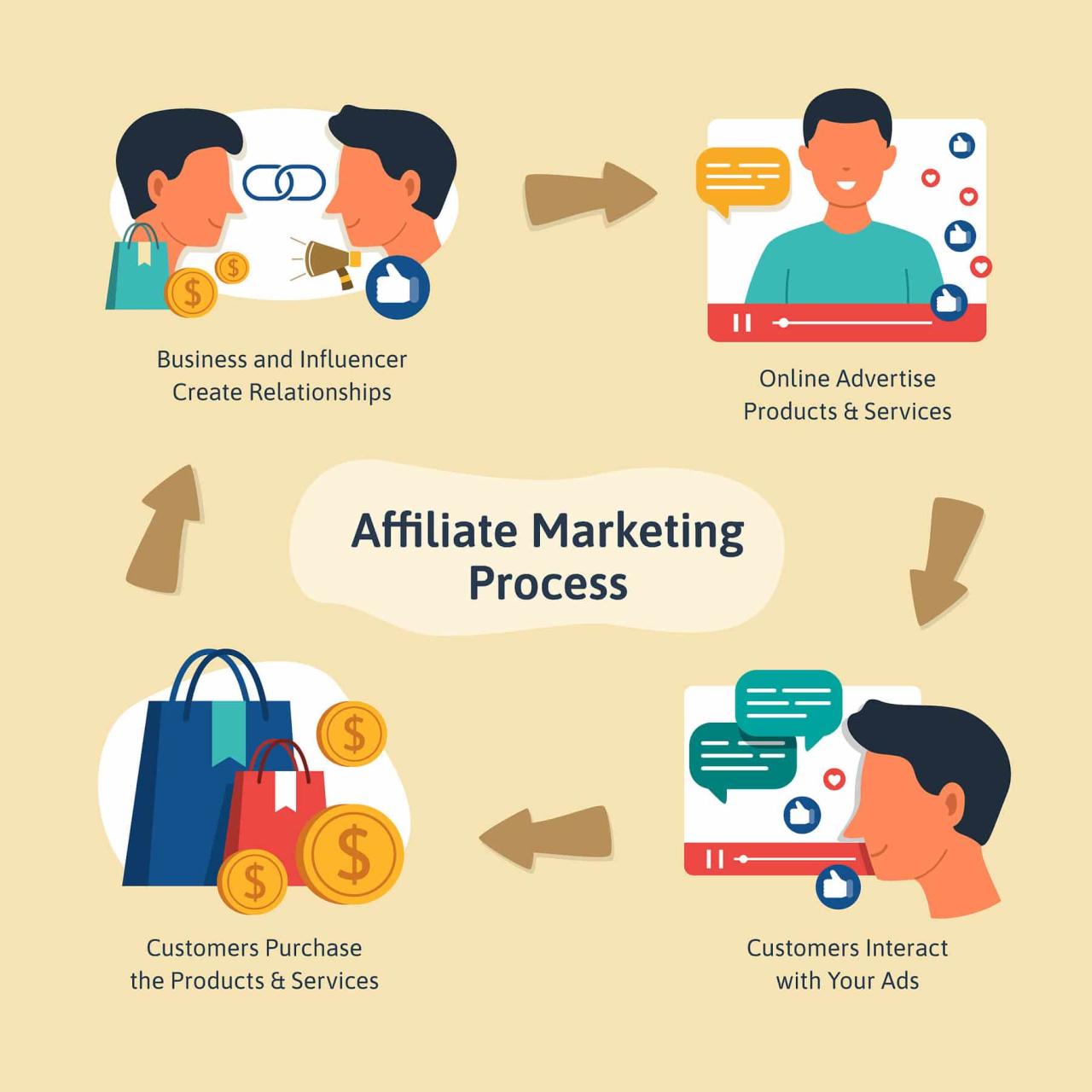
Welcome to the world of spokane heating and air conditioning, where your comfort is our top priority! Experience the perfect blend of innovation and reliability as we offer state-of-the-art solutions tailored to meet your home and business needs. Our expertise in heating and air conditioning ensures a cozy, climate-controlled environment all year round.
With a commitment to quality service, Spokane Heating and Air Conditioning stands out as a trusted provider, ready to tackle any temperature challenge. Whether you’re seeking efficient heating for those chilly winters or a refreshing cool breeze during hot summers, we’ve got you covered with our wide range of services and products designed for ultimate customer satisfaction.
Are you ready to transform your life? Introducing the latest innovation that’s about to change the way you think about products in your daily routine! Our new product is designed with YOU in mind, helping you unlock your true potential and achieve your goals like never before.
What Makes Our Product Stand Out?
In a world overflowing with options, what separates our product from the rest? It’s simple! Our unique features, cutting-edge technology, and user-friendly design make it the ultimate choice for anyone looking to enhance their lifestyle.
- Innovative Design: Our product boasts a sleek and modern look, making it not only functional but also a stylish addition to your daily arsenal.
- User-Friendly: Say goodbye to complicated setups. With our intuitive interface, you can start using it right out of the box!
- Top-Notch Quality: Made with premium materials, our product is built to last, ensuring you get the most value for your investment.
- Eco-Friendly: We care about the planet! Our product is made with sustainable practices, so you can feel good about your purchase.
How It Works
Our product integrates seamlessly into your life. With advanced technology that adapts to your specific needs, you will experience enhanced efficiency and productivity. Whether you’re at home, at work, or on the go, our product guarantees to make your daily tasks easier and more enjoyable.
Imagine a day where you can complete your tasks faster, enjoy your leisure time more, and feel accomplished at every hour. This is no longer a dream; it’s a reality with our product. With just a few simple steps, you’ll be on your way to a more organized and efficient lifestyle.
Testimonials from Happy Customers
Don’t just take our word for it! Here’s what some of our satisfied customers have to say:
“This product has changed my life completely. I never knew I needed it until I tried it! Highly recommend!”
-Sarah L.
“I was skeptical at first, but after using it for just a week, I can’t imagine my life without it now!”
-John D.
“A game changer! It’s made my daily routine much more manageable and enjoyable!”
-Emma T.
Get Yours Today!
What are you waiting for? Elevate your lifestyle by getting your own unit of our revolutionary product. Available online for a limited time only, we are offering an exclusive discount for early adopters. Don’t miss out on this incredible opportunity to invest in yourself and your future!
Simply click the button below to secure your order, and join thousands of satisfied customers who have transformed their lives with our product!
Frequently Asked Questions (FAQs)
1. How do I use the product?
Using our product is a breeze! Just follow the user manual included in the package, and you’ll be up and running in no time.
2. Is there a warranty?
Absolutely! We offer a comprehensive warranty to ensure your satisfaction and peace of mind.
3. Can I return the product if I’m not satisfied?
Yes, we have a hassle-free return policy. If for any reason you’re not satisfied, you can return the product within 30 days for a full refund!
Join the Movement!
Be a part of the community that is embracing change and striving for excellence. Connect with us on social media to stay updated on the latest tips, tricks, and product launches. Join the conversation and share your journey with others who are just as passionate about improving their lives!
Follow us on:
Final Thoughts
Transform your life with our innovative product that is designed to help you succeed. Don’t wait another moment to take control of your future. Seize this chance to make a change that will lead to a happier, more fulfilled you.
Join the thousands of satisfied customers who have already taken the leap. Remember, investing in yourself is the best decision you can make. Get ready to experience life at its fullest with our revolutionary product!
FAQ Overview
What types of heating systems do you install?

We install a variety of heating systems, including furnaces, heat pumps, and radiant heating systems, tailored to fit your specific needs.
How often should I service my HVAC system?
For optimal performance, it’s recommended to service your HVAC system at least once a year, ideally before the peak heating or cooling season.
Do you offer emergency HVAC services?
Yes, we provide 24/7 emergency HVAC services to ensure your comfort is never compromised.
What brands do you service?
We service all major brands of heating and air conditioning equipment, ensuring that we can meet your specific requirements.
Can I finance my HVAC installation?
Absolutely! We offer flexible financing options to make your HVAC installation more accessible.