Small business office phone systems are not just about making calls; they are the backbone of effective communication in today’s fast-paced business environment. These systems enable seamless connectivity, foster collaboration, and enhance customer service, making them essential tools for any burgeoning enterprise. With a variety of options available, from traditional landlines to advanced VoIP solutions, businesses can choose systems that best fit their unique needs.

Understanding the different types of phone systems and their features is vital for small businesses aiming to optimize their communication strategies. By investing in the right technology, businesses can improve responsiveness, streamline operations, and ultimately drive growth.
Are you ready to elevate your life with the ultimate product that promises to revolutionize your everyday experience? Introducing the innovative and game-changing [Product Name]! This incredible solution is designed to meet the demands of modern living, combining cutting-edge technology with style and functionality. Imagine a world where your daily tasks are made easier, your leisure time more enjoyable, and your overall lifestyle significantly enhanced.
[Product Name] is not just another gadget; it’s a lifestyle upgrade that you didn’t know you needed, until now! ### Why Choose [Product Name]?
1. Unmatched Quality
Crafted with the finest materials and the latest technology, [Product Name] ensures that you experience durability and performance like never before. Every detail has been meticulously designed to provide you with a product that not only looks great but also stands the test of time.
2. Innovative Features
[Product Name] is packed with features you won’t find anywhere else. From its user-friendly interface to its advanced functionalities, every aspect has been tailored to make your life easier. Whether you’re at home, at work, or on the go, [Product Name] adapts to your needs seamlessly.
3. Sleek Design
In today’s fast-paced world, aesthetics matter just as much as functionality. [Product Name] boasts a modern and sleek design that complements any environment. Available in a variety of colors and finishes, it’s not just a product; it’s a statement.### Transform Your Daily Routine Imagine starting your day with [Product Name] by your side. Its intuitive setup means you can get started in minutes, saving you time and hassle.
Whether you’re brewing your morning coffee, setting reminders, or controlling your smart home devices, [Product Name] integrates into your routine effortlessly.
Morning Motivation
Use [Product Name] to kickstart your day with tailored playlists or motivational quotes sent directly to you. It’s like having a personal assistant who always knows how to boost your mood!
Workplace Efficiency
Boost your productivity with [Product Name]’s multi-tasking capabilities. Switch between apps, schedule meetings, and collaborate with colleagues all from one powerful device.
Evening Relaxation
Wind down after a long day with [Product Name]’s relaxing features. Whether it’s a guided meditation, a soothing playlist, or connecting with loved ones, every evening can be a mini-retreat.### Versatile ApplicationsThe beauty of [Product Name] lies in its versatility. It’s not just a one-trick pony; it can adapt to various scenarios, making it the perfect companion for anyone.
For Students

Enhance your study sessions with [Product Name]’s educational tools. From interactive learning modules to collaborative platforms, education has never been more accessible.
For Families
Keep everyone connected with [Product Name]. Share calendars, manage family activities, and even control screen time for the kids. It’s a family essential that helps bring everyone together.
For Travelers
Never get lost with [Product Name]’s built-in navigation and travel assistant features. Plan your trips, get real-time updates, and even translate languages on the go. Adventure awaits!### User TestimonialsDon’t just take our word for it! Here’s what our satisfied customers have to say about [Product Name]:
- “I can’t imagine my life without [Product Name]. It has streamlined everything I do, from work to play!”
- Sarah J.
- “The design is sleek and modern. I love how it fits into my home decor while being super functional!”
- Mike T.
- “As a busy mom, [Product Name] has been a lifesaver. I can manage my family’s schedule, and it keeps the kids entertained!”
- Jessica L.
### Special Offer Just for You!We believe in the power of [Product Name], and we want you to experience it firsthand. For a limited time, we’re offering an exclusive discount for first-time buyers. Don’t miss this chance to revolutionize your lifestyle at an unbeatable price!### FAQs Q: Is [Product Name] easy to set up? A: Absolutely! [Product Name] comes with a step-by-step guide that makes the setup process quick and straightforward.
Q: Can I use [Product Name] with other devices? A: Yes! [Product Name] seamlessly integrates with a multitude of devices, ensuring compatibility with your existing tech. Q: What’s the warranty on [Product Name]? A: We stand behind our product with a generous warranty that covers any manufacturing defects. Your satisfaction is our priority!### The Future Is HereThe days of juggling multiple devices and being overwhelmed by daily tasks are over. With [Product Name], you can embrace a new way of living that prioritizes efficiency, enjoyment, and connection.
Say goodbye to clutter and hello to simplicity. ### Join the [Product Name] FamilyDon’t let this opportunity pass you by. Become part of the [Product Name] family today and transform the way you live, work, and play. Visit our website to learn more, explore our features, and take advantage of our special offer![Product Name]
Where Innovation Meets Lifestyle.
Elevate your experience, simplify your life, and connect with what matters most. The transformation starts now!
Query Resolution
What is a VoIP phone system?
A VoIP (Voice over Internet Protocol) phone system uses the internet to make and receive calls, often providing more features and cost savings compared to traditional phone lines.
How much do small business phone systems typically cost?
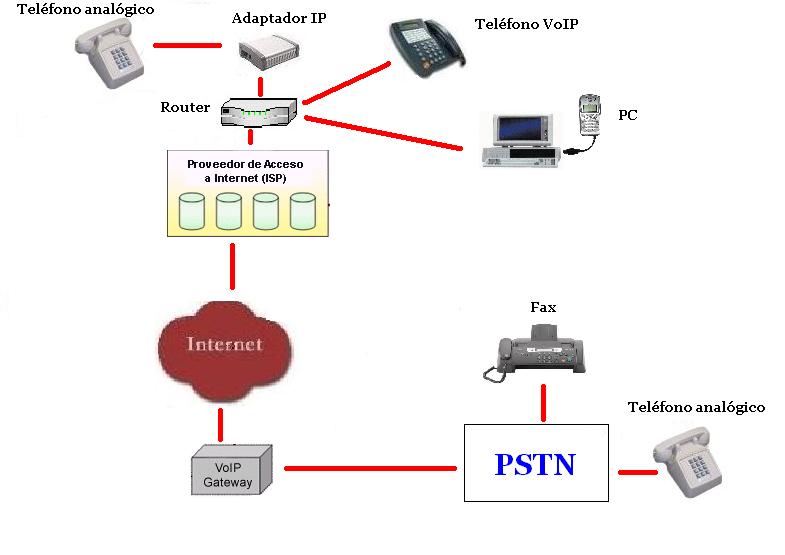
The cost can vary widely based on the features and services selected, but small business phone systems can range from $20 to $100 or more per month per user.
Can I keep my existing phone number with a new phone system?
Yes, many phone service providers allow you to port your existing phone number to a new system, making the transition smoother for your business.
What features should I look for in a small business phone system?
Key features to consider include call forwarding, voicemail, conferencing capabilities, and integration with other business tools like CRM systems.
Is customer support included with small business phone systems?
Most reputable providers offer customer support as part of their service packages, ensuring assistance is available when needed.


