Rockstar 2FA: Imagine a world where your GTA Online empire, meticulously built over countless hours, is safe from the clutches of digital thieves. Sounds dreamy, right? This isn’t some far-off fantasy; it’s the promise of robust two-factor authentication (2FA) for Rockstar Games accounts. We delve into the vital need for stronger security measures in the gaming world, exploring how 2FA can be a game-changer, and examining the potential pitfalls and solutions along the way. Get ready to level up your online security!
This deep dive examines Rockstar Games’ current security landscape, highlighting vulnerabilities and comparing their practices to industry giants. We’ll dissect various 2FA methods, their pros and cons, and design a user-friendly implementation for the Rockstar Games Launcher. We’ll also explore real-world attack scenarios, illustrating the critical role of 2FA in thwarting cybercriminals and safeguarding your hard-earned progress. We’ll discuss the balancing act between enhanced security and maintaining a smooth user experience.
Rockstar Games and Security Practices
Rockstar Games, the powerhouse behind iconic franchises like Grand Theft Auto and Red Dead Redemption, operates vast online gaming platforms with millions of active users. The security of these platforms and the associated player accounts is paramount, not just for protecting player data but also for maintaining the integrity and enjoyment of the gaming experience. However, the scale of their operations presents significant security challenges.
Rockstar’s current security infrastructure, while constantly evolving, relies on a multi-layered approach. This typically includes password protection, email verification, two-factor authentication (2FA), and potentially other measures like IP address monitoring and account lockout mechanisms after multiple failed login attempts. They also employ various methods to detect and mitigate common threats such as hacking, phishing, and unauthorized access. The exact details of their security measures, however, remain largely undisclosed for obvious security reasons.
Potential Vulnerabilities in Rockstar Games’ Security Systems
Despite Rockstar’s efforts, several potential vulnerabilities remain. Phishing attacks, where malicious actors impersonate Rockstar to trick players into revealing their login credentials, continue to pose a significant threat. The complexity of their online games also introduces potential vulnerabilities in their game servers and databases. Exploits within the game code itself could allow malicious actors to gain unauthorized access to player accounts or manipulate game data. Furthermore, the sheer volume of player data they handle makes them a prime target for large-scale data breaches. Any weakness in their data protection mechanisms could have devastating consequences.
Comparison of Rockstar Games’ Security Measures with Other Major Game Developers
Compared to other major game developers like Blizzard Entertainment or Epic Games, Rockstar’s public disclosures on their security practices are relatively limited. While many developers openly discuss their security protocols and investments in security technology, Rockstar maintains a more opaque approach. This makes direct comparison challenging. However, based on observable security incidents and industry best practices, it can be inferred that Rockstar’s security measures, while likely robust, might not always be as comprehensive or transparent as those of some competitors who actively promote their security initiatives.
Importance of Robust Security for Online Gaming Platforms
Robust security is not just a desirable feature for online gaming platforms; it’s a fundamental necessity. Player trust is directly tied to the security of their accounts and personal information. A major data breach or widespread hacking incident can severely damage a company’s reputation, leading to player attrition and significant financial losses. Beyond financial implications, compromised accounts can lead to in-game disruptions, unfair gameplay, and even real-world harm if personal information is leaked. Therefore, continuous investment in robust security measures, proactive threat detection, and transparent communication with players are crucial for the long-term health and success of any online gaming platform.
Two-Factor Authentication (2FA) Implementations
Source: medium.com
Rockstar Games, known for its immersive gaming experiences, needs equally robust security measures to protect its players’ accounts and data. Two-Factor Authentication (2FA) is a crucial element of this strategy, offering an extra layer of protection against unauthorized access. Choosing the right 2FA method and implementing it seamlessly within the Rockstar Games ecosystem is key to a positive user experience and enhanced security.
Different 2FA methods offer varying levels of security and convenience. Understanding these trade-offs is essential for Rockstar to make an informed decision.
Types of 2FA Methods and Their Characteristics
Several 2FA methods exist, each with its own advantages and disadvantages. The optimal choice depends on the specific security needs and user experience preferences.
- Time-Based One-Time Passwords (TOTP): TOTP generates a unique code that changes every 30 seconds, typically using an authenticator app like Google Authenticator or Authy. This method offers strong security and is widely adopted. However, it requires users to have a smartphone or other device with the authenticator app installed and functioning.
- Hardware Security Keys: These physical devices, like Yubikeys or similar, plug into a USB port or connect via NFC. They provide extremely strong security, as they are resistant to phishing attacks and are difficult to clone. The downside is the added cost and the need for users to carry and manage the physical key.
- SMS-Based 2FA: This method sends a verification code to the user’s registered mobile phone number. While convenient, it’s vulnerable to SIM swapping attacks, where a malicious actor gains control of the user’s phone number, rendering this method less secure than others.
- Email-Based 2FA: Similar to SMS, a verification code is sent to the user’s registered email address. This method is less secure than TOTP or hardware keys due to vulnerabilities like email spoofing and account compromise.
2FA Implementation within the Rockstar Games Ecosystem
Rockstar could leverage several points of integration for 2FA. A robust implementation would cover all key access points to the Rockstar Games ecosystem.
- Rockstar Games Launcher: Implementing 2FA at login to the launcher is paramount, protecting access to game libraries, purchases, and account settings.
- Social Club: Protecting access to the Social Club platform, where players connect, share content, and manage their profiles, is crucial. 2FA would significantly enhance security here.
- In-Game Purchases: For in-game purchases of virtual currency or items, 2FA adds an extra layer of protection against unauthorized transactions.
User Experience Implications of Different 2FA Methods
The user experience is critical. A poorly implemented 2FA system can frustrate players and lead to abandonment.
- TOTP: While secure, requires users to download and use an authenticator app, adding a step to the login process. Clear instructions and support are vital.
- Hardware Security Keys: Requires a physical device, increasing setup complexity. However, the enhanced security might outweigh this inconvenience for high-value accounts.
- SMS/Email-Based 2FA: Convenient, but less secure, requiring careful consideration of the trade-off between ease of use and security.
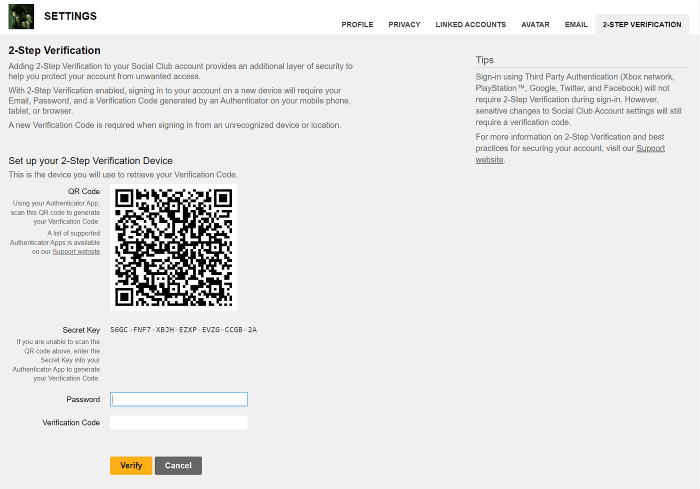
Rockstar Games Launcher 2FA UI Flow
A user-friendly implementation is crucial. The following Artikels a potential UI flow for enabling 2FA within the Rockstar Games Launcher:
1. Settings Menu: The user navigates to the account settings within the launcher.
2. Security Tab: A dedicated “Security” tab displays available security options, prominently featuring 2FA setup.
3. 2FA Method Selection: The user chooses their preferred 2FA method (TOTP, Hardware Key, etc.). Clear descriptions of each method’s security and convenience are provided.
4. Method-Specific Setup: Guided instructions are provided, depending on the selected method. For TOTP, a QR code is displayed for scanning with an authenticator app. For hardware keys, instructions on connecting the key are provided.
5. Verification: The user enters a code from their chosen 2FA method to verify the setup.
6. Confirmation: A confirmation message indicates successful 2FA activation.
Security Risks and Mitigation Strategies
Source: miro.com
Rockstar Games accounts, brimming with virtual assets, hard-earned progress, and potentially linked to real-world financial information, are prime targets for malicious actors. The absence of robust security measures, particularly two-factor authentication (2FA), significantly increases the vulnerability of these accounts to various attacks. Understanding these risks and implementing effective mitigation strategies is crucial for both Rockstar Games and its players.
Failing to implement 2FA exposes Rockstar Games accounts to a range of threats, from simple account takeovers to more sophisticated attacks aimed at stealing valuable in-game items or even accessing linked financial accounts. These threats can lead to significant financial losses, frustration, and a diminished gaming experience for players. The impact extends beyond individual players; widespread account compromises can damage Rockstar Games’ reputation and undermine user trust.
Real-World Examples of Online Gaming Account Attacks
Numerous real-world examples highlight the devastating consequences of inadequate security in online gaming. For instance, credential stuffing attacks, where stolen usernames and passwords from other online services are used to attempt logins on gaming platforms, are incredibly common. Phishing scams, often disguised as legitimate Rockstar Games communications, can trick users into revealing their login credentials. Malware infections on players’ devices can also lead to keyloggers recording their login information, granting attackers unauthorized access. In some cases, sophisticated attacks exploit vulnerabilities in the game’s client or server software to gain control of multiple accounts simultaneously. The consequences range from stolen in-game currency and rare items to the complete loss of gaming progress and the potential for identity theft.
Comparison of 2FA Methods and Effectiveness Against Attack Vectors
| 2FA Method | Credential Stuffing | Phishing | Malware/Keyloggers |
|---|---|---|---|
| SMS-based OTP | High Resistance | Medium Resistance (SIM swapping vulnerability) | Low Resistance (SIM swapping vulnerability) |
| Authenticator App (e.g., Google Authenticator) | High Resistance | High Resistance | High Resistance |
| Hardware Security Key (e.g., YubiKey) | High Resistance | High Resistance | High Resistance |
| Email-based OTP | Medium Resistance | Low Resistance (email compromise vulnerability) | Low Resistance (email compromise vulnerability) |
The table demonstrates that while SMS-based OTP offers a degree of protection, it’s vulnerable to SIM swapping attacks. Authenticator apps and hardware security keys provide significantly stronger protection against all listed attack vectors. Email-based OTP, while offering some security, is susceptible to email compromise, rendering it less effective than other methods.
Educating Rockstar Games Users About 2FA
A multi-pronged approach is needed to effectively educate Rockstar Games users about the importance of 2FA. This includes clear and concise in-game notifications, readily accessible help articles and FAQs on the Rockstar Games website, and engaging social media campaigns highlighting the benefits of 2FA and the risks of not using it. The messaging should emphasize the simplicity of setting up 2FA and the significant protection it offers against account compromises. Regular reminders and email communications can further reinforce the importance of this critical security measure. Consider incorporating interactive tutorials and videos to make the learning process more engaging and accessible to a wider audience. Finally, offering incentives, such as exclusive in-game items or temporary boosts, for enabling 2FA can encourage adoption.
Impact of 2FA on User Experience
Implementing two-factor authentication (2FA) significantly enhances the security of Rockstar Games accounts, protecting players from unauthorized access and account hijacking. However, this added layer of security inevitably introduces potential friction into the user experience, a trade-off that needs careful consideration. Balancing robust security with a smooth and enjoyable gaming experience is crucial for maintaining player satisfaction and engagement.
Potential Negative Impacts of 2FA on User Convenience
The extra step required for 2FA – typically requiring a code from a phone or authenticator app – can be perceived as inconvenient, especially for players accustomed to seamless logins. This added time investment, however minor, can disrupt the flow of gameplay, particularly during intense gaming sessions or when players are quickly trying to access their accounts. Furthermore, reliance on a secondary device (like a smartphone) adds another point of potential failure. Lost or malfunctioning phones, weak mobile signal, or even simply forgetting to bring the phone can lead to frustrating login delays or complete account lockout. The complexity of setting up and managing 2FA, including choosing a method and troubleshooting issues, can also deter some players from enabling it.
Mitigation Strategies for Negative Impacts of 2FA
Several strategies can be employed to mitigate the negative impacts of 2FA on user experience. Offering a range of 2FA methods caters to different user preferences and technical capabilities. For example, alongside authenticator apps, Rockstar could offer SMS-based codes as a simpler alternative, though acknowledging the inherent security trade-offs. Clear and concise instructions, supplemented with visual guides, can streamline the 2FA setup process. Regular in-game prompts reminding players of the importance of 2FA and providing easy access to support can also encourage adoption and reduce frustration. Furthermore, implementing a system that allows for temporary disabling of 2FA under specific circumstances (e.g., temporary travel, device loss) could provide a balance between security and convenience.
Comparison of 2FA Implementations in Other Gaming Platforms, Rockstar 2fa
Other gaming platforms like Steam, Epic Games Store, and PlayStation Network have successfully integrated 2FA. Examining their implementations reveals a range of approaches. Steam, for example, offers a variety of methods, including authenticator apps and email codes, providing flexibility for users. Epic Games Store’s implementation is relatively straightforward, prioritizing simplicity and ease of use. By contrast, some platforms may have more cumbersome processes, leading to user frustration. Analyzing these different approaches can inform the design of a Rockstar 2FA system that optimizes both security and user experience. For example, if a platform is known for its clear and easy-to-understand instructions, Rockstar can model its own implementation based on that successful design.
Balancing Security and User Experience in 2FA System Design
The optimal 2FA system balances robust security with minimal disruption to the user experience. This requires a careful consideration of several factors, including the choice of authentication methods, the clarity of instructions, and the overall user interface. A well-designed system will be intuitive, easy to use, and provide clear feedback to the user at each stage of the authentication process. Regular user feedback and iterative improvements based on real-world usage data are crucial for refining the system and addressing any usability issues. A system that is too complex or inconvenient will likely see low adoption rates, undermining its security benefits. Conversely, a system that prioritizes simplicity at the expense of security leaves users vulnerable. The ideal solution lies in finding a balance between these two critical aspects. For example, Rockstar could implement a system where the initial setup is thorough but subsequent logins are streamlined, leveraging technologies that minimize user input while maximizing security.
Future Considerations for Rockstar Games Security
Rockstar Games, custodians of iconic franchises like Grand Theft Auto and Red Dead Redemption, face an ever-evolving landscape of cyber threats. Their massive online player base and valuable intellectual property make them a prime target for sophisticated attacks. Maintaining robust security is not just a matter of protecting player data; it’s crucial for the long-term health and reputation of the company. Moving beyond 2FA requires a proactive, multi-layered approach to security.
The sheer scale of Rockstar’s online presence amplifies the potential impact of security breaches. A successful attack could result in significant financial losses, reputational damage, and legal repercussions. Furthermore, the increasing sophistication of hacking techniques, including AI-powered attacks and the exploitation of zero-day vulnerabilities, necessitates a continuous evolution of security measures.
Potential Future Threats to Rockstar Games Accounts
The threat landscape for Rockstar Games accounts is dynamic and complex. Beyond simple password cracking, future threats may involve highly targeted attacks leveraging social engineering, phishing campaigns disguised as official Rockstar communications, or the exploitation of vulnerabilities in third-party software integrated with their platforms. Advanced persistent threats (APTs), where attackers maintain long-term access to systems, pose a significant risk, potentially leading to data exfiltration or manipulation of game mechanics. Furthermore, the increasing use of automation in cyberattacks, including botnets and AI-driven tools, could overwhelm traditional security measures. The potential for insider threats, whether malicious or accidental, should also be considered.
Recommendations for Enhancing Rockstar Games’ Security Practices
Strengthening Rockstar Games’ security requires a multi-pronged strategy. This includes implementing advanced threat detection systems capable of identifying and responding to anomalies in real-time. Regular security audits and penetration testing by independent experts are essential to proactively identify and address vulnerabilities. Employee security awareness training should be a continuous process, educating staff about phishing scams, social engineering tactics, and secure coding practices. Implementing a robust incident response plan, including clear communication protocols and established procedures for containment and recovery, is crucial. Finally, proactive engagement with the security community and sharing of threat intelligence can help Rockstar Games stay ahead of emerging threats.
System for Monitoring and Responding to Security Incidents
A comprehensive security information and event management (SIEM) system is vital for monitoring Rockstar Games accounts. This system should collect and analyze security logs from various sources, including game servers, authentication systems, and network infrastructure. Real-time threat detection capabilities should be integrated, triggering alerts based on predefined rules and anomaly detection algorithms. A dedicated security operations center (SOC) staffed with experienced security professionals should be responsible for monitoring alerts, investigating incidents, and coordinating response efforts. The system should also include automated response mechanisms, such as blocking malicious IP addresses or temporarily suspending compromised accounts. Regular testing and refinement of the incident response plan are crucial to ensure its effectiveness.
Role of Biometric Authentication in Enhancing Security
Biometric authentication, using unique biological traits like fingerprints or facial recognition, offers a significant enhancement to Rockstar Games’ security posture. Integrating biometric authentication as an additional layer of security alongside 2FA can significantly increase the difficulty for attackers to compromise accounts. However, the implementation should prioritize user privacy and data protection, adhering to strict data handling regulations and minimizing the storage of sensitive biometric data. The system should also offer alternative authentication methods for users who are unable or unwilling to use biometric authentication. Regular updates and security audits of the biometric system are essential to mitigate vulnerabilities and ensure its ongoing effectiveness.
Illustrative Example
Source: gta5grand.com
Let’s dive into two scenarios highlighting the crucial role of 2FA in protecting Rockstar Games accounts from phishing attacks. These examples illustrate the stark difference between a vulnerable account and one secured with this vital security measure.
Phishing attacks are a constant threat in the online world, and gamers are unfortunately frequent targets. The lure of exclusive in-game content, early access, or even just the fear of account suspension can make even the most cautious players vulnerable. Understanding how these attacks work is the first step to protecting yourself.
Phishing Attack Without 2FA
Imagine Alex, a dedicated Grand Theft Auto Online player, receives an email seemingly from Rockstar Games. The email looks convincingly legitimate, complete with the Rockstar logo and a professional tone. It warns Alex that his account has been flagged for suspicious activity and requires immediate verification by clicking a link to update his account details. Unsuspecting, Alex clicks the link, which takes him to a fake Rockstar Games login page. He enters his username and password, unknowingly handing over his credentials to the phisher. Within minutes, his account is compromised. The attacker can now access his virtual currency, rare in-game items, and potentially even link his account to malicious software. The lack of 2FA allowed the attacker complete access.
Phishing Attack With 2FA Enabled
Now, let’s consider Ben, another GTA Online player who has enabled 2FA on his Rockstar Games account. He receives a similar phishing email, seemingly from Rockstar Games, with the same urgency and convincing design. He’s wary, but the email’s professional look almost convinces him. He clicks the link, but instead of gaining direct access, he’s directed to a fake login page. He enters his username and password. However, because 2FA is enabled, he’s then prompted for a one-time code from his authenticator app or via SMS. He doesn’t receive any such code from Rockstar because he never actually logged in through the official website. He recognizes the email as fraudulent and immediately reports it as spam. His account remains secure.
Visual Representation of Scenario Differences
We can represent this visually:
“`
Scenario 1: No 2FA
——————–
[Email] –> [Fake Login Page] –> [Username/Password Entered] –> [Account Compromised]
Scenario 2: 2FA Enabled
———————–
[Email] –> [Fake Login Page] –> [Username/Password Entered] –> [2FA Code Request] –> [No Authentic Code Received] –> [Attack Fails]
“`
This simple text-based representation clearly illustrates the crucial difference: the additional layer of security provided by 2FA stops the attacker in their tracks.
Impact on User Trust and Rockstar Games’ Reputation
A successful phishing attack, especially on a large scale, severely damages user trust in Rockstar Games. News of compromised accounts, stolen virtual currency, and other related issues can lead to negative publicity, impacting the company’s reputation and potentially causing financial losses. Conversely, robust security measures, such as 2FA, demonstrate Rockstar Games’ commitment to protecting its users, fostering trust and maintaining a positive brand image. The difference between a successful and failed attack directly correlates to the perception of Rockstar Games’ security posture and overall user confidence.
Closing Notes: Rockstar 2fa
Ultimately, the implementation of Rockstar 2FA isn’t just about adding another layer of security; it’s about fostering a more trustworthy and enjoyable gaming experience. By understanding the threats, implementing effective 2FA solutions, and educating players, Rockstar Games can significantly reduce the risk of account compromises and build a stronger, more secure community. The future of online gaming hinges on proactive security measures, and 2FA is a crucial first step in that direction. So, gear up and protect your virtual assets – your digital empire awaits!