Attack vectors with a malware sandbox: Dive deep into the shadowy world of malware analysis! We’ll unravel the mysteries of how these digital bad actors operate, exploring the common attack routes they use and the clever techniques employed to evade detection. Get ready for a thrilling journey into the heart of cybersecurity, where every line of code tells a story.
This exploration will cover the core functionality of a malware sandbox, from its components and analysis stages to the contrasting approaches of dynamic and static analysis. We’ll dissect prevalent attack vectors, including their detection methods and in-sandbox manifestations, and examine evasion tactics and countermeasures. The analysis extends to network and file-based attacks, illustrating how sandboxes monitor and analyze these threats. Finally, we’ll delve into advanced techniques like behavioral analysis and machine learning, showcasing how they enhance malware detection accuracy and efficiency.
Malware Sandbox Functionality
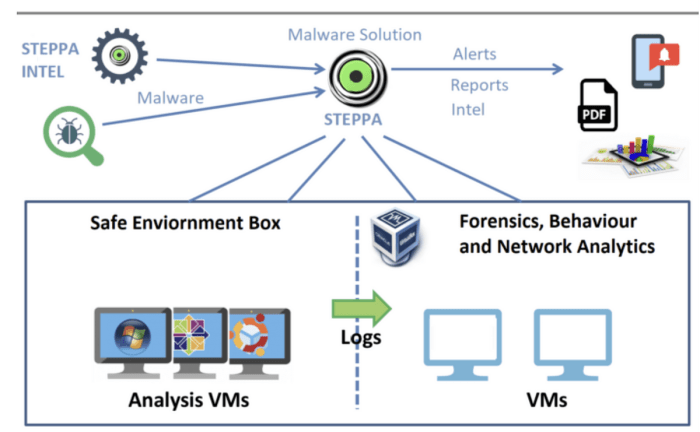
Malware sandboxes are essential tools in cybersecurity, providing a controlled environment to analyze malicious software without risking damage to your actual systems. Think of it as a digital quarantine zone for suspicious files. By observing the malware’s behavior within this safe space, analysts can understand its capabilities, identify its techniques, and ultimately develop defenses against it.
A typical malware sandbox environment consists of several core components working in concert. First, there’s the virtual machine (VM) or container, a highly isolated environment where the malware runs. This isolation is crucial, preventing the malware from accessing or affecting the host system’s resources. Next, a monitoring system constantly observes the malware’s activities, logging everything from system calls and network connections to file modifications and registry changes. This detailed log is invaluable for analysis. Finally, a reporting engine compiles the collected data into a comprehensive report, providing analysts with a clear picture of the malware’s behavior and functionality. This might include details about the malware’s communication channels, its objectives, and the techniques it uses to evade detection.
Malware Analysis Stages within a Sandbox
The analysis process within a sandbox typically unfolds in several distinct stages. Initially, the malware sample is uploaded and prepared for execution within the isolated environment. The next stage involves the actual execution of the malware, where the monitoring system diligently records its actions. This is followed by a detailed analysis of the collected data, which includes identifying malicious behaviors, extracting indicators of compromise (IOCs), and correlating the observed activities with known malware families or attack techniques. Finally, the sandbox generates a comprehensive report summarizing its findings. This report is crucial for incident response and threat intelligence.
Dynamic vs. Static Analysis Techniques
Malware sandboxes employ both dynamic and static analysis techniques to gain a comprehensive understanding of malicious software. Dynamic analysis involves executing the malware in the sandbox and observing its behavior in real-time. This approach allows analysts to identify actions that only occur during runtime, such as network connections, file creation, and registry modifications. In contrast, static analysis examines the malware’s code without executing it. This involves techniques like code disassembly, identifying function calls, and searching for known malicious patterns. Static analysis can reveal the malware’s structure and potential capabilities, even before it is run. While dynamic analysis provides insights into runtime behavior, static analysis helps uncover the malware’s underlying design and potential functionality. A combined approach, leveraging both dynamic and static analysis, offers the most complete picture.
Sandbox Architectures: Advantages and Disadvantages
Different sandbox architectures offer various trade-offs between performance, accuracy, and complexity. Choosing the right architecture depends on specific needs and resources.
| Architecture | Advantages | Disadvantages | Example Use Case |
|---|---|---|---|
| Virtual Machine (VM)-based | High isolation, accurate behavior emulation | Resource-intensive, slower analysis | Analyzing sophisticated malware with complex system interactions |
| Container-based | Lightweight, faster analysis | Lower isolation than VMs, potential for container escape | Quickly screening large volumes of samples for basic malicious behavior |
| Hardware-assisted | Very high speed and isolation, efficient resource utilization | High initial investment cost | High-throughput analysis in large security operations centers |
| Cloud-based | Scalability, accessibility, cost-effectiveness (potentially) | Dependence on internet connectivity, potential security concerns with data transfer | Analyzing malware samples from various sources for large organizations |
Common Attack Vectors Analyzed
Malware analysis in a sandbox environment is crucial for understanding how malicious code operates and for developing effective countermeasures. By observing the behavior of malware within a controlled, isolated space, security researchers can identify attack vectors, understand their techniques, and develop robust detection methods. This section details five prevalent attack vectors and their detection within a sandbox.
Fileless Malware Execution, Attack vectors with a malware sandbox
Fileless malware operates entirely within the system’s memory, avoiding the creation of persistent files on the disk. This makes detection challenging as traditional antivirus solutions relying on signature-based detection may miss it. Sandbox analysis focuses on monitoring system calls and memory manipulation. Detecting fileless malware involves observing unusual memory allocation patterns, process injections, and the execution of code from memory. For example, a sandbox might detect a fileless attack if it observes a process injecting code into another legitimate process without creating a new file on the disk. The sandbox’s monitoring tools would flag the unusual memory activity and the suspicious process injection as potential indicators of compromise.
Network Communication
Many malware samples establish outbound connections to command-and-control (C2) servers to receive instructions or exfiltrate stolen data. Sandboxes monitor network traffic for suspicious connections, unusual ports, and communication patterns. A sandbox can detect this by analyzing the network traffic generated by the malware, identifying connections to known malicious IP addresses or domains, or observing unusual communication volumes or patterns. For instance, a sandbox might observe a large volume of data being sent to an unknown IP address on an unusual port, indicating data exfiltration.
Registry Manipulation
Malware often modifies the Windows Registry to achieve persistence or to alter system settings. Sandboxes monitor registry key changes and value modifications. Detection involves analyzing registry activity for suspicious changes, such as the creation of new run keys that automatically execute malware upon system startup. A sandbox might flag a suspicious registry key change if the malware creates a new run key that executes a malicious script every time the system boots. This would indicate an attempt to establish persistence.
System Service Manipulation
Malware can exploit system services to gain elevated privileges or evade detection. Sandboxes monitor the creation, modification, and deletion of system services. Detection focuses on identifying suspicious service creation, unusual service parameters, or attempts to replace legitimate services with malicious ones. For example, a sandbox might detect a malicious service if it observes the creation of a new service with a suspicious name and path, which is designed to execute malicious code with elevated privileges.
Social Engineering Attacks (Phishing within the Sandbox)
While not directly executed by the malware itself, social engineering techniques often precede a malware infection. A sandbox, though not a complete user environment, can simulate user interaction and help identify phishing attempts. This involves analyzing the behavior of the malware if it attempts to manipulate user interaction within a limited sandbox environment, such as by displaying fake login prompts or attempting to extract credentials. This can be detected by monitoring user interface interactions within the sandbox and analyzing any attempts to capture user input. For example, the sandbox might detect a phishing attempt if the malware displays a fake login prompt designed to steal user credentials.
Malware Lifecycle in a Sandbox
A flowchart illustrating the typical lifecycle of a malware sample within a sandbox, highlighting key attack vector detection points, would show the following stages:
1. Sample Execution: The malware sample is executed in an isolated environment.
2. Behavior Monitoring: The sandbox monitors system calls, network traffic, registry changes, and memory activity.
3. Attack Vector Detection: Specific attack vectors (fileless execution, network communication, registry manipulation, etc.) are identified based on observed behavior.
4. Analysis & Reporting: The sandbox analyzes the collected data and generates a report detailing the malware’s behavior and identified attack vectors.
5. Containment & Quarantine: The sandbox isolates the malware and prevents further damage.
Evasion Techniques and Sandbox Detection
Malware authors are constantly developing new ways to outsmart security analysts, and the sandbox environment is no exception. Evasion techniques are crucial for malware to avoid detection and analysis, allowing it to successfully deploy its payload and achieve its malicious goals. Understanding these techniques is vital for improving sandbox efficacy and strengthening overall security posture.
Malware employs a range of sophisticated methods to evade detection within sandbox environments. These methods often involve analyzing the environment itself, looking for telltale signs that it’s not a typical user’s system. This allows the malware to alter its behavior or remain dormant, making analysis significantly more difficult.
Common Malware Evasion Techniques
Malware employs a variety of tactics to avoid detection within sandboxes. These techniques range from simple checks for virtual machine indicators to more complex code obfuscation and polymorphic behavior. Understanding these methods helps in developing robust countermeasures.
For instance, some malware checks for the presence of common virtualization software or specific hardware configurations associated with sandboxes. Others might detect the presence of debugging tools or unusual system activity indicative of a controlled environment. Advanced techniques involve analyzing system calls, network activity, and even the timing of processes to identify the controlled nature of the sandbox.
Examples of Sandbox Environment Identification and Adaptation
Many malware samples actively probe their environment for characteristics associated with sandbox analysis. One common technique is to check for the existence of specific files or registry keys known to be present in many sandbox environments. Another approach is to monitor system resources and network activity, looking for patterns inconsistent with a normal user’s system.
Imagine a piece of malware that checks for the presence of a specific virtual machine’s network adapter. If detected, it might choose to remain dormant or alter its behavior to avoid detection. Similarly, some malware samples might analyze the system’s CPU usage, memory allocation, or network bandwidth. If these metrics fall outside of a predetermined range, the malware could infer that it is running within a sandbox and adjust its operations accordingly.
Methods of Concealing Malicious Behavior
The goal of many evasion techniques is to hide the malware’s malicious behavior from the analyst. This can involve various strategies, from encrypting malicious code to using legitimate system calls for malicious purposes. The use of polymorphism, where the malware changes its code signature to avoid signature-based detection, is also common.
For example, a piece of malware might use steganography to hide its malicious payload within an image file. Or it might use a technique called “process hollowing,” where it replaces a legitimate process with its own malicious code, making it harder to trace its origin. Sophisticated malware can even employ anti-analysis techniques such as code obfuscation and packing, making it very difficult to reverse-engineer the code and understand its functionality.
Countermeasures Against Evasion Techniques
Several countermeasures can be implemented to mitigate the effectiveness of malware evasion techniques within a sandbox environment. These strategies aim to make the sandbox environment appear as realistic as possible while simultaneously providing tools for effective malware analysis.
Effective countermeasures require a multi-layered approach. This includes using advanced sandboxing techniques that simulate realistic user behavior, employ dynamic analysis to observe malware behavior in real-time, and utilize advanced code analysis tools to de-obfuscate malicious code.
- Employing advanced anti-analysis techniques to detect and counteract sandbox detection attempts.
- Using diverse sandbox configurations to avoid consistent detection patterns.
- Regularly updating sandbox environments and analysis tools.
- Leveraging behavioral analysis to identify malicious activities irrespective of code obfuscation.
- Implementing code de-obfuscation techniques to analyze the underlying malicious code.
Analyzing Network-Based Attack Vectors
Source: ac.kr
Malware sandboxes don’t just watch files; they meticulously monitor the network activity of suspicious software. This is crucial because many modern threats rely on network communication for command-and-control (C2) or data exfiltration. By observing this network traffic, analysts can gain valuable insights into the malware’s behavior and its ultimate goals.
Network-based analysis within a sandbox involves capturing and examining all network packets generated by the malware. This allows security researchers to identify malicious communication patterns, understand the malware’s infrastructure, and ultimately, prevent future attacks. This deep dive into network traffic is essential for understanding the full scope of a malware’s capabilities.
Network Traffic Capture and Analysis Methods
Sandboxes employ various methods to capture and analyze network traffic. These methods ensure that all communication attempts are recorded and scrutinized for malicious activity. The choice of method often depends on the sandbox’s architecture and the sophistication of the malware being analyzed. Common techniques include using virtual network interfaces, packet mirroring, and inline inspection. Virtual network interfaces allow the sandbox to isolate the malware’s network traffic, ensuring it doesn’t affect the host system. Packet mirroring creates a copy of the traffic without interrupting the network’s flow, while inline inspection actively monitors and filters network traffic in real-time.
Examples of Network-Based Attack Vectors
Malware frequently uses network communication for nefarious purposes. One common vector is command-and-control (C2) communication, where the malware connects to a remote server to receive instructions or updates. This could involve establishing connections to suspicious IP addresses or domains, using unconventional ports, or employing encryption to obfuscate communication. Data exfiltration is another prevalent attack vector, where stolen data is secretly transmitted to a remote server. This often involves techniques like using encrypted channels or breaking data into smaller packets to evade detection. For instance, a banking trojan might steal login credentials and transmit them to a C2 server in encrypted form, while a ransomware variant might exfiltrate encrypted files before demanding a ransom.
Comparison of Network Monitoring Techniques
| Technique | Description | Advantages | Disadvantages |
|---|---|---|---|
| Packet Capture (e.g., tcpdump, Wireshark) | Captures all network packets passing through a specified interface. | Comprehensive, detailed analysis possible; readily available tools. | Can generate large amounts of data, requiring significant storage and processing power; can be resource-intensive. |
| Network Virtualization | Creates a virtual network for the sandbox, isolating it from the host network. | Enhanced security, prevents malware from affecting the host system. | Requires more complex setup and configuration; might introduce performance overhead. |
| Inline Inspection | Monitors and filters network traffic in real-time. | Immediate detection of malicious activity; can block malicious connections. | Can introduce latency; requires careful configuration to avoid legitimate traffic being blocked. |
| Proxy-Based Monitoring | All network traffic is routed through a proxy server which monitors and logs it. | Centralized logging and analysis; easy to implement. | Can introduce performance overhead; requires careful configuration to avoid interfering with legitimate traffic. |
Analyzing File-Based Attack Vectors: Attack Vectors With A Malware Sandbox
Source: medium.com
Malware analysis within a sandbox often centers around understanding how malicious files interact with a system. File-based attacks leverage the inherent trust systems place in files to deliver payloads, ranging from simple scripts to sophisticated, multi-stage executables. Analyzing these vectors requires a detailed examination of file operations and the identification of suspicious behaviors.
File-based attack vectors are analyzed in a sandbox by monitoring the files a program interacts with, and analyzing the changes those interactions cause. This involves tracking file creation, modification, deletion, and access attempts. The sandbox environment provides a safe space to observe these actions without risking damage to a live system. By meticulously logging these events, analysts can reconstruct the attack and identify malicious activities.
Identifying Malicious File Operations
The identification of malicious file operations relies heavily on comparing observed behavior against known indicators of compromise (IOCs). This involves examining file metadata (creation timestamps, sizes, permissions), content analysis (searching for known malicious code signatures or patterns), and behavioral analysis (observing unusual file access patterns or interactions with other system components). For example, the creation of files in system directories with unusual names or permissions could indicate malicious activity. Similarly, the rapid modification of configuration files or the deletion of critical system logs can be strong indicators of a compromise. Anomalous file access patterns, such as attempts to access files with no legitimate reason, are also flagged. Automated tools within the sandbox can assist in this process, using machine learning to identify patterns and anomalies that might escape manual detection.
Examples of File-Based Attack Vectors
Malicious scripts, such as those written in PowerShell or JavaScript, can be used to execute commands or download further malicious payloads. These scripts often exploit system vulnerabilities or leverage social engineering techniques to gain execution. For instance, a seemingly benign .js file might download and execute a hidden executable from a remote server. Similarly, malicious executables, often disguised as legitimate programs, can directly execute harmful code upon execution. These can range from simple viruses that replicate themselves to sophisticated rootkits that conceal their presence on the system. Even seemingly innocuous document files (like .doc or .pdf) can contain embedded malicious macros or objects that execute malicious code when opened.
Identifying Malicious Code within Benign Files
Sandboxes employ various techniques to uncover malicious code hidden within seemingly benign files. Static analysis involves examining the file’s structure and content without executing it. This might include searching for known malware signatures, analyzing the file’s metadata, or using disassemblers to inspect the code. Dynamic analysis involves executing the file in a controlled environment and monitoring its behavior. This allows analysts to observe how the file interacts with the system and identify any malicious actions it might perform. Techniques such as code emulation and memory forensics can further assist in uncovering hidden malicious code. For example, a seemingly benign image file might contain a hidden executable embedded within its data stream. The sandbox would detect the execution of this hidden executable and its subsequent actions, even if the image file itself appeared harmless. The sandbox would log this activity, highlighting the malicious component despite its clever concealment.
Visualizing Attack Vector Analysis
Understanding malware behavior isn’t just about reading logs; it’s about seeing the bigger picture. Visual representations are crucial for making sense of the complex interactions within a sandbox environment, allowing analysts to quickly identify key attack stages and pinpoint evasion techniques. Effective visualization transforms raw data into actionable intelligence, streamlining the analysis process and improving overall efficiency.
Visual representations of malware execution within a sandbox provide a clear and concise overview of the attack’s progression. This allows analysts to easily identify critical stages, understand the malware’s interactions with the system, and ultimately determine its malicious intent. These visualizations are particularly useful for communicating findings to non-technical stakeholders.
Malware Execution Flow Visualization
A typical visualization would resemble a timeline, charting the malware’s actions over time. Imagine a horizontal axis representing time, and a vertical axis representing different system processes or files. Each action performed by the malware, such as creating a file, accessing a network resource, or modifying registry entries, is represented by a node on the timeline. These nodes are connected by arrows indicating the sequence of events. Color-coding could highlight different types of actions (e.g., file system operations in blue, network activity in red, registry modifications in green). For example, a node might show “File Created: C:\Users\Public\malicious.exe” at a specific timestamp, followed by an arrow leading to a node indicating “Network Connection: 192.168.1.100:8080,” illustrating the malware’s progression from file creation to establishing a network connection. The length of the arrows could even represent the time elapsed between actions. This visual timeline offers a comprehensive, chronological overview of the malware’s behavior within the sandbox.
Visual Representation of a File-Based Attack
Consider a hypothetical scenario where a malware sample uses a file-based attack vector. Our visual representation would show a central node representing the initial malware file. From this central node, several branches would extend. One branch might depict the malware unpacking itself, creating several additional files. These files would be represented as child nodes, linked to the parent node. Another branch could show the malware attempting to read and modify system configuration files, represented by nodes labeled with the file paths and the type of access (read, write, execute). A third branch might illustrate the malware attempting to execute a payload from one of the newly created files, visually linked to the relevant child node. Each node would contain metadata, such as timestamps, file sizes, and MD5 hashes. The entire diagram would clearly illustrate the chain of events, from the initial infection to the execution of the final payload, making it easy to understand the file-based attack’s progression. The color-coding scheme mentioned earlier would further enhance the visualization’s clarity.
Call Graphs and Control-Flow Graphs
Call graphs and control-flow graphs provide detailed insights into the malware’s internal workings. A call graph illustrates the function calls within the malware’s code, showing how different functions interact with each other. This can reveal the malware’s control flow and identify critical functions responsible for malicious actions. A control-flow graph, on the other hand, represents the sequence of instructions executed by the malware, highlighting loops, conditional statements, and function calls. These graphs are particularly useful for identifying obfuscation techniques and understanding the malware’s logic. Both graphs can be integrated into the overall visualization, providing a deeper understanding of the malware’s internal behavior and its connection to the external actions observed in the sandbox. Imagine these graphs as nested diagrams within the main timeline visualization, offering a zoomed-in view of specific functions or code segments. For example, a particular function responsible for establishing network connections could be expanded to show its internal call graph, providing detailed information about the underlying network communication mechanisms.
Advanced Sandbox Techniques
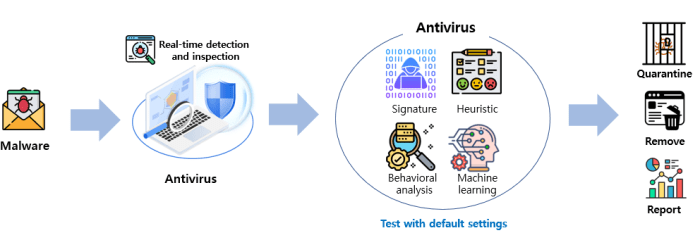
Traditional malware analysis often relies on signature-based detection, a reactive approach that struggles to keep pace with the ever-evolving landscape of sophisticated threats. Advanced sandboxes, however, leverage powerful techniques like behavioral analysis and machine learning to proactively identify malicious activity, even from unknown malware. This shift towards proactive detection significantly enhances the accuracy and efficiency of malware analysis.
Behavioral analysis goes beyond simply looking for known signatures; it observes the actions a program takes within a controlled environment. This allows for the identification of malicious behavior patterns, even if the specific code hasn’t been seen before. Machine learning algorithms further amplify this capability by learning from vast datasets of known malicious and benign software behaviors, enabling the system to identify subtle anomalies indicative of malicious intent.
Machine Learning Algorithms in Malware Detection
Machine learning plays a crucial role in enhancing the effectiveness of advanced sandboxes. Various algorithms, such as Support Vector Machines (SVMs), Random Forests, and Neural Networks, are employed to analyze the massive amounts of data generated within the sandbox environment. These algorithms learn to distinguish between benign and malicious behaviors by identifying patterns and correlations in system calls, registry modifications, network connections, and other observable actions. For instance, an SVM might be trained to classify malware based on the frequency and sequence of specific system calls, while a neural network could analyze a broader range of behavioral features to identify more complex attack patterns. The application of these algorithms allows sandboxes to detect zero-day exploits and polymorphic malware that would evade traditional signature-based systems.
Comparison of Signature-Based and Behavioral Analysis
Traditional signature-based detection relies on identifying known malware signatures—specific code patterns or characteristics—within a file. This approach is relatively simple to implement but is limited by its reactive nature. New malware variants or obfuscated code can easily bypass signature-based systems. In contrast, behavioral analysis focuses on the actions of a program, rather than its code. This proactive approach allows for the detection of unknown malware by identifying suspicious behaviors, such as unauthorized network connections, attempts to modify system files, or unusual memory access patterns. Behavioral analysis is more robust against evasion techniques and can detect novel malware variants that lack known signatures. The combination of both methods offers the most comprehensive protection. Think of it like this: signature-based detection is like searching for a specific criminal’s face in a crowd, while behavioral analysis is like observing the crowd for suspicious actions, such as someone attempting to pickpocket others.
Examples of Advanced Sandbox Improvements
Advanced sandbox techniques significantly improve malware detection in several ways. For example, consider the case of a new ransomware variant that employs sophisticated obfuscation techniques to evade signature-based detection. A behavioral analysis sandbox can still detect this malware by observing its actions: encryption of user files, communication with a command-and-control server, and attempts to delete backups. Similarly, advanced sandboxes can effectively analyze polymorphic malware, which changes its code each time it runs, making signature-based detection ineffective. By focusing on behavioral patterns, these sandboxes can identify the malicious intent even if the code itself is different. The improved accuracy and efficiency translate to faster identification of threats, reduced response times, and minimized damage caused by malicious software. Furthermore, machine learning algorithms can continuously adapt and improve their detection capabilities by learning from new data, making the system more resilient to evolving threats.
Final Wrap-Up
Source: medium.com
Understanding attack vectors within a malware sandbox is crucial for effective cybersecurity. By dissecting the techniques used by malicious actors and the countermeasures employed by analysts, we can build a more robust defense against emerging threats. This journey into the digital underbelly highlights the constant arms race between attackers and defenders, a battle fought line by line of code within the virtual confines of the sandbox. The insights gained equip us to better anticipate and neutralize future attacks.





