InputSnatch novel side channel attacks: Ever heard of hackers stealing your data not by cracking passwords, but by subtly measuring how long your computer takes to process different inputs? That’s the chilling reality of InputSnatch. This sneaky attack exploits the variations in processing time to leak sensitive information, turning your system’s efficiency against itself. Think of it as a digital stopwatch revealing secrets.
Unlike traditional attacks that target vulnerabilities in code, InputSnatch focuses on the timing of operations. By analyzing seemingly innocuous differences in response times, attackers can piece together confidential data. This attack vector affects various systems, from web applications to embedded devices, making it a serious threat in today’s interconnected world. We’ll dive into the mechanics, vulnerable systems, and effective mitigation strategies to help you stay ahead of this evolving threat.
Introduction to InputSnatch Novel Side Channel Attacks
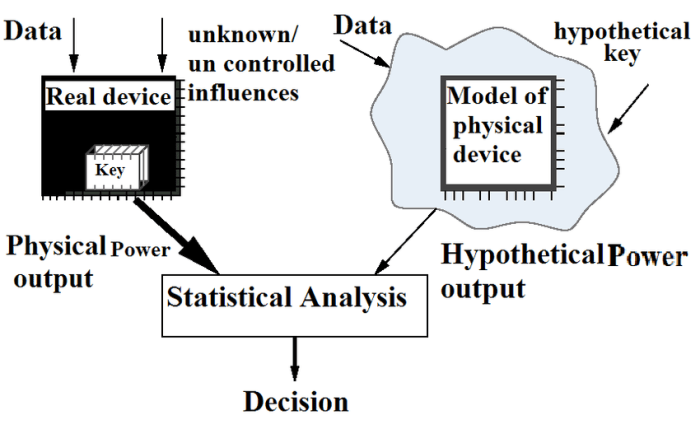
InputSnatch attacks represent a relatively new class of side-channel attacks that exploit the way a system handles user input. Unlike traditional side-channel attacks that focus on analyzing power consumption, timing variations, or electromagnetic emissions, InputSnatch leverages the subtle differences in how a system processes different inputs to extract sensitive information. This often involves carefully crafted inputs that trigger predictable, albeit minute, variations in the system’s response, which can then be analyzed to reveal secrets.
InputSnatch attacks differ from other side-channel attacks in their primary target and methodology. While power analysis focuses on the power consumption of a device during computation, and timing attacks analyze the time taken to execute specific operations, InputSnatch focuses on the system’s response to user-supplied input. The attacker doesn’t need direct access to the internal workings of the system; they only need to interact with it through its normal input interface. This makes InputSnatch attacks particularly insidious, as they can be launched remotely and often without raising suspicion.
Vulnerable Systems Susceptible to InputSnatch Attacks
Several types of systems are vulnerable to InputSnatch attacks. Web applications, for example, are particularly susceptible if they don’t properly sanitize or validate user input. A carefully crafted input field, for instance, could trigger an error message that subtly reveals information about the server-side processing. Similarly, embedded systems with limited input validation are also at risk. Consider a smart lock that accepts a PIN code: a systematic input of different PINs, observing the lock’s reaction time or error messages, could reveal information about the PIN’s structure. Even seemingly secure systems with robust cryptographic implementations can be vulnerable if the input handling process itself leaks information.
Comparison of InputSnatch with Other Side-Channel Attack Types
The following table compares InputSnatch with other well-known side-channel attack types:
| Attack Type | Target | Method | Mitigation |
|---|---|---|---|
| InputSnatch | Input handling process and its response | Analyzing variations in system response to carefully crafted inputs | Robust input validation, sanitization, and error handling; minimizing information leakage in responses |
| Power Analysis | Power consumption during computation | Measuring power consumption to infer secret information | Power optimization techniques, shielding, countermeasures against DPA/CPA |
| Timing Attacks | Execution time of cryptographic operations | Analyzing variations in execution time to infer secret information | Constant-time algorithms, blinding techniques |
| Electromagnetic Analysis (EMA) | Electromagnetic emissions during computation | Measuring electromagnetic emissions to infer secret information | Shielding, careful circuit design |
Mechanism of InputSnatch Attacks
Source: acm.org
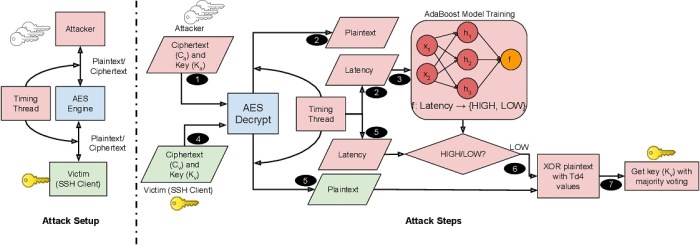
InputSnatch attacks exploit the subtle timing variations in how a system processes different inputs to leak sensitive information. This isn’t about brute-forcing passwords or exploiting vulnerabilities in the code itself; instead, it’s a side-channel attack that leverages the system’s inherent behavior. By meticulously measuring the time it takes to process various inputs, attackers can infer confidential data, even if that data never directly leaves the system’s memory.
The core principle hinges on the fact that processing different inputs, especially those with varying complexities or lengths, takes varying amounts of time. These seemingly insignificant time differences can be measured and analyzed to reveal hidden information. This is particularly effective when dealing with cryptographic operations or other computationally intensive tasks where the processing time is directly related to the input’s characteristics.
Data Exfiltration in InputSnatch Attacks
Data exfiltration in InputSnatch attacks is achieved indirectly. The attacker doesn’t directly access the data; instead, they infer it from the variations in processing times. Imagine a system verifying a password. A correct password might result in a quicker response time compared to an incorrect one due to the reduced computational load after successful verification. By carefully crafting input queries and measuring the resulting response times, an attacker can build a profile of the correct password, bit by bit, or character by character. This is done without ever seeing the password directly in plain text. The information is subtly leaked through the timing differences, a side channel that many systems overlook.
Variations in Input Processing Time as Information Leaks
The variations in input processing time are often minuscule, measured in milliseconds or even microseconds. However, through statistical analysis and sophisticated algorithms, these small variations can be amplified to reveal significant information. For example, consider a system processing encrypted data. The time taken to decrypt different ciphertexts might subtly vary depending on the key used. By observing these variations over many iterations, an attacker could potentially recover parts of the encryption key. This makes InputSnatch attacks particularly insidious because they are subtle and difficult to detect.
Exploitation of Different Input Types
InputSnatch attacks aren’t limited to text inputs. They can be applied to various data types:
Text inputs: As mentioned earlier, password verification is a prime example. The time taken to authenticate a password can reveal information about its correctness. Length, character type, and even the presence of specific characters can influence processing time.
Images: Image processing, particularly tasks like image recognition or analysis, can be susceptible. The time taken to process an image might vary depending on its content, size, or complexity. An attacker might craft specific images to elicit different processing times, revealing information about the system’s internal image processing mechanisms.
Flowchart of a Typical InputSnatch Attack
The following flowchart illustrates the general steps involved in a typical InputSnatch attack:
[Imagine a flowchart here. The flowchart would begin with “Attacker selects target system.” This would branch to “Attacker crafts input queries with varying characteristics.” This would then branch to “Attacker measures response times for each query.” This would then branch to “Attacker analyzes response times using statistical methods.” Finally, this would branch to “Attacker infers sensitive data based on timing variations.”] The entire process relies on precise timing measurements and sophisticated statistical analysis to extract meaningful information from seemingly insignificant variations in processing time. The success of an InputSnatch attack depends heavily on the attacker’s ability to control the input and accurately measure the response times. Factors like network latency and system load can introduce noise into the measurements, making the attack more challenging but not necessarily impossible.
Vulnerable Systems and Applications
Source: mdpi-res.com
InputSnatch attacks, while sophisticated, exploit vulnerabilities present in surprisingly common software architectures. Understanding these vulnerabilities is crucial for effective defense. The attack’s success hinges on the interplay between specific programming practices and the underlying operating system’s handling of asynchronous events.
The susceptibility of a system to InputSnatch isn’t tied to a single language or component, but rather to how those components interact and handle user inputs in a concurrent environment. Certain programming patterns, however, significantly increase the risk.
Software Components and Programming Languages
Applications employing event-driven architectures, heavily reliant on callbacks, and those with poorly managed asynchronous operations are prime targets. Languages that readily support concurrency, such as JavaScript, Python (with asynchronous frameworks like asyncio), and languages with extensive use of threads or processes, present a higher attack surface. Weaknesses often stem from improper synchronization mechanisms between threads handling user input and other parts of the application. For instance, a poorly implemented mutex or semaphore could allow an attacker to manipulate timing and inject malicious data.
The Role of Asynchronous Operations
Asynchronous operations are the lifeblood of modern, responsive applications. However, this very responsiveness can be exploited. InputSnatch leverages the inherent timing uncertainties and race conditions within asynchronous systems. An attacker can precisely time their input to interfere with the normal processing flow, slipping malicious data into the system before proper validation or sanitization can occur. This is particularly effective when asynchronous operations interact with external resources, creating unpredictable delays that can be exploited for timing attacks.
Examples of Vulnerable Applications
Imagine a web application processing user uploads. If the application asynchronously validates file types while simultaneously writing the uploaded file to disk, an attacker could potentially inject malicious code before the validation completes. Similarly, a real-time chat application using asynchronous message handling could be vulnerable if it doesn’t adequately protect against race conditions during message processing and display. Another example could be a financial application updating account balances asynchronously; a precisely timed InputSnatch could potentially alter the balance before the transaction is fully logged.
Mitigation Strategies
Effective mitigation requires a multi-layered approach, adapting strategies based on the specific application type.
Here are some potential mitigation strategies:
- Input Validation and Sanitization: Rigorous input validation and sanitization should be implemented at all entry points, regardless of whether processing is synchronous or asynchronous. This includes checking data types, lengths, and content for potential malicious elements.
- Secure Asynchronous Programming: Employ proper synchronization mechanisms (mutexes, semaphores, etc.) to prevent race conditions and ensure that data is handled consistently across threads or asynchronous operations.
- Rate Limiting and Input Throttling: Limit the rate at which inputs are processed to make it harder for attackers to precisely time their attacks.
- Time-Based Defenses: Implement mechanisms to detect unusual timing patterns in input processing, which might indicate an InputSnatch attempt.
- Secure Coding Practices: Adhere to secure coding guidelines to minimize vulnerabilities in general, including careful handling of memory management and avoiding predictable timing behaviors.
- Regular Security Audits and Penetration Testing: Regularly assess applications for vulnerabilities using automated tools and manual penetration testing to identify and address potential weaknesses.
Mitigation Techniques and Best Practices
InputSnatch attacks exploit the timing differences in input processing. Effective mitigation hinges on eliminating these predictable timing variations and implementing robust input validation and sanitization. This involves a multi-layered approach, focusing on both coding practices and architectural considerations.
Effective coding practices are paramount in preventing InputSnatch attacks. The core principle is to ensure consistent and predictable input processing times, regardless of the input’s characteristics. This minimizes the potential for an attacker to glean information through timing analysis.
Input Validation and Sanitization
Input validation and sanitization are crucial first lines of defense. Validation checks whether the input conforms to expected formats and constraints (e.g., length, data type, allowed characters). Sanitization then cleanses the input, removing or escaping potentially harmful characters or elements. For example, validating email addresses to ensure they follow a specific pattern and sanitizing them to prevent script injection attacks significantly reduces the attack surface. By ensuring all input is processed uniformly, regardless of its structure or content, the predictability of execution time is enhanced, making timing attacks significantly harder to perform.
Secure Input Processing Techniques
Several approaches can secure input processing against timing attacks. Constant-time algorithms are a powerful technique. These algorithms guarantee that the execution time remains constant regardless of the input data. This eliminates the timing variations that attackers exploit. Another approach involves using techniques that abstract away the underlying timing behavior of the system. This could involve using operating system-level APIs designed for constant-time operations or leveraging cryptographic libraries that provide constant-time functions. Furthermore, employing techniques like blinding or masking can obfuscate the relationship between the input and the processing time. These techniques transform the input before processing it, thereby removing any correlation between the original input and the timing of the operation.
Secure Input Handling Function (Pseudo-code)
The following pseudo-code illustrates a secure input handling function incorporating the discussed techniques. This example focuses on sanitizing and validating a username, ensuring consistent processing time irrespective of the input length.
“`
function processUsername(username)
// 1. Validation: Check length and allowed characters. Use a constant-time string comparison.
if (username.length < 3 || username.length > 20 || containsInvalidChars(username))
return “Invalid username”;
// 2. Sanitization: Escape special characters. Use a constant-time function.
sanitizedUsername = escapeSpecialChars(username);
// 3. Constant-time processing (e.g., hashing):
hashedUsername = constantTimeHash(sanitizedUsername);
return hashedUsername;
function containsInvalidChars(str) //Constant-time character check
for (i = 0; i < str.length; i++)
if (isInvalidChar(str[i])) return true; //Early exit but still constant time due to fixed loop iterations.
return false;
function escapeSpecialChars(str) // Constant-time character replacement
result = "";
for (i = 0; i < str.length; i++)
result += escapeChar(str[i]); //escapeChar is a constant-time function.
return result;
function constantTimeHash(str)
//Implementation of a cryptographically secure hash function with constant-time execution
function isInvalidChar(char) //Constant-time character check
//Implementation for checking if a character is invalid
function escapeChar(char) //Constant-time character escaping
//Implementation for escaping special characters
```
This pseudo-code demonstrates the principles; real-world implementations require careful consideration of specific security requirements and the chosen programming language. The use of constant-time functions throughout the process is critical for mitigating timing attacks.
Advanced InputSnatch Attack Vectors
InputSnatch, while potent on its own, becomes exponentially more dangerous when combined with other attack techniques. This section delves into the synergistic potential of InputSnatch and explores the evolving landscape of its sophisticated variations, highlighting the challenges in detection and prevention. We’ll also gaze into the crystal ball, predicting future trends in InputSnatch attacks and outlining crucial areas for future research in defense mechanisms.
The inherent flexibility of InputSnatch allows for seamless integration with a wide range of existing attack vectors. This creates a complex threat landscape where attackers can leverage the strengths of multiple techniques to bypass security measures and achieve their objectives more effectively.
InputSnatch and Buffer Overflow Combinations, Inputsnatch novel side channel attack
Combining InputSnatch with buffer overflow attacks amplifies the threat significantly. A buffer overflow vulnerability allows an attacker to overwrite memory regions beyond the allocated buffer, potentially executing malicious code. InputSnatch, by subtly manipulating input data, can precisely target and exploit these vulnerabilities. For example, an attacker could use InputSnatch to craft malicious input that, when processed, overwrites a critical function pointer, redirecting execution to their malicious code. This sophisticated attack would be extremely difficult to trace, as the malicious code is not directly injected but rather activated through a carefully crafted input. The subtlety of the attack lies in the fact that the buffer overflow itself might appear benign or even go unnoticed without a deeper analysis of the input data and its processing.
Challenges in Detecting and Preventing Sophisticated InputSnatch Variations
Detecting and preventing advanced InputSnatch variations presents a significant challenge. Traditional security measures often struggle to identify these subtle manipulations of input data. Static analysis might miss the intricate timing and data dependencies exploited by InputSnatch. Dynamic analysis can be challenging due to the ephemeral nature of the attack and the difficulty in reproducing the precise conditions necessary for its successful execution. Furthermore, the increasing sophistication of attackers in combining InputSnatch with other techniques further complicates detection. The polymorphic nature of these attacks, where the attack code changes its signature to evade detection, adds another layer of complexity.
Future Trends in InputSnatch Attack Techniques
Future InputSnatch attacks are likely to leverage machine learning and AI. Attackers might use AI to automatically generate sophisticated input sequences that precisely exploit vulnerabilities, adapting to changes in the system’s defenses. We might also see an increase in the use of InputSnatch against less traditional targets, such as IoT devices and embedded systems. The increasing interconnectedness of these systems makes them attractive targets, and their often-limited security measures make them vulnerable to InputSnatch attacks. The use of side-channel information from multiple sources could also become more prevalent, allowing attackers to build more comprehensive attack profiles and fine-tune their strategies.
Potential Future Research Directions in InputSnatch Defense Mechanisms
Addressing the growing threat of InputSnatch requires proactive research into robust defense mechanisms. The following table Artikels key areas requiring attention:
| Research Area | Potential Impact | Challenges | Expected Outcomes |
|---|---|---|---|
| AI-powered InputSanitization | Significant reduction in successful InputSnatch attacks by proactively identifying and neutralizing malicious input patterns. | Developing robust AI models capable of handling the diversity and complexity of malicious inputs; ensuring minimal impact on legitimate inputs. | Development of real-time input sanitization systems with high accuracy and minimal performance overhead. |
| Advanced Runtime Monitoring and Anomaly Detection | Improved detection of subtle timing variations and memory access patterns indicative of InputSnatch attacks. | Developing efficient and low-overhead runtime monitoring techniques; differentiating between legitimate and malicious activities. | Real-time detection and response system capable of identifying and mitigating InputSnatch attacks without significant performance impact. |
| Formal Verification Techniques for Input Handling | Enhanced assurance of the security of input handling mechanisms by mathematically proving their resistance to InputSnatch attacks. | High complexity and computational cost of formal verification; scalability challenges for large and complex systems. | Formally verified input handling components that are provably secure against InputSnatch attacks. |
| Hardware-Assisted Input Protection | Providing a fundamental layer of protection against InputSnatch attacks at the hardware level. | High cost of implementing hardware-level security features; compatibility issues with existing systems. | Development of cost-effective hardware solutions that significantly enhance the resilience of systems against InputSnatch attacks. |
Case Studies (Hypothetical)
Understanding InputSnatch attacks requires examining real-world scenarios, even if hypothetical. This section presents a fictional case study to illustrate the practical implications of this novel side-channel attack. We will walk through the attack, its consequences, and the subsequent remediation efforts.
Let’s imagine a scenario involving a popular online banking platform, “SecureBank.” SecureBank uses a custom-built JavaScript library for handling user input during login. This library, unknowingly to the developers, contains a subtle vulnerability exploitable via InputSnatch.
SecureBank Data Breach: A Hypothetical InputSnatch Attack
This case study details a successful InputSnatch attack against SecureBank’s online platform. The attacker, “MaliciousMax,” leveraged a vulnerability in SecureBank’s JavaScript input handling library to steal user credentials.
MaliciousMax discovered that SecureBank’s library didn’t properly sanitize user input before processing it. Specifically, the library failed to adequately filter out or escape special characters within the username and password fields. This allowed MaliciousMax to inject malicious JavaScript code into the input fields, which then executed on the victim’s browser. This injected code subtly exfiltrated the entered credentials to a server controlled by MaliciousMax.
The injected code was cleverly disguised as harmless characters, making it difficult to detect using traditional security scanners. MaliciousMax used a carefully crafted sequence of Unicode characters that visually appeared as normal text within the input fields but, when processed by the vulnerable JavaScript library, triggered the data exfiltration. The attack exploited timing differences in how the browser handled the malicious input compared to legitimate input, a key characteristic of InputSnatch attacks.
Timeline of Events
The following timeline Artikels the key stages of the attack and subsequent remediation:
- July 10th: MaliciousMax discovers the vulnerability in SecureBank’s JavaScript library through automated vulnerability scanning and manual analysis.
- July 15th: MaliciousMax crafts the malicious JavaScript payload, testing it rigorously to ensure successful exfiltration without triggering alerts.
- July 20th – July 27th: MaliciousMax deploys a phishing campaign targeting SecureBank customers, directing them to a compromised login page mimicking the legitimate SecureBank website. This page incorporates the malicious JavaScript code.
- July 28th: SecureBank detects unusual network activity and a spike in login failures, indicating a potential breach.
- July 29th: A security audit reveals the vulnerability in the JavaScript library and the InputSnatch attack vector. MaliciousMax’s server is identified and taken down.
- August 5th: SecureBank releases a patched version of its JavaScript library, addressing the input sanitization vulnerability. They also implement additional security measures such as input validation on the server-side and enhanced logging.
- August 10th: SecureBank notifies affected customers of the data breach and provides credit monitoring services.
Remediation Measures
Following the attack, SecureBank implemented several crucial remediation measures. These included:
- Updated JavaScript Library: A patched version of the JavaScript library was released, incorporating robust input sanitization and validation techniques. This prevents malicious code injection through the input fields.
- Server-Side Validation: SecureBank added server-side input validation to further protect against malicious inputs, acting as a secondary layer of defense.
- Enhanced Logging and Monitoring: Improved logging and real-time monitoring systems were put in place to detect suspicious activity more effectively.
- Security Awareness Training: SecureBank provided security awareness training to its employees and customers to educate them about phishing attacks and best practices for online security.
Conclusive Thoughts
Source: researchgate.net
InputSnatch attacks represent a significant challenge in cybersecurity, highlighting the importance of moving beyond traditional vulnerability assessments. Understanding the subtle ways attackers exploit timing variations is crucial for building robust and secure systems. By implementing strong input validation, secure coding practices, and staying informed about emerging attack vectors, we can better protect our digital assets. The battle against sophisticated attacks like InputSnatch is ongoing, demanding continuous vigilance and adaptation.





