integrate vulnerability scanning into your CI/CD pipeline to catch issues early.
- Implement a robust patching strategy: Keep your Kubernetes components, container images, and underlying infrastructure updated with the latest security patches.
- Utilize least privilege access control: Grant only necessary permissions to users and services within your Kubernetes cluster.
- Employ network policies: Restrict network traffic between pods and namespaces to limit the impact of potential breaches.
- Monitor system logs and audit trails: Regularly review logs for suspicious activity and ensure audit trails are properly configured.
- Employ automated security tools: Utilize tools like Falco for runtime security monitoring and response.
- Conduct regular security audits and penetration testing: Simulate real-world attacks to identify weaknesses in your security posture.
Mitigation Strategies for Critical Kubernetes Vulnerabilities

Source: medium.com
Protecting your Kubernetes cluster from critical vulnerabilities requires a multi-layered approach. Ignoring these vulnerabilities can lead to significant security breaches, data loss, and operational downtime. Effective mitigation hinges on proactive measures, regular updates, and robust access control.
Addressing critical vulnerabilities involves a combination of preventative strategies and reactive responses. This includes patching known vulnerabilities, implementing strong access controls, and continuously monitoring your cluster for suspicious activity. A layered security approach is crucial, as relying on a single method is insufficient to guarantee complete protection.
Patching and Updating Vulnerable Components
Regular patching and updates are fundamental to mitigating Kubernetes vulnerabilities. Outdated components often contain known security flaws that attackers can exploit. A well-defined patching strategy should include a process for identifying vulnerable components, testing patches in a staging environment, and then rolling them out to production. This process minimizes disruption and ensures the patches are effective. Consider using automated tools to streamline the patching process and receive timely alerts for new vulnerabilities. For instance, a robust CI/CD pipeline can automate the testing and deployment of security patches, reducing the risk of human error and speeding up the response time.
Implementing Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a crucial security mechanism in Kubernetes. It limits the privileges granted to users and service accounts, preventing unauthorized access and limiting the impact of compromised credentials. By assigning roles with specific permissions, you can ensure that only authorized entities can perform sensitive actions. For example, a developer should only have access to the namespaces they are working on, not the entire cluster. Incorrectly configured RBAC can leave your cluster vulnerable, so meticulous planning and implementation are necessary. Regular audits of RBAC configurations are also crucial to identify and address potential weaknesses.
Network Policies and Security Contexts
Network policies define communication rules within the Kubernetes cluster, controlling which pods can communicate with each other. This granular control helps to isolate applications and prevent lateral movement by attackers. Security contexts, on the other hand, define security settings for containers, such as running containers as non-root users and limiting their capabilities. These measures enhance the security posture of individual pods and reduce the potential impact of compromised containers. A well-defined network policy, for example, might restrict communication between a database pod and any pods outside a specific namespace.
Implementing Security Controls: Examples
Implementing strong security controls involves a combination of techniques. For example, enabling pod security policies (although deprecated, they offer insights into the principles of container security) or using their successor, Pod Security Admission, helps to enforce security best practices at the container level. Employing network segmentation by separating sensitive applications into their own namespaces further isolates them from potential threats. Furthermore, regular security audits and penetration testing can identify and address vulnerabilities before they are exploited. A recent example of a real-world security incident involving a misconfigured network policy highlighted the importance of meticulous planning and regular reviews. This misconfiguration allowed unauthorized access to sensitive data, emphasizing the need for thorough testing and monitoring.
Comparing Patching Approaches
There are several approaches to patching, each with its own advantages and disadvantages. “In-place” patching updates the running components without downtime, while “rolling updates” gradually replace components with minimal disruption. “Blue-green deployments” involve deploying the updated components to a separate environment and then switching traffic once validated. The choice of approach depends on factors like application sensitivity, downtime tolerance, and the complexity of the application. A critical application might benefit from a blue-green deployment to minimize risk, while a less sensitive application could use an in-place update.
Responding to Critical Vulnerability Exploits
Source: website-files.com
A critical Kubernetes vulnerability exploit can bring your entire infrastructure to its knees – fast. Think data breaches, service outages, and a hefty bill for recovery. Knowing how to react swiftly and effectively is crucial to minimizing damage and restoring operations. This section details the essential steps involved in responding to such a critical situation, from initial containment to post-incident analysis.
Effective incident response isn’t just about fixing the immediate problem; it’s about learning from the experience to prevent future attacks. A well-defined response plan, coupled with regular security audits and training, forms the bedrock of a robust security posture.
Containment Procedures
Containment is the first, crucial step in mitigating the impact of a Kubernetes vulnerability exploit. The goal is to isolate the affected systems and prevent the attacker from further compromising your environment. This might involve disconnecting the compromised nodes from the network, blocking malicious traffic at the firewall, or temporarily disabling affected services. Speed is paramount; the longer the attacker has access, the greater the potential damage.
Remediation Strategies
Once containment is established, the focus shifts to remediation. This involves identifying the root cause of the exploit, patching the vulnerability, and restoring affected systems to a secure state. This often includes updating Kubernetes components, applying security patches to affected applications, and restoring data from backups. Thorough testing is essential after remediation to ensure the vulnerability is completely resolved and systems are functioning correctly.
Incident Response Best Practices
A structured approach to incident response is vital. This involves establishing clear communication channels, documenting all actions taken, and assigning roles and responsibilities to team members. Regular security drills and simulations can help prepare your team for real-world scenarios. Post-incident analysis is equally crucial; it allows you to identify weaknesses in your security posture and implement improvements to prevent future incidents. This process often includes reviewing logs, analyzing attack vectors, and updating security policies.
A Step-by-Step Guide to Incident Response
A clear, actionable plan is essential for effective incident response. Following these steps can help minimize damage and ensure a swift recovery:
- Detect the Exploit: Identify the signs of a compromise, such as unusual network traffic, unauthorized access attempts, or system performance degradation. Automated monitoring tools are invaluable here.
- Isolate the Affected Systems: Immediately isolate the compromised nodes or pods from the network to prevent further damage. This might involve disconnecting them from the network, blocking traffic at the firewall, or using Kubernetes namespaces to restrict access.
- Analyze the Attack: Investigate the nature of the attack to understand how the attacker gained access and the extent of the compromise. Examine logs, network traffic, and system activity for clues.
- Remediate the Vulnerability: Patch the vulnerability by updating Kubernetes components, applying security patches to affected applications, and restoring data from backups. Thorough testing is crucial after remediation.
- Restore Systems: Bring affected systems back online after remediation, ensuring they are secure and functioning correctly.
- Conduct Post-Incident Analysis: Review the incident to identify weaknesses in your security posture and implement improvements to prevent future incidents. This often involves reviewing logs, analyzing attack vectors, and updating security policies.
- Document Everything: Maintain a detailed record of all actions taken during the incident response process. This documentation will be invaluable for future investigations and incident response planning.
Preventing Future Critical Vulnerabilities
Proactive security measures are paramount in the ever-evolving landscape of Kubernetes vulnerabilities. Ignoring preventative strategies is akin to leaving your front door unlocked – inviting trouble. A robust, multi-layered approach is crucial to minimize the risk of future critical vulnerabilities and maintain the integrity of your Kubernetes clusters. This involves a combination of secure coding practices, rigorous testing, and a commitment to continuous improvement.
Preventing future Kubernetes vulnerabilities necessitates a proactive and multi-faceted strategy. This goes beyond simply patching known issues; it’s about building a security culture and implementing practices that minimize the likelihood of vulnerabilities arising in the first place. A strong security posture requires a blend of technical safeguards and organizational commitment.
Secure Coding Practices and Image Scanning
Secure coding practices are the foundation of preventing vulnerabilities. This involves adhering to established security principles throughout the software development lifecycle (SDLC). Developers should be trained on secure coding techniques, including input validation, output encoding, and proper error handling. Regular code reviews and static analysis tools can help identify potential vulnerabilities before they reach production. Furthermore, comprehensive image scanning is vital. Automated tools should scan container images for known vulnerabilities and malware before deployment. This helps ensure that only secure and trusted images are running in your Kubernetes environment. Failure to perform these checks is like driving a car without brakes – potentially disastrous. For instance, a recent incident at a major financial institution saw a compromised container image leading to a data breach, costing millions in remediation and reputational damage.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying and addressing vulnerabilities before malicious actors can exploit them. Security audits provide a comprehensive assessment of your Kubernetes environment’s security posture, identifying weaknesses in configurations, access controls, and other critical areas. Penetration testing simulates real-world attacks to identify exploitable vulnerabilities. These tests should be conducted regularly, ideally by independent security experts, to ensure an unbiased and thorough evaluation. A well-structured penetration test can expose vulnerabilities that might otherwise go unnoticed, saving your organization from potentially devastating consequences. Think of it as a yearly health check-up for your Kubernetes cluster, ensuring its continued health and robustness.
Preventative Measures, Implementation, and Effectiveness
| Preventative Measure | Implementation Details | Effectiveness |
|---|---|---|
| Secure Coding Practices | Training developers on secure coding principles, implementing static code analysis tools, conducting regular code reviews. | High – significantly reduces the likelihood of introducing vulnerabilities during development. |
| Image Scanning | Integrating automated image scanning tools into the CI/CD pipeline to check for known vulnerabilities and malware before deployment. | High – prevents deployment of compromised container images. |
| Regular Security Audits | Conducting periodic audits to assess the overall security posture of the Kubernetes environment. | Medium – identifies configuration weaknesses and potential vulnerabilities. |
| Penetration Testing | Simulating real-world attacks to identify exploitable vulnerabilities. | High – proactively discovers and mitigates vulnerabilities before attackers can exploit them. |
| Least Privilege Access Control | Granting users and services only the necessary permissions to perform their tasks. | High – limits the impact of potential breaches. |
| Network Segmentation | Isolating different parts of the Kubernetes cluster to limit the impact of a potential breach. | Medium to High – reduces the attack surface and prevents lateral movement. |
The Role of Container Security: Critical Kubernetes Vulnerability
Kubernetes, while incredibly powerful, is only as secure as its constituent parts. A weak link in the chain, particularly insecure container images, can unravel the entire system’s security, leaving your cluster vulnerable to devastating attacks. Focusing on container security is paramount to maintaining a robust and resilient Kubernetes environment. This means securing the very building blocks of your applications.
Container image security is crucial because these images form the foundation of your deployments. A compromised image can lead to a compromised pod, and subsequently, your entire cluster. Think of it like this: if you build your house with faulty bricks, the whole structure is at risk, regardless of how strong the foundation is. Similarly, if your container images contain vulnerabilities, the security of your Kubernetes cluster is severely weakened.
Secure Container Image Building
Building secure container images requires a multi-layered approach. It begins with using minimal base images, only including necessary packages and dependencies. This reduces the attack surface, minimizing the potential for vulnerabilities to creep in. Next, leverage automated build processes and incorporate static analysis tools during the build pipeline. This helps catch potential issues early, before they make it into production. Finally, always sign your images to ensure authenticity and integrity. This guarantees that the images deployed are exactly what you intended, preventing tampering or malicious injection. Imagine a construction site where every brick is checked for quality before being used; that’s the level of scrutiny needed in container image building.
Container Image Scanning
Regularly scanning container images for known vulnerabilities is a non-negotiable step. Tools like Trivy, Clair, and Anchore Engine are invaluable for this process. These tools analyze the image layers, identifying any known vulnerabilities based on publicly available databases like the National Vulnerability Database (NVD). Think of these scanners as sophisticated X-ray machines for your container images, revealing hidden weaknesses before they can be exploited. The results of these scans should trigger automated remediation actions, such as rejecting insecure images or initiating a rebuild with updated packages. Failure to address these vulnerabilities promptly can lead to serious security breaches.
Immutable Infrastructure
Adopting immutable infrastructure is a powerful strategy for minimizing vulnerability exposure. This approach involves creating new container images for every deployment, rather than updating existing ones. This ensures that any vulnerabilities introduced in previous deployments are not carried forward. Once a container image is built and deployed, it remains unchanged. This simplifies rollback processes and limits the impact of potential exploits. It’s like having a perfectly replicated backup of your system, ready to replace any compromised version quickly and easily. This predictability enhances your ability to react swiftly to security incidents.
Kubernetes Security Best Practices
Securing your Kubernetes cluster is paramount, given its role as the orchestrator of your containerized applications. A robust security posture isn’t just about reacting to vulnerabilities; it’s about proactively building a system that’s inherently resistant to attacks. This involves a multi-layered approach encompassing network security, access control, image security, and more. Let’s dive into the essential best practices that can significantly bolster your Kubernetes security.
Network Security
Network segmentation and control are fundamental to Kubernetes security. Uncontrolled network access can expose your applications and sensitive data to malicious actors. Implementing robust network policies helps restrict communication between pods and namespaces, limiting the blast radius of a potential compromise. For instance, a well-defined network policy might prevent a compromised pod in one namespace from accessing sensitive databases in another.
- Use NetworkPolicies to control inter-pod communication within namespaces.
- Implement ingress controllers with appropriate authentication and authorization mechanisms.
- Segment your Kubernetes cluster into separate virtual networks for different applications or teams.
- Regularly review and update your network policies to reflect evolving security needs.
Access Control
Properly managing access to your Kubernetes cluster is crucial. Unrestricted access can lead to unauthorized modifications or data breaches. Employing Role-Based Access Control (RBAC) allows you to granularly define permissions for users and service accounts, ensuring that only authorized entities can perform specific actions. This principle of least privilege significantly reduces the potential impact of compromised credentials.
- Implement Role-Based Access Control (RBAC) to manage user and service account permissions.
- Use least privilege principle: grant only necessary permissions to users and service accounts.
- Regularly audit and review user and service account permissions.
- Employ strong authentication mechanisms, such as multi-factor authentication (MFA).
Image Security
Container images form the foundation of your Kubernetes deployments. Vulnerable images can easily compromise your entire cluster. Employing robust image scanning and securing your image registry are vital steps in maintaining a secure environment. Consider using tools that automatically scan images for known vulnerabilities before deployment.
- Use a secure container registry with access control and vulnerability scanning capabilities.
- Employ automated image scanning to detect vulnerabilities before deployment.
- Utilize immutable images to minimize the risk of post-deployment modifications.
- Maintain an up-to-date inventory of your container images and their associated vulnerabilities.
Security-Hardened Kubernetes Distribution
Choosing a security-hardened Kubernetes distribution provides a solid foundation for your security posture. These distributions often include built-in security features, such as enhanced auditing and security controls, reducing the need for manual configuration and minimizing the risk of misconfiguration. Examples include distributions that prioritize security features and offer regular security updates.
- Select a Kubernetes distribution with a strong security track record and regular security updates.
- Utilize features such as built-in security scanning and auditing capabilities.
- Ensure the distribution aligns with your security requirements and compliance standards.
Last Point
Securing your Kubernetes environment against critical vulnerabilities requires a proactive and multi-faceted approach. By combining robust vulnerability scanning, proactive mitigation strategies, and a well-defined incident response plan, you can significantly reduce your exposure to risk. Remember, staying updated on the latest security best practices and regularly auditing your infrastructure are vital steps in safeguarding your applications and data. Don’t wait until it’s too late – take control of your Kubernetes security today.





