Hackers launch zero day attacks to exploits corrupted files to evade security tools – Hackers launch zero-day attacks to exploit corrupted files to evade security tools – a chilling reality in today’s digital landscape. These stealthy attacks leverage vulnerabilities in seemingly innocuous files, bypassing traditional security measures with alarming ease. Imagine a carefully crafted Word document, seemingly harmless, secretly carrying a payload that silently grants hackers access to your entire system. This isn’t science fiction; it’s the grim truth of sophisticated cybercrime, and understanding the mechanics behind these attacks is crucial for staying ahead of the curve.
The sophistication of these attacks lies in their ability to exploit zero-day vulnerabilities – flaws unknown to software developers and security companies. Hackers often use social engineering techniques to trick victims into opening malicious files, or they might exploit existing vulnerabilities in software to install backdoors that allow them to plant these corrupted files later. Once inside, the malware can range from data theft to complete system compromise, causing significant financial and reputational damage. The methods employed to evade detection are equally cunning, relying on obfuscation, polymorphism, and other advanced techniques that render traditional antivirus software ineffective.
Zero-Day Exploits: Hackers Launch Zero Day Attacks To Exploits Corrupted Files To Evade Security Tools
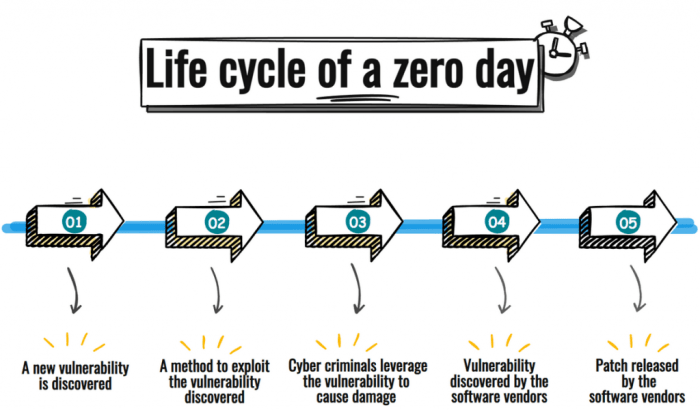
Source: balbix.com
Zero-day exploits represent a significant threat in the cybersecurity landscape. These attacks leverage previously unknown vulnerabilities, meaning security software hasn’t had the opportunity to develop defenses. When targeting corrupted files, these exploits become even more insidious, often bypassing traditional security measures. Understanding the mechanics behind these attacks is crucial for bolstering defenses.
Zero-day exploits targeting corrupted files rely on the attacker’s ability to craft malicious code that leverages flaws within a file’s structure or the software used to process it. This code, hidden within seemingly benign data, executes when the corrupted file is opened or processed, allowing the attacker to gain unauthorized access or control of the system.
Methods of Discovering and Weaponizing Zero-Day Vulnerabilities
Hackers employ various sophisticated techniques to uncover and weaponize zero-day vulnerabilities. Reverse engineering of software is a common method, painstakingly dissecting the code to identify weaknesses. Fuzzing, a technique that involves feeding a program with malformed or unexpected inputs, can also reveal vulnerabilities. Furthermore, hackers actively participate in bug bounty programs, ethically reporting vulnerabilities to earn rewards, though this knowledge can also be exploited for malicious purposes. The weaponization process involves crafting exploit code that precisely targets the identified vulnerability and delivers the desired payload – be it malware, data theft, or system compromise.
How Corrupted Files Facilitate Zero-Day Attacks
Corrupted files serve as ideal vectors for zero-day attacks because they often bypass security scanners. Antivirus and other security software primarily focus on detecting known malware signatures. Since zero-day exploits target unknown vulnerabilities, these security tools are ineffective. The corrupted file itself may appear benign to the user, masking the malicious code embedded within. This deceptive nature allows the attacker to successfully deliver the payload without triggering alarms. The corrupted file can also be designed to exploit vulnerabilities in specific software applications, further enhancing its effectiveness. For instance, a seemingly innocuous image file could contain code that exploits a vulnerability in the image viewer, granting the attacker access to the system.
Examples of Targeted File Types
Several file types are commonly targeted due to their frequent use and the potential for vulnerabilities within their processing mechanisms. The table below illustrates some examples.
| File Type | Vulnerability | Exploitation Method | Impact |
|---|---|---|---|
| .doc (Microsoft Word Document) | Memory corruption vulnerability in the document parser | Malicious macro code embedded within the document | Remote code execution, data theft |
| .pdf (Portable Document Format) | Vulnerability in the PDF rendering engine | JavaScript code embedded within the PDF | System compromise, malware installation |
| .jpg (JPEG Image) | Vulnerability in the image decoding library | Malicious code hidden within the image metadata | Arbitrary code execution |
| .exe (Executable File) | Buffer overflow vulnerability | Overwriting buffer memory with malicious code | Complete system takeover |
Evasion Techniques Employed by Hackers
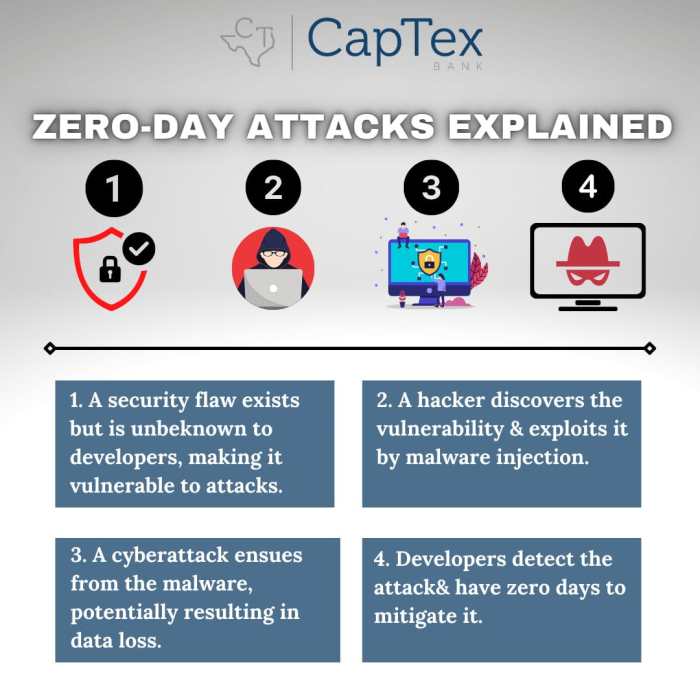
Source: captex.bank
Zero-day exploits are the ultimate weapon in a hacker’s arsenal, offering a window of opportunity before defenses can be patched. But even the most potent exploit is useless if it can’t bypass security software. This requires sophisticated evasion techniques, making the attack far more challenging to detect and prevent. The following sections detail some common strategies employed by hackers to achieve this.
Hackers utilize a range of techniques to evade detection, focusing on exploiting vulnerabilities in security software design and leveraging the limitations of current anti-malware solutions. These methods are constantly evolving, necessitating a proactive and adaptive approach to cybersecurity.
Anti-Virus and Intrusion Detection System Bypass
Bypassing antivirus (AV) and intrusion detection systems (IDS) is crucial for a successful zero-day attack. Hackers achieve this through several means. One common method is to leverage the inherent limitations of signature-based detection. These systems rely on identifying known malware signatures; however, a zero-day exploit, by definition, lacks a known signature. Furthermore, hackers often employ techniques like code obfuscation and polymorphism to disguise the malicious code, rendering it unrecognizable to signature-based systems. Another strategy involves exploiting vulnerabilities in the security software itself, bypassing its core functionality. This might involve exploiting a buffer overflow vulnerability in the AV engine or manipulating system calls to evade detection.
Obfuscation and Polymorphism in Malicious Code, Hackers launch zero day attacks to exploits corrupted files to evade security tools
Obfuscation is the process of making code difficult to understand. This can involve using code packing, encryption, and encoding to hide the true functionality of the malicious code. A simple example is packing the code into a smaller, compressed format that makes reverse engineering more difficult. Polymorphism, on the other hand, involves modifying the code’s structure without altering its functionality. This makes it difficult for signature-based detection systems to identify the malware, as its signature is constantly changing. For example, a polymorphic virus might alter its code slightly each time it infects a new system, rendering existing signatures ineffective.
Hypothetical Scenario: Evading Security Measures
Imagine a hacker targeting a financial institution. They’ve discovered a zero-day vulnerability in a specific version of the bank’s internal network management software. To exploit this, they create a custom-built exploit that uses a combination of techniques. First, the exploit code is heavily obfuscated using multiple layers of encryption and code packing, making it difficult for static analysis tools to understand its functionality. Second, the exploit incorporates polymorphic elements, ensuring that its signature changes each time it’s executed. Finally, the exploit is delivered via a seemingly benign email attachment, bypassing email spam filters. Upon execution, the exploit leverages the zero-day vulnerability to gain unauthorized access, potentially stealing sensitive financial data before security tools can react. The obfuscation and polymorphism ensure that the AV and IDS systems fail to detect the malicious activity, allowing the hacker to achieve their objective undetected.
Impact and Consequences of Attacks
Zero-day exploits leveraging corrupted files can have devastating consequences for individuals and organizations alike. The stealthy nature of these attacks, coupled with the lack of readily available defenses, means that damage can escalate rapidly and extensively before detection. The impact extends far beyond simple data loss, encompassing significant financial repercussions and long-term reputational harm.
The success of a zero-day attack using corrupted files can lead to a wide range of negative outcomes, significantly impacting the victim’s operations and security posture. The severity of the consequences depends on several factors, including the type of data compromised, the attacker’s goals, and the organization’s ability to respond effectively. Understanding these potential impacts is crucial for developing robust security strategies and mitigating future risks.
Types of Data Breaches
Successful zero-day attacks exploiting corrupted files can result in various types of data breaches. These breaches can expose sensitive personal information, intellectual property, financial records, and confidential business strategies. The specific type of data compromised depends heavily on the target and the attacker’s objectives. For example, a targeted attack against a healthcare provider might focus on stealing patient medical records, while an attack on a financial institution might aim to acquire customer banking details. A breach can also involve the theft of source code, leading to intellectual property theft and potentially compromising the security of other systems. The consequences of such breaches can be far-reaching and long-lasting.
Financial and Reputational Damage
The financial costs associated with zero-day attacks can be substantial. These costs include the direct expenses of investigating the breach, notifying affected individuals, implementing remedial measures, and potentially paying legal fees and fines. Beyond direct costs, organizations can experience significant indirect financial losses, such as lost revenue due to business disruption, decreased customer trust, and the cost of restoring damaged systems and data. The reputational damage resulting from a successful attack can be equally devastating. A data breach can severely tarnish an organization’s image, leading to loss of customer confidence and potential damage to future business opportunities. For example, a well-publicized data breach could deter potential investors or partners and damage the organization’s brand reputation. The long-term impact on revenue and growth can be profound.
Categorization of Potential Impacts
The potential impacts of successful zero-day attacks using corrupted files can be broadly categorized as follows:
- Data Loss: This includes the theft or destruction of sensitive data, such as customer information, financial records, intellectual property, or confidential business documents. The consequences can range from minor inconvenience to significant financial and legal liabilities, depending on the nature and sensitivity of the data lost.
- System Compromise: A successful attack can lead to complete system compromise, giving attackers full control over the affected systems. This allows them to install malware, steal data, disrupt operations, or use the compromised system to launch further attacks against other targets. The cost of restoring compromised systems and regaining operational capacity can be substantial.
- Financial Loss: This encompasses direct costs (e.g., investigation, remediation, legal fees, fines) and indirect costs (e.g., lost revenue, decreased productivity, damage to reputation). The magnitude of financial loss can vary widely depending on the size and nature of the organization and the extent of the damage caused.
- Legal and Regulatory Penalties: Organizations may face significant legal and regulatory penalties for failing to adequately protect sensitive data. These penalties can include fines, lawsuits, and reputational damage. Compliance with data protection regulations (such as GDPR) is paramount, and failure to comply can result in severe consequences.
Security Measures and Mitigation Strategies
Zero-day exploits targeting corrupted files represent a significant threat to any organization. The unpredictable nature of these attacks necessitates a multi-layered defense strategy that focuses on prevention, detection, and rapid response. Proactive measures are far more effective and cost-efficient than reactive ones, emphasizing the importance of a robust security posture.
Preventing zero-day attacks requires a combination of technical safeguards and robust security practices. Simply relying on a single solution is insufficient; a layered approach is crucial to maximize protection. This involves strengthening system defenses, implementing robust detection mechanisms, and establishing clear incident response protocols.
Best Practices to Prevent Zero-Day Attacks Targeting Corrupted Files
Implementing preventative measures significantly reduces the likelihood of successful zero-day attacks. A proactive approach, focusing on minimizing vulnerabilities and strengthening defenses, is paramount. This involves several key strategies, Artikeld below.
- Regular Software Updates and Patching: Promptly applying security patches and updates for all software, including operating systems, applications, and firmware, is critical. These updates often address known vulnerabilities that attackers could exploit.
- Robust Anti-Malware and Endpoint Detection and Response (EDR) Solutions: Employing advanced anti-malware solutions and EDR systems provides an extra layer of protection by detecting and blocking malicious code, even if it’s previously unknown. Regularly update these solutions to maintain their effectiveness.
- Strict File Access Control: Implementing granular access control mechanisms prevents unauthorized users from accessing or modifying critical files. This minimizes the impact of a successful compromise, limiting the attacker’s ability to spread laterally.
- Data Validation and Sanitization: Rigorous data validation and sanitization procedures help identify and neutralize malicious code embedded within seemingly legitimate files. This includes checking file signatures and using tools to detect and remove hidden malicious content.
- Email Security and Filtering: Implementing strong email security measures, including spam filters, anti-phishing solutions, and email authentication protocols (like DMARC, SPF, and DKIM), reduces the likelihood of receiving malicious attachments or links.
- Employee Security Awareness Training: Educating employees about phishing scams, social engineering tactics, and safe file handling practices is essential. Human error remains a significant vulnerability, and training can significantly reduce the risk of accidental exposure.
Vulnerability Management and Patching
Proactive vulnerability management is essential in mitigating the risk of zero-day exploits. This involves regularly scanning systems for vulnerabilities, prioritizing those that pose the greatest risk, and promptly applying patches. Delayed patching significantly increases the window of opportunity for attackers.
The process involves using vulnerability scanners to identify weaknesses in systems and applications. These scanners compare the system’s configuration against known vulnerabilities in databases like the National Vulnerability Database (NVD). Prioritization is crucial; focusing on critical vulnerabilities first ensures that the most serious threats are addressed promptly.
Data Backup and Recovery Strategies
Even with robust security measures, the possibility of a successful zero-day attack remains. Therefore, a comprehensive data backup and recovery strategy is crucial. This strategy should include regular backups, stored both on-site and off-site, and a well-tested recovery plan.
Regular backups minimize data loss in case of a successful attack. The frequency of backups depends on the criticality of the data and the organization’s risk tolerance. Off-site backups protect against physical damage or disasters that could affect on-site storage. A tested recovery plan ensures that the organization can quickly and efficiently restore its data and systems in the event of an attack. This plan should include detailed procedures, responsibilities, and contact information.
Responding to a Zero-Day Attack
A flowchart illustrating the steps involved in responding to a zero-day attack would look like this:
[Imagine a flowchart here. The flowchart would start with “Incident Detection,” branching to “Initial Containment (Isolate affected systems),” then “Investigation (Determine the extent of the breach),” followed by “Eradication (Remove malicious code),” “Recovery (Restore systems and data from backups),” and finally “Post-Incident Activity (Review and improve security measures).”] Each step would involve detailed actions and responsibilities, with clear communication and collaboration across different teams. The goal is to minimize the impact of the attack, quickly restore operations, and learn from the incident to prevent future occurrences.
Case Studies of Real-World Attacks
Zero-day exploits represent a significant threat in the cybersecurity landscape. Their unpredictable nature and ability to bypass existing security measures make them particularly dangerous. Examining real-world examples provides crucial insight into the tactics employed by attackers and the devastating consequences of successful breaches. Understanding these cases allows for the development of more robust security strategies.
The following case studies highlight the diverse methods used in successful zero-day attacks, emphasizing the importance of proactive security measures and rapid response capabilities.
Stuxnet Worm
Stuxnet, a sophisticated worm discovered in 2010, stands as a prime example of a highly targeted zero-day attack. Its impact was significant, showcasing the potential for devastating consequences when advanced techniques are employed against critical infrastructure.
- Attack Vector: USB drives and network connections were used to initially spread the worm, leveraging vulnerabilities in industrial control systems (ICS) software.
- Exploited Vulnerability: Stuxnet exploited multiple zero-day vulnerabilities in Microsoft Windows and Siemens industrial control system software. These vulnerabilities allowed the worm to gain unauthorized access and control of targeted systems.
- Consequences: The worm caused significant damage to Iranian nuclear facilities by subtly altering the operation of uranium enrichment centrifuges, delaying their enrichment process. This demonstrated the potential for physical damage and disruption through cyberattacks.
Equation Group Attacks
The Equation Group, a highly sophisticated advanced persistent threat (APT) group, is believed to have been behind a series of targeted zero-day attacks. Their operations highlight the level of resources and expertise required to develop and deploy such attacks.
- Attack Vector: The Equation Group used a variety of attack vectors, including highly targeted spear-phishing emails, compromised software updates, and network intrusions to deliver their malware payloads.
- Exploited Vulnerability: The group exploited numerous zero-day vulnerabilities in various operating systems and software applications. Many of these vulnerabilities were deeply embedded within the hardware and firmware of targeted systems, making them extremely difficult to detect and mitigate.
- Consequences: The attacks resulted in the compromise of highly sensitive data and intellectual property from various organizations and governments worldwide. The group’s ability to bypass established security measures showcased the limitations of traditional security solutions.
NotPetya Ransomware
While not strictly a zero-day attack in the traditional sense, the NotPetya ransomware attack in 2017 leveraged a previously unknown vulnerability in the Ukrainian accounting software MEDoc to spread rapidly and cause widespread disruption. This illustrates how vulnerabilities in seemingly less critical software can have global repercussions.
- Attack Vector: The attack began with the compromise of the MEDoc software update mechanism, allowing the malware to spread to thousands of systems through legitimate software updates.
- Exploited Vulnerability: The malware exploited a vulnerability in MEDoc that allowed it to spread laterally across networks, infecting other systems regardless of their security posture.
- Consequences: NotPetya caused billions of dollars in damages worldwide, affecting various industries and organizations. The attack demonstrated the devastating potential of supply chain attacks and the importance of securing even seemingly minor software components.
Comparing these attacks reveals a common theme: the exploitation of vulnerabilities in software and hardware to gain unauthorized access and control. While the specific attack vectors and exploited vulnerabilities varied, all three cases demonstrated the ability to bypass traditional security tools through the use of previously unknown vulnerabilities. The attacks also highlighted the importance of robust patching, security awareness training, and comprehensive incident response planning to mitigate the risks associated with zero-day exploits.
The Role of File Integrity Monitoring
File integrity monitoring (FIM) is a crucial layer of security, especially in the face of sophisticated zero-day attacks. These attacks, by their very nature, exploit vulnerabilities unknown to existing security software. FIM systems act as a vigilant watchdog, constantly comparing the state of critical system files and applications against known good baselines, instantly flagging any unauthorized modifications – a telltale sign of malicious activity. This proactive approach offers a powerful defense against the stealthy maneuvers of zero-day exploits.
FIM systems function by creating a baseline hash or checksum of files considered critical to system security. Regularly, these systems then compare the current state of those files to the baseline. Any discrepancies – such as a change in file size, modification time, or the checksum itself – trigger an alert, signaling a potential compromise. This method is particularly effective against zero-day attacks because it doesn’t rely on signature-based detection, which is easily bypassed by novel malware.
FIM System Features and Functionalities
Effective FIM solutions offer a range of features designed to enhance detection and response capabilities. These features work in concert to provide a robust and comprehensive security posture. Real-time monitoring is a key component, ensuring immediate alerts upon detection of any unauthorized changes. Automated responses, such as quarantining affected files or initiating incident response procedures, streamline the handling of potential threats. Detailed reporting and logging functionalities are crucial for post-incident analysis and security auditing, providing valuable insights into the nature and extent of the attack. Centralized management consoles facilitate efficient monitoring of multiple systems and allow administrators to tailor policies to specific needs. Finally, the ability to integrate with other security tools, such as SIEM systems, enhances overall security effectiveness by providing a unified view of security events.
FIM Limitations and Mitigation Strategies
While FIM provides significant protection, it’s not a silver bullet. One limitation is the potential for false positives. Legitimate system updates or administrative actions can trigger alerts if not properly accounted for in the baseline. Careful configuration and the use of whitelisting techniques can help minimize these false positives. Another limitation is the potential for attackers to bypass FIM by targeting files not included in the monitoring scope. A comprehensive monitoring strategy requires meticulous identification of all critical files and applications. Additionally, FIM is only as effective as the baseline it’s built upon. Regular updates and the use of robust hashing algorithms are crucial to maintain accuracy and prevent evasion. Finally, attackers could potentially modify files in memory, leaving no trace on the disk, thereby evading detection. Employing advanced techniques like memory forensics and runtime application self-protection (RASP) can mitigate this risk.
Examples of FIM System Alerts
Alert Type: File Integrity Violation
File Path: C:\Windows\System32\kernel32.dll
Event Time: 2024-10-27 10:30:00
Description: Checksum mismatch detected. The checksum of the file ‘kernel32.dll’ has changed since the last scan. Potential malware infection or unauthorized modification.
Alert Type: Unauthorized File Creation
File Path: C:\Users\Administrator\Documents\malicious.exe
Event Time: 2024-10-27 10:45:00
Description: A new file, ‘malicious.exe’, has been created in a restricted directory. This could indicate a malware infection or unauthorized activity.
Ultimate Conclusion

Source: com.au
Zero-day attacks leveraging corrupted files represent a significant and evolving threat. While complete prevention is impossible, a multi-layered approach involving robust security software, proactive vulnerability management, employee training, and vigilant file integrity monitoring offers the best defense. Staying informed about the latest attack vectors and techniques is paramount, as the battle against sophisticated cybercriminals is an ongoing arms race. The consequences of a successful attack can be devastating, making proactive security measures not just a good idea, but a business imperative in today’s interconnected world.





