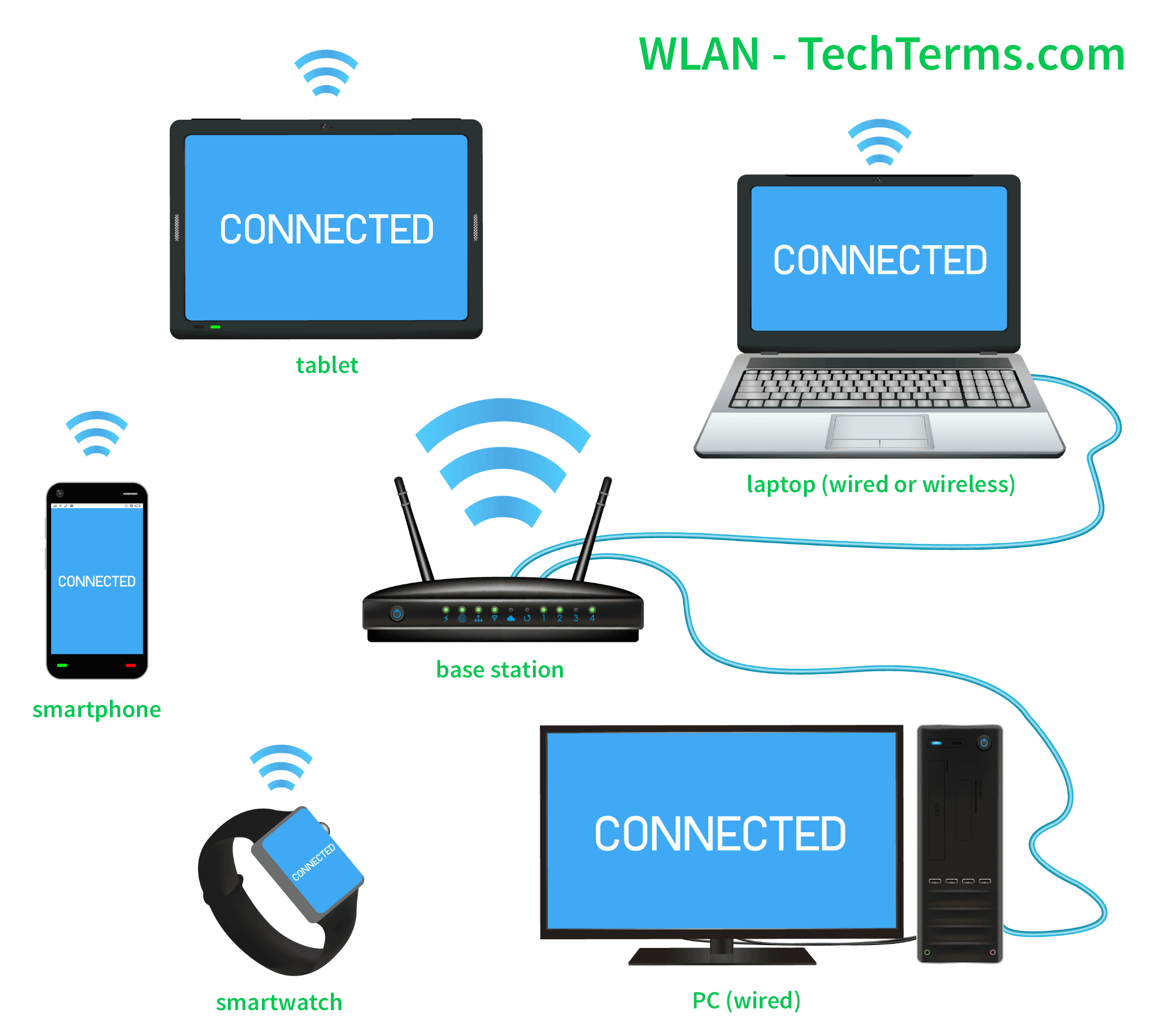
Introducing small office phone systems, your gateway to streamlined communication and enhanced productivity. With the right phone system, you can connect effortlessly with your clients and team, ensuring that every call counts. Discover how modern solutions can transform your small office into a hub of efficiency and collaboration, perfectly tailored to meet your business needs.
These systems not only offer reliable connectivity but also come equipped with advanced features such as voicemail, call forwarding, and conferencing capabilities. Embrace the technology that fosters clear communication, making it easier than ever to manage your business operations effectively.
Are you tired of spending hours cleaning your home, only to see it dirty again in a matter of days? The UltraClean 3000 is here to revolutionize your cleaning routine! With cutting-edge technology and user-friendly design, this innovative cleaning solution will transform your lifestyle and give you the free time you deserve.
Why Choose the UltraClean 3000?
Imagine a world where cleaning your home is as easy as pressing a button. The UltraClean 3000 makes that dream a reality! With its advanced features, this device offers unparalleled performance and convenience. Here’s why it’s the must-have cleaning tool of the year:
- Smart Technology: Equipped with AI-driven sensors, the UltraClean 3000 automatically adjusts its cleaning mode based on the surface type and level of dirt, ensuring optimal performance every time.
- Powerful Suction: Say goodbye to dirt and allergens! Our powerful suction technology eliminates even the most stubborn particles, leaving your home spotless and fresh.
- Eco-Friendly: The UltraClean 3000 is designed with the environment in mind. It uses energy-efficient components and eco-friendly cleaning solutions, making your home cleaner and greener.
- Self-Cleaning Mechanism: Enjoy a hassle-free cleaning experience! The UltraClean 3000 features a self-cleaning function, reducing maintenance and ensuring your device is always ready to tackle any mess.
Features That Will Blow Your Mind!
The UltraClean 3000 isn’t just another cleaning device; it’s a lifestyle upgrade! Here are some of the standout features that set it apart from the competition:
1. Multi-Surface Capability
From hardwood floors to carpets, tiles to upholstery, the UltraClean 3000 can handle it all! Its versatile design adapts to different surfaces, allowing you to clean every nook and cranny of your home effortlessly.
2. Voice Activation
Cleaning has never been easier! With built-in voice recognition, you can simply command the UltraClean 3000 to start, stop, or change modes without lifting a finger. Imagine how much easier your life will be!
3. Smart Home Integration
Seamlessly connect the UltraClean 3000 with your smart home devices. Schedule cleanings through your smartphone or sync it with your virtual assistant. Control your cleaning schedule from anywhere, anytime!
4. Long Battery Life
No more interruptions! The UltraClean 3000 boasts an impressive battery life, allowing it to clean for hours on end without needing a recharge. Get your cleaning done in one go, and enjoy your newfound time!
How Does It Work?
The UltraClean 3000 utilizes an intricate system of brushes, sensors, and suction power to provide a thorough cleaning experience. Here’s a step-by-step breakdown:
- Preparation: Simply charge the device for a few hours prior to use. Once charged, position it in your desired starting area.
- Voice Command: Use the voice activation feature or the mobile app to command the UltraClean 3000 to start cleaning.
- Automatic Navigation: The device scans the room using its AI sensors, determining the best cleaning path while avoiding obstacles.
- Efficient Cleaning: The UltraClean 3000 uses powerful suction and rotating brushes to pick up dirt and debris from all surfaces.
- Self-Cleaning: After each cleaning session, the device activates its self-cleaning feature, ensuring it remains in top condition for your next use.
Testimonials: What Our Happy Customers Are Saying
Don’t just take our word for it! Here’s what some of our satisfied customers have to say about their UltraClean 3000 experience:
“I was skeptical at first, but the UltraClean 3000 has changed my life! I can finally spend more time with my kids instead of cleaning all day.” – Sarah J.
“The voice activation feature is a game-changer! I can start cleaning while I’m cooking dinner. It’s so convenient!” – Mike T.
“I love that it’s eco-friendly! I can clean my home without harming the environment. Highly recommend!” – Emily R.
Limited Time Offer: Get Yours Today!
Don’t miss out on the chance to transform your cleaning routine forever! For a limited time only, purchase the UltraClean 3000 at a special discounted price. Experience the future of home cleaning and reclaim your time!
Order Now and Enjoy Exclusive Benefits!
- Free Shipping: Enjoy complimentary shipping on your order, directly to your doorstep.
- 30-Day Money-Back Guarantee: Try the UltraClean 3000 risk-free! If you’re not completely satisfied, return it within 30 days for a full refund.
- Extended Warranty: Your investment is protected with our extended warranty option, ensuring longevity and support.
Conclusion: Join the Cleaning Revolution!
The UltraClean 3000 is more than just a cleaning device; it’s an investment in your time, health, and happiness. Say goodbye to tedious cleaning routines and hello to a cleaner, more organized home. With its smart features and powerful performance, you’ll wonder how you ever lived without it!
Ready to take the plunge? Click the link below to order your UltraClean 3000 now and start enjoying a cleaner home today!
Order Your UltraClean 3000 Now!
Transform your cleaning experience and embrace the future with the UltraClean 3000!
Answers to Common Questions
What are small office phone systems?
Small office phone systems are communication solutions designed specifically for small businesses, offering features like call handling, voicemail, and conferencing.
How do I choose the right small office phone system?
Consider factors such as the number of users, desired features, budget, and whether you prefer a cloud-based or on-premise solution.
Can small office phone systems integrate with other software?
Yes, many systems offer integration with CRM software, email, and other business applications to enhance productivity.
Are small office phone systems cost-effective?
Yes, they are designed to provide essential communication tools at a lower cost compared to traditional phone systems.
What support options are available for small office phone systems?
Most providers offer technical support, installation assistance, and online resources to help users maximize their phone system’s potential.




