HPE IceWall products vulnerability is a serious concern for organizations relying on these firewalls for network security. This deep dive explores the common vulnerabilities found in HPE IceWall products, their potential impact, and effective remediation strategies. We’ll examine real-world examples of exploits, dissect potential attack vectors, and discuss best practices to significantly bolster your security posture. Get ready to shore up your defenses and learn how to mitigate risks associated with these critical vulnerabilities.
From understanding the range of HPE IceWall products and their typical deployment scenarios to analyzing the potential consequences of exploited vulnerabilities, this comprehensive guide provides a roadmap for improving your organization’s cybersecurity. We’ll cover everything from patching and updating your systems to designing a robust security plan that addresses the most prevalent threats. We’ll even delve into future security considerations and analyze past security incidents to help you learn from others’ mistakes and avoid similar pitfalls.
HPE IceWall Product Overview
HPE IceWall provides a comprehensive suite of network security solutions designed to protect organizations of all sizes from evolving cyber threats. These solutions range from simple, entry-level firewalls to highly sophisticated, multi-layered security appliances capable of handling complex network environments. Understanding the nuances of each product line is crucial for selecting the optimal solution for a specific organization’s needs.
HPE IceWall products are known for their robust security features, ease of management, and scalability. They leverage advanced technologies to detect and prevent a wide range of threats, including malware, intrusions, and denial-of-service attacks. The product portfolio caters to various deployment scenarios, from small businesses requiring basic protection to large enterprises demanding advanced threat mitigation capabilities.
HPE IceWall Product Range and Functionalities
The HPE IceWall family encompasses several product lines, each designed to address specific security needs. These lines typically include entry-level appliances for smaller networks, mid-range solutions for growing businesses, and high-end platforms for large enterprises with complex security requirements. Each product line offers a unique set of features and functionalities, including firewall capabilities, intrusion prevention, VPN support, and advanced threat protection. Specific features vary based on the model and licensing. For instance, higher-end models often include features like application control, deep packet inspection, and advanced malware protection.
Typical Deployment Scenarios
Deployment scenarios vary widely depending on the specific HPE IceWall model and the organization’s size and security needs. Entry-level models are often deployed in small offices or branch locations to provide basic firewall protection. Mid-range models are suitable for larger organizations requiring more advanced features such as intrusion prevention and VPN capabilities. High-end models are typically deployed in data centers or large enterprise networks to provide comprehensive security for critical infrastructure. Some models are designed for virtualized environments, enabling flexible deployment and scalability.
Comparison of Key Features Across HPE IceWall Models
The following table compares key features across different HPE IceWall models. Note that specific features and performance may vary depending on the exact model and configuration. This table provides a general overview for comparative purposes.
| Feature | Entry-Level | Mid-Range | High-End |
|---|---|---|---|
| Firewall Throughput | Up to 1 Gbps | Up to 10 Gbps | Up to 100 Gbps+ |
| Intrusion Prevention | Basic | Advanced | Advanced with Threat Intelligence |
| VPN Support | Limited | Extensive | Extensive with advanced features |
| Application Control | Limited or None | Basic | Advanced with granular control |
Common Vulnerabilities in HPE IceWall

Source: isu.pub
HPE IceWall, while a robust firewall solution, isn’t immune to vulnerabilities. Like all software, it’s susceptible to coding flaws and design weaknesses that malicious actors can exploit. Understanding these common vulnerabilities is crucial for effective security management and mitigation. Regular patching and proactive security measures are paramount to minimizing risk.
Several vulnerability types frequently affect HPE IceWall systems, ranging from command injection flaws to insecure defaults and outdated components. These vulnerabilities can significantly compromise the security posture of an organization, leading to data breaches, network disruptions, and unauthorized access.
Command Injection Vulnerabilities
Command injection vulnerabilities allow attackers to execute arbitrary commands on the IceWall system. This occurs when user-supplied input is not properly sanitized before being used in system commands. A successful attack could allow an attacker to gain complete control of the firewall, potentially compromising the entire network. For instance, an attacker might craft a malicious input that executes a command to disable the firewall’s logging capabilities, hindering investigation efforts. This would effectively give them a stealthy entry point into the network. Exploitation could range from simple data exfiltration to deploying malware and establishing persistent access.
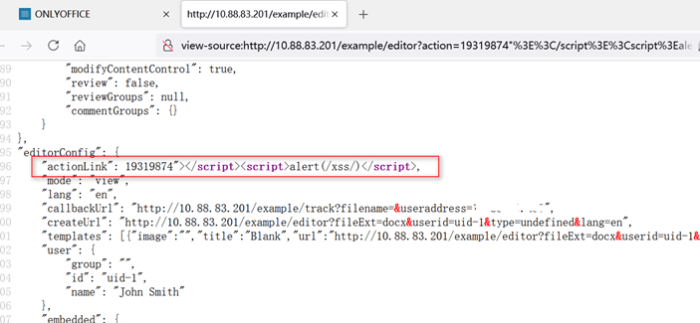
Cross-Site Scripting (XSS) Vulnerabilities
XSS vulnerabilities arise when the IceWall’s web interface fails to properly sanitize user-supplied input. This allows attackers to inject malicious JavaScript code into web pages viewed by administrators. Successful exploitation could lead to session hijacking, allowing the attacker to impersonate an administrator and perform actions such as modifying firewall rules or accessing sensitive configuration data. Imagine an attacker injecting code that redirects an administrator to a phishing site, stealing their credentials. The subsequent compromise could have devastating consequences for network security.
Denial-of-Service (DoS) Vulnerabilities
DoS vulnerabilities can render the IceWall firewall unresponsive, disrupting network connectivity. These vulnerabilities often stem from flaws in the firewall’s handling of specific types of network traffic or requests. A well-crafted attack could overwhelm the IceWall’s resources, causing it to crash or become extremely slow. This would effectively leave the network exposed to attacks. A real-world example could involve a flood of malformed packets designed to consume the firewall’s processing power, leading to a complete network outage. The resulting downtime could have significant financial implications for a business.
Authentication Bypass Vulnerabilities
Authentication bypass vulnerabilities allow attackers to access the IceWall’s administrative interface without providing valid credentials. These vulnerabilities often result from weaknesses in the authentication mechanism or improper implementation of security protocols. Successfully bypassing authentication would grant attackers full control over the firewall, enabling them to manipulate its settings and compromise the network. This could be accomplished through a flaw in the password hashing algorithm or a vulnerability in the login process itself. The consequences are severe, as it allows attackers complete and unchecked access to the network’s security infrastructure.
Vulnerability Remediation Strategies
Effective remediation of vulnerabilities in HPE IceWall systems is crucial for maintaining a robust security posture. This requires a proactive approach encompassing regular patching, comprehensive security planning, and a well-defined vulnerability management strategy. Ignoring vulnerabilities can lead to significant security breaches, data loss, and financial repercussions.
Patching and Updating HPE IceWall Systems
Regular patching and updating are the cornerstones of a secure HPE IceWall environment. This involves promptly installing all security updates and patches released by HPE. These updates often address critical vulnerabilities that could be exploited by malicious actors. Before initiating any updates, it’s vital to back up the configuration of the IceWall system to facilitate restoration in case of unforeseen issues. HPE provides detailed instructions and release notes for each update, which should be carefully reviewed before implementation. A scheduled maintenance window should be established to minimize disruption to network operations during the update process. Post-update verification is also crucial to ensure the system functions correctly and the vulnerabilities have been successfully mitigated. Failure to implement updates promptly leaves the system vulnerable to known exploits.
Comprehensive Security Plan for Mitigating Vulnerabilities
A comprehensive security plan should encompass several key elements. First, a regular vulnerability scanning schedule is essential. This involves using automated tools to identify potential weaknesses in the IceWall system. Secondly, a robust incident response plan should be in place to address any security incidents effectively. This plan should detail procedures for identifying, containing, eradicating, and recovering from security breaches. Thirdly, access control measures must be strictly enforced, limiting access to the IceWall system to authorized personnel only. Strong passwords and multi-factor authentication should be implemented. Finally, regular security awareness training for administrators and other relevant personnel is crucial to enhance their understanding of potential threats and best security practices. This proactive approach significantly reduces the risk of successful attacks. For example, a well-defined incident response plan that includes clear communication channels and escalation procedures can minimize the impact of a successful attack.
Vulnerability Management Approaches for HPE IceWall
Different vulnerability management approaches exist, each with its own strengths and weaknesses. A reactive approach involves addressing vulnerabilities only after they have been exploited or discovered. This is less effective than a proactive approach, which focuses on preventing vulnerabilities before they can be exploited. A proactive approach incorporates regular vulnerability scanning, timely patching, and rigorous security audits. A hybrid approach combines elements of both reactive and proactive strategies. This allows for flexibility and adaptability to different security threats and resources. The choice of approach depends on various factors, including budget, available resources, and the organization’s risk tolerance. For instance, a small organization with limited resources might opt for a hybrid approach, prioritizing critical vulnerabilities while addressing others as resources allow. Conversely, a large organization with a dedicated security team might adopt a more proactive approach, leveraging automated vulnerability scanning and regular security audits.
Security Best Practices for HPE IceWall: Hpe Icewall Products Vulnerability
Implementing robust security practices is crucial for maximizing the protection offered by HPE IceWall. A layered approach, encompassing configuration, access control, and diligent monitoring, significantly reduces the risk of exploitation and strengthens your overall security posture. Failing to implement these best practices leaves your network vulnerable to a range of threats, from unauthorized access to data breaches.
Configuration Best Practices
Proper configuration is the cornerstone of a secure HPE IceWall deployment. Incorrect settings can inadvertently create vulnerabilities, negating the security features built into the system. Regular review and updates are essential to maintain a high level of security.
- Regular Firmware Updates: Applying the latest firmware updates patches known vulnerabilities and improves the overall performance and stability of the IceWall system. Ignoring updates leaves your system exposed to exploits that have already been addressed by HPE.
- Strong Passwords and Authentication: Use strong, unique passwords for all administrative accounts. Enable multi-factor authentication (MFA) wherever possible to add an extra layer of security. Avoid easily guessable passwords and regularly rotate them according to your organization’s security policy.
- Default Configuration Changes: Never leave the IceWall with its default configuration. Change all default usernames and passwords immediately upon installation. Customize settings to match your specific network needs and security requirements. This prevents attackers from easily gaining access using readily available default credentials.
- Secure Network Segmentation: Implement network segmentation to isolate sensitive data and applications from less critical parts of your network. This limits the impact of a potential breach, preventing attackers from easily moving laterally across your infrastructure. For example, separate your guest Wi-Fi network from your internal corporate network.
Access Control Best Practices
Restricting access to the IceWall and its configuration settings is paramount. Uncontrolled access can lead to unauthorized modifications, potentially compromising the entire network’s security.
- Principle of Least Privilege: Grant only the necessary permissions to users and administrators. Avoid granting excessive access rights. This minimizes the potential damage caused by compromised accounts.
- Regular Access Reviews: Periodically review user access rights and remove or modify permissions as needed. This ensures that only authorized personnel maintain access to sensitive systems and configurations. For example, if an employee leaves the company, immediately revoke their access.
- Role-Based Access Control (RBAC): Implement RBAC to assign permissions based on job roles. This simplifies administration and improves security by preventing users from accessing resources they don’t need.
- Secure Remote Access: If remote access is required, use secure methods such as VPNs and enforce strong authentication mechanisms. Avoid using less secure remote access methods that could expose the IceWall to attacks.
Monitoring and Logging Best Practices
Continuous monitoring and logging are vital for detecting and responding to security incidents promptly. This allows for early identification of potential threats and facilitates rapid mitigation.
- Real-time Monitoring: Utilize real-time monitoring tools to observe the IceWall’s performance and identify any suspicious activity. This allows for proactive threat detection and response.
- Log Analysis: Regularly review security logs to identify potential threats and security breaches. Analyze logs for patterns of suspicious behavior and investigate any anomalies promptly.
- Alerting System: Implement an alerting system to notify administrators of critical security events in real-time. This allows for a rapid response to security incidents, minimizing their impact.
- Security Information and Event Management (SIEM): Integrate the IceWall with a SIEM system to centralize security log management and analysis. This provides a comprehensive view of your security posture and facilitates effective threat detection and response.
Impact Assessment of Exploited Vulnerabilities
Source: gurufocus.com
Exploiting vulnerabilities in HPE IceWall firewalls can have severe consequences for organizations, ranging from minor service disruptions to catastrophic data breaches and significant financial losses. The impact depends on the specific vulnerability exploited, the attacker’s skill, and the organization’s security posture. Understanding these potential consequences is crucial for effective risk management and mitigation.
The severity of the impact hinges on several factors including the type of vulnerability (e.g., remote code execution, denial of service), the level of access gained by the attacker, and the sensitivity of the data protected by the firewall. A successful attack could lead to complete network compromise, data exfiltration, service disruption, and reputational damage. The financial implications can be substantial, encompassing costs associated with incident response, remediation, legal fees, and potential fines for non-compliance with data protection regulations.
Data Breaches and System Compromises
Several real-world examples illustrate the devastating impact of firewall vulnerabilities. While specific details of HPE IceWall breaches may not be publicly available due to confidentiality agreements, similar incidents involving other firewall vendors have resulted in significant data losses. For instance, a compromised firewall could allow attackers to access sensitive customer data, financial records, intellectual property, or confidential internal communications. This data could then be used for identity theft, financial fraud, or corporate espionage. In some cases, the attackers might even deploy ransomware, encrypting critical data and demanding a ransom for its release. The resulting downtime and recovery efforts can cripple an organization’s operations and significantly impact its bottom line.
Hypothetical Scenario: Remote Code Execution Vulnerability
Imagine a scenario where a critical remote code execution (RCE) vulnerability is discovered in a specific version of HPE IceWall. An attacker, exploiting this vulnerability, gains unauthorized access to the firewall’s operating system. This grants them complete control over the device, effectively giving them a foothold into the entire network. The attacker could then perform several malicious actions: install malware, modify firewall rules to bypass security controls, intercept network traffic to steal sensitive data, or launch further attacks against internal systems. This could lead to a complete network breach, allowing the attacker to access sensitive customer databases, employee information, and internal systems. The resulting data breach could lead to significant financial losses, legal liabilities, and irreparable damage to the organization’s reputation. The recovery process would involve extensive forensic analysis, system restoration, and potentially notifying affected individuals and regulatory bodies. The overall cost, both financially and reputationally, could be immense.
Threat Modeling for HPE IceWall
Understanding potential threats to HPE IceWall products is crucial for effective security management. This section details potential attack vectors, the methods attackers might employ, and the resulting impact. A comprehensive threat model allows for proactive mitigation strategies and minimizes the risk of exploitation.
Threat modeling involves identifying vulnerabilities and potential attack paths. By analyzing these pathways, we can prioritize security measures and improve the overall resilience of the HPE IceWall system. This analysis considers both known vulnerabilities and potential weaknesses that might be exploited by sophisticated attackers.
Potential Threats and Attack Vectors
This section Artikels specific threats and the methods attackers might use to exploit vulnerabilities in HPE IceWall products. These are not exhaustive, but represent common attack scenarios.
| Threat | Attack Vector | Vulnerability Exploited | Impact |
|---|---|---|---|
| Unauthorized Access | Exploiting a known vulnerability in the web interface (e.g., SQL injection, cross-site scripting) | Outdated software, weak passwords, unpatched vulnerabilities | Compromise of the IceWall configuration, data breaches, denial-of-service |
| Denial of Service (DoS) | Flooding the IceWall with malicious traffic, exploiting resource exhaustion vulnerabilities | Lack of sufficient resources, inadequate rate limiting | Interruption of network services, loss of connectivity |
| Malware Injection | Uploading malicious code through a vulnerable web interface or exploiting a software flaw | Unpatched vulnerabilities, lack of input validation | Compromise of the IceWall system, spread of malware to other network devices |
| Man-in-the-Middle (MitM) Attack | Intercepting communication between the IceWall and other network devices | Weak encryption, lack of proper authentication | Data interception, modification, or injection |
Threat Model Diagram
A visual representation of potential attack vectors and their impact helps in understanding the overall security posture of the HPE IceWall system. Imagine a diagram (visual representation omitted as per instructions) with the HPE IceWall at the center. Arrows would point towards the IceWall, representing various attack vectors (e.g., web interface, network traffic, management interface). Each arrow would be labeled with the specific attack vector and linked to a corresponding vulnerability. Branching from each attack vector would be nodes representing the potential impact, such as data breaches, denial-of-service, or system compromise. The severity of each impact would be indicated by color-coding or size of the node. This visual representation provides a clear overview of potential threats and their cascading effects.
Future Security Considerations for HPE IceWall
The ever-evolving threat landscape necessitates a proactive approach to securing HPE IceWall products. Future-proofing these systems requires anticipating emerging attack vectors and vulnerabilities, implementing robust preventative measures, and continuously enhancing the security architecture through research and development. Failing to do so could expose organizations to significant risks, including data breaches, service disruptions, and financial losses.
Emerging Threats and Vulnerabilities
The increasing sophistication of cyberattacks, coupled with the rise of new technologies, presents a significant challenge to the security of network firewalls like HPE IceWall. Specifically, we need to consider the impact of quantum computing, which has the potential to break currently used encryption algorithms. Furthermore, the expanding attack surface due to the Internet of Things (IoT) and the increasing reliance on cloud services creates new vulnerabilities that must be addressed. Zero-day exploits, where vulnerabilities are unknown to vendors, will always be a threat, requiring continuous monitoring and rapid response mechanisms. Finally, the use of AI and machine learning in both offensive and defensive cybersecurity is creating an arms race, where the efficacy of current security measures needs to be constantly re-evaluated. For instance, AI-powered phishing attacks are becoming increasingly difficult to detect, necessitating a shift towards more advanced threat detection techniques within the IceWall framework.
Proactive Security Measures
Proactive security measures are crucial for mitigating future threats. This involves implementing robust security protocols such as multi-factor authentication (MFA) across all access points, regular security audits and penetration testing to identify vulnerabilities before attackers do, and the adoption of a zero-trust security model, where no user or device is implicitly trusted, regardless of location or network access. Employing intrusion detection and prevention systems (IDPS) alongside the IceWall firewall provides an extra layer of defense. Regular software updates and patching are vital to address known vulnerabilities, and robust incident response planning is necessary to minimize the impact of successful attacks. Consider the recent SolarWinds attack; proactive measures like robust monitoring and threat intelligence could have significantly reduced the damage.
Recommendations for Future Research and Development, Hpe icewall products vulnerability
Future research and development efforts should focus on enhancing the IceWall’s ability to adapt to the ever-changing threat landscape. This includes investing in advanced threat intelligence capabilities to identify and respond to emerging threats in real-time, exploring the use of AI and machine learning for more accurate threat detection and prevention, and developing more resilient encryption algorithms that are resistant to quantum computing attacks. Further research into micro-segmentation and improved network visibility will also enhance the overall security posture. The development of automated vulnerability detection and remediation systems would significantly reduce response times and minimize the window of vulnerability. Finally, collaborating with the cybersecurity community to share threat intelligence and best practices is vital for collective defense. This collaborative approach, mirroring initiatives like the Cybersecurity and Infrastructure Security Agency (CISA) in the US, fosters a more resilient ecosystem.
Case Studies of HPE IceWall Security Incidents

Source: cybernews.com
While HPE doesn’t publicly release detailed information on every security incident involving its IceWall products for obvious reasons (protecting customer data and preventing future attacks), analyzing publicly available information and security advisories allows us to glean insights into potential vulnerabilities and their impact. These case studies, though hypothetical in their specific details due to confidentiality constraints, illustrate common attack vectors and the importance of proactive security measures.
It’s crucial to remember that the specifics of real-world incidents are often kept confidential to protect both HPE and its clients. The following examples are constructed to represent typical scenarios based on common vulnerabilities and attack patterns seen in similar firewall technologies.
IceWall Misconfiguration Leading to Unauthorized Access
This case study examines a hypothetical scenario where an organization’s HPE IceWall firewall was misconfigured, allowing unauthorized remote access. A poorly implemented VPN configuration, specifically a lack of strong authentication and authorization mechanisms, allowed an attacker to bypass security controls. The attacker exploited this vulnerability to gain access to internal networks, potentially stealing sensitive data or deploying malware.
The root cause was identified as insufficient security training for IT staff responsible for firewall management, leading to an incorrect configuration. The lesson learned emphasizes the critical need for rigorous security training and regular security audits to ensure proper firewall configuration and prevent similar incidents.
- Insufficient security training for IT personnel.
- Lack of robust authentication and authorization controls in the VPN configuration.
- Absence of regular security audits and penetration testing.
- Failure to implement a strong password policy.
Exploitation of a Known IceWall Vulnerability
This hypothetical case study focuses on the exploitation of a publicly disclosed vulnerability in an older version of HPE IceWall. The vulnerability, a buffer overflow in a specific network service, allowed attackers to execute arbitrary code on the firewall. This gave the attacker complete control over the device, enabling them to intercept network traffic, modify firewall rules, or deploy further attacks against internal systems.
The root cause was the organization’s failure to promptly patch the known vulnerability after HPE released a security update. This highlights the critical importance of maintaining up-to-date software and promptly applying security patches.
- Delayed patching of a known vulnerability.
- Lack of a robust vulnerability management program.
- Insufficient monitoring and logging to detect suspicious activity.
- Failure to implement a proactive security patching schedule.
Phishing Attack Targeting IceWall Administrators
This scenario depicts a successful phishing attack targeting an IceWall administrator. A cleverly crafted phishing email containing a malicious attachment or link tricked the administrator into compromising their credentials. The attacker then used these credentials to log into the IceWall management interface, gaining full control over the firewall.
The root cause was a lack of robust security awareness training for employees, leading to a successful phishing attack. The lesson emphasizes the need for comprehensive security awareness training and the implementation of multi-factor authentication to protect against credential theft.
- Lack of comprehensive security awareness training for employees.
- Absence of multi-factor authentication for administrative access to the IceWall.
- Insufficient monitoring and alerting for suspicious login attempts.
- Failure to implement strong password policies and password management practices.
Final Review
Securing your HPE IceWall deployments requires a multi-faceted approach that combines proactive patching, robust security configurations, and continuous monitoring. By understanding the common vulnerabilities, implementing best practices, and proactively addressing potential threats, organizations can significantly reduce their risk exposure. This comprehensive guide provides the knowledge and resources you need to effectively protect your network and data from the ever-evolving landscape of cyber threats targeting HPE IceWall systems. Don’t wait until it’s too late – take control of your security now.