Hackers weaponizing typosquatted libraries? Yeah, it’s a thing, and it’s scarier than your grandma’s Wi-Fi password. Imagine this: you’re building your next killer app, innocently pulling in code from seemingly legit sources. But lurking beneath the surface, a tiny typo in a library name hides a Trojan horse, ready to unleash malware on your unsuspecting users – and potentially your entire business. This sneaky tactic, typosquatting, is becoming increasingly sophisticated, and understanding how it works is crucial for developers everywhere.
This deep dive explores the dark art of typosquatting, detailing how hackers create malicious library look-alikes, weaponize them for attacks ranging from data theft to complete system compromise, and the devastating consequences for developers who fall victim. We’ll cover detection methods, preventative measures, and real-world examples to arm you with the knowledge to stay ahead of these digital ninjas.
Typosquatting Techniques

Source: mod.uk
Typosquatting, in the context of software libraries, is a sneaky attack where malicious actors create packages with names very similar to legitimate ones, hoping developers will accidentally install the wrong version. This seemingly small mistake can have massive consequences, ranging from data breaches to the complete compromise of an application. The ease with which typosquatting can be achieved, coupled with the potential for devastating impact, makes it a persistent threat in the software development ecosystem.
Typosquatting methods rely on exploiting the human tendency to make typing errors. Hackers leverage this by creating packages with names containing slight variations of popular library names. These variations can be as subtle as a single character change, a swapped letter, or the addition/omission of a character. The more popular the library, the higher the likelihood of a successful typosquatting attack.
Predictable Typos in Library Names
Hackers often analyze the most common typos made when searching for or typing library names. They then register these variations as package names on package repositories like PyPI (Python Package Index) or npm (Node Package Manager). Common mistakes include replacing ‘o’ with ‘0’, ‘l’ with ‘1’, or adding extra characters. For instance, a malicious actor might create a package called `react-reduxx` to prey on developers searching for the legitimate `react-redux` package. The similarity is enough to fool a hurried developer, especially when searching through long lists of results.
The Role of Domain Name Registration in Typosquatting Attacks
While not directly involved in typosquatting library packages themselves, domain name registration plays a crucial role in broader typosquatting campaigns. Hackers often register domain names that mimic the legitimate library’s website or documentation. This allows them to create convincing phishing sites or to host malicious versions of the library’s documentation, further increasing the chances of a successful attack. For example, a malicious actor might register a domain like `react-redux.com.co` to appear similar to the legitimate `react-redux.com` website.
Examples of Malicious Typosquatted Libraries and Their Functionalities
Numerous instances of malicious typosquatted libraries have been documented. While specific examples are constantly evolving and often removed quickly, the general pattern remains consistent. These malicious packages often contain hidden code that steals sensitive data, installs backdoors, or executes other harmful actions. For example, a seemingly innocuous library might secretly log all user activity or inject malicious code into the application’s core functionality. Another example could be a package designed to steal API keys or other credentials, allowing attackers to gain unauthorized access to systems and data.
Comparison of Legitimate and Malicious Library Names
| Legitimate Library Name | Malicious Library Name | Type of Attack | Impact |
|---|---|---|---|
| requests | requuests | Character addition | Data theft, backdoor installation |
| axios | axiox | Character substitution | Credential theft, malicious code execution |
| lodash | lod4sh | Character substitution | System compromise, data exfiltration |
| express | exprees | Character omission | Remote code execution, denial-of-service |
Weaponization Methods
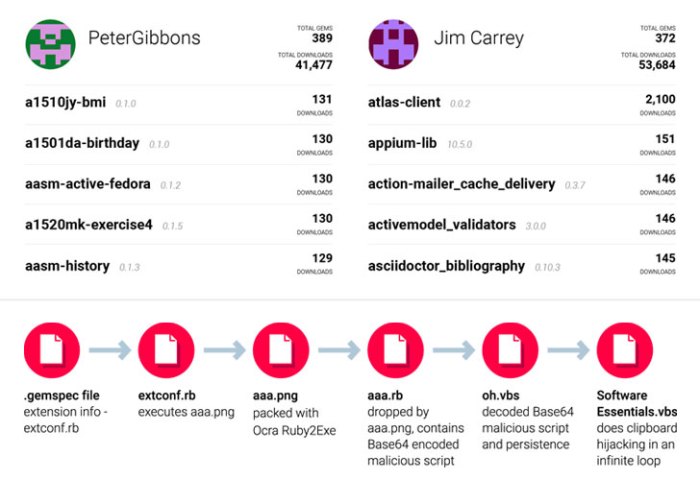
Source: thehackernews.com
Typosquatted libraries, subtly misspelled versions of legitimate packages, aren’t just innocent mistakes; they’re Trojan horses waiting to infiltrate your systems. Once downloaded, these seemingly harmless packages unleash a range of malicious activities, leveraging the trust developers place in package managers. Understanding how these libraries are weaponized is crucial for bolstering your software supply chain security.
The weaponization of typosquatted libraries relies on several key strategies, all designed to exploit the developer’s reliance on automated package management tools and their inherent trust in package repositories. These malicious packages often mimic legitimate libraries in both name and functionality, but contain hidden code designed to perform malicious actions. The attack vectors are multifaceted and often combined for maximum impact.
Attack Vectors, Hackers weaponizing typosquatted libraries
The success of a typosquatting attack hinges on the attacker’s ability to exploit the trust placed in automated dependency management. The most common vector is simply the inclusion of the malicious package in a project’s dependency list. This can happen through simple typos during manual package installation or through vulnerabilities in the package manager itself. Another vector involves compromising legitimate package repositories, either directly or indirectly, to insert the malicious package. This allows the attacker to target a wider range of potential victims without requiring individual compromises. Finally, sophisticated attacks might involve social engineering or supply chain attacks to subtly introduce the malicious package into a project’s dependencies.
Malware Families and Attack Types
Several malware families and attack types leverage typosquatted libraries. Information stealers are a frequent choice, designed to exfiltrate sensitive data like API keys, credentials, and proprietary code. These stealers often communicate with command-and-control servers to send the stolen data. Ransomware is another possibility; the malicious library could encrypt critical files or systems, demanding a ransom for decryption. Cryptojacking is also common, where the library secretly mines cryptocurrency, consuming system resources without the user’s knowledge or consent. Finally, backdoors are often installed, allowing attackers persistent access to the compromised system. These attacks can range from simple data exfiltration to complete system compromise.
Examples of Malicious Code
While specific examples of malicious code from typosquatted libraries are often obfuscated and evolve rapidly, the general principles remain consistent. A common tactic involves embedding malicious code within seemingly benign functions. For instance, a library designed for image processing might contain a function that appears to perform image resizing, but secretly uploads sensitive data to a remote server.
Example: A function named `resizeImage()` might appear legitimate, but secretly contains code that exfiltrates sensitive data in the background. This data exfiltration might be triggered by a specific event, such as the processing of a particular image file or the execution of a specific command.
Another technique involves using seemingly innocuous libraries as a cover for malicious activities. The attacker might create a legitimate-looking library that depends on a malicious, typosquatted library. This makes it more difficult to identify the malicious component because it is hidden within a chain of dependencies.
Typosquatting Attack Flowchart
Imagine a flowchart. The first box would be “Developer makes typo in package name.” This leads to a second box: “Malicious package downloaded.” Next, “Malicious code executes.” This branches into multiple boxes representing different malicious actions: “Data exfiltration,” “Ransomware deployment,” “Backdoor installation,” and “Cryptojacking.” Finally, all these branches converge into a single final box: “System compromised.” This visual representation illustrates the simplicity and effectiveness of the attack.
Impact and Consequences
The weaponization of typosquatted libraries represents a significant threat to the integrity and security of modern software development. The subtle nature of these attacks, coupled with the widespread reliance on third-party components, creates a potent vulnerability in the software supply chain, leading to potentially devastating consequences for both developers and end-users. The ripple effect of a successful attack can extend far beyond the initial compromise, impacting numerous applications and potentially causing widespread disruption.
The consequences for developers who unwittingly incorporate malicious typosquatted libraries into their projects are severe. Beyond the immediate security risks posed to their applications, developers face significant reputational damage, potential legal liabilities, and financial losses stemming from remediation efforts, lost revenue, and potential customer churn. The trust placed in a developer’s software is irrevocably damaged when vulnerabilities are discovered, leading to diminished credibility and a loss of market share.
Software Supply Chain Disruption
Compromised libraries introduce a critical vulnerability into the software supply chain. Imagine a scenario where a popular JavaScript library, widely used in thousands of applications, is typosquatted. A malicious actor replaces the legitimate library with a near-identical version containing a backdoor. This backdoor could allow the attacker to steal sensitive data, deploy ransomware, or conduct other malicious activities across all applications utilizing the compromised library. The scale of such an attack is enormous, affecting potentially millions of users and creating a widespread security crisis. The disruption to the software supply chain is multifaceted, impacting development timelines, security audits, and the overall confidence in the reliability of third-party components.
Developer Consequences
Developers who unknowingly integrate malicious libraries face a range of severe consequences. Firstly, their applications become vulnerable to attack, potentially leading to data breaches, financial losses for their clients, and reputational damage for their company. The cost of remediation, including security audits, code revisions, and communication with affected users, can be substantial. Furthermore, legal repercussions, including lawsuits from affected parties, are a real possibility. This can lead to significant financial burdens and long-term damage to the developer’s professional standing. For open-source projects, the reputational damage can extend to the entire community, undermining trust and impacting future contributions.
Financial and Reputational Damage
The financial impact of a successful typosquatting attack can be catastrophic. Costs associated with incident response, legal fees, remediation efforts, and potential compensation to affected users can quickly escalate into millions of dollars. Beyond the direct financial losses, the reputational damage can be equally devastating. A compromised application can lead to a loss of customer trust, damage to brand image, and a decline in market share. This reputational damage can persist for years, significantly hindering future growth and profitability. The long-term consequences can be far-reaching, affecting future investment and partnerships.
Mitigation Strategies
Preventing the use of malicious libraries requires a multi-layered approach. This includes thorough vetting of all third-party dependencies, employing robust dependency management tools, implementing code signing and verification mechanisms, and regularly scanning for vulnerabilities using automated tools. Maintaining an up-to-date understanding of known typosquatting attempts and utilizing automated security scanning solutions are also crucial steps. Furthermore, educating developers about the risks of typosquatting and best practices for dependency management is essential to mitigating the threat.
Hypothetical Attack Scenario
Let’s consider a hypothetical scenario involving a popular Python library, “requests.” A malicious actor creates a typosquatted version, “reqests,” and publishes it to a less reputable package repository. An unsuspecting developer, relying on automated dependency management, installs “reqests” instead of the legitimate “requests” library. The malicious library secretly logs all network traffic from the application, allowing the attacker to steal sensitive data, including API keys and user credentials. The impact is immediate and far-reaching, compromising the application’s security and potentially exposing a large number of users to data theft or other malicious activities. The developer faces the considerable costs of remediation, reputational damage, and potential legal repercussions.
Detection and Prevention

Source: mdpi.com
Typosquatting attacks, while insidious, aren’t insurmountable. Proactive measures and diligent monitoring can significantly reduce the risk of incorporating malicious libraries into your projects. A multi-layered approach, combining automated tools with careful manual review, is crucial for effective detection and prevention.
Detecting typosquatted libraries requires a combination of automated scanning and manual code review. This is because automated tools might miss subtle variations or cleverly disguised malicious packages. A robust strategy involves integrating several layers of security checks throughout the software development lifecycle.
Automated Scanning Tools and Techniques
Automated tools play a vital role in identifying potentially malicious libraries. These tools typically leverage techniques such as dependency analysis and code scanning to flag suspicious packages. They often compare the names of your project’s dependencies against known malicious packages or those with suspicious patterns. Many open-source and commercial tools are available to assist in this process. For instance, tools that integrate directly with package managers (like npm or pip) can analyze the dependency tree and alert you to any potentially compromised packages. Others might scan the code within the libraries for known malicious code signatures or suspicious behaviors.
Secure Library Management and Dependency Checks
Maintaining a secure library management strategy is paramount. This includes carefully vetting all libraries before inclusion, prioritizing well-maintained and reputable sources. Regularly updating dependencies is also critical, as updates often patch security vulnerabilities. Implementing a robust dependency management system, including clear versioning and dependency locking, helps prevent accidental inclusion of malicious libraries. Strict policies regarding the approval process for new libraries, including security audits and code reviews, should be in place. Furthermore, using a dedicated dependency management tool and actively monitoring security advisories can significantly reduce vulnerabilities.
Verifying Software Library Authenticity
Verifying the authenticity of a software library involves several steps. First, always download libraries from official repositories or trusted sources. Avoid using unofficial or third-party repositories unless absolutely necessary and after thorough verification. Next, cross-reference the library’s metadata, such as checksums and digital signatures, with the official source. Discrepancies can indicate tampering or a malicious imitation. Examining the library’s code for suspicious activity, such as unexpected network connections or file system modifications, is another essential step. Finally, reviewing the library’s code and its history for evidence of malicious intent, such as obfuscation or unusual behavior, is critical. This can be a manual process or automated with code analysis tools.
Preventative Measures for Developers
Preventing typosquatting attacks requires a proactive approach. Here’s a list of preventative measures developers can take:
- Use a robust dependency management system: Tools like npm, pip, or Maven offer features to manage and lock dependencies, reducing the chance of accidental inclusion of malicious libraries.
- Employ automated dependency scanning tools: Integrate tools that automatically scan for known malicious libraries into your development workflow.
- Regularly update dependencies: Staying current with security patches is crucial to mitigating vulnerabilities.
- Thoroughly vet libraries before inclusion: Verify the library’s authenticity, review its code, and check its reputation before incorporating it into your project.
- Verify the library’s source: Download libraries from official sources and trusted repositories only.
- Use checksums and digital signatures: Compare the downloaded library’s checksums and digital signatures with those provided by the official source to ensure authenticity.
- Implement code reviews: Regular code reviews can help identify malicious code or suspicious patterns.
- Train developers on security best practices: Educate developers about the risks of typosquatting and the importance of secure coding practices.
Case Studies: Hackers Weaponizing Typosquatted Libraries
Typosquatting attacks, while subtle, have had a significant real-world impact. Examining successful attacks reveals recurring patterns and highlights crucial lessons for developers and security professionals. Understanding these case studies is vital for bolstering defenses against future threats.
Several notable instances demonstrate the effectiveness and danger of typosquatting. These attacks often leverage the ease with which users can make minor typing errors, leading them to download malicious packages instead of legitimate ones. The consequences can range from data breaches to the complete compromise of systems.
The Eventbrite Typosquatting Incident
This incident involved a malicious package mimicking the legitimate Eventbrite library. The attacker registered a similarly named package on a popular package repository. Unsuspecting developers, mistyping the package name during installation, unknowingly downloaded and integrated the malicious code. The malicious package contained code designed to steal API keys and sensitive user data. The impact was significant, potentially exposing user information and allowing attackers to manipulate Eventbrite events. The attackers capitalized on the auto-completion features of package managers, further increasing the likelihood of accidental installation. This case highlights the importance of careful package verification and the implementation of robust security measures during the development process. The aftermath included immediate removal of the malicious package from the repository and a public awareness campaign urging developers to double-check package names.
A Case Study Involving a Popular JavaScript Library
Another example involved a typosquatted version of a widely used JavaScript library. The malicious package was nearly identical in name to the legitimate library, differing by only a single character. The attack leveraged the popularity of the original library, ensuring a large potential victim pool. The malicious code within the typosquatted library acted as a backdoor, allowing attackers remote access to systems using the compromised package. This incident underscores the vulnerability of relying solely on package name similarity for verification. It emphasizes the need for robust code review practices and the implementation of security scanning tools capable of detecting malicious code embedded within packages. The incident led to improved security practices within the affected development community, including more rigorous code audits and enhanced dependency management processes.
Comparison of Typosquatting Attacks
While the specific methods and payloads may vary, successful typosquatting attacks share common characteristics. They all exploit human error, leveraging the ease with which users can make typing mistakes. They often target popular and widely used libraries to maximize their impact. The malicious packages typically mimic legitimate ones closely, making detection challenging. Variations arise in the specific techniques used to deliver the malicious payload and the ultimate goal of the attack (data theft, system compromise, etc.). However, the core principle remains consistent: leveraging minor spelling variations to trick users into installing malicious code.
Conclusive Thoughts
In the ever-evolving landscape of cybersecurity, typosquatting presents a significant threat to developers and software supply chains. The subtle nature of these attacks highlights the critical need for vigilance and proactive security measures. From rigorous dependency checks to employing robust code scanning tools, protecting your projects from typosquatted libraries requires a multi-layered approach. Staying informed about emerging threats and adopting best practices are paramount to avoiding the potentially catastrophic consequences of falling prey to this insidious form of cybercrime. The fight against malicious code is ongoing, and understanding the enemy is the first step towards victory.





