CISA details red teams activity including TTPs network defense – sounds intense, right? It is. This deep dive explores how the Cybersecurity and Infrastructure Security Agency (CISA) uses red teams to probe organizational defenses, the sophisticated tactics, techniques, and procedures (TTPs) they employ, and how you can beef up your network security to withstand their (and other attackers’) assaults. We’ll unpack CISA’s red team methodologies, the specific TTPs used, and the crucial network defense strategies needed to stay ahead of the game. Get ready to level up your cybersecurity game.
We’ll examine real-world examples of successful CISA red team engagements, highlighting the vulnerabilities uncovered and the subsequent remediation strategies. Think of it as a behind-the-scenes look at the cutting edge of cybersecurity defense, showing you exactly what the pros are doing – and how you can replicate their success in your own organization. We’ll even cover the reporting process and best practices for communicating findings to stakeholders, so you can make informed decisions about your security posture.
CISA Red Team Activities
CISA’s red teaming activities are a crucial part of the agency’s mission to enhance cybersecurity across the nation. These engagements simulate real-world cyberattacks to identify vulnerabilities and improve defensive capabilities within critical infrastructure and government entities. The goal is proactive risk mitigation, preventing potentially devastating breaches before they occur.
Scope and Objectives of CISA Red Team Activities
CISA red teams conduct sophisticated, simulated cyberattacks against targeted organizations. The scope encompasses a wide range of attack vectors, from phishing campaigns and malware infections to exploiting known vulnerabilities in software and network infrastructure. Objectives include identifying vulnerabilities, assessing the effectiveness of existing security controls, and providing actionable recommendations for improvement. This proactive approach aims to strengthen the nation’s cybersecurity posture against increasingly sophisticated threats.
Targeted Organizations
CISA red teams target a diverse range of organizations, prioritizing those deemed critical to national infrastructure and security. This includes federal government agencies, state and local governments, and private sector entities involved in sectors like energy, healthcare, and finance. The selection process focuses on organizations that represent significant national interests and could suffer catastrophic consequences from a successful cyberattack.
Target Selection Process
The selection of targets for CISA red team engagements is a multi-faceted process. It involves careful consideration of several factors, including the organization’s criticality to national infrastructure, its cybersecurity posture (based on available risk assessments), and the potential impact of a successful cyberattack. Vulnerability assessments and threat intelligence are also key components in this decision-making process. Prioritization is based on a risk-based approach, focusing on the highest-impact targets.
Examples of Successful CISA Red Team Engagements
While specific details of CISA red team engagements are often kept confidential to protect operational security and avoid providing adversaries with actionable intelligence, public reports frequently highlight the effectiveness of these activities. For instance, CISA’s engagements have consistently uncovered critical vulnerabilities in various organizations’ security controls, leading to significant improvements in their defensive capabilities. These successes have often resulted in the implementation of enhanced security protocols, improved incident response plans, and increased awareness of potential threats. The outcomes of these engagements are frequently shared (in anonymized form) with the broader cybersecurity community to promote better overall security practices.
Comparison of CISA Red Team Methodologies
| Methodology | Target | Techniques | Outcomes |
|---|---|---|---|
| Simulated Phishing Campaign | Federal Agency | Spear phishing emails, malicious links, social engineering | Identification of vulnerabilities in employee training and email security |
| Network Penetration Testing | Critical Infrastructure Provider | Vulnerability scanning, exploitation of known vulnerabilities, lateral movement | Discovery of exploitable weaknesses in network security controls, improved network segmentation |
| Red Team Exercise focusing on insider threat | State Government Agency | Social engineering, data exfiltration, privilege escalation | Enhanced security awareness training, improved access control policies, strengthened data loss prevention measures |
| Supply Chain Attack Simulation | Major Financial Institution | Compromise of third-party vendor, lateral movement to target systems | Improved vendor risk management practices, enhanced security controls for third-party access |
Threat Tactics, Techniques, and Procedures (TTPs) Employed by CISA Red Teams: Cisa Details Red Teams Activity Including Ttps Network Defense
Source: radware.com
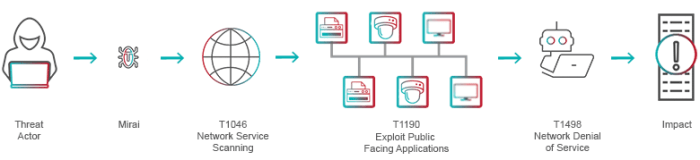
CISA red teams, acting as sophisticated adversaries, employ a diverse range of tactics, techniques, and procedures (TTPs) to rigorously test the security posture of federal agencies and critical infrastructure. Their actions aren’t about malice; instead, they provide invaluable insights into vulnerabilities, ultimately strengthening national cybersecurity. Understanding these TTPs is key to appreciating the depth and breadth of CISA’s efforts.
Common TTPs Used by CISA Red Teams
CISA red teams leverage a wide array of TTPs, mirroring real-world threats. These techniques are carefully selected based on the specific target and objectives of the engagement. The goal is to simulate realistic attacks, revealing vulnerabilities that might otherwise go undetected. Common TTPs frequently employed include phishing campaigns (using spear-phishing and watering hole attacks), exploiting known vulnerabilities (using publicly available exploits and zero-day vulnerabilities where appropriate), lateral movement within networks (using techniques like pass-the-hash and exploiting trust relationships), data exfiltration (using various methods like covert channels and compromised accounts), and denial-of-service attacks.
Rationale Behind TTP Selection in Different Scenarios
The choice of TTPs is highly contextual. A red team engagement focused on a financial institution might prioritize techniques related to data exfiltration and financial fraud, whereas an engagement targeting a power grid might focus on industrial control system (ICS) compromise and disruption techniques. For instance, a scenario involving a suspected insider threat might incorporate social engineering and privilege escalation tactics, whereas an external threat simulation might involve network scanning and exploitation of publicly exposed services. The selection always aims to realistically mirror the most likely attack vectors and objectives for a given target.
Comparison of CISA Red Team TTPs with Those of Other Threat Actors
While CISA red teams employ many TTPs similar to those used by real-world threat actors, there are key differences. CISA adheres to strict ethical guidelines and legal limitations, focusing on identifying vulnerabilities without causing actual damage. Advanced persistent threats (APTs), for example, often operate with far greater stealth and persistence, potentially remaining undetected for extended periods. Criminal groups, meanwhile, might focus on specific financial gains, employing techniques optimized for rapid monetary return. The key difference lies in the intent: CISA aims for improvement; other actors may aim for exploitation.
Hypothetical Red Team Engagement Scenario and Employed TTPs
Consider a hypothetical scenario targeting a fictitious hospital. The red team’s objective is to assess the hospital’s ability to detect and respond to a ransomware attack. The engagement might begin with a phishing campaign targeting hospital staff, delivering a malicious attachment. Successful infection would lead to lateral movement within the network, aiming to compromise critical systems such as patient records and medical devices. Data exfiltration would be attempted, simulating a ransomware deployment. Finally, the team would assess the hospital’s incident response capabilities and recovery time. The TTPs used would include spear-phishing, malware delivery, lateral movement techniques, data exfiltration, and ransomware deployment.
Categorization of TTPs Based on the MITRE ATT&CK Framework
The MITRE ATT&CK framework provides a standardized taxonomy for categorizing adversary behaviors. The hypothetical hospital scenario above would involve TTPs across multiple ATT&CK categories, including:
* Initial Access: Spear-phishing, exploiting vulnerabilities in publicly exposed services. This involves the initial intrusion into the network.
* Execution: Malware delivery and execution within the compromised systems. This involves running malicious code.
* Persistence: Establishing persistence to maintain access to the compromised systems. This ensures continued access even after a reboot.
* Privilege Escalation: Gaining higher-level access to critical systems and data. This grants access to more sensitive information.
* Defense Evasion: Techniques to avoid detection by security tools. This includes avoiding anti-virus and intrusion detection systems.
* Credential Access: Obtaining credentials to access sensitive systems and data. This involves stealing passwords or other authentication information.
* Discovery: Identifying valuable assets and systems within the network. This involves reconnaissance and mapping the network.
* Lateral Movement: Moving laterally within the network to compromise additional systems. This involves spreading the attack across the network.
* Data Exfiltration: Exfiltrating sensitive data from the network. This involves stealing data and moving it out of the network.
* Impact: The ultimate impact of the attack, such as data encryption (ransomware). This is the final effect of the attack.
Network Defense Strategies Against CISA Red Team TTPs
Source: grotto-networking.com
CISA red teams employ sophisticated techniques to penetrate networks, mirroring real-world attacker tactics. Effective defense requires a multi-layered approach, focusing on proactive security measures and robust incident response capabilities. Understanding the specific TTPs used by CISA red teams is crucial for developing targeted defenses. This section details key network security controls, their implementation, limitations, and complementary strategies to bolster overall network resilience.
Key Network Security Controls and Their Implementation
Implementing strong network security controls is paramount in mitigating the risks posed by CISA red team activities. These controls act as a layered defense, making it significantly harder for attackers to achieve their objectives. Effective implementation requires a thorough understanding of the organization’s network architecture and security posture.
- Intrusion Detection/Prevention Systems (IDS/IPS): IDS/IPS systems monitor network traffic for malicious activity, alerting security personnel to potential threats and, in the case of IPS, automatically blocking them. Implementation involves deploying sensors strategically throughout the network, configuring them with appropriate rulesets based on known CISA red team TTPs and threat intelligence feeds, and integrating them with a Security Information and Event Management (SIEM) system for centralized monitoring and analysis.
- Firewall Management: Firewalls act as the first line of defense, controlling network access based on pre-defined rules. Effective implementation requires regularly reviewing and updating firewall rules to reflect current threat landscapes and known CISA red team tactics, employing stateful inspection to track network connections, and implementing robust logging and monitoring capabilities.
- Endpoint Detection and Response (EDR): EDR solutions monitor endpoint devices (computers, servers, etc.) for malicious activity, providing real-time visibility into potential compromises. Implementation involves deploying agents on all endpoints, configuring them for comprehensive monitoring, and integrating them with a centralized management console for threat hunting and incident response.
Limitations of Network Security Controls and Complementary Measures
While crucial, individual network security controls have inherent limitations. A layered approach, combining multiple controls, is necessary for comprehensive protection.
- IDS/IPS Limitations: IDS/IPS systems can be bypassed by sophisticated attackers who utilize evasion techniques. Complementary measures include advanced threat protection solutions that leverage machine learning and behavioral analysis to detect advanced persistent threats (APTs).
- Firewall Limitations: Firewalls can be circumvented through techniques like tunneling or exploiting vulnerabilities in applications running behind them. Complementary measures include application control and web application firewalls (WAFs) to further restrict access and protect against application-layer attacks.
- EDR Limitations: EDR solutions rely on agents deployed on endpoints, making them vulnerable to attacks that target the agent itself. Complementary measures include robust endpoint security hygiene, including regular patching and software updates, and employing techniques like micro-segmentation to limit the impact of compromised endpoints.
Best Practices for Network Defense Against CISA Red Team Activities
Proactive measures and continuous improvement are vital for effective network defense.
- Regular Security Audits and Penetration Testing: Regularly assess network security posture through vulnerability scans, penetration testing, and red team exercises to identify weaknesses and improve defenses.
- Employee Security Awareness Training: Educate employees about phishing attacks, social engineering, and other common attack vectors to reduce human error, a major vulnerability in many organizations.
- Incident Response Planning and Rehearsals: Develop a comprehensive incident response plan and regularly rehearse it to ensure readiness in the event of a security breach.
- Threat Intelligence Integration: Leverage threat intelligence feeds to stay informed about emerging threats and proactively adjust security controls.
- Zero Trust Security Model: Adopt a zero-trust security model, verifying every user and device before granting access to resources, regardless of network location.
Network Segmentation and Enhanced Network Defense
Network segmentation divides the network into smaller, isolated segments, limiting the impact of a security breach. If one segment is compromised, the attacker’s lateral movement is restricted, preventing access to other sensitive areas. Implementing network segmentation involves carefully planning the network architecture, using firewalls and other access control mechanisms to restrict traffic flow between segments, and regularly reviewing the segmentation strategy to ensure its effectiveness. This approach significantly enhances the overall effectiveness of network defenses against CISA red team TTPs by containing the blast radius of a successful attack.
CISA Red Team Reporting and Remediation
CISA red team reports provide a crucial bridge between simulated attacks and real-world security improvements. These reports aren’t just lists of vulnerabilities; they’re detailed roadmaps guiding organizations toward stronger defenses. Understanding their format and the subsequent remediation process is vital for leveraging the full value of a CISA red team engagement.
CISA red team reports typically follow a structured format, prioritizing clarity and actionable insights. The report begins with an executive summary, highlighting the key findings and their potential impact. This is followed by a detailed methodology section, outlining the scope, tools, and techniques employed during the assessment. The core of the report lies in its vulnerability descriptions, which detail each identified weakness, its severity, potential impact, and supporting evidence (e.g., screenshots, logs). Finally, the report concludes with recommendations for remediation, prioritizing the most critical vulnerabilities and providing guidance on effective mitigation strategies. This structured approach ensures that organizations can quickly grasp the situation and focus their remediation efforts effectively.
CISA Red Team Report Content and Structure
A typical CISA red team report includes sections detailing the engagement’s objectives, scope, and methodology. A comprehensive description of the identified vulnerabilities follows, categorized by severity and impact. Each vulnerability includes details on the exploited techniques, the attack path, and evidence gathered during the assessment. The report also presents a risk assessment, quantifying the potential damage from each vulnerability, and concludes with specific remediation recommendations, prioritized based on criticality and feasibility. The inclusion of a timeline detailing the assessment activities enhances the report’s comprehensiveness. Finally, appendices might include detailed technical information or supporting documentation.
Remediation Process Based on CISA Red Team Findings
The remediation process begins with a thorough review of the CISA red team report. This involves prioritizing vulnerabilities based on their severity and potential impact, considering factors like business criticality and data sensitivity. Next, a remediation plan is developed, outlining the steps required to address each vulnerability, including timelines, responsible parties, and required resources. This plan is then implemented, with progress tracked and documented. Finally, a validation process verifies that the implemented remediation measures effectively mitigate the identified vulnerabilities. Regular security assessments are essential to ensure ongoing protection.
Effective Remediation Strategies for Common Vulnerabilities
Effective remediation strategies vary depending on the specific vulnerability. For example, addressing a vulnerability related to weak passwords requires implementing strong password policies, enforcing multi-factor authentication (MFA), and conducting regular password audits. Similarly, vulnerabilities related to unpatched software necessitate a robust patch management program, involving regular vulnerability scanning, prompt patch deployment, and rigorous testing. Network security vulnerabilities often require implementing firewalls, intrusion detection/prevention systems (IDS/IPS), and network segmentation. Finally, addressing phishing vulnerabilities requires comprehensive security awareness training for employees, coupled with robust email filtering and anti-phishing measures. These strategies emphasize proactive and layered security approaches.
Communicating Findings and Remediation Plans to Stakeholders
Effective communication is crucial for successful remediation. Findings should be communicated clearly and concisely to both technical and non-technical stakeholders. This involves using accessible language, avoiding technical jargon whenever possible, and focusing on the impact of vulnerabilities on the organization. Remediation plans should be equally transparent, outlining the steps involved, the timeline, and the responsible parties. Regular updates on progress are essential, keeping stakeholders informed and building confidence in the remediation process. A collaborative approach, involving all stakeholders in the process, fosters buy-in and ensures successful implementation.
Sample Remediation Plan
Let’s assume a CISA red team report identifies a vulnerability in a web application allowing SQL injection. The remediation plan would involve:
Phase 1: Assessment (1 week): Detailed analysis of the vulnerable code to understand the extent of the vulnerability.
Phase 2: Remediation (2 weeks): Implementing parameterized queries or stored procedures to prevent SQL injection attacks. Thorough testing of the implemented changes to ensure effectiveness.
Phase 3: Validation (1 week): Conducting penetration testing to verify that the vulnerability has been successfully remediated. Reviewing logs and security alerts to confirm the absence of further SQL injection attempts.
Phase 4: Documentation (1 week): Updating security documentation to reflect the changes made and lessons learned. Creating a training module for developers to prevent similar vulnerabilities in the future.
This plan demonstrates a structured approach, allocating specific timeframes and responsibilities for each stage. Regular progress reports would keep stakeholders informed throughout the process.
Impact and Lessons Learned from CISA Red Team Activities
Source: contentstack.io
CISA red team engagements offer invaluable insights into an organization’s cybersecurity posture, revealing vulnerabilities that traditional security assessments often miss. These activities go beyond theoretical assessments, providing real-world demonstrations of attack vectors and their potential impact, ultimately leading to stronger, more resilient defenses. The lessons learned extend far beyond immediate remediation; they inform long-term security strategies and contribute to a more proactive security culture.
The impact of CISA red team activities is multifaceted. Immediately, they identify critical vulnerabilities, from misconfigured systems to exploitable software flaws. In the long term, they foster a more mature security culture within the organization, driving improvements in incident response planning, threat intelligence integration, and employee security awareness training. The insights gained are invaluable in refining security architectures and prioritizing resource allocation for maximum effectiveness.
CISA Red Team Impact on Organizational Cybersecurity
CISA red team activities directly improve an organization’s cybersecurity posture by providing a realistic assessment of its defenses. The findings highlight weaknesses in areas such as network segmentation, endpoint security, and identity and access management. This allows organizations to prioritize remediation efforts based on the actual risk posed, rather than relying on theoretical assessments. For example, a red team engagement might reveal a critical vulnerability in a web application that could lead to a data breach. This knowledge allows the organization to immediately patch the vulnerability and implement stronger security controls, mitigating the risk of a successful attack. This proactive approach, driven by the red team’s findings, significantly reduces the organization’s attack surface and enhances its overall resilience.
Lessons Learned from CISA Red Team Engagements
Several key lessons consistently emerge from CISA red team engagements. Firstly, the importance of strong security fundamentals is paramount. Basic hygiene practices, such as patching systems regularly, implementing strong password policies, and regularly updating software, are often overlooked, yet they represent the first line of defense against many attacks. Secondly, the value of robust security awareness training for employees cannot be overstated. Many successful attacks exploit human error, such as clicking on phishing links or falling for social engineering tactics. Thirdly, regular security assessments and penetration testing, including red team engagements, are crucial for maintaining a strong security posture. These assessments provide a continuous feedback loop, allowing organizations to identify and address vulnerabilities before they can be exploited by malicious actors. Finally, effective incident response planning is critical. A well-defined incident response plan ensures that organizations can quickly and effectively respond to security incidents, minimizing their impact.
Benefits of Proactive Security Measures, Cisa details red teams activity including ttps network defense
The findings from CISA red team engagements strongly advocate for proactive security measures. A reactive approach, where security issues are addressed only after an incident occurs, is far less effective and far more costly. Proactive measures, such as regular vulnerability scanning, penetration testing, and security awareness training, allow organizations to identify and mitigate risks before they can be exploited. This approach minimizes the likelihood of successful attacks, reduces the potential impact of incidents, and ultimately saves time and resources. Investing in proactive security measures is an investment in the long-term security and resilience of the organization.
Case Study: Fictional Example of a CISA Red Team Engagement and Remediation
Consider a fictional financial institution, “First National Bank,” that underwent a CISA red team engagement. The red team successfully exploited a vulnerability in the bank’s web application, gaining unauthorized access to customer data. This breach was facilitated by an outdated version of the application’s underlying framework and insufficient input validation. Following the engagement, First National Bank immediately implemented several remediation measures. They upgraded the web application framework, implemented robust input validation, strengthened access controls, and enhanced their intrusion detection system. Furthermore, they conducted comprehensive employee security awareness training to prevent similar vulnerabilities from being exploited in the future. The CISA report detailed the attack path, highlighting the specific vulnerabilities exploited, and provided recommendations for remediation. This allowed the bank to strengthen its security posture and prevent future breaches.
Visual Representation of CISA Red Team Activities, Vulnerabilities, and Remediation
Imagine a flowchart. The starting point is “CISA Red Team Activities,” branching out to several boxes representing “Identified Vulnerabilities” (e.g., outdated software, weak passwords, misconfigured firewall). Each vulnerability box then leads to a “Remediation Efforts” box, showing specific actions taken (e.g., software updates, password changes, firewall configuration adjustments). Lines connect these boxes, demonstrating the direct relationship between the red team’s findings, the identified weaknesses, and the subsequent remediation steps. The flowchart visually illustrates the process of identifying, addressing, and mitigating security risks, demonstrating the direct impact of CISA red team activities on improving an organization’s overall security.
Final Conclusion
So, CISA’s red team activities aren’t just about finding weaknesses; they’re about building a stronger, more resilient cybersecurity landscape. By understanding the TTPs employed by these elite teams and implementing robust network defense strategies, organizations can proactively mitigate risks and enhance their overall security posture. This isn’t just about patching vulnerabilities; it’s about adopting a proactive mindset and embracing continuous improvement in your cybersecurity journey. The insights gained from CISA’s work are invaluable, offering a roadmap to bolster your defenses and stay one step ahead of the ever-evolving threat landscape. Are you ready to take your security to the next level?





