Denial of servicedos attack – Denial of Service (DoS) attacks: the digital equivalent of a mob storming a building, shutting down vital online services. These attacks, ranging from simple floods to sophisticated, distributed assaults, cripple websites, online businesses, and even critical infrastructure. Understanding the mechanics, vulnerabilities, and defenses against DoS attacks is crucial in today’s hyper-connected world, where a single attack can have devastating consequences.
From the basics of how these attacks work –think overwhelming a server with traffic until it buckles— to the advanced strategies used by attackers, this guide explores the full spectrum of DoS attacks. We’ll examine the various types, including volumetric, protocol, and application attacks, and delve into the vulnerabilities they exploit, such as weak security protocols and insufficient server resources. We’ll also cover mitigation strategies, from firewalls and intrusion detection systems to the use of CDNs and rate limiting techniques, and explore real-world examples of the devastating impact these attacks can have.
Denial of Service (DoS) Attacks
Denial-of-service (DoS) attacks are a persistent threat to online services, ranging from small websites to massive global infrastructures. Understanding their mechanics is crucial for building resilient systems and mitigating their impact. Essentially, a DoS attack aims to disrupt or make a service unavailable to legitimate users by flooding it with traffic or exploiting vulnerabilities.
DoS attacks work by overwhelming a target system’s resources, preventing it from responding to legitimate requests. This overload can manifest in various forms, depending on the attack’s method and the target’s vulnerabilities. The ultimate goal is simple: to make the service unusable for its intended audience. Think of it like clogging a highway with enough cars that no one can get through.
Types of DoS Attacks
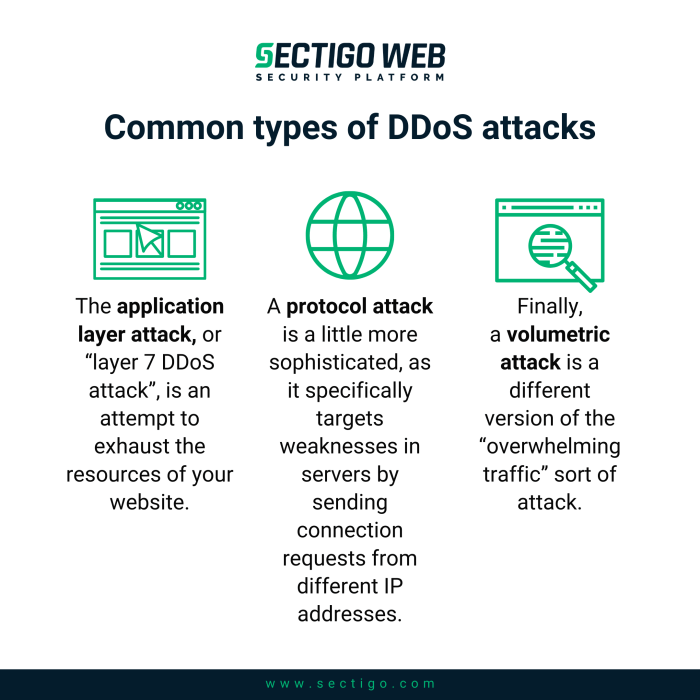
DoS attacks aren’t a monolithic entity; they come in various flavors, each with its own characteristics and attack vector. Categorizing them helps in understanding their nuances and devising appropriate countermeasures.
- Volumetric Attacks: These attacks flood the target with massive amounts of traffic, consuming bandwidth and overwhelming network resources. Examples include UDP floods and ICMP floods, which send a deluge of packets to the target, exhausting its capacity to process them. Imagine a firehose constantly spraying water – the target system simply can’t handle the sheer volume.
- Protocol Attacks: These attacks exploit vulnerabilities in network protocols to disrupt communication. SYN floods, for example, exploit the TCP three-way handshake by sending a massive number of SYN requests without completing the connection, consuming server resources. Think of it as someone constantly ringing your doorbell and then hanging up before you answer, preventing you from answering legitimate calls.
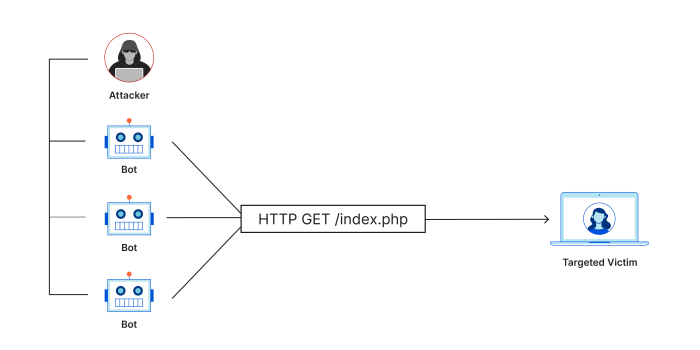
- Application Layer Attacks: These attacks target specific applications or services, exploiting vulnerabilities in their software to disrupt their functionality. HTTP floods, for example, send a large number of requests to a web server, overloading it and making it unresponsive. This is like sending so many orders to a restaurant that the kitchen staff can’t keep up, resulting in delays and ultimately, an inability to serve customers.
Real-World Examples and Impact
Numerous high-profile DoS attacks have demonstrated the devastating consequences of these assaults. The 2016 Dyn DDoS attack, for instance, targeted Dyn, a major DNS provider, resulting in widespread outages for websites like Twitter, Netflix, and Spotify. The sheer scale of the attack crippled internet access for millions of users, highlighting the potential for significant disruption. Another example is the Mirai botnet, which used compromised IoT devices to launch massive DDoS attacks, showcasing the vulnerability of interconnected systems. These attacks cause financial losses, reputational damage, and disruption of essential services.
Comparison of DoS Attack Vectors
Different DoS attacks utilize different methods to achieve their goal. Volumetric attacks focus on sheer volume, while protocol attacks exploit vulnerabilities in network protocols. Application layer attacks target specific applications. The choice of attack vector often depends on the attacker’s resources and the target’s vulnerabilities. A sophisticated attacker might combine multiple vectors for a more effective attack.
Hypothetical DoS Attack Scenario
Imagine a popular online gaming platform. A malicious actor launches a distributed denial-of-service (DDoS) attack, utilizing a botnet of compromised devices. The attack employs a multi-vector approach, combining volumetric attacks (UDP floods) with application layer attacks (exploiting vulnerabilities in the game’s login server). The sheer volume of traffic overwhelms the platform’s network infrastructure, and the targeted application-layer attacks further cripple the login system, making it impossible for legitimate players to access the game. This results in significant downtime, frustrated players, and potential financial losses for the gaming company. The attack demonstrates the effectiveness of a coordinated, multi-vector approach in achieving a successful DoS attack.
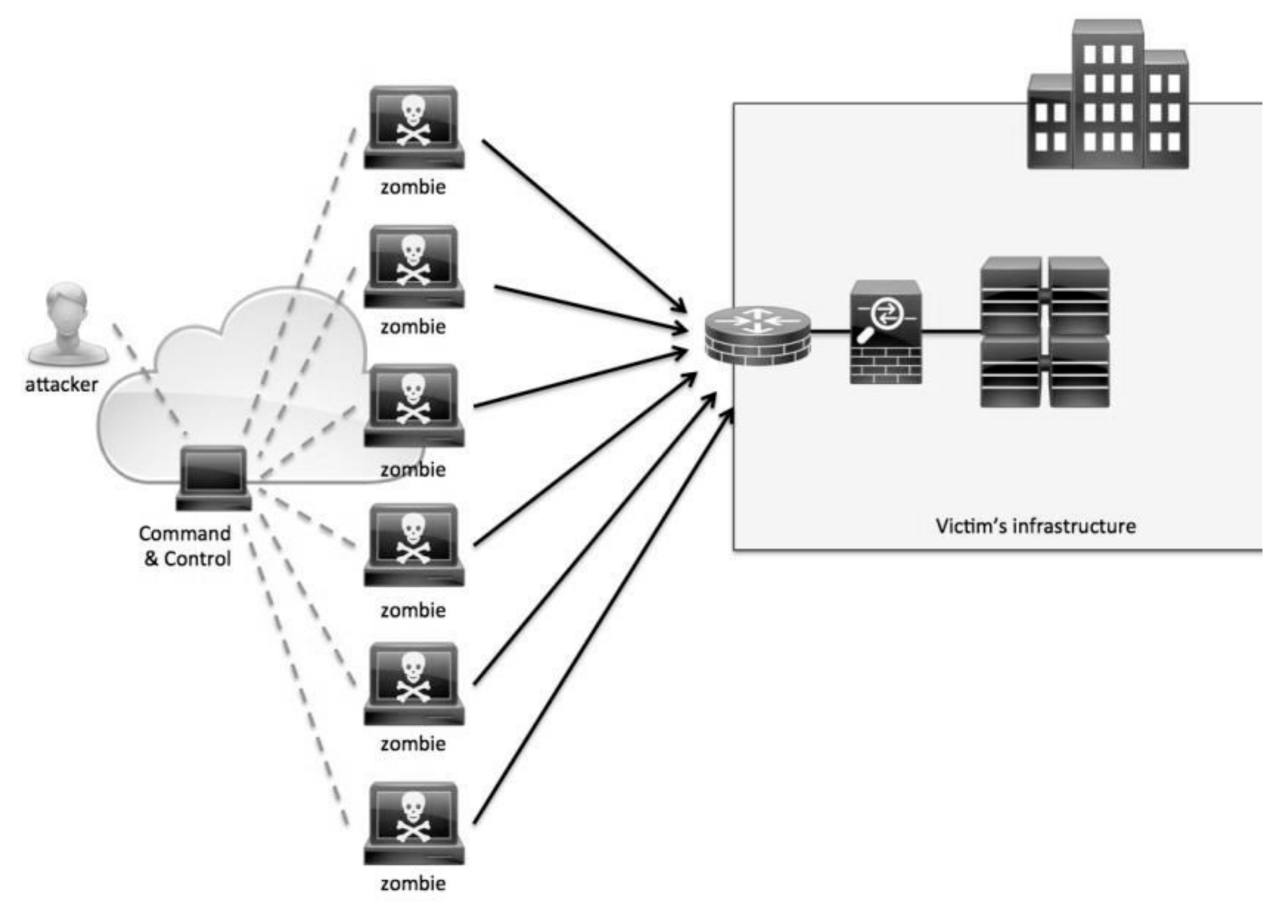
Vulnerabilities Exploited in DoS Attacks
Source: mdpi-res.com
Denial-of-service (DoS) attacks exploit weaknesses in network infrastructure and applications to overwhelm a target system, making it unavailable to legitimate users. Understanding these vulnerabilities is crucial for effective mitigation strategies. This section delves into the common vulnerabilities leveraged in DoS attacks, exploring their mechanisms and impact.
Common Network Vulnerabilities
DoS attacks often target fundamental network components. Weak points like open ports, unpatched systems, and poorly configured firewalls can be easily exploited. Attackers might flood a target with traffic directed at specific ports, overwhelming the system’s ability to process legitimate requests. A lack of robust rate limiting and traffic filtering mechanisms further exacerbates this vulnerability. For instance, an open port 23 (Telnet) without proper authentication allows attackers to easily initiate brute-force attacks, consuming server resources and potentially leading to a DoS condition.
The Role of Weak Security Protocols
Outdated or insecure protocols significantly increase a system’s susceptibility to DoS attacks. Protocols like older versions of SNMP (Simple Network Management Protocol) or Telnet lack robust authentication and encryption, making them easy targets for attackers to manipulate and send malicious traffic. For example, an attacker could exploit vulnerabilities in a weak SNMP implementation to send excessive management requests, thereby overloading the target device and causing a denial-of-service condition. The transition to secure protocols like SSH (Secure Shell) and HTTPS (Hypertext Transfer Protocol Secure) is vital for mitigating this risk.
Impact of Insufficient Bandwidth and Server Resources
Limited bandwidth and inadequate server resources are prime factors contributing to DoS vulnerability. If a server lacks the capacity to handle a sudden surge in traffic, even legitimate traffic might be dropped, resulting in a de facto denial of service. Similarly, insufficient processing power or memory can lead to system slowdowns or crashes when faced with a flood of requests, even if those requests are relatively small. A web server hosting a popular website, for example, might experience a DoS condition if it doesn’t have enough processing power to handle a large number of simultaneous requests, leading to slow response times or complete unavailability.
Software Flaws Leading to DoS Vulnerabilities
Software bugs and vulnerabilities can be exploited to launch highly effective DoS attacks. Buffer overflows, memory leaks, and race conditions are examples of programming flaws that can be manipulated to disrupt service. A well-known example is the Heartbleed vulnerability, which allowed attackers to extract sensitive data from affected servers, but also could have been used to trigger a DoS condition by exhausting server resources. Regular software updates and thorough security testing are essential to mitigate this risk.
Vulnerability Comparison
| Vulnerability | Exploitation Method | Impact | Mitigation |
|---|---|---|---|
| Open Ports | Port Scanning, Flooding | System Overload | Firewall Configuration, Port Securing |
| Weak Security Protocols (e.g., Telnet) | Malicious Traffic Injection | Resource Exhaustion | Protocol Upgrades (SSH, HTTPS) |
| Insufficient Bandwidth/Resources | Traffic Flooding | Service Unavailability | Capacity Planning, Resource Scaling |
| Software Flaws (e.g., Buffer Overflow) | Exploiting vulnerabilities | System Crash, Resource Exhaustion | Software Updates, Security Patches |
Mitigation and Prevention Strategies
Source: sectigo.com
DoS attacks, while terrifying in their potential to cripple online services, aren’t insurmountable. A multi-layered approach, combining proactive measures and reactive responses, is crucial for effective mitigation and prevention. Think of it like building a fortress – you need strong walls, vigilant guards, and a well-defined escape route in case of a breach.
Firewall and Intrusion Detection System Implementation
Firewalls act as the first line of defense, filtering incoming network traffic based on predefined rules. They can block suspicious traffic patterns often associated with DoS attacks, such as floods of requests from a single IP address or a burst of requests targeting specific ports. Intrusion Detection Systems (IDS), on the other hand, monitor network traffic for malicious activity, analyzing patterns and identifying potential attacks. By integrating firewalls and IDS, organizations can create a robust system that detects and blocks malicious traffic before it reaches their servers. Effective implementation involves configuring firewalls to block known attack vectors and setting up IDS alerts to trigger immediate responses to suspicious activity. Regular updates to both systems’ rule sets are essential to keep pace with evolving attack techniques.
Rate Limiting Techniques
Rate limiting is a crucial technique to control the flow of incoming requests. It involves setting limits on the number of requests allowed from a single IP address or a specific network within a given time frame. Exceeding these limits triggers automated responses, such as temporarily blocking the offending IP address or throttling the request rate. Implementing rate limiting involves configuring web servers or network devices to enforce these limits. This might involve using specialized modules or plugins for web servers (like Apache or Nginx) or leveraging features built into network hardware like routers or load balancers. A well-defined rate-limiting policy should balance security needs with the legitimate user experience, avoiding legitimate users being unintentionally blocked. For instance, a website might allow 10 requests per second from a single IP, increasing to 50 for trusted sources.
Content Delivery Network (CDN) Utilization, Denial of servicedos attack
CDNs distribute website content across multiple servers globally, reducing the load on a single origin server. This distributed architecture makes it significantly harder for attackers to overwhelm a single point of failure. If an attacker targets one CDN server, the rest continue to serve content without interruption. CDNs also often incorporate built-in DDoS mitigation techniques, like rate limiting and traffic scrubbing, adding another layer of protection. Choosing a reputable CDN provider with a proven track record in DDoS mitigation is crucial. The selection should consider factors such as geographic coverage, performance, and the specific mitigation techniques offered.
Responding to a DoS Attack: A Flowchart
The following describes a flowchart depicting the response to a DoS attack. The process starts with detection, then moves through mitigation, analysis, and recovery.
Imagine a flowchart with these boxes and arrows:
Box 1: DoS Attack Detected (e.g., via IDS alerts, performance monitoring tools) -> Arrow -> Box 2: Implement Mitigation Strategies (e.g., rate limiting, blocking malicious IPs, engaging CDN mitigation services) -> Arrow -> Box 3: Analyze Attack Vectors (e.g., identify attack source, type of attack) -> Arrow -> Box 4: Recovery and Post-Incident Review (e.g., restore services, analyze logs, strengthen security measures)
Impact and Consequences of DoS Attacks
Source: cloudflare.com
Denial-of-service (DoS) attacks aren’t just a minor inconvenience; they represent a significant threat with far-reaching consequences, impacting businesses, individuals, and even national infrastructure. The ripple effects of a successful attack can be devastating, leading to substantial financial losses, reputational damage, and legal repercussions. Understanding these impacts is crucial for effective prevention and mitigation strategies.
Economic Consequences of DoS Attacks
The financial toll of a DoS attack can be staggering. Direct costs include the expense of mitigating the attack, such as hiring cybersecurity experts, implementing new security measures, and recovering lost data. Indirect costs are even more substantial, encompassing lost revenue from disrupted business operations, damaged customer relationships, and the potential for future business losses due to decreased customer confidence. For example, a major e-commerce site experiencing a prolonged DoS attack could lose millions of dollars in sales during the downtime. The cost of recovering from a successful attack can also include legal fees and potential fines. A study by Cybersecurity Ventures estimated that the global cost of cybercrime, including DoS attacks, would reach $10.5 trillion annually by 2025, highlighting the severe economic impact of these attacks.
Reputational Damage from DoS Attacks
Beyond the immediate financial repercussions, DoS attacks inflict significant reputational damage. Customers lose trust in organizations unable to protect their services, leading to decreased customer loyalty and potential shifts to competitors. The negative publicity surrounding a successful attack can severely damage a company’s brand image, impacting its ability to attract new customers and investors. This damage can persist long after the attack is resolved, requiring extensive public relations efforts and rebuilding of trust. For instance, a bank experiencing a DoS attack might see a drop in customer deposits and a loss of confidence in its security measures, potentially impacting its stock price.
Legal Implications of Launching DoS Attacks
Launching a DoS attack is not only unethical but also illegal in most jurisdictions. Depending on the severity and impact of the attack, perpetrators face severe penalties, including hefty fines and imprisonment. The legal consequences extend beyond the attackers themselves; organizations can also face legal action for failing to adequately protect their systems from attacks, especially if negligence contributed to the attack’s success. Furthermore, international laws and treaties are increasingly addressing cybercrime, making cross-border prosecution of DoS attackers more likely.
Disruption of Services and Data Loss from DoS Attacks
The most immediate impact of a DoS attack is the disruption of services. Websites become inaccessible, online transactions are halted, and critical business operations are crippled. This disruption can last for hours, days, or even weeks, depending on the sophistication and scale of the attack. In addition to service disruption, DoS attacks can lead to data loss, either through direct destruction of data or through the inability to access and backup critical information during the downtime. The consequences of data loss can be catastrophic, especially for organizations handling sensitive customer data or financial information.
Impact of DoS Attacks on the Healthcare Sector
The healthcare sector is particularly vulnerable to DoS attacks. Hospitals and clinics rely heavily on interconnected systems for patient records, medical imaging, and administrative functions. A successful DoS attack can disrupt access to critical patient information, delay or prevent medical treatments, and compromise the safety and well-being of patients. Imagine a hospital’s electronic health records system becoming inaccessible during a major emergency; the consequences could be life-threatening. The disruption of these systems can also lead to significant financial losses due to cancelled appointments, delayed procedures, and the need for costly emergency measures.
Advanced DoS Attacks and Defenses
Stepping up the ante from simple DoS attacks, we enter the realm of Distributed Denial of Service (DDoS) attacks – a significantly more potent and challenging threat. These attacks leverage a vast network of compromised devices, forming a formidable army to overwhelm a target’s online resources. Understanding the intricacies of DDoS attacks and the robust defenses needed to counter them is crucial in today’s interconnected world.
Characteristics of Distributed Denial of Service (DDoS) Attacks
Unlike traditional DoS attacks originating from a single source, DDoS attacks flood the target with traffic from numerous compromised systems, known as bots. This distributed nature makes them incredibly difficult to mitigate, as tracing the origin and blocking each individual attack vector becomes a herculean task. The sheer volume of traffic overwhelms the target’s infrastructure, rendering it inaccessible to legitimate users. The impact can range from minor service disruptions to complete outages, leading to significant financial losses and reputational damage. The scale and sophistication of these attacks are constantly evolving, requiring proactive and adaptive defense strategies.
Techniques Used in DDoS Attacks
DDoS attacks employ a range of techniques to maximize their impact. Botnets, networks of compromised computers controlled remotely by attackers, are a cornerstone of DDoS attacks. These bots are often infected with malware and used to send massive amounts of traffic towards the target. Amplification techniques, which exploit vulnerabilities in network protocols to magnify the impact of the attack, are another critical component. For instance, an attacker might send a small request to a DNS server, which then responds with a much larger response to the target, effectively amplifying the attack’s power. Other techniques include UDP floods, which exploit the connectionless nature of UDP to send a deluge of packets, and HTTP floods, which target web servers with a massive number of requests.
Advanced DDoS Mitigation Techniques
Combating sophisticated DDoS attacks demands equally sophisticated defense mechanisms. Cloud-based DDoS mitigation services are increasingly popular, offering scalable and robust protection. These services leverage geographically distributed networks of servers to absorb and filter malicious traffic before it reaches the target’s infrastructure. Other advanced techniques include advanced firewall systems with sophisticated traffic analysis capabilities, and real-time threat intelligence feeds that identify and block emerging attack vectors. Implementing robust rate limiting and traffic shaping measures can also help to control the flow of incoming traffic and prevent overload. Furthermore, using techniques like anycast DNS can distribute traffic across multiple servers, increasing resilience.
Comparison of Traditional DoS and DDoS Attack Vectors
Traditional DoS attacks, originating from a single source, are relatively easier to detect and mitigate compared to DDoS attacks. Their limited bandwidth makes them less impactful. DDoS attacks, however, are far more challenging due to their distributed nature, utilizing multiple sources and often employing sophisticated techniques like botnets and amplification. The scale and complexity of DDoS attacks make them a far more significant threat, requiring more robust and proactive mitigation strategies. The key difference lies in the source and scale of the attack; a single source versus a distributed network of compromised machines.
Best Practices for Preventing and Responding to DDoS Attacks
Preventing and responding to DDoS attacks requires a multi-layered approach:
- Implement a robust security posture: Regular security audits, vulnerability scanning, and patching are crucial to prevent systems from becoming part of a botnet.
- Employ DDoS mitigation services: Leveraging cloud-based or on-premise DDoS mitigation solutions provides an extra layer of protection.
- Utilize advanced firewall systems: Configure firewalls to filter malicious traffic based on patterns and known attack signatures.
- Implement rate limiting and traffic shaping: Control the flow of incoming traffic to prevent overload.
- Develop an incident response plan: Establish a clear plan outlining steps to take in the event of a DDoS attack, including communication protocols and escalation procedures.
- Regularly test your defenses: Conduct simulated DDoS attacks to assess the effectiveness of your mitigation strategies and identify weaknesses.
- Monitor network traffic: Continuously monitor network traffic for suspicious activity, enabling early detection of potential attacks.
Case Studies of Notable DoS Attacks
DoS attacks aren’t just theoretical threats; they’ve caused significant disruptions and financial losses in the real world. Understanding these real-world examples helps us grasp the scale and sophistication of these attacks, and learn from past mistakes to better protect ourselves. Let’s delve into a prominent case study.
The 2016 Dyn DDoS Attack
The October 2016 attack on Dyn, a major Domain Name System (DNS) provider, serves as a prime example of a large-scale, distributed denial-of-service attack. Dyn’s infrastructure was overwhelmed by a massive flood of malicious traffic originating from a vast botnet of compromised IoT devices – things like security cameras and DVRs – many of which were infected with the Mirai malware. This attack crippled the availability of numerous high-profile websites and online services, including Twitter, Netflix, Spotify, and Reddit, for hours.
Methods Used and Impact
The attack leveraged a massive botnet, exploiting vulnerabilities in IoT devices with weak or default passwords. The sheer volume of requests from these compromised devices overwhelmed Dyn’s servers, preventing legitimate users from accessing the services they relied on. The impact was widespread and significant, demonstrating the potential for even relatively unsophisticated attacks to cause major disruptions. The disruption affected millions of users globally and resulted in substantial financial losses for businesses that relied on these affected services.
Response Strategies Implemented
Dyn responded by implementing various mitigation strategies, including traffic filtering, rate limiting, and working with internet service providers to block malicious traffic sources. However, the scale and sophistication of the attack made complete mitigation challenging. The attack highlighted the limitations of existing defenses against massive, distributed attacks originating from a vast number of sources.
Vulnerabilities Exploited
The primary vulnerability exploited was the lack of security on millions of IoT devices. Many of these devices shipped with default, easily guessable passwords, making them prime targets for botnet recruitment. The Mirai malware exploited these weak passwords to take control of the devices and use them to participate in the DDoS attack. The attack also exposed vulnerabilities in Dyn’s infrastructure, though the specifics weren’t publicly released.
Key Findings of the Dyn DDoS Attack
- The attack utilized a massive botnet composed of millions of compromised IoT devices.
- Weak passwords and default credentials on IoT devices were key vulnerabilities exploited.
- The Mirai malware played a crucial role in coordinating the attack.
- The attack caused widespread service disruption for numerous major websites and online services.
- Mitigation strategies proved challenging due to the scale and distributed nature of the attack.
Closure: Denial Of Servicedos Attack
In the ever-evolving landscape of cyber threats, understanding and mitigating Denial of Service attacks is no longer optional—it’s essential. While the sophistication of these attacks continues to grow, so too do the defenses. By proactively addressing vulnerabilities, implementing robust security measures, and staying informed about the latest attack vectors, individuals and organizations can significantly reduce their risk and ensure the continued availability of their critical online services. The fight against DoS attacks is a constant battle, but with the right knowledge and tools, the odds can be significantly improved.





