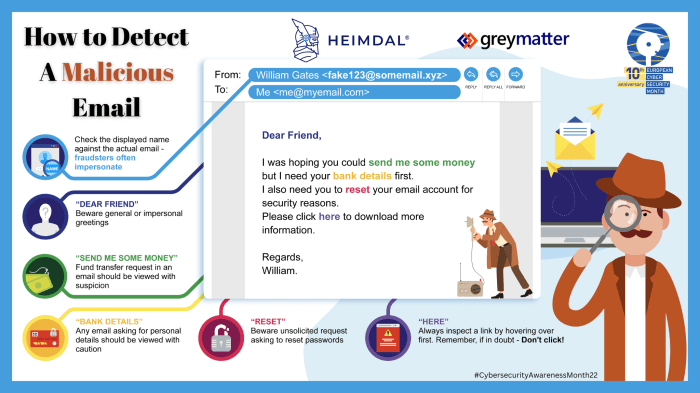
ProjectSend authentication vulnerability—that phrase alone should send shivers down the spine of any security-conscious developer. Imagine the chaos: sensitive data exposed, unauthorized access rampant, and your reputation in tatters. This isn’t some abstract threat; it’s a real-world danger lurking in the shadows of poorly secured systems. We’re peeling back the layers to uncover the vulnerabilities within ProjectSend’s authentication system, from password management pitfalls to the perils of third-party integrations. Get ready to upgrade your security game.
This deep dive explores ProjectSend’s authentication architecture, pinpointing potential weaknesses in password management, session handling, and third-party authentication integrations. We’ll analyze the potential impact of a successful attack, detailing the consequences ranging from data breaches to complete system compromise. We’ll then equip you with practical mitigation strategies, secure coding practices, and a robust incident response plan—all designed to fortify your ProjectSend system against the digital wolves at the door.
ProjectSend Authentication Overview
ProjectSend’s authentication system, while recently patched, presented a vulnerability that highlighted the importance of robust security measures in any system handling sensitive data. Understanding its architecture and authentication methods is crucial for preventing future incidents. This section provides a detailed overview of the system’s design and functionality before the vulnerability was addressed.
ProjectSend employed a multi-layered authentication approach, combining elements of traditional methods with more modern security practices. The system’s core relied on a centralized authentication server responsible for verifying user credentials and issuing session tokens. This server interacted with various application components, including the web interface and API endpoints, to manage user access. The complexity of this architecture, while offering enhanced security in theory, unfortunately, also created opportunities for vulnerabilities.
ProjectSend Authentication Architecture
The ProjectSend authentication architecture was client-server based. Clients, such as web browsers or mobile applications, initiated authentication requests to the central authentication server. This server validated credentials against a database containing user information, including usernames, passwords (hashed using a one-way function), and other relevant security attributes. Upon successful authentication, the server issued a session token, a unique identifier that allowed the client to access protected resources without repeatedly providing credentials. This token was typically stored in a secure cookie or within the application’s local storage. The server also employed various security measures, such as input validation and rate limiting, to mitigate common attack vectors. However, a flaw in the session token management ultimately led to the recently addressed vulnerability.
ProjectSend Authentication Methods
ProjectSend primarily supported username/password authentication. Users were required to provide their registered username and password to gain access. The system also incorporated email verification during account creation to prevent unauthorized registrations. While multi-factor authentication (MFA) was considered for future implementation, it was not active at the time of the vulnerability. The lack of MFA contributed to the severity of the identified security flaw, as it relied solely on the security of the username/password combination and session token.
ProjectSend Authentication Flow
The authentication flow involved several steps. First, a user would submit their credentials (username and password) via the login form or API endpoint. The client would then transmit these credentials to the authentication server. The server would retrieve the user’s information from the database, compare the provided password with the stored hash using a suitable algorithm, and verify the username’s validity. If the credentials matched and the user account was active, the server would generate a unique session token and return it to the client. The client would then store this token, enabling access to protected resources. Subsequent requests would include the session token, allowing the server to verify the user’s ongoing authentication. The vulnerability resided within the process of session token generation and management, specifically concerning its vulnerability to session hijacking.
Vulnerability Identification in ProjectSend Authentication
ProjectSend, like any system relying on authentication, presents a juicy target for attackers. Understanding the potential weaknesses in its password management, session handling, and third-party integrations is crucial for bolstering its security posture. Let’s delve into the specific vulnerabilities that could compromise ProjectSend’s defenses.
Password Management Vulnerabilities
Weak password policies are a common entry point for attackers. ProjectSend’s password management system might be vulnerable if it doesn’t enforce sufficient password complexity (length, character types, etc.), lacks account lockout mechanisms after multiple failed login attempts, or fails to utilize robust password hashing algorithms like bcrypt or Argon2. Failing to implement these safeguards leaves the system susceptible to brute-force attacks, dictionary attacks, and rainbow table attacks, all of which could potentially expose user credentials. For instance, a system requiring only six-character passwords with only alphanumeric characters would be significantly easier to crack than one demanding a minimum of 12 characters including symbols and numbers. The absence of account lockout further exacerbates this vulnerability, allowing attackers to try numerous combinations without penalty.
Session Management Vulnerabilities
Session management is another critical area. If ProjectSend’s session management isn’t properly implemented, attackers could hijack or extend sessions, gaining unauthorized access. Vulnerabilities might include the lack of secure, randomly generated session IDs, insufficient session timeouts, the absence of HTTPS, or the failure to invalidate sessions upon logout. A successful session hijacking attack could allow an attacker to access a user’s account and perform actions on their behalf without their knowledge. For example, if sessions aren’t properly invalidated after logout, an attacker could potentially reuse a stolen session ID to regain access.
Third-Party Authentication Service Vulnerabilities
Relying on third-party authentication services like OAuth or OpenID Connect introduces additional vulnerabilities. If the chosen third-party service suffers a security breach, ProjectSend’s users might be indirectly affected. Furthermore, ProjectSend’s integration with these services needs to be carefully implemented to avoid vulnerabilities like insecure redirects or improper handling of access tokens. Imagine a scenario where a vulnerability in a third-party authentication provider allows attackers to obtain user access tokens. If ProjectSend doesn’t properly validate these tokens, attackers could use them to gain unauthorized access to ProjectSend resources.
Common Authentication Vulnerabilities Affecting ProjectSend
Several common authentication vulnerabilities could affect ProjectSend. These include SQL injection attacks (if authentication queries aren’t properly parameterized), cross-site scripting (XSS) attacks (if user-supplied data isn’t properly sanitized), and cross-site request forgery (CSRF) attacks (if appropriate protection mechanisms aren’t in place). A successful SQL injection attack could allow an attacker to bypass authentication mechanisms altogether, while XSS attacks could allow attackers to steal user credentials or execute malicious code in the user’s browser. CSRF attacks, on the other hand, could trick users into performing actions they didn’t intend to, such as changing their passwords or granting access to attackers.
Impact Assessment of ProjectSend Authentication Vulnerabilities
A successful authentication attack on ProjectSend could have far-reaching and severe consequences, impacting everything from user data privacy to the overall operational integrity of the system. The vulnerabilities, if exploited, could lead to significant financial losses, reputational damage, and legal repercussions. Understanding the potential impact is crucial for implementing effective mitigation strategies.
The potential consequences of a compromised authentication system are multifaceted and interconnected. We’ll explore the different types of impacts, their likelihood, and potential mitigation strategies.
Data Breaches Resulting from Authentication Vulnerabilities
Exploiting ProjectSend’s authentication vulnerabilities could allow attackers to gain unauthorized access to sensitive user data. This could include personally identifiable information (PII) like names, addresses, email addresses, and phone numbers. More critically, it could also expose financial data, medical records, or other highly sensitive information, depending on the nature of data stored within the ProjectSend system. A large-scale breach could lead to identity theft, financial fraud, and significant reputational damage for ProjectSend and its users. Consider the 2017 Equifax breach, where a vulnerability in their authentication system led to the exposure of personal information for over 147 million people – a stark reminder of the devastating consequences of inadequate authentication security.
Unauthorized Access and Privilege Escalation
Successful authentication attacks don’t just lead to data breaches; they can also grant attackers unauthorized access to the ProjectSend system itself. This could range from simply viewing sensitive data to gaining complete control over the system. Privilege escalation, where an attacker gains higher-level access than initially intended, is a significant concern. For example, an attacker might initially gain access to a user account, but then exploit a vulnerability to elevate their privileges to administrator level, granting them complete control over the system and its data. This could enable them to modify data, install malware, or disrupt the system’s operation entirely.
Impact Assessment Table
The following table summarizes the potential consequences of different authentication vulnerabilities in ProjectSend, considering their impact, likelihood, and potential mitigation strategies.
| Vulnerability Type | Impact | Likelihood | Mitigation Strategy |
|---|---|---|---|
| SQL Injection | Data breach, unauthorized access, system compromise | Medium to High (depending on input validation) | Input validation, parameterized queries, regular security audits |
| Cross-Site Scripting (XSS) | Session hijacking, data theft, phishing attacks | Medium to High (depending on output encoding) | Output encoding, Content Security Policy (CSP), regular security audits |
| Brute-force attacks | Account lockout, unauthorized access | Low to Medium (depending on password complexity and lockout mechanisms) | Strong password policies, account lockout mechanisms, rate limiting |
| Session hijacking | Unauthorized access, data theft | Medium (depending on session management practices) | Secure session management, HTTPS, regular security audits |
Mitigation Strategies for ProjectSend Authentication Vulnerabilities
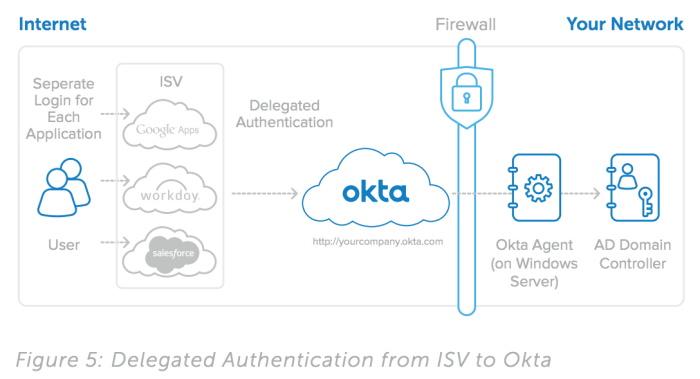
Source: okta.com
Fixing ProjectSend’s authentication flaws isn’t just about patching holes; it’s about building a robust, multi-layered security system. This requires a proactive approach, addressing weaknesses at every stage, from password management to third-party integrations. Let’s dive into practical strategies to fortify ProjectSend’s defenses.
Secure Password Policies for ProjectSend
Strong password policies are the first line of defense against brute-force attacks and credential stuffing. A well-designed policy minimizes the risk of easily guessable passwords compromising the system. ProjectSend should enforce a minimum password length (at least 12 characters), mandate a mix of uppercase and lowercase letters, numbers, and symbols, and prohibit the use of common passwords or dictionary words. Regular password changes, coupled with password complexity requirements, significantly enhance security. Consider implementing a password strength meter to guide users towards creating robust passwords. For added security, ProjectSend could also incorporate multi-factor authentication (MFA) as a secondary verification layer. This might involve sending a one-time code to the user’s registered email or mobile phone. Think of it like adding a second lock to your front door – it’s a significant deterrent.
Secure Session Management Strategy for ProjectSend
Session management is crucial. Weak session management allows attackers to hijack user sessions and gain unauthorized access. ProjectSend needs short-lived sessions with robust timeouts. This means automatically logging users out after a period of inactivity, preventing prolonged access if a device is left unattended. HTTPS should be mandatory for all authentication-related communications, encrypting data in transit and protecting against eavesdropping. Regularly rotating session IDs and using secure, unpredictable session identifiers are also vital. Implementing mechanisms to detect and prevent session hijacking, such as session fixation prevention, is crucial. This involves generating a new session ID after successful authentication, thwarting attempts to pre-determine session IDs and hijack them.
Mitigating Vulnerabilities Related to Third-Party Authentication Services
Relying on third-party authentication services like Google or Facebook adds convenience, but also introduces potential vulnerabilities. ProjectSend needs to carefully vet these services, ensuring they adhere to industry best practices and have a strong security track record. Regularly reviewing the security policies and updates of these providers is essential. Furthermore, ProjectSend should limit the data shared with these third-party services to only what’s strictly necessary for authentication. Over-sharing user data exposes ProjectSend to risks if the third-party service is compromised. Consider using OAuth 2.0 or OpenID Connect, which offer more secure authorization flows compared to simpler methods.
Best Practices for Securing ProjectSend’s Authentication System
Implementing a comprehensive security strategy requires a multi-faceted approach. Here are some best practices to enhance ProjectSend’s authentication system:
- Regularly update all software components, including the authentication system and any related libraries, to patch known vulnerabilities.
- Implement robust input validation to prevent injection attacks (SQL injection, cross-site scripting).
- Conduct regular security audits and penetration testing to identify and address potential weaknesses proactively.
- Use strong encryption algorithms for storing sensitive data like passwords (e.g., bcrypt, Argon2).
- Employ a comprehensive logging and monitoring system to detect and respond to suspicious activity.
- Educate users about secure password practices and the importance of recognizing phishing attempts.
- Implement rate limiting to mitigate brute-force attacks by restricting the number of login attempts from a single IP address within a specific timeframe.
- Follow the principle of least privilege, granting users only the necessary access rights.
Secure Coding Practices for ProjectSend Authentication

Source: slideplayer.com
Implementing robust secure coding practices is paramount for protecting ProjectSend’s authentication system from a range of vulnerabilities. Failing to do so leaves the system exposed to attacks that could compromise user data and system integrity, leading to significant reputational and financial damage. This section details crucial practices to mitigate these risks.
Preventing SQL Injection Attacks
SQL injection attacks exploit vulnerabilities in database interactions to execute malicious SQL code. In ProjectSend’s authentication module, this could allow attackers to bypass authentication, modify user data, or even gain complete control of the database. The primary defense is parameterized queries or prepared statements. Instead of directly embedding user input into SQL queries, these techniques treat user input as parameters, preventing the injection of malicious code. For example, instead of constructing a query like "SELECT * FROM users WHERE username = '" + username + "' AND password = '" + password + "'", a parameterized query would separate the user-supplied data from the SQL code itself. This ensures that the database treats the input as data, not executable code. Furthermore, rigorous input validation, described below, further strengthens this defense.
Preventing Cross-Site Scripting (XSS) Attacks
Cross-site scripting (XSS) attacks allow attackers to inject malicious scripts into web pages viewed by other users. In ProjectSend’s authentication context, this could lead to session hijacking, credential theft, or the distribution of malware. The most effective prevention is output encoding. Before displaying any user-supplied data on the webpage, especially in authentication-related messages or feedback, it must be properly encoded using appropriate methods (e.g., HTML encoding for HTML context, URL encoding for URLs, and JavaScript encoding for JavaScript context). This prevents the browser from interpreting the malicious script as code. Regular security audits and penetration testing can further identify and address any XSS vulnerabilities.
Input Validation to Prevent Authentication Bypass
Input validation is a fundamental security practice that verifies the format, type, and length of user inputs before processing them. Bypassing input validation can enable attackers to manipulate authentication logic, potentially leading to unauthorized access. For example, ProjectSend should validate that usernames and passwords conform to specific length and character restrictions. It should also check for the presence of special characters that could be used to exploit vulnerabilities. Data type validation is equally important; ensuring that numerical fields only receive numbers, and that strings are handled appropriately, prevents unexpected behavior that could be exploited. Implementing robust input validation significantly reduces the risk of authentication bypass attempts.
Preventing Buffer Overflow Vulnerabilities
Buffer overflow vulnerabilities occur when a program attempts to write data beyond the allocated buffer size, potentially overwriting adjacent memory locations. In ProjectSend’s authentication system, this could lead to arbitrary code execution, granting attackers complete control of the system. The key to preventing buffer overflow vulnerabilities is to use safe functions that check for buffer boundaries before writing data. These functions, often provided by programming languages or libraries, handle memory allocation and data writing securely. Furthermore, input validation, as discussed earlier, plays a critical role in preventing buffer overflows by ensuring that the input data does not exceed the buffer’s capacity. Regular code reviews and static analysis tools can help identify potential buffer overflow vulnerabilities before deployment.
Penetration Testing and Vulnerability Scanning for ProjectSend Authentication: Projectsend Authentication Vulnerability

Source: mojoauth.com
ProjectSend’s authentication system, while seemingly robust, requires rigorous testing to uncover potential weaknesses. Penetration testing and vulnerability scanning are crucial steps in ensuring its security and preventing unauthorized access. These methods proactively identify vulnerabilities before malicious actors can exploit them, saving significant time and resources in the long run.
A penetration test simulates real-world attacks against ProjectSend’s authentication system to identify exploitable vulnerabilities. This involves systematically attempting to bypass security controls, such as password cracking, session hijacking, and exploiting known vulnerabilities in the underlying software. The goal is not just to find vulnerabilities, but to understand how attackers might exploit them and the potential impact.
Vulnerability Scanning Tools for ProjectSend Authentication, Projectsend authentication vulnerability
Several automated tools can scan ProjectSend’s authentication system for common vulnerabilities. These tools analyze the system’s configuration, code, and network traffic to identify potential weaknesses. Choosing the right tools depends on the specific needs and resources available. Some tools are more comprehensive, while others focus on specific vulnerability types.
Examples include OpenVAS, Nessus, and QualysGuard. OpenVAS is an open-source vulnerability scanner offering a wide range of checks. Nessus, a commercial offering, provides a more comprehensive and user-friendly interface. QualysGuard offers a cloud-based solution with extensive reporting and compliance features. The choice often comes down to budget, required features, and integration with existing security infrastructure.
Interpreting Vulnerability Scan Results for ProjectSend Authentication
Interpreting the results of a vulnerability scan requires careful consideration. A vulnerability scanner will report various potential weaknesses, each with a severity level (e.g., critical, high, medium, low). It’s crucial to prioritize vulnerabilities based on their severity and the likelihood of exploitation. False positives are also common, requiring manual verification to confirm whether a reported vulnerability is genuine. Understanding the context of each vulnerability is key to accurate assessment. For instance, a reported SQL injection vulnerability might be a false positive if the application properly sanitizes user inputs.
Penetration Testing Tools and Techniques for ProjectSend Authentication
Penetration testing goes beyond automated scans, employing manual techniques to explore vulnerabilities more deeply. This often involves using specialized tools to simulate real-world attacks.
For example, Burp Suite can intercept and modify HTTP requests to test for vulnerabilities like cross-site scripting (XSS) and SQL injection. Nmap can be used to map the network infrastructure and identify open ports, potentially revealing weaknesses in the authentication system’s network configuration. Metasploit provides a framework for exploiting known vulnerabilities, allowing penetration testers to simulate various attack scenarios. These tools, combined with manual testing techniques, provide a more comprehensive assessment of ProjectSend’s authentication security than automated scans alone.
Incident Response Plan for ProjectSend Authentication Breaches
A robust incident response plan is crucial for minimizing the damage caused by a successful authentication breach in ProjectSend. This plan Artikels the steps to be taken, from initial detection to full recovery and post-incident analysis. Effective response hinges on speed, precision, and a well-defined process.
Incident Detection and Reporting
The first step involves establishing clear channels for reporting suspected authentication breaches. This includes defining who can report incidents (e.g., system administrators, security analysts, end-users), and specifying the reporting procedure (e.g., email, ticketing system, dedicated phone line). Automated alerts triggered by unusual login activity, failed login attempts exceeding a threshold, or suspicious IP addresses should also be implemented. A detailed log of all authentication attempts is essential for rapid identification of anomalies. This log should include timestamps, usernames, IP addresses, and success/failure status.
Initial Containment and Investigation
Upon detection, the immediate priority is to contain the breach. This may involve temporarily disabling user accounts suspected of compromise, restricting access to affected systems, and isolating vulnerable network segments. A dedicated incident response team should be activated to conduct a thorough investigation. This involves analyzing logs, examining system configurations, and interviewing affected users to understand the scope and nature of the breach. The team will determine the root cause of the breach, the extent of data compromised, and the affected systems.
Eradication and Remediation
Once the investigation is complete, the focus shifts to eradicating the threat and remediating the vulnerabilities. This may involve patching software, updating security configurations, resetting compromised passwords, and implementing stronger authentication mechanisms (e.g., multi-factor authentication). Data recovery and restoration from backups might be necessary if data was compromised. All affected systems should be thoroughly scanned for malware or other malicious code.
Recovery and System Restoration
After eradication and remediation, systems should be carefully restored to their operational state. This includes verifying system integrity, restoring data from backups, and testing system functionality. User accounts should be re-enabled, and access control measures should be reviewed and strengthened. A thorough post-incident review should be conducted to ensure that all affected systems are secure.
Post-Incident Activity and Lessons Learned
Following a successful restoration, a comprehensive post-incident review is vital. This involves documenting the entire incident response process, identifying areas for improvement, and updating the incident response plan accordingly. Lessons learned should be communicated to relevant stakeholders, including system administrators, security personnel, and end-users. This will enhance the organization’s preparedness for future incidents and reduce the potential impact of future breaches. The review should also include a detailed analysis of the root cause of the breach, the effectiveness of existing security controls, and the overall impact of the incident.
Incident Response Flowchart Description
The flowchart begins with “Incident Detection” which branches into “Report Incident” and “Automated Alert.” Both paths converge at “Initial Assessment,” leading to “Containment Actions” (e.g., disabling accounts, isolating systems). Next is “Investigation,” followed by “Eradication & Remediation” (patching, password resets). “System Restoration” follows, leading to “Post-Incident Review,” which concludes with “Plan Updates & Communication.” Each stage has a clear definition of actions and responsibilities. The flowchart visually depicts the sequential steps and decision points involved in effectively responding to an authentication breach.
Final Thoughts
Securing ProjectSend’s authentication isn’t just about ticking boxes; it’s about building a fortress against the relentless tide of cyber threats. By understanding the vulnerabilities, implementing robust mitigation strategies, and embracing a proactive security posture, you can significantly reduce your risk. Remember, a single breach can have devastating consequences. Proactive security is not an expense; it’s an investment in your peace of mind and the future of your project.