Detecting classifying ddos attacks – Detecting and classifying DDoS attacks is crucial for online survival. These relentless digital sieges, ranging from simple volumetric floods to sophisticated application-layer assaults, can cripple websites, disrupt services, and inflict significant financial damage. Understanding the various attack types – volumetric, protocol, and application – is the first step in building robust defenses. This exploration dives into the methods used to identify, categorize, and ultimately mitigate these pervasive threats, equipping you with the knowledge to protect your digital assets.
We’ll cover everything from basic network intrusion detection systems (NIDS) and signature-based detection to advanced techniques like machine learning and behavioral analysis. We’ll dissect real-world case studies, revealing the tactics employed by attackers and the strategies used to counter them. Get ready to navigate the complex world of DDoS defense, and learn how to stay one step ahead of the digital onslaught.
Introduction to DDoS Attacks
Distributed Denial-of-Service (DDoS) attacks are a significant threat to online services, ranging from small websites to massive online platforms. These attacks overwhelm a target system with a flood of internet traffic, rendering it inaccessible to legitimate users. Understanding the different types of attacks and their motivations is crucial for effective mitigation strategies.
DDoS attacks disrupt the normal operation of online services, causing significant financial and reputational damage. The sheer volume of traffic can crash servers, making websites unavailable, and crippling online businesses. The impact extends beyond monetary losses, affecting user trust and potentially jeopardizing sensitive data.
Types of DDoS Attacks
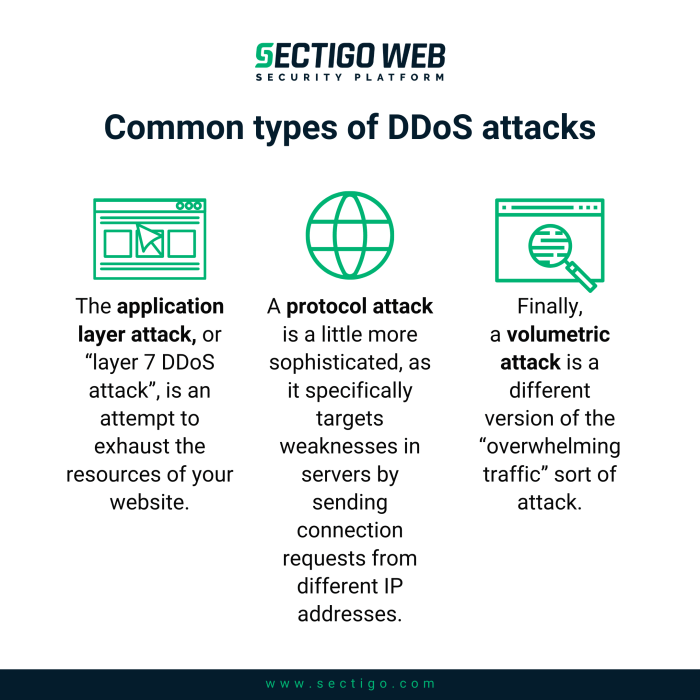
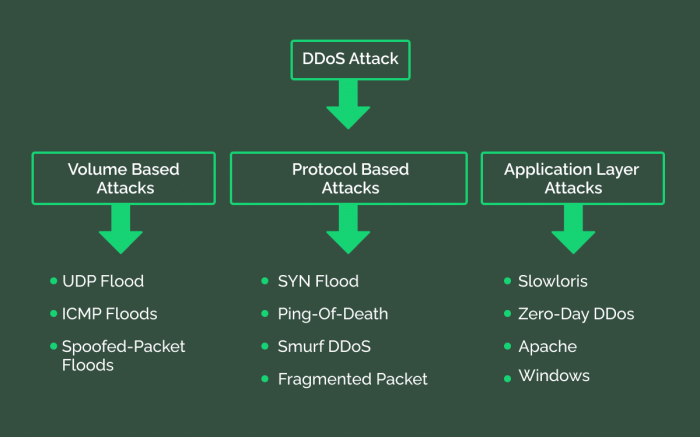
DDoS attacks are categorized based on their methods. Understanding these categories helps in identifying and responding to these attacks effectively. Three primary types are volumetric, protocol, and application layer attacks.
- Volumetric Attacks: These attacks flood the target with massive amounts of traffic, overwhelming its bandwidth and preventing legitimate requests from being processed. Common examples include UDP floods and ICMP floods, which send vast quantities of packets to consume network resources.
- Protocol Attacks: These attacks exploit vulnerabilities in network protocols to disrupt communication. They often target the network infrastructure rather than the application itself. SYN floods, for instance, exploit the TCP three-way handshake to exhaust server resources.
- Application Layer Attacks: These attacks target specific applications or services running on the target server. They aim to exhaust application resources, such as memory or processing power, by sending numerous requests designed to consume those resources. HTTP floods and Slowloris attacks are examples of this type.
Motivations Behind DDoS Attacks
The motivations behind launching DDoS attacks are diverse and can range from simple vandalism to financially motivated attacks.
- Extortion: Attackers may demand payment to stop an ongoing attack or to prevent future attacks. This is often seen targeting businesses or individuals with a high online profile.
- Vandalism/Activism: Some attacks are carried out as acts of protest or vandalism, targeting organizations or individuals whose actions the attacker disapproves of. These attacks can be politically or ideologically motivated.
- Competitive Advantage: In some cases, businesses may use DDoS attacks to disrupt competitors, gaining a temporary advantage in the marketplace. This is an unethical and illegal practice.
- Testing Security: Although ethically questionable, some organizations might conduct “ethical hacking” involving DDoS attacks to test the resilience of their own systems. This must be done with proper authorization and within strict ethical guidelines.
Impact of Successful DDoS Attacks
The consequences of a successful DDoS attack can be severe and far-reaching, affecting organizations and individuals alike.
- Financial Losses: Downtime caused by DDoS attacks can lead to significant financial losses, including lost revenue, operational costs, and reputational damage.
- Reputational Damage: Inability to access online services can severely damage an organization’s reputation, leading to customer churn and loss of trust.
- Data Breaches: While not always directly caused by DDoS attacks, the disruption can create vulnerabilities that could lead to secondary security incidents, such as data breaches.
- Legal Ramifications: Organizations can face legal repercussions for failing to adequately protect their systems from DDoS attacks, especially if sensitive data is compromised.
Detection Methods for DDoS Attacks
Source: sectigo.com
Detecting Distributed Denial-of-Service (DDoS) attacks requires a multifaceted approach, leveraging both signature-based and anomaly-based detection techniques. Understanding the strengths and weaknesses of each method is crucial for building a robust defense strategy. These methods, when combined with a well-implemented Network Intrusion Detection System (NIDS), offer a comprehensive solution for identifying and mitigating DDoS threats.
Signature-Based and Anomaly-Based Detection
Signature-based detection relies on identifying known attack patterns or “signatures.” This involves comparing network traffic against a database of pre-defined signatures representing various DDoS attack types. While effective against known attacks, it struggles with novel or mutated attacks that haven’t been added to the signature database. Conversely, anomaly-based detection focuses on identifying deviations from established network traffic patterns. It establishes a baseline of “normal” network behavior and flags any significant deviations as potential attacks. This method is better at detecting zero-day attacks but can generate false positives if the baseline isn’t properly configured or if network behavior changes legitimately. A hybrid approach, combining both methods, often provides the most comprehensive protection.
Implementing a Basic Network-Based Intrusion Detection System (NIDS)
Implementing a basic NIDS to detect DDoS activity involves several key steps. First, select and install appropriate NIDS software. Many open-source options exist, offering varying levels of functionality and complexity. Next, configure the NIDS to monitor the relevant network segments. This involves specifying the interfaces to monitor and the types of traffic to analyze. Then, define the rules and thresholds for detecting DDoS activity. This might involve setting limits on the number of packets per second from a single IP address or the total bandwidth consumed. Following this, regularly review the NIDS logs for alerts and suspicious activity. This proactive monitoring allows for timely response to potential attacks. Finally, integrate the NIDS with other security tools, such as firewalls and intrusion prevention systems (IPS), to enhance overall security posture. This integrated approach facilitates coordinated responses to identified threats.
Common Indicators of Compromise (IOCs) Associated with DDoS Attacks
Understanding common indicators of compromise is vital for effective DDoS detection and mitigation. The following table highlights key IOCs, their descriptions, and potential mitigation strategies.
| IOC | Description | Mitigation Strategy | Example |
|---|---|---|---|
| High Volume of Traffic from Single Source or Multiple Sources | A sudden surge in network traffic originating from a single IP address or a coordinated group of IPs. | Rate limiting, traffic filtering, and blacklisting. | Thousands of SYN packets originating from hundreds of different IP addresses targeting a single web server. |
| Unusual Packet Sizes or Types | An unexpected increase in the number of unusually large or small packets, or the appearance of uncommon packet types. | Packet filtering based on size and type. | A flood of small UDP packets, exceeding normal network traffic. |
| High CPU or Network Resource Utilization | Significant spikes in CPU utilization or network bandwidth consumption, indicating server overload. | Load balancing, scaling resources, and implementing DDoS mitigation services. | Web server CPU usage reaching 100% and network interfaces reaching maximum bandwidth. |
| Slow Response Times | Significant delays in application response times, indicating network congestion or server overload. | Caching, content delivery networks (CDNs), and application-level DDoS protection. | Website loading times increase dramatically, impacting user experience. |
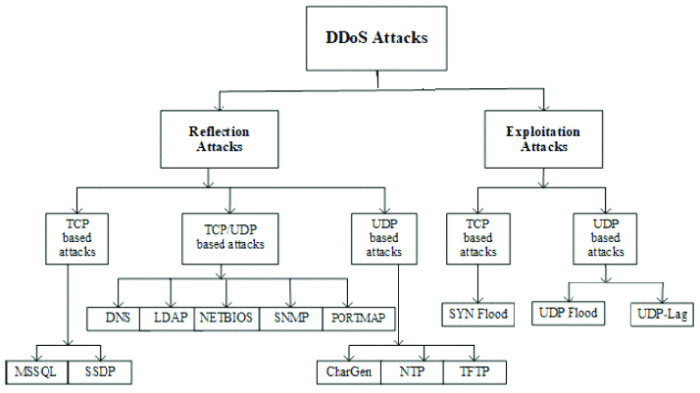
Classification of DDoS Attacks
DDoS attacks aren’t a monolithic threat; they come in various flavors, each demanding a unique defense strategy. Accurately classifying these attacks in real-time is crucial for effective mitigation, but it’s a surprisingly tricky business. Think of it like trying to identify different species of birds based solely on their flight patterns – challenging, right?
The complexity stems from the ever-evolving tactics employed by attackers. They constantly modify their techniques to evade detection and overwhelm defenses. Furthermore, the sheer volume of network traffic during a DDoS attack can make analysis difficult, obscuring the underlying attack signature. Add to this the potential for sophisticated camouflage techniques, and you have a real challenge for network security professionals.
Challenges in Real-Time DDoS Attack Classification
Real-time classification faces significant hurdles. The dynamic nature of DDoS attacks, with attackers constantly shifting tactics, necessitates adaptive classification systems. Traditional signature-based approaches struggle to keep pace with new attack vectors. The sheer scale of traffic during an attack can overwhelm even sophisticated analysis tools, leading to delays or inaccuracies in classification. Finally, the ability of attackers to mask their actions using techniques like botnet camouflage makes accurate identification even more difficult. Consider the case of a sophisticated Mirai-based attack leveraging a massive botnet: identifying the true source and the specific attack type requires advanced analysis beyond simple traffic volume monitoring.
A Flowchart for Classifying DDoS Attacks
A robust classification process requires a multi-step approach. The following flowchart illustrates a possible process, starting with initial traffic analysis and progressing through various stages of identification.
Imagine a flowchart with the following stages:
1. Initial Traffic Monitoring: High traffic volume detected? (Yes/No). If No, no DDoS attack. If Yes, proceed.
2. Traffic Analysis: Identify unusual traffic patterns. High volume of UDP packets? High volume of SYN packets? High volume of HTTP requests? (Yes/No to each).
3. Protocol Analysis: Determine the targeted protocol (UDP, TCP, HTTP, etc.).
4. Source Identification: Attempt to identify the source IP addresses. Are they distributed across a wide range (suggestive of a botnet)? (Yes/No).
5. Attack Type Classification: Based on the preceding analysis, classify the attack (e.g., UDP flood, SYN flood, HTTP flood, volumetric attack, application-layer attack).
6. Mitigation Strategy Selection: Choose an appropriate mitigation strategy based on the identified attack type.
This flowchart simplifies a complex process, but it highlights the need for a systematic approach involving multiple layers of analysis.
Key Features for Differentiating DDoS Attack Types
Different DDoS attacks exhibit distinct characteristics. A UDP flood, for example, is characterized by a massive influx of UDP packets to a target server, often overwhelming its resources. Conversely, a SYN flood targets the TCP handshake process, flooding the target with SYN requests without completing the connection, exhausting server resources. HTTP floods, on the other hand, target web servers by sending an overwhelming number of HTTP requests, aiming to exhaust server capacity and bring down the website. The key differences lie in the targeted protocol and the specific method used to overwhelm the target. Understanding these differences is essential for developing effective countermeasures.
Mitigation Strategies for DDoS Attacks: Detecting Classifying Ddos Attacks
Source: researchgate.net
So, you’ve learned about DDoS attacks – the digital equivalent of a swarm of angry bees targeting your website. Now, let’s talk about fighting back. Mitigating DDoS attacks isn’t about stopping every single attack; it’s about minimizing their impact and ensuring your services stay online. This requires a multi-layered approach, combining preventative measures with reactive solutions.
Effective DDoS mitigation relies on a blend of technologies and strategies. The goal is to identify and filter malicious traffic before it reaches your servers, preventing them from being overwhelmed. This involves a combination of techniques aimed at both preventing attacks and minimizing their effects once they’ve started.
Rate Limiting
Rate limiting is a fundamental defense mechanism. It works by setting limits on the number of requests a single IP address or a group of IP addresses can make within a specific timeframe. If a source exceeds the predefined threshold, its requests are temporarily blocked or throttled. This is particularly effective against simple volumetric attacks like UDP floods, where a large number of requests originate from a relatively small number of sources. For instance, a website might limit the number of login attempts from a single IP to prevent brute-force attacks, a type of DDoS attack. Sophisticated rate-limiting systems can also adapt to changing attack patterns, dynamically adjusting thresholds based on real-time traffic analysis.
Blackholing
Blackholing is a more drastic approach. It involves dropping all traffic from a suspected malicious source without further inspection. While effective at stopping an attack quickly, it also carries the risk of blocking legitimate traffic if the source identification is inaccurate. This is why blackholing is often used as a last resort, or in conjunction with other techniques that provide more accurate traffic filtering. Imagine a network security team noticing a sudden surge of traffic from a specific IP address – blackholing that IP address would immediately halt the flood of malicious packets, preventing further disruption. However, if that IP address also happens to be a legitimate customer, the service would be interrupted until the issue is resolved.
Scrubbing
Scrubbing is the process of cleaning malicious traffic from the network stream before it reaches your servers. This usually involves sending traffic to a dedicated scrubbing center, a highly resilient network infrastructure equipped to filter out malicious traffic while allowing legitimate traffic to pass through. Scrubbing centers use advanced techniques to identify and remove malicious packets, including deep packet inspection and anomaly detection. Think of it as a highly efficient filter that cleans the incoming traffic, removing the harmful elements before they can reach your servers. The cleaned traffic is then forwarded to your network, ensuring the availability of your services. This is particularly useful for large-scale, sophisticated attacks that require advanced filtering capabilities.
Comparison of DDoS Mitigation Solutions
Choosing between on-premise and cloud-based DDoS mitigation solutions depends on various factors, including budget, technical expertise, and the scale of your infrastructure. On-premise solutions offer greater control but require significant investment in hardware and expertise. Cloud-based solutions, on the other hand, offer scalability and cost-effectiveness, especially for smaller organizations. A large enterprise with a massive network infrastructure might opt for an on-premise solution to maintain tight control over security, while a smaller e-commerce business might find a cloud-based solution more practical and cost-effective.
Best Practices for Preventing and Mitigating DDoS Attacks
Preventing and mitigating DDoS attacks requires a proactive approach. It’s not enough to simply react to attacks; you need to implement preventative measures to minimize their impact and reduce the likelihood of successful attacks.
- Regularly update your network infrastructure and security software to patch vulnerabilities.
- Implement robust access control lists (ACLs) to limit access to your network resources.
- Use a web application firewall (WAF) to protect against application-layer attacks.
- Employ a distributed denial-of-service (DDoS) mitigation service to protect against large-scale attacks.
- Monitor your network traffic for suspicious activity and respond promptly to any anomalies.
- Develop an incident response plan to address DDoS attacks effectively.
- Regularly test your DDoS mitigation strategies to ensure they are effective.
- Train your staff on DDoS attack recognition and response procedures.
Advanced DDoS Detection Techniques
Source: securetriad.io
Detecting and mitigating sophisticated DDoS attacks requires moving beyond traditional signature-based methods. The sheer volume and complexity of modern attacks necessitate leveraging advanced techniques that can adapt to evolving threat landscapes. This involves incorporating machine learning algorithms, sophisticated behavioral analysis, and a deep understanding of network flow data.
The rise of increasingly complex DDoS attacks necessitates the adoption of advanced detection techniques that go beyond simple signature matching. These advanced methods rely heavily on the power of machine learning, behavioral analysis, and the careful examination of network flow data to identify and respond to these sophisticated threats effectively. The goal is to detect anomalies and patterns indicative of an attack before significant damage is done.
Machine Learning for Enhanced DDoS Detection Accuracy
Machine learning algorithms are revolutionizing DDoS attack detection. By training models on vast datasets of network traffic, both benign and malicious, these algorithms can learn to identify subtle patterns and anomalies that are indicative of DDoS activity. This surpasses the limitations of rule-based systems, which often struggle to keep pace with the ever-changing tactics of attackers. For instance, a machine learning model might learn to identify unusual spikes in traffic from specific IP addresses or unusual patterns in packet sizes and inter-arrival times, even if these patterns haven’t been seen before. This proactive approach allows for the identification of zero-day attacks, which traditional methods often miss. The accuracy of these models continuously improves as they are exposed to more data, leading to a more robust and adaptable defense system.
Behavioral Analysis for Sophisticated DDoS Attack Identification, Detecting classifying ddos attacks
Behavioral analysis focuses on identifying deviations from established network traffic patterns. Instead of relying on pre-defined signatures, this approach examines the overall behavior of network traffic, looking for anomalies such as sudden increases in traffic volume, unexpected changes in traffic patterns, or unusual source-destination relationships. For example, a sudden surge in SYN packets without corresponding ACK packets could indicate a SYN flood attack. Similarly, a large number of requests originating from a small set of IP addresses might signal a UDP flood or other volumetric attack. Sophisticated attacks often try to mask their behavior by using botnets distributed across many IP addresses, making simple volume-based detection less effective. Behavioral analysis helps to uncover these hidden patterns and classify the attack based on its unique characteristics.
Network Flow Data Analysis for DDoS Anomaly Detection
Network flow data provides a granular view of network traffic, recording information such as source and destination IP addresses, ports, protocols, packet counts, and bytes transferred. Analyzing this data can reveal anomalies indicative of DDoS activity. A typical DDoS attack pattern might show a sudden and significant increase in traffic volume from numerous sources targeting a specific destination.
Imagine a network flow graph. The X-axis represents time, and the Y-axis represents the number of packets per second. Under normal conditions, the graph would show a relatively stable baseline. During a DDoS attack, a sharp spike would appear, dramatically exceeding the baseline. This spike would be characterized by a large number of flows originating from many different IP addresses, all directed towards the same target. Further analysis might reveal that these flows are using the same port and protocol, further confirming the attack. By analyzing the flow data, security professionals can identify the source of the attack, the target, and the type of attack being used, enabling a more targeted response.
Case Studies of DDoS Attacks
Understanding the real-world impact of DDoS attacks requires examining specific instances. These case studies illustrate the diverse methods employed by attackers, the devastating consequences for victims, and the strategies used to mitigate these attacks. Analyzing these events provides invaluable insights into the evolving landscape of cyber threats and the ongoing arms race between attackers and defenders.
High-profile DDoS attacks have targeted major companies, government agencies, and even critical infrastructure. The scale and sophistication of these attacks continue to increase, highlighting the need for robust security measures. These attacks not only cause financial losses but can also disrupt essential services, impacting individuals and society as a whole. The methods used range from simple volumetric attacks flooding networks with traffic to more sophisticated application-layer attacks exploiting vulnerabilities in specific software.
The 2016 Dyn DDoS Attack
The October 2016 attack against Dyn, a major Domain Name System (DNS) provider, serves as a prime example of a large-scale DDoS attack. This attack leveraged a massive botnet of compromised IoT devices (primarily Mirai-infected devices) to flood Dyn’s servers with traffic, resulting in widespread outages for many prominent websites and online services, including Twitter, Netflix, and Spotify. The attack demonstrated the power of IoT botnets and the potential for significant disruption to the internet infrastructure. Mitigation efforts involved traffic filtering, rate limiting, and working with internet service providers to block malicious traffic sources.
The attack lasted several hours, causing significant disruption to users globally. The sheer scale of the attack, originating from a massive botnet, overwhelmed Dyn’s infrastructure. The impact extended far beyond Dyn itself, cascading across the internet and impacting numerous websites and online services.
The 2016 Dyn attack underscored the vulnerability of critical internet infrastructure to large-scale DDoS attacks and the potential for significant societal disruption. The reliance on interconnected systems highlighted the need for improved security measures across the entire internet ecosystem, not just at individual companies.
The 2022 GitHub DDoS Attack
In February 2022, GitHub experienced a large-scale DDoS attack that leveraged a massive botnet of compromised devices to flood its servers with requests. While GitHub did not disclose the exact details of the attack, they reported successfully mitigating the attack with their existing infrastructure and security measures. This case highlights the ongoing need for robust security measures to protect against increasingly sophisticated DDoS attacks. The scale of the attack was significant, demanding immediate and effective mitigation strategies from GitHub’s security team. Their ability to successfully mitigate the attack showcases the importance of proactive security investments and a robust incident response plan.
Last Word
In the ever-evolving landscape of cyber warfare, mastering the art of detecting and classifying DDoS attacks is no longer a luxury, but a necessity. From understanding the attacker’s motivations to leveraging advanced technologies like machine learning, a multi-faceted approach is essential. By implementing robust mitigation strategies, staying updated on emerging threats, and embracing best practices, organizations and individuals can significantly reduce their vulnerability to these devastating attacks. The fight against DDoS is ongoing, but with knowledge and preparedness, we can win.